The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

We all know the internet isn't exactly a safe place. While plenty of its users are innocent and kind, you won't last long unless you treat every new screen name like a criminal (we're all this cynical while surfing the web, right?). Well, that cynicism is proven correct today, a post on Medium uncovered a group of scammers on the iOS App Store that are costing victims up to $400 a month.

Onshore, or on a boat, have you ever wondered what swims below in the dark water? Using standard equipment and a new process, marine scientists can now get a good look at what is swimming by—just by analyzing the water.

Welcome back to this series on making physical objects come to life on HoloLens with Vuforia. Now that we've set up Vuforia and readied our ImageTarget and camera system, we can see our work come to life. Because in the end, is that not one of the main driving forces when developing—that Frankenstein-like sensation of bringing something to life that was not there before?

Dutch filmmaker Anthony Van der Meer published his 2015 thesis short from Willem de Kooning Academy in South Holland online in December 2016. It's a brilliant piece of work that managed to be touching, alarming, and informative at the same time. His documentary, which already has over 6 million views on YouTube, covered the journey made by a stolen smartphone and how the theft and ensuing tracking affected all parties involved.

I fry foods a lot. A LOT. We're talking wings by the dozen here. As a result, I go through a ton of frying oil. Now, frying oil isn't the most expensive ingredient out there, but it adds up when you fry regularly. Of course, I always reuse my oil, but straining it can be a huge mess and it gets to a certain point where enough is enough. It's time to start fresh.

If you're standing in a foreign city, surrounded by signage in a language you don't understand, you won't suddenly be able to read it. But with a clever feature in Google's Translate app, your smartphone can.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

Welcome back, NB community, to my series on sorting. I introduced in my last article the concept of complexity. When I say complexity, I'm talking about time complexity.

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

If Android is all about options, then iOS is all about new features. Every year without fail, Apple announces a cool software component that brings something new to the table, and this year was no different.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Welcome back! Sorry for being so quiet, I've been rather busy with this project lately! Anyways, in the last iteration of how to train your python, we covered lists. Today we'll be introducing iteration and the two loops python has to offer, for and while. Also, we'll be covering a couple general use functions. So, let's get started!

Editor's Note: The research described in the article below has been criticized and any conclusions based off this research should be examined with a skeptical eye. The article has been edited to reflect these issues.

Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean just the basics, I mean to make an extensive series that takes it all the way from "Hello, World!" to popular third party modules, and everything in between!

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

There are a bunch of new and interesting features packed inside of Windows 10, but one of the most exciting ones is the Microsoft Edge web browser, the long-awaited replacement of Internet Explorer.

Hello Hackers/Viewers, It is a new day, and you might be thinking, It is so boring, why not try to be cool with computers in front of my friends? That is why, I have made this tutorial to make fake viruses using notepad to look cool!

Apple has once again improved functionality of Siri, their personal voice assistant for iPad and iPhone, in iOS 9—and this update is a big one. You can now use Siri to find photos based on location and date, set up contextual reminders, find your friends and family, and more.

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Are you stranded in a hotel room with no kitchen, but craving the comfort of a home-cooked meal? Fear not, I have found some interesting ways to cook food without the luxury of an oven, stove, microwave, or even a toaster!—also known as "hotel room cooking."

Since its creation, Arduino has been growing exponentially more popular as DIY enthusiasts and Makers alike realize its potential. As new versions of the device are released, many easy-to-use peripherals are showing up on the market also.

Back in the day when computers relied on CRT monitors, having a static image displayed for too long actually resulted in the image being burned into the screen. For this reason, screensavers were developed, which display animated images in constant motion to prevent burning in when you stepped away from your computer.

Fish is delicious, and as the Harvard School of Public Health points out, incredibly good for you. There are many studies that show regularly consuming a couple of servings of fish per week can help prevent heart disease and may well reduce your chances of stroke, depression, and getting Alzheimer's. After all, there's a reason why fish is called "brain food."

If you have a hard time remembering what you've just read on your iPad or Kindle, try changing the font next time. The typeface you use to read books, newspapers, and online articles is either hurting or helping your memory, and you'll be surprised which ones are killing your brain cells.

You've got to be sick of it by now. Those meaningless and unsatisfying articles, lists, and videos you were duped into clicking on because their headline made them impossible to resist.

Yesterday, I wanted to remove BackTrack from my system and install Kali, and at the same time didn't want to damage my Windows 7 or my hard drive. I searched a lot of articles, but almost all of them wanted me to have a backup Windows 7 CD, which I don't possess.

In today's dog-eat-dog world, every minute matters. Whether you're in school or working for the Man, a huge amount of your day is consumed by tasks, assignments, and other kinds of work. Then there's the time you spend playing video games, watching TV, or screwing around on your Samsung Galaxy S3.

Seemingly lost in the fanfare of the numerous features and specs of the Nexus 5 were a few highly innovative and handy add-ons—a low-power step detector and step-counting sensor—useful for tracking fitness data.

Editor's Note: The claims by Vani Hari which were originally detailed in the article below about azodicarbonamide were unscientific in nature. This article has been updated to reflect that and provide more scientific context on the issue.

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

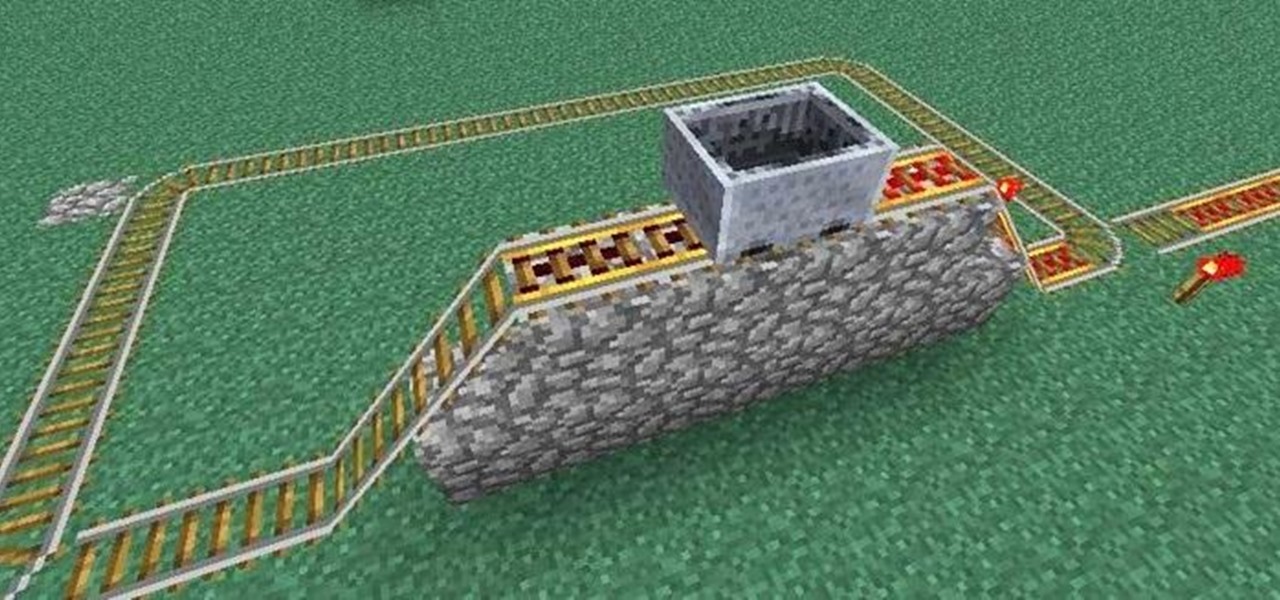
What's nice about Minecraft 1.3 is that it makes minecart stations so simple. Before, you needed redstone and buttons and powered rails in order to make a good minecart station. Now you hardly need anything at all! That said, if you want to be snazzy, all of the minecart stations we covered in this earlier article are still completely functional. You may also want to check out this article on how to make empty minecarts come back to you, if you want some extra bells and whistles.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...