This how-to video will help you expand your iPod library. Rockbox turns your iPod into a FLAC- and OGG-playing, open-source monster. Learn how to install this custom firmware on your iPod to enable it to play all sorts of audio file types and even games. Watch this video tutorial and learn how to free your iPod with Rockbox.

Make a classic Margarita with Trago top shelf tequila! Explore the silver, reposado and the anejo varieties of tequila. This margarita is shaken, not stirred or frozen.

This instructable aims to show you how to cut any type of disk to a desired shape. It is particularly useful in cutting down cheap 12cm DVD-+R 's into more expensive (can be up to 10 times more) 8cm DVD-+R disks. The technique shown here works with all disk types. The video below shows us cutting a music CD into a heart shape, and also illustrates the basics of cutting 12cm disks into 8cm ones. The actual cutting of a disk (and the guide) can be seen here:

Selene Yeager takes you through an interval cycling workout called 3-2-1 for hill surges. The format of the workout is to do repeated hard short bursts with increasing intensity. This type of workout will help when you're biking up hills or trying to overcome your limits.

Chef Don from HouseCallChef demonstrates how to grill mushrooms, asparagus, zucchini and yellow squash. You can also grill other vegetables such as parsnip, rutabaga, potatoes, tomatoes or peppers, and even some fruits like pineapple, watermelon, apples and oranges. You can use any type of grill that you want.
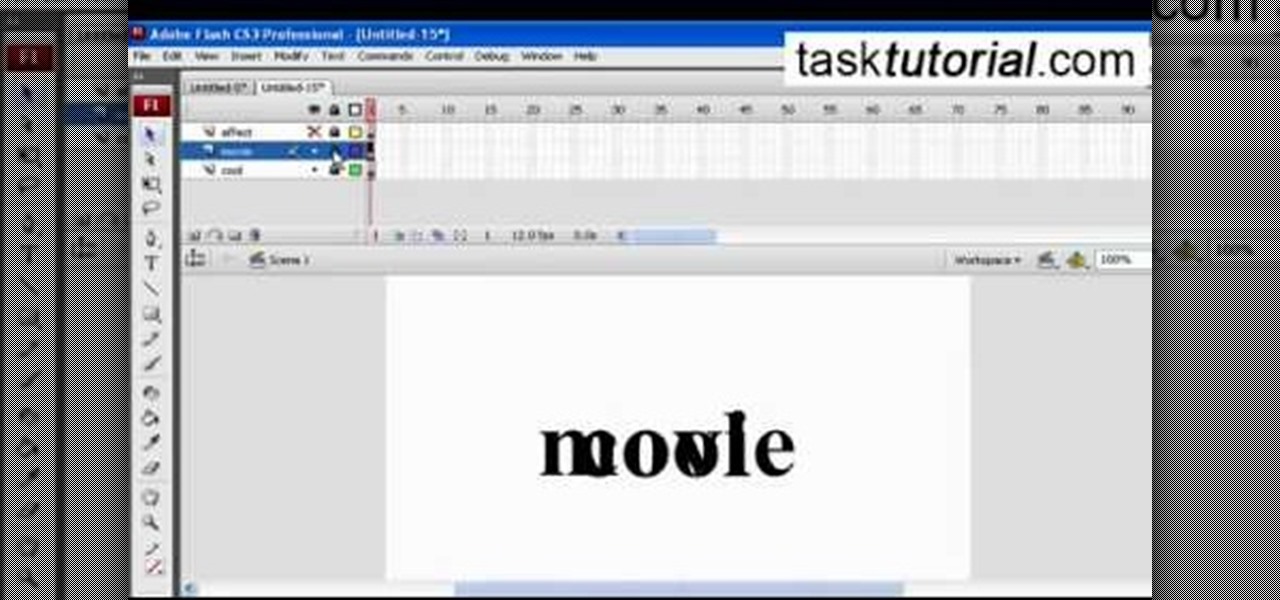
A great free video training from tasktutorial on how to create a cool movie text effect in Flash. Start by creating the text; type in "cool", rename the layer and lock it. Now type "movie" and rename the layer. Type in "effect" and rename this layer as well. Now focus on the first layer. Convert it to movie clip. Now convert the other two layers to movie clips as well. Stack the three layers on top of each other. Next add a key frame starting from frame 10. Select the "cool" layer. Re-size it...

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to transform a photo into a flashy poster in Photoshop.

Stan shows an easy way to see and clean the files that are hogging hard drive space in the computer using a free software called "windirtstat". Now enter the following address in the web browser "windirtstat.info" and scroll down the page until you get the downloading and installing section. Click on the link "windirtstat1.1.2Setup(Ansi&Unicode)" which will be right after the "for all flavors of windows" this will direct you to "SOURCEFORGE.NET" download creations. This will ask you to save t...

In this series of videos you'll learn how to draw with charcoal from a professional artist. Expert William Cotterell shows you what types of art supplies you'll need to get started, including various types of charcoal, compressed and pencil varieties, types of erasers that work best with charcoal, and the best types of paper for making charcoal drawings. He also shares tips for choosing a subject, understanding light, blending techniques, adding highlights, and using Fixatif to protect your w...

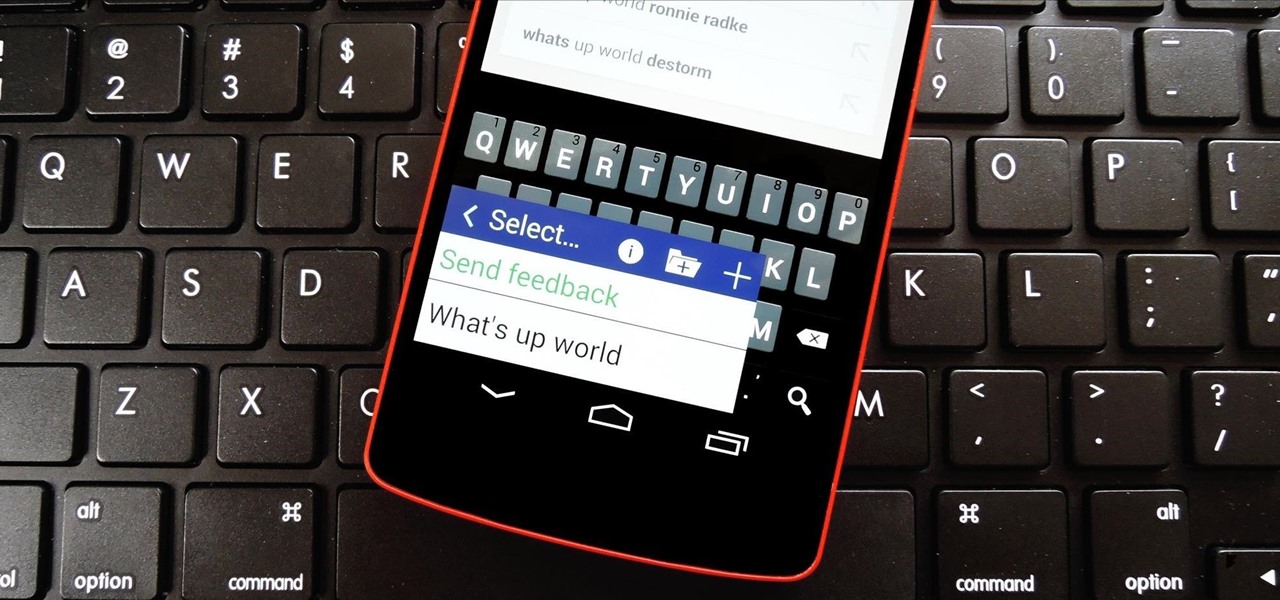
Remember when typing without physical keys seemed ridiculous? Now, touch typing is the smartphone norm. That said, mistakes are inevitable on small screens. So before you start hammering on that delete key or shaking your iPhone like a madman, know that there's a better way to undo text you didn't mean to type — no shaking involved.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

After learning that you'll need to spend at least $74 on a special charger and a USB Type-C Lightning cable to enable fast charging on the new iPhone X and iPhone 8 models, you may be wondering why you can't just use the standard Lightning cable. While we can't answer why Apple didn't include the USB-C cable in the box with their new phones, we can explain why you need USB-C to enable fast charging.

Typing out thirty hashtags on Instagram is always such an annoying process. Figuring out the best hashtags to use to get more likes is also tricky. You can't just keep copying and pasting the same hashtags on every post — that's like attacking the same tribe every time. You got to diversify, which takes a lot of conscious effort to be on top of the current best hashtags to use.

Dramatic new research may change the fate of the hundreds of people who wait for a kidney transplant every year. The study hinged on the ability to cure hepatitis C infections, a possibility that became a reality in 2014.

As many as 700 species of bacteria live on our teeth and in our mouth, and just like the microbiomes inhabiting other parts of our bodies, they change in response to diseases and other health conditions.

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

From laptops to tablets, technology is taking over classrooms. Elementary schools offer kids tablets, and college students are bringing laptops into lecture halls, leaving their notebooks behind. Today, many students prefer putting their fingers to a keyboard rather than pen to paper, but are these helpful devices truly beneficial?

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

What Is IPython? IPython is a richly featured replacement for the standard python interpreter. It offers a wider range of functionality, that the standard

The Nexus 6 is one of the few devices on the market that sports a 1440p "QHD" display. This means that the amount of pixels displayed is higher than almost any other smartphone, which sounds great on the surface, but is not without its drawbacks.

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

There are a lot of instances where we find ourselves typing virtually the same phrase that we've typed many times before. Whether it's the standard spousal reply of "I'll be home in a few", or a work-related phrase like "I'll have that to you by the end of the day", typing phrases like these can feel very redundant at times.

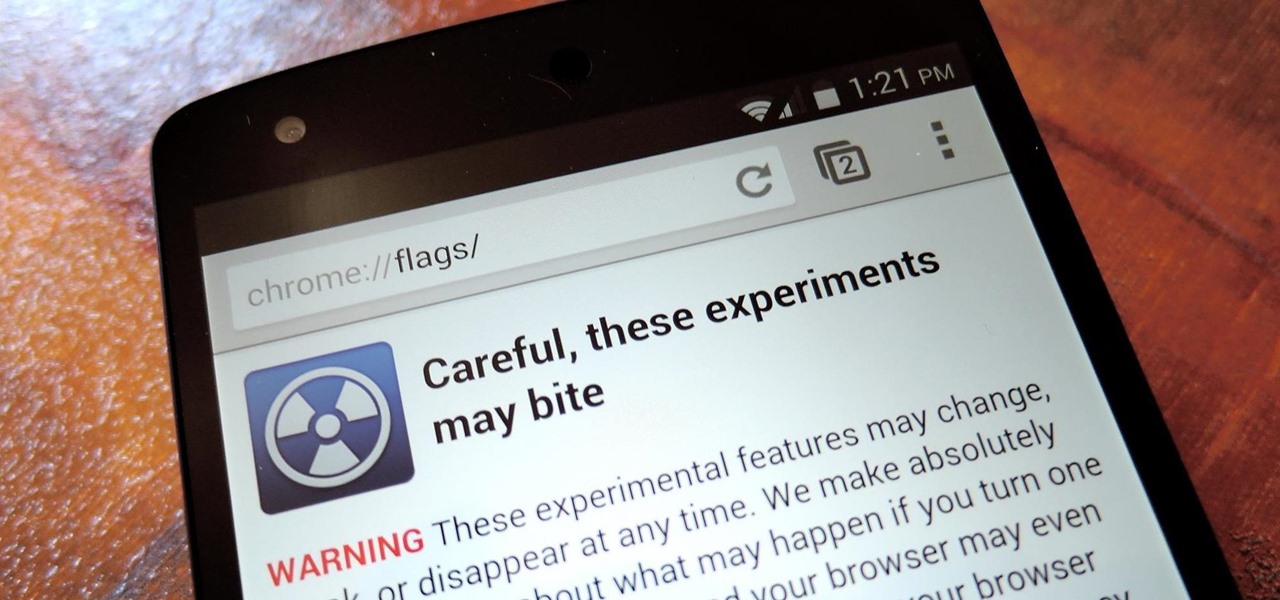
With the release of Jelly Bean, Chrome became the default web browser on Android. The wildly successful desktop browser was now fully entrenched in the world's largest mobile operating system.

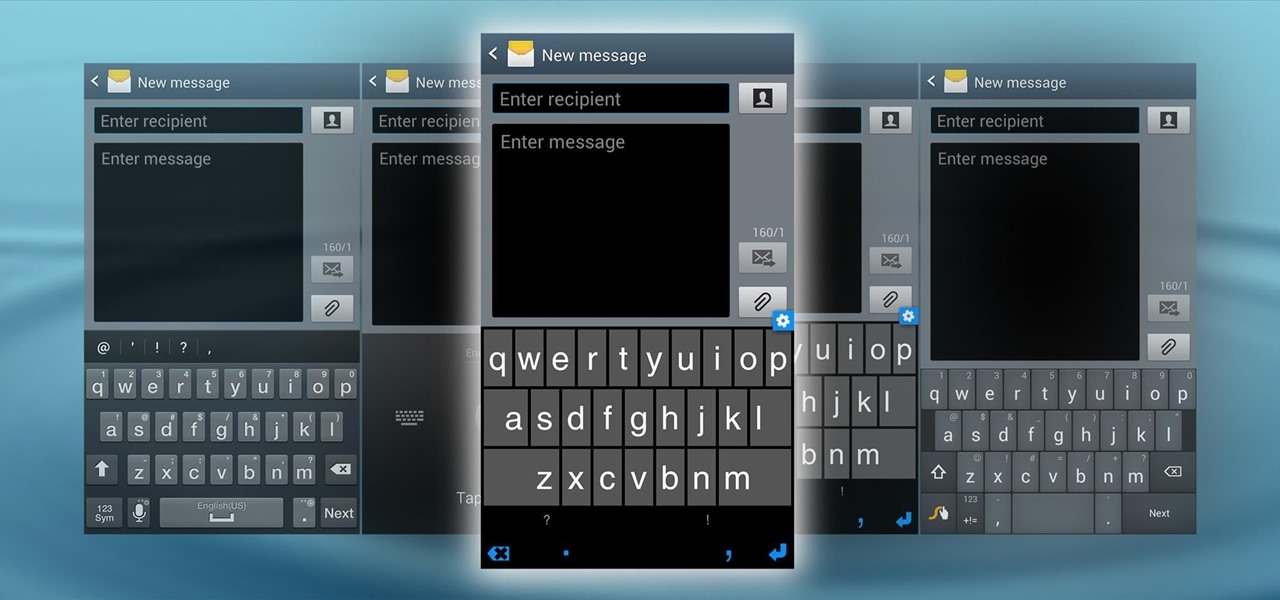
The space on your phone is extremely valuable, so getting the most out of your screen real estate can help you out when multitasking or for just making your device feel bigger. One thing that is often overlooked when it comes to saving space on the screen is the keyboard.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

The absence of a physical keyboard is both a gift and a curse. When it was announced in 2007 that the first iPhone would have a touchscreen only, people literally lost their shit. Now, almost 7 years later, you'd be hard-pressed to find a smartphone that still has a physical keyboard.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

Who doesn't hate Auto Correct? There's nothing worse than hitting 'Send' only to realize that your phone betrayed you by changing a word so that your message doesn't even mean the same thing anymore—especially when it's going to someone like your boss or parents.

With the use of Terminal, anyone can run multiple instances of the same application on a Mac. When you have multiple windows open in a web browser, the windows are all running under the same Process ID (PID). But, with multiple instances, each has its own unique PID. So why would you want to run multiple instances of the same app? There are several reasons a person may run clones of the same application, but the most popular would be so that the user could multitask. Some applications, like t...

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.