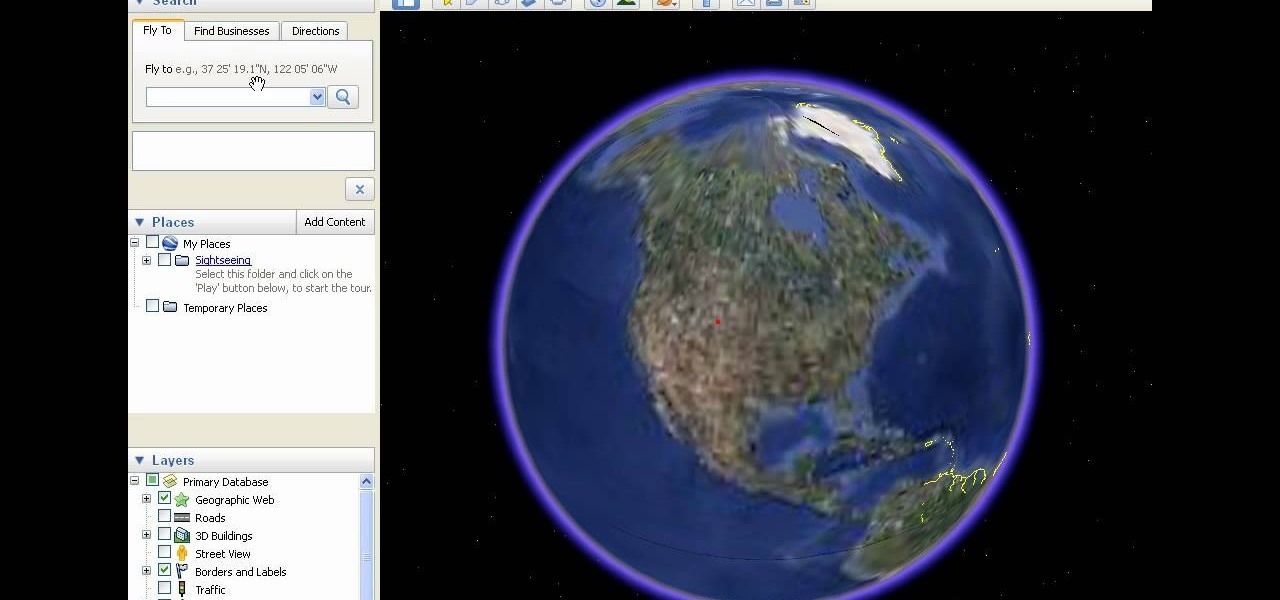
This video shows how to download and use Google Earth. To download it, go to earth.google.com and click “Download Google Earth”. Then follow the directions according to where you want to save it, and it will automatically be installed. You will see an icon pop up on your desktop. Double click on the icon to open Google Earth.

Weddings are very expensive and one way to say a little is to make or have you maid of honor make the wedding bouquet and the bridesmaids’ bouquets. You need a straight handle bridal bouquet holder and a stand to hold the bouquet holder in place while you work on it. You will need 12 roses fully hydrated and open.

Peggy Erbison shares her knowledge of palmistry in this video. The heart line starts under the pinky and moves across and up towards the middle and index finger. The next line she talks about is the head line. This line is the center line that explains how your thinking is. The line that rounds out and wraps around the base of the thumb is the life line. This line connects to the head line at the beginning. These are the 3 main lines on the palm. Contrary to popular belief, the life line does...
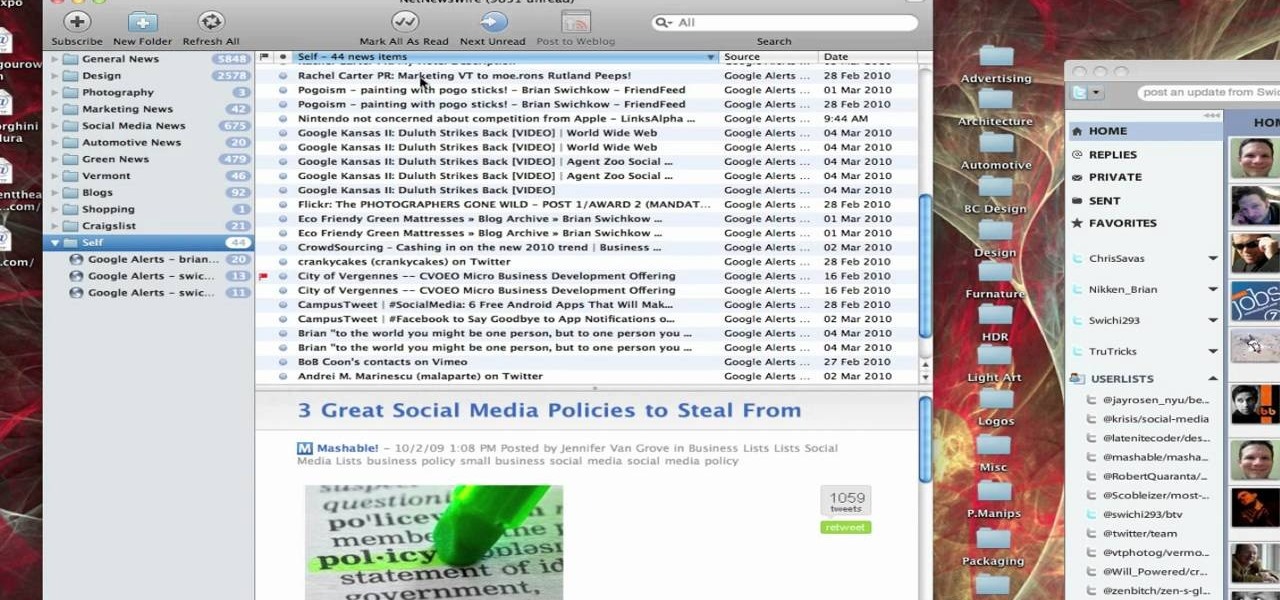
This video tutorial from TruTricks presents how to setup Google customized alerts.Open your internet browser and search for Google Alerts using Google search engine.Click first result that says Google Alerts.You will need to sign in to use this Google feature.Google or Google mail account will work. If you don't have it you should create one.After you signed in Google Alerts welcome screen will open.Here you can create new Google alerts using Create a Google Alert window.Enter Search Term you...

You are typing along and you notice one of they keys on your keyboard isn't responding like it should. It is common to get a stuck key and you won't need to take your keyboard to fix this problem. You can do it right at home.

This how-to video is about how to use command prompt to view the blocked websites at school. This step by step instruction will help one to open the blocked websites at school.

This video tutorial from TutVid shows how to create a simple movie poster text effect in Adobe Photoshop CS4.

Watch this science video tutorial from Nurd Rage on how to get lithium metal from an Energizer battery. They show you how to get Lithium Metal from an Energizer Ultimate Lithium battery.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to send SMS and MMS messages on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

In this video series, learn how to dress different plus size body types. Our expert, Michele Varon, shows you the different types of plus size women. With her plus size models, you can see which body type you most closely resemble. Once you know, you can start to find flattering clothing for various occasions.

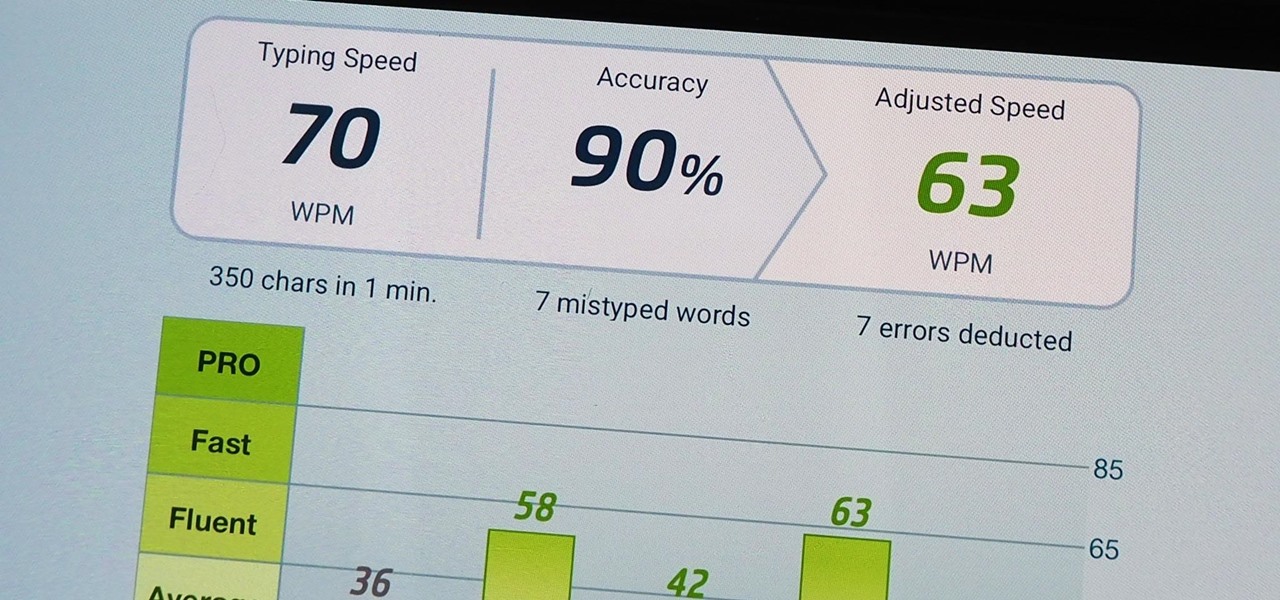
We use our smartphones every single day. They're a part of our daily routine, and as a result, we've gotten really good at using them — especially when it comes to typing very quickly. But just how fast can you type on your iPhone? Can you match your speed on a physical keyboard for your computer or tablet? You might just surprise yourself.

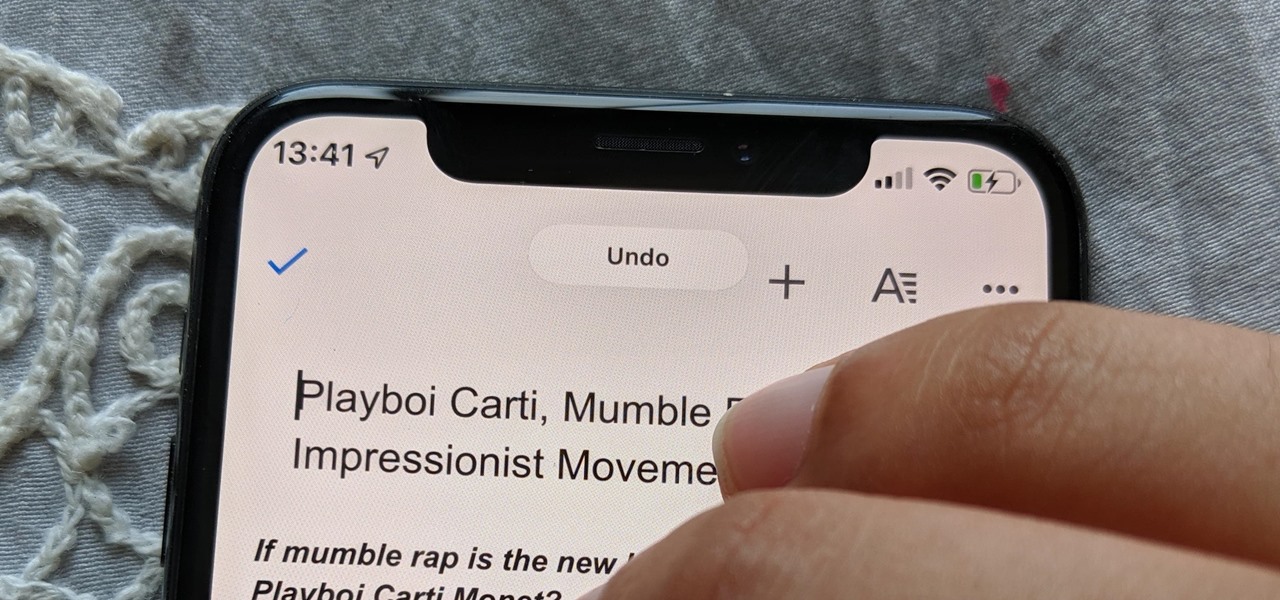
Between sending iMessages, jotting down notes, and crafting emails, you do a lot of typing on your iPhone. No doubt, you've been in the middle of an important task when everything comes to a screeching, obtrusive halt, where a rogue "Undo Typing" pop-up forces you to close it before continuing with your typing. Don't put up with the BS anymore — here's how to stop it.

Spreading your reach to new audiences on Instagram takes time and effort. It's not only about taking unique photos and curating an exciting feed. You should choose the time of day wisely, connect with popular brands, and take advantage of hashtags. Unfortunately, hashtags can make it seem like you're trying too hard, but you can make them invisible — in stories, at least.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

Shake to undo is now the worst way to take back what you just typed on your iPhone. Among the many changes in iOS 13, Apple has updated text gestures, including how you select a word, sentence, and paragraph, copy and paste text, and undo and redo what you type.

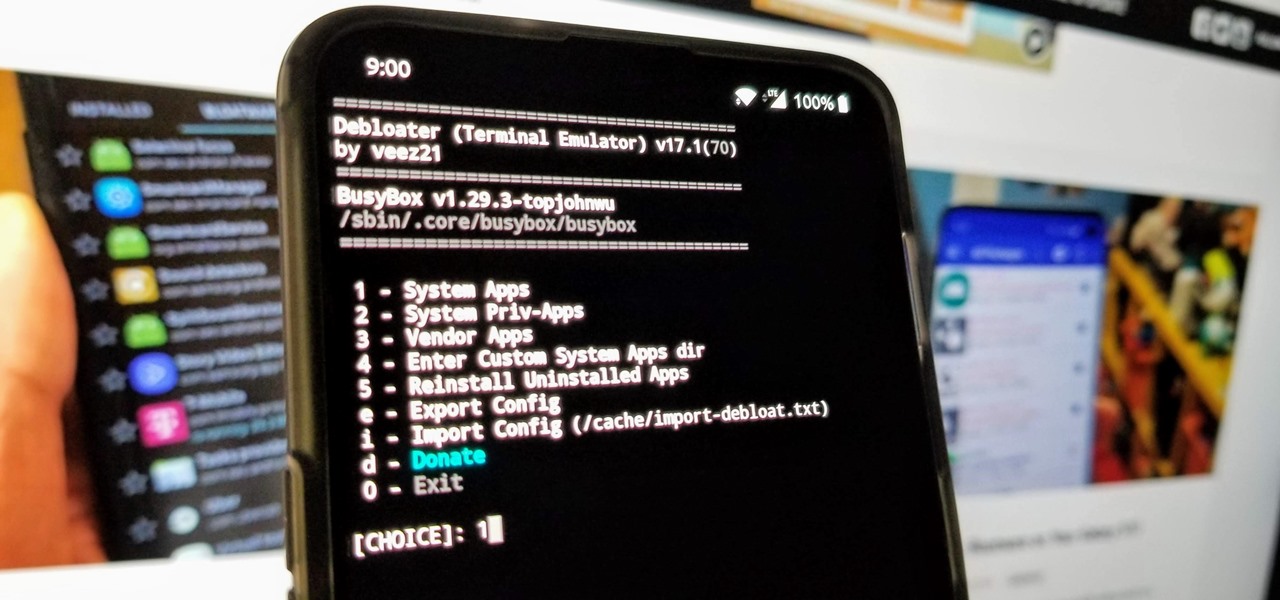
When you get a new phone, the last thing you want to deal with is a ton of preinstalled programs staring back at you. They not only clutter your home screen with apps you'll probably never use, but they're also wasting space on your internal storage and potentially draining battery. To truly uninstall them, you'll need root — but even then, it can be hard to pin down all the apps that should be removed.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.

In its never-ending quest to innovate its flagships, Apple's newer iPhone models with Face ID do away with the iconic Home button present since the first iPhone back in 2007. That means screenshots, force-restarting, switching apps, Apple Pay, and the home screen all work differently on the iPhone X, XR, XS, XS Max, 11, 11 Pro, and 11 Pro Max. One of the more important aspects, Siri, is also slightly different.

The keyboard is one of the biggest weak points of iOS devices, in part due to the lack of an option to add a number row. Fortunately, there is a way to quickly switch between the numeric and alphabet layouts on your iPhone or iPad's keyboard.

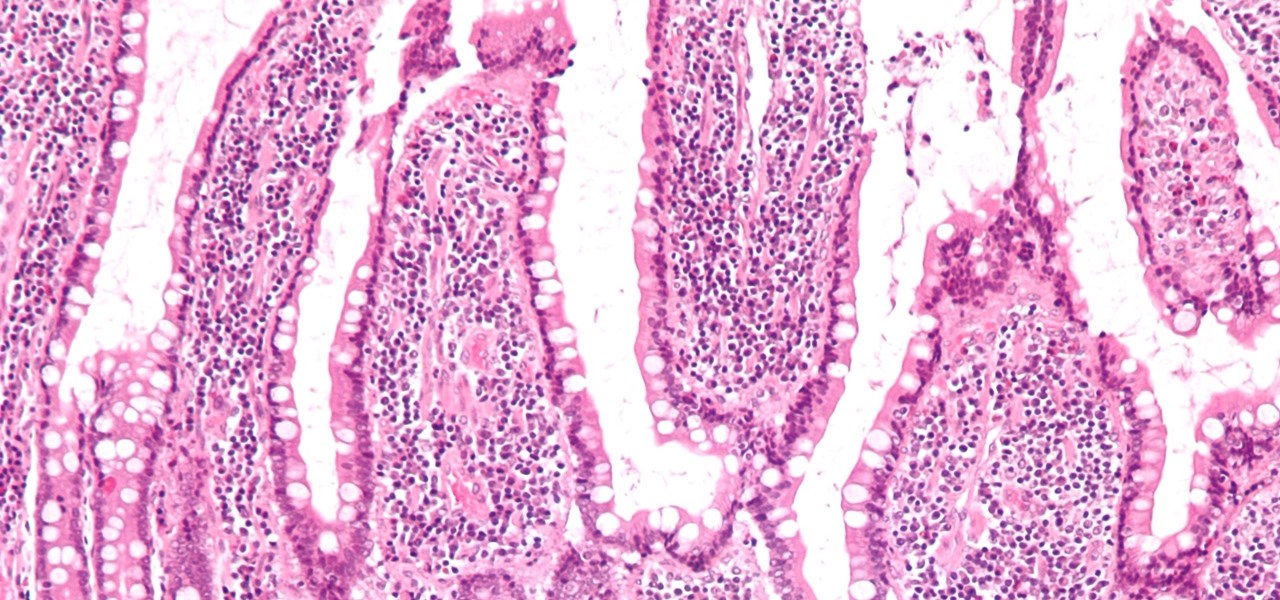
If the all the fingerlike projections in our gut were flattened out, its surface area would be 100 times bigger than our skin's. It's so large that the actions of just a small part of it can impact our health. A new research study has found that enterochromaffin cells in the intestinal lining alert the nervous system to signs of trouble in the gut — trouble that ranges from bacterial products to inflammatory food molecules.

A recently confirmed polio outbreak in Syria is connected to low levels of vaccination, worsened by conflict. It is the first confirmed incidence of polio in Syria since 2014. Before 2013, the last case of polio in Syria was in 1999.

Back in May 2017, Apple filed a patent application for a way to communicate with Siri by writing her questions and responses using iMessage. While that didn't make it into iOS, thankfully, something even better did — a way to ask Siri things with the keyboard directly in the Siri interface. This works in iOS 11 and later.

Could your fever, body aches, cough, and sore throat be the flu? Soon, finding out may not involve a trip to the doctor.

The hatred is almost universal—by now, even late night TV hosts are bashing Apple's move to ditch the headphone jack in the iPhone 7. It's not like the disdain is baseless, either, because there are plenty of problems that come along with removing the iPhone's only analog sound output.

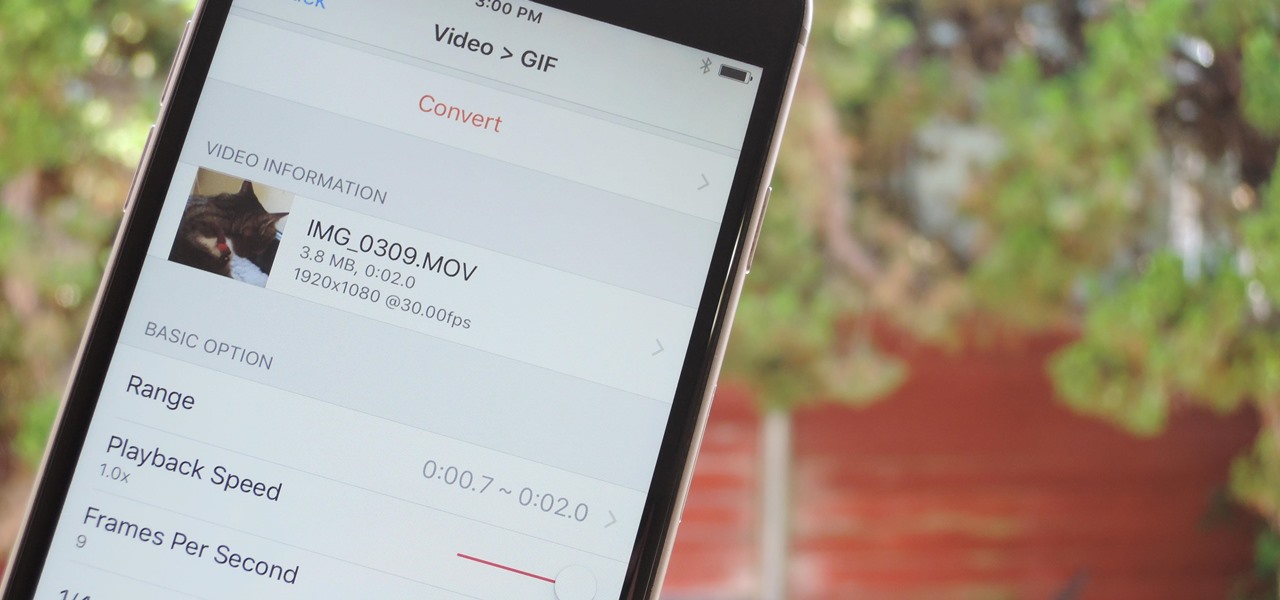
The internet has officially been taken over by GIFs—they're everybody's favorite method of communication these days, and nary a meme would exist without them. But even with the abundance of GIF-sharing websites, and even GIF keyboards, we're still a bit lacking in regard to creating GIFs on a mobile device.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

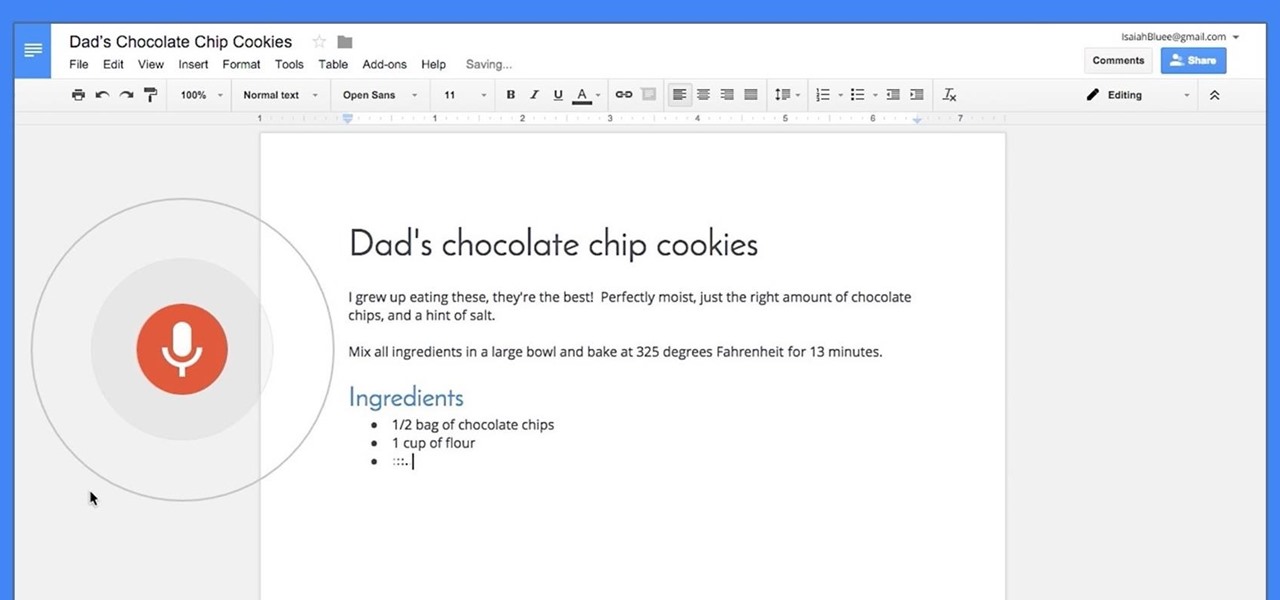
Google launched voice typing for Google Docs last Fall, and followed that up about six months later with voice commands that let you format and edit text as well. You can do things like select text, apply format settings like alignment and headings, and add and edit tables—all with your voice.

Google is rolling out an update for Google Drive that streamlines the online file storage/sharing app, and finally gives you access to the Trash folder that had only been available on the desktop version.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Facebook just keeps coming up with more and more diversions to help you ignore your responsibilities. At least this diversion is a little more intellectual than most of the other things that can easily distract you on Facebook.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

Hello there Nullbytes, In my previous tutorial found here,

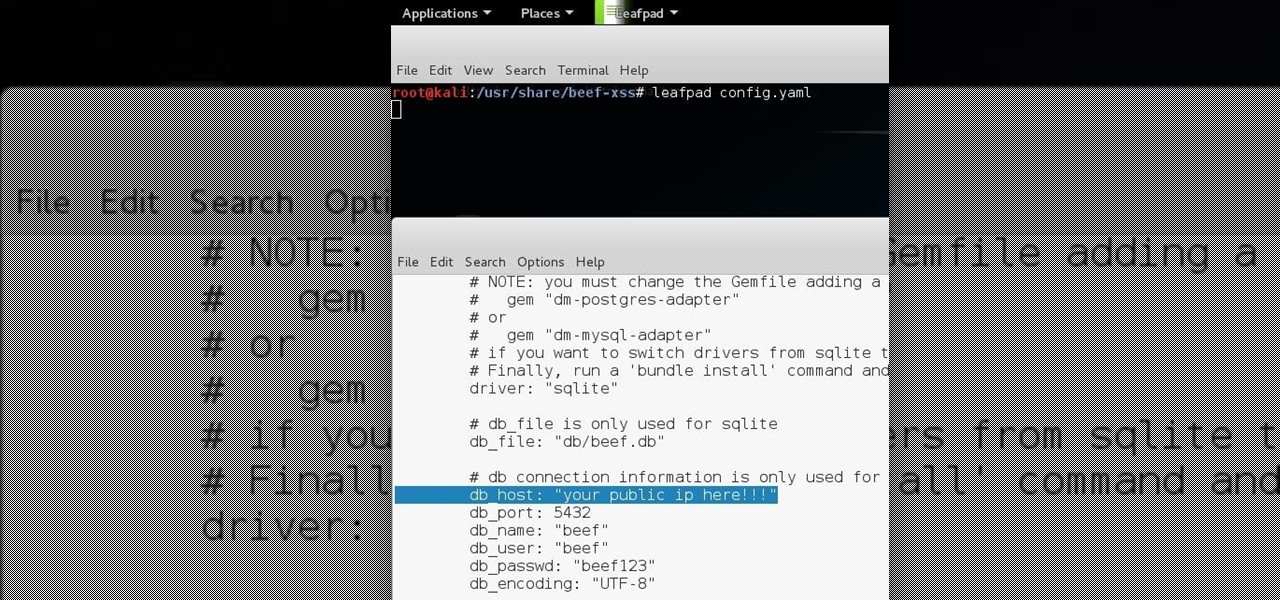
Hello all Just thought id share how ive managed to get beef working over the internet.

The notification light on phones and tablets is slowly disappearing. The once staple feature is now only found on a few devices, and a bevy of other notification systems have sought to fill the gap. The most popular of these systems is Ambient Display, which has grown in popularity with OEMs over the last couple of years; even Google's own Nexus line of phones have made the plunge.

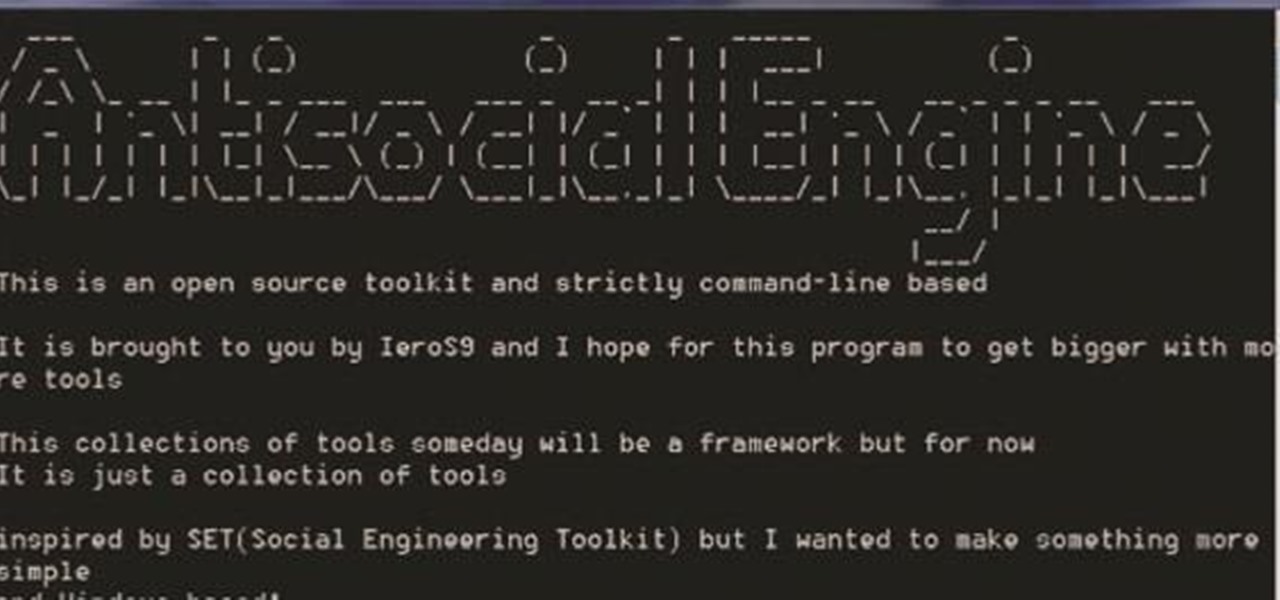
A.E Hi again this is my second post on nullbyte. The first one was on how to make a remote screenshot captor, now I will give you a presentation for a project of mine(I have named It Antisocial Engine) that It is not something extraordinary but will help many guys.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

In python, or any scripting language for that matter, there are certain things that you will carry with you throughout your entire scripting career. Some of the most basic things that you will keep with you are output, variables, and their value types. We'll start by going over output, then cover variables and their types. So, let's get started!