You've gotten used to your brand spankin' new Nexus 7 and finally have a feel for Android, but now you want more features. Well, user Juan Mercator was in that predicament, and asked how to install the ever popular CyanogenMod ROM on his Nexus 7 over on our Nexus 7 SoftModder forum.

Nikola Tesla is one of the most tragic figures in the history of science, a history that is practically filled to the brim with tragic figures. Francis Bacon, a 16th century philosopher and scientist, caught pneumonia and died because he was trying to stuff snow into a dead chicken. Marie Curie died as a result of her long-term exposure to radioactivity, and her papers from the 1890s are too radioactive to touch without protective gear to this day.

The upcoming web series "Crypto-Historians" does for cryptohistory what Indiana Jones did for archaeology. For those who don't know, cryptohistory is the study of supernatural or alien elements throughout history, and yes—it's a "real" field.

Particles, such as electrons, have a property called spin which can be measured at any angle, but when measured always results in one of two answers—up or down.
If you have a Samsung Galaxy S3 or Galaxy Note 2, you might not have noticed it yet, but there's an annoying little bug that centers around your clipboard. If you tend to do a lot of copy/pasting on your device, you've probably seen it happen—your phone crashes.

It doesn't really matter what kind of cell phone you have—battery life is one of the most important features for any electronic device. We've written tons of articles on how to get better battery life from your Android, iPhone, Kindle, and more, but we've never really covered Windows Phones before—until now. The Nokia Lumia 920 and other devices running Windows Phone 8 suffer from battery problems just like any other mobile device. So, if you've got one in your hands that can't seem to make i...

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

As a former English major, I have a love/hate relationship with many books. And when I saw that this NFC-enabled charging dock project included a little book mutilation, I was suddenly more interested. Now, for those of you who have nothing against books, this is still a great project to add some style to your tech devices.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

This most recent school shooting, one of the worst in history, has devastated our country. That such an act can be performed not by a begrudged child, but by one or more adults, is nearly unthinkable.

Every year, Black Friday gets a little more insane. People get up at ungodly hours, wait in lines forever, and get into some of the most ridiculous fights you've ever seen. All in the name of saving some cash. Everyone loves saving money, but without a game plan, you could end up missing all the good deals and going home with nothing. Luckily, the Internet is here to take some of the stress out of holiday shopping. With these sites and apps, you can find out about all the best deals before yo...

Want to take vibrant photographs like this one? You won't find this filter in Instagram, and that's because it's a little more difficult than just slapping a digital filter on a solo photo. The extra RGB colors are created using a special strip device called the Harris shutter, invented by Robert Harris of Kodak.

You've had your Xbox 360 for a few years now and your game collection is pretty extensive. Maybe it's not that extensive, but it's still substantial. Now imagine that you live in Europe and you're moving to the United States. I don't know why—maybe your dad got a job offer. Don't ask me, ask your parents. They're the ones that are making you move. Anyways, as most Xbox users know, games are coded by region. Games that work in Europe might not work in the United States. Does this mean you shou...

Many of us in the Steampunk community have pets that we love and cherish, myself included, and we want those pets to share our joy of Steampunk. In reality, they couldn't care less, but for some reason we still love to dress them up. Their reactions usually range from bemused acceptance to temper tantrums, but the awwwws we get from onlookers usually makes it worthwhile.

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

Apple's iTunes Match service is a great feature for people who have large libraries or want to sync their music across a lot of different devices. It lets you store any song in your library that exists in the iTunes Store on the cloud, even songs you imported from CDs, and even improves the quality of some of them. But, like any new service, it's not without its problems, and the fact that it costs $25 a year makes those problems seem even worse. Among the issues that users reported, unmatche...

There's definitely a lot of new things to get used to in iOS 6, with over 200 added features, but which ones stand out about the rest? Well, it all depends on what device you're using. Some features will only work on newer models, but most of the hidden features are accessible to all.

Tripwires are a new mechanic released in Minecraft 1.3, and people are still trying to figure out how best to use them. Minecart returns are a great idea, but what about traps?

War leaves a lot of stuff behind. Torn families, delegitimized institutions, mass graves, and unexploded ordinances litter the post occupation landscape. Whether or not you have driven the imperialist out, or are still in the phase of armed resistance, you will need the ability to safely diffuse bombs. My bomb defusing Silvia-bot can do it all. She can catch grasshoppers, cut wires, collect samples, tase enemies and even play chess! Materials

There's been a lot in the news lately about tracking devices, and it's been pretty much all bad. They can be useful if your car gets stolen, but if you weren't the person who installed it, chances are you don't want it there. Just type "GPS tracking device" into Google and on any given day you'll find an article about someone who got busted by one of these things. Even if you don't have to worry about getting into trouble, you still don't want people following you. Here's how to make sure you...

Have you ever felt like you wanted to totally annihilate someone in Minecraft with a machine gun? Yeah, me, too. Thankfully, you can!

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

If you loved The Da Vinci Code by Dan Brown, then listen up— there's been a new discovery found hidden within Leonardo da Vinci's most famous painting— the Mona Lisa.

While the iPhone world's attention might be fixated on Apple's upcoming iOS 14 and all of its new features, it's still in beta. What's not in beta anymore? Apple's latest iOS 13 update — iOS 13.6 — which dropped on July 15.

Does TikTok scare you? Trust me, I get it. It's a strange, unfamiliar place to those of us not accustomed to its ways, populated by teenagers and college students with their own subcultures, memes, and humor. But here's the thing: TikTok has something for everyone, you included.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

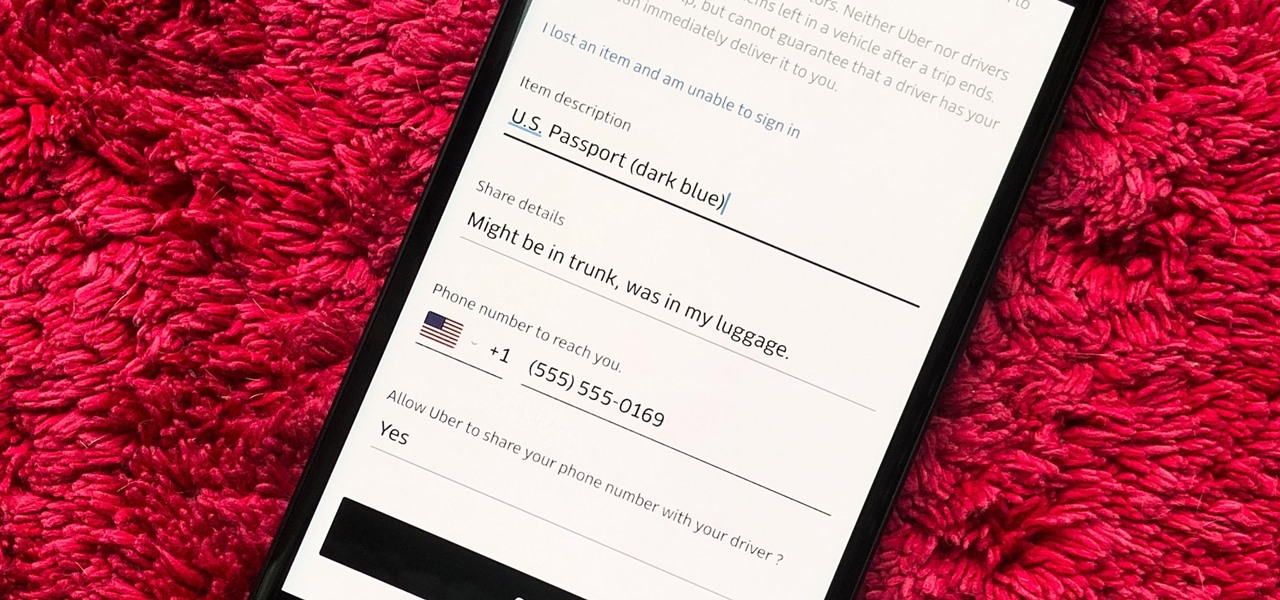
You would think that recovering your smartphone or another important item that you leave behind in an Uber ride would be a simple process, but it can actually be a pain in the ass. You have to find out how to report it to the driver, hope the driver is honest, pay a fee, and contact Uber directly if none of that works. But we're here to help make this process as easy as possible for you.

WhatsApp is the go-to messaging app for millions worldwide and its easy to see why. The app can be considered the Swiss Army Knife of texting thanks to numerous features like Group Chats and Status Stories, in addition to striking a great balance between ease of access and overall security.

Twitter's official iOS app is adequate if you're not much of a tweeter, but if you are, there's a lot of useful features that are missing. Luckily, there are plenty of free Twitter clients available that you can use on your iPhone. These third-party apps have features such as customizable interfaces, post scheduling, and different browser options for opening links, to name just a few.

So, you've lost your Apple TV remote. Maybe it's busted. What are you supposed to do now? You could go out and buy a new one, but they're expensive if you have a newer Apple TV with a Siri Remote, and wouldn't you rather spend that money on a movie? You might be without a working dedicated remote, but you likely have the next best thing already in your pocket.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

When you want to post a breathtaking landscape or picture-perfect portrait that you just took with your DSLR camera to Instagram, Facebook, or some other social platform, there's an easy way to do so — even if you don't have a computer handy, which is typical when you're out and about.