What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!
Video: . This video explains how to install Android OS on a PC using VirtualBox. How to install Android OS on a PC Using VirtualBox.

The easiest way to change your mouse pointers using Deviant Art artwork is explained in this informative and easy-to-follow video.

Don't go to that rave tonight without the proper knowledge of glowsticking. Learn the basics right here from TheNeonColorSwitch. This two-part tutorial will show you how to freehand glowstick and color switch with four sticks.

One of American Apparel's most famous articles of clothing for women is their Le Sac dress, which is no ordinary dress. It's simplistic look mocks it ingenious design, which can be shaped, formed, mutated, tie, and tucked in at least TWELVE different ways to create a different dress for each day of the week. The Architectural Mini look is just one of the ways to style it, and this video shows you exactly that. Use this art deco style for a sexy, architectural inspired halter look.

Can you believe this dress? American Apparel have outdone themselves again! A dress that's not just "one" dress, but at least "eight" dresses. The Le Sac dress is a marvelous article of clothing because it can be worn every day of the week… without looking like a hobo. It's a different style each day, with at least TWELVE different styles. And there's even a look for you dominatrices out there, a super sexy and daring S&M style Dominatrix look. See how easy it is!

American Apparel is famous for selling articles of clothing that can be worn in multiple ways. Their latest creation is the Le Sac dress. This dress can be tied and twisted all over the place to come up with TWELVE or more styles! You can wear this outfit every single day and everyone would think you were in something new. So, if you are looking for a sexy, Greek-inspired off the shoulder look, check this official tutorial out for the Grecian look. Learn how to wear your Sac and look amazing.

The fine folks at ITS Tactical made this detailed tutorial on how to make a two-piece lock pick set out of only a few paper clips and using only a multi-tool in the construction. The host begins by demonstrating how to construct the pick, then how to use it on a real lock. It is not as easy as using a real lock pick, but will still work. As the host emphasizes at the beginning of the video, these picks are only to be used in emergency situations, and NOT to break into other people's homes wil...

We've all seen the breathtaking, colorful photos of the Eagle, Egg and Cat's Eye Nebulae. You may not recognize them by name, but you've seen them, whether in astronomy textbooks, magazines, websites, album covers, or tee shirts. They are some of the most striking photographs ever taken from the Hubble Space Telescope (HST).

Some people may think that vegan and vegetarians do not eat protein. This how to video is an informative episode about protein, some easy protein snacks, and a comparison between ground beef and textured vegetable protein. Watch and learn how to get protein into your diet when you are a vegan or vegetarian.

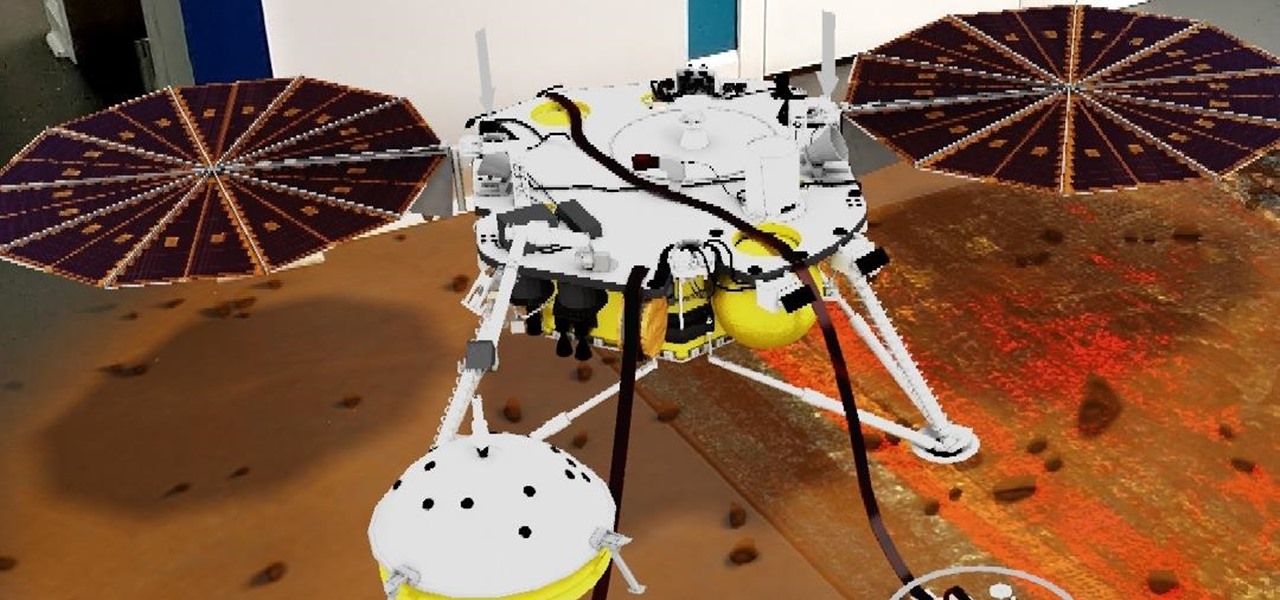
In the latest installment in its burgeoning augmented reality journalism practice, The New York Times is bringing its readers closer to Mars and NASA's latest spacecraft set to travel to the red planet.

The internet is chock-full of fun and interesting content, but there's only so much time in the day for consuming it. That's when saving webpages for later comes in handy. If you don't want your bookmarks and favorites folders to clutter up fast, consider using the "Reading List" feature built right in Safari on your iPhone.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.

Hello, everyone. If you've been following my recent articles, you'll know that I've been rather busy lately working on a project, a rather large one. I've been working with Pheonix750 and Ciuffy to build the Null Byte suite of tools! I got the green light from our admin a while ago, and we've been developing like mad ever since! I'm very excited to launch this project. So, let's start by explaining what it is...

Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system.

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

For all of the flak that it catches, Wikipedia is still a great source of information. Contributors take their work very seriously, so the vast majority of information is cited, and the site serves very well as a starting point to learn about a new topic.

We've all had to write an essay or research paper at some point, and undoubtedly the hardest part about it is always the citation, right? If you ask me, it's a huge pain in the arse. Even more so if you're gathering your facts from a huge variety of sources.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

These days, news papers, online editorials and magazines are filled with news on Iran and Syria. Of course, that is expected, as such sources need to stay current to stay in the game. My concern is that most of these articles talk about what to do about these situations.

You start the Swedish back massage first by putting lotion in your hands to warm it. You first use long fleeting strokes and work your way into shorter spinal column strokes (remembering of course to keep even pressure). You then move to the petrissage stroke running your hands smoothly interchanging the openness of your fingers alternately all across the back. You then go back to work on the trapezes remembering to push outward from the spinal column. The video also brings up the concept of ...

This is a great instructional video on how to pipe cake lilies, morning glories and roses. In this video you can learn the techniques on how to decorate cakes. It shows you how to pipe flowers such as lilies, morning glory, roses, leaves and stack cake. You can learn almost anything you need to know in just 10 minutes by watching this informative video. This teaches you to decorate cakes beautifully. This Pipe cake lilies is becoming more and more popular these days. The decorating methods ar...

If you just got done watching the video tutorials on the "human skeleton structure," then this is your next step. Check out this educational science video series on the neuroanatomy of the human body.

If you've ever been to a Marie Callender's restaurant, then you know their chicken pot pie is the most popular and most often requested dish. That's because chicken pot pies, while a rather simple concept, contain just enough bready goodness, veggies, chicken, and sauce filling to get you full and way satisfied.

Many, many Americans cannot do a single pull-up. That is just the state of our society. And it means that these people, if faced with a survival situation where they are dangling for a ledge or need to scale a building, are less likely to survive than they could be. This video will teach you how to develop your pull-up motion and techniques to improve your strength and survival ability.

This is a demonstration of making a hand tied bouquet.Keep all the required articles nearby on the table.Take a few stems of lemon grass and bind them with a wire to form a single bunch.Tie the aspedestra leaves in a loop with wrapping a wire to the stem.Now take the stems with single flower like movie star roses or carnations or iris or tulips pluck or cut the loose petals.Now hold one of the stems loosely in the left hand,now with the right hand place the second stem so that the flower is o...

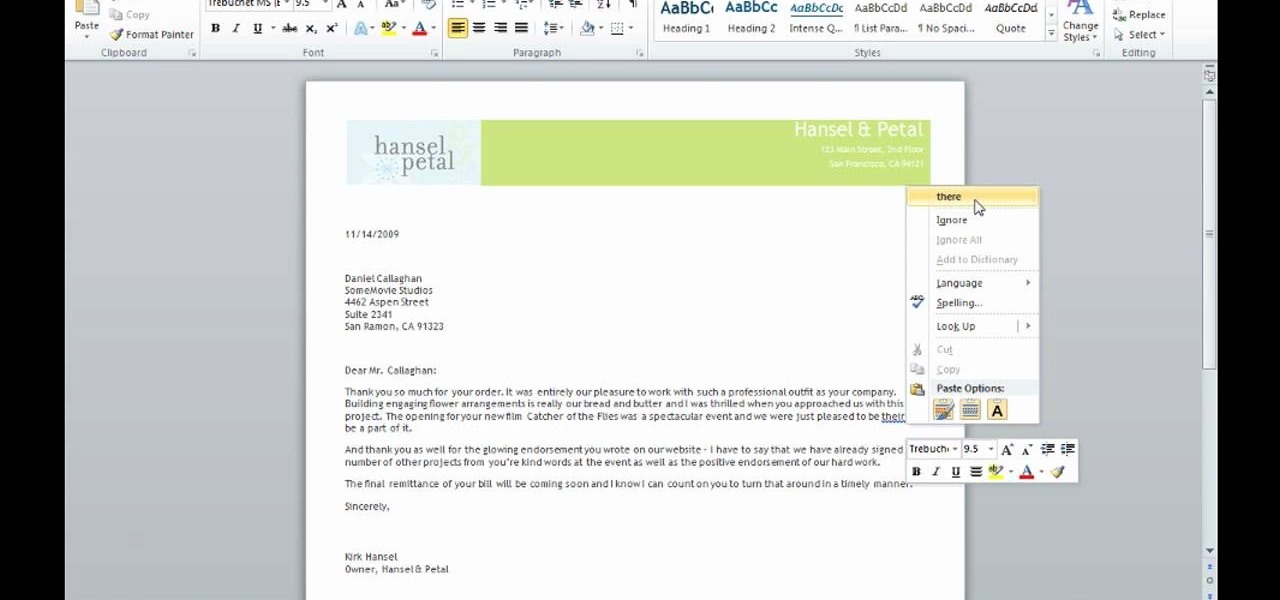
This video tutorial is a quick explanation of the ins and outs of spell and grammar check when using MS Word 2010. One of the main things highlighted in this video is that unlike previous additions, this year's version offers more contextual correction. For example, when the word their was used in an article, it was spelled correctly but used in the wrong context. The spell and grammar checker will underline this to let you know that it is incorrect. If you hit the spell and grammar check but...

Sometimes it can be difficult to find information essential to a citation on a webpage, like an author or a date. Here are some steps you can take to make up for this lack of information.

MAKE and Kipkay brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

MAKE and Kipkay brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

MAKE and Kipkay brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

A seasonal how-to for creating easy, perfect paper snowflakes. This is a fun Christmas craft this holiday season. To begin, start with a square sheet of paper. Fold the sheet corner to corner. Fold again to create a new triangle. Cut like crazy! For all sorts of patterns and ideas check out this accompanying article:

Plagiarism is a serious offense, even if you are copying from the web. With this tutorial, learn how to cite websites properly using MLA format and avoid any trouble.

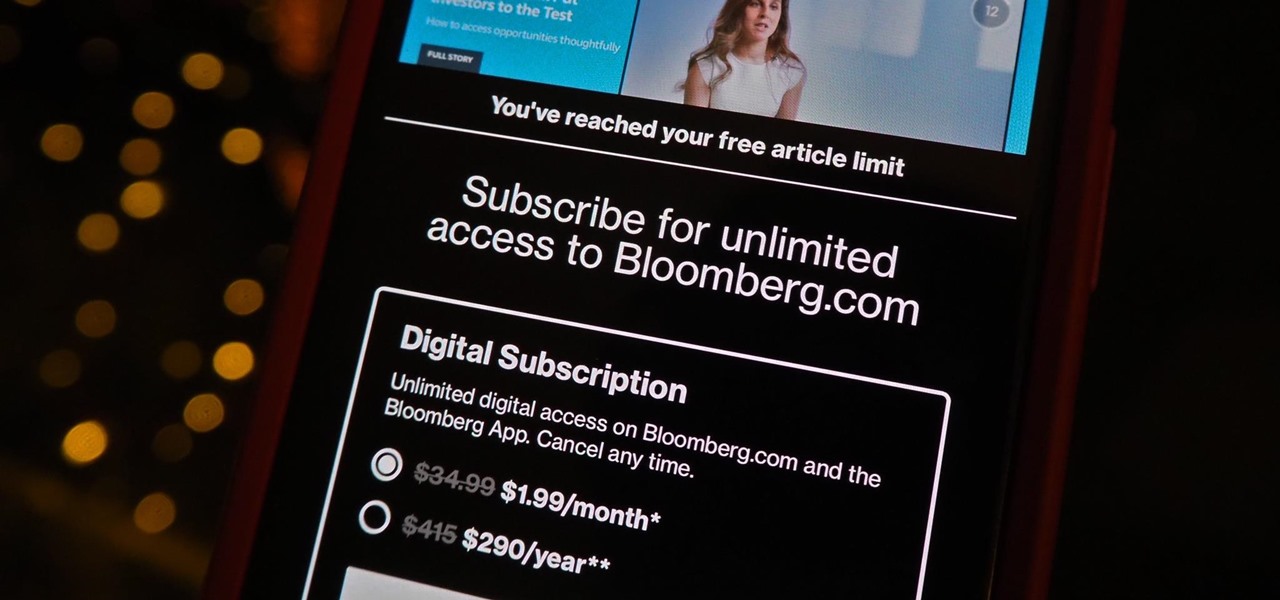
One of the most aggravating things that can happen on Facebook, Twitter, and other social media apps is when a friend shares an exciting story, and a paywall prevents you from reading any of it. You could pay for a subscription to unlock it, but there are so many news sites that it can be both confusing and expensive to spend money on all of them.

You're halfway through reading an article on your iPhone, when the display just turns off. Frustrated, you open the article again, only for the display to go black again. You shouldn't have to keeping touching the screen to keep your iPhone from going to sleep. Luckily, you can delay or even stop your iPhone from doing so with just a few taps.

Why would Magic Leap, a company preparing to launch its first augmented reality headset this year, need a developer for iPhone and iPad apps? It's not as crazy as it sounds.

Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...