
How To: Display lightning FX & fog into back of tombstone
Check out this demonstrational video to learn how to create lighting FX and fog behind the back of a tombstone that's a great prop for Halloween sets.


Check out this demonstrational video to learn how to create lighting FX and fog behind the back of a tombstone that's a great prop for Halloween sets.

In this fun and informative video, we show you how to walk in high heels. Video: .

Here's a very informative video for those of you learning to drive in the Nottingham and surrounding areas. We look at what to do when you get to the end of a road and you can't see what's coming from the sides. Keep slow so you can look, assess, decide and act upon what you see. You have to wait at a give way line and definitely stop at the stop sign. It's the law.
As informative as they can be, the new app icon badges and unread counts on the Galaxy S9's home screen are a little redundant since Android already has a notification center. If you'd rather not have these little dots overlaid on your home screen icons, there's an easy way to disable and hide them.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...
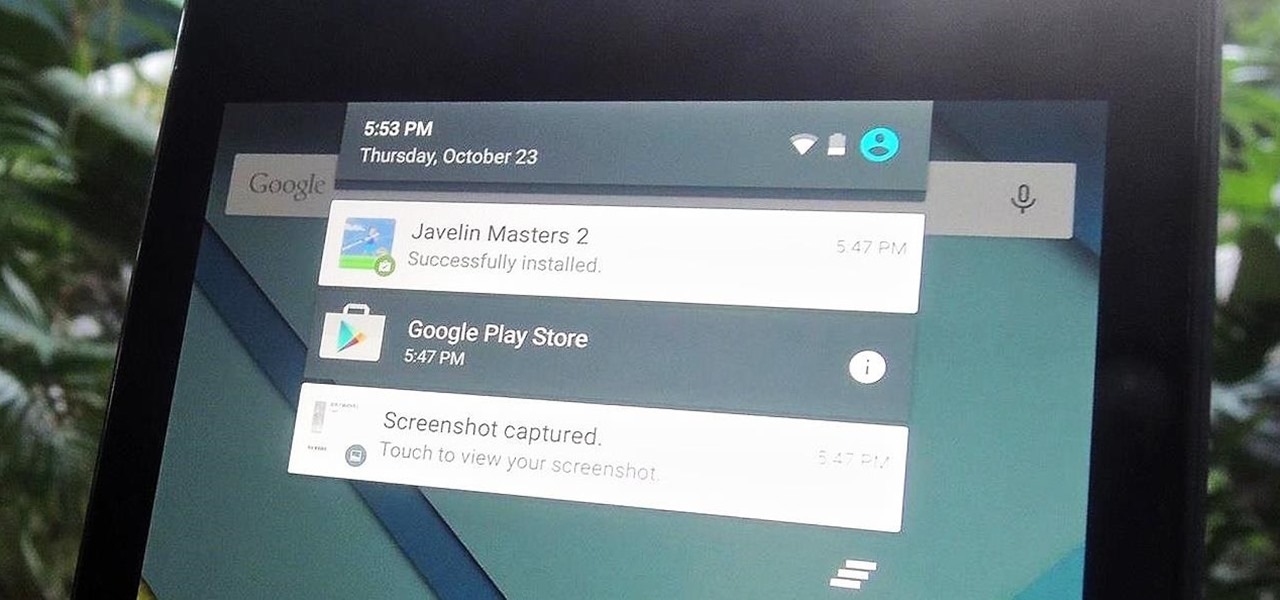
Notifications sometimes come in bulk on Android—especially after booting up. While some of them are helpful or informative, most can be immediately dismissed as soon as they come in.

With the Samsung Galaxy S5 all but assured to be showcased in a just a few weeks, we've got our hands on some fresh details of the upcoming flagship device.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

After winning the 2015 FIFA Women's World Cup, the USA Women's National Soccer Team is ready to defend its title in the 2019 tournament.

After getting its start with models of augmented reality planets that serve as targets for augmented reality experiences, AstroReality is diversifying its portfolio by paying tribute to one of the space agencies that made its products possible.

If you have yet to receive your invitation to next weekend's royal wedding in the UK, then you can still experience part of the pomp and circumstance in augmented reality courtesy of ABC News.

Although The New York Times may have won the race in terms of presenting coverage of the 2018 Winter Olympics through augmented reality first, The Washington Post is nevertheless working to compete in AR in a different way—via gaming.

Earlier this month, John Oliver spent a segment on Last Week Tonight explaining native advertising, a practice followed by many online media outlets such as BuzzFeed, The New York Times, and VICE, which combines editorial content along with sponsored advertisements.
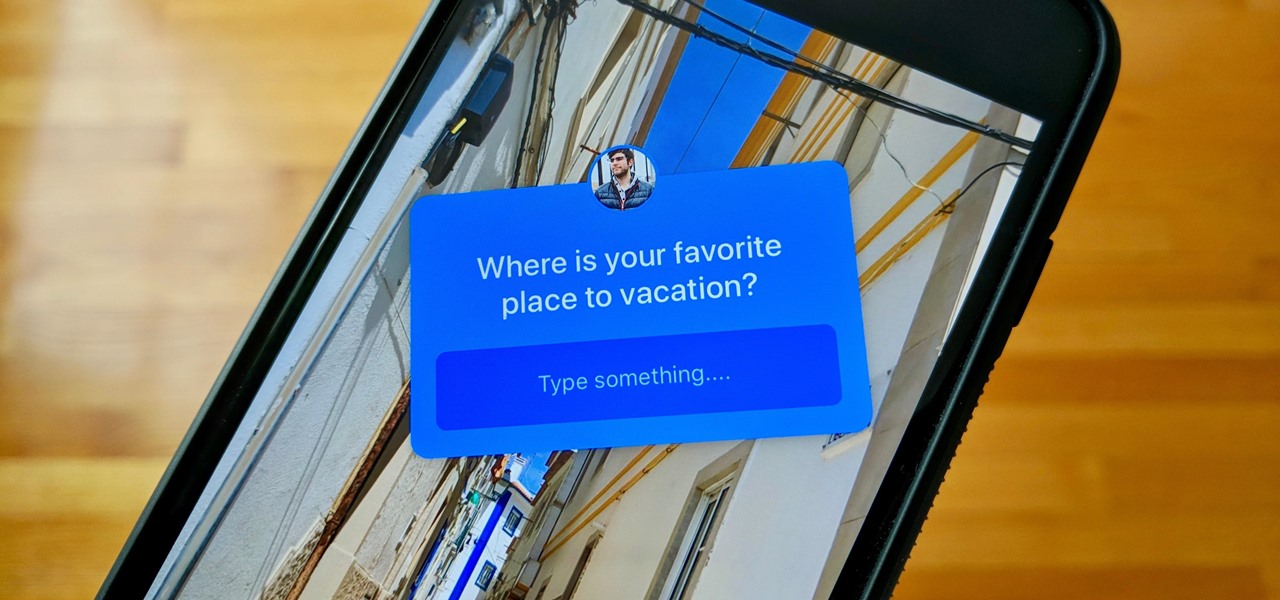
Your Instagram followers deserve to be heard. Whether through polls or DMs, Instagram offers your followers a unique way to share their thoughts and opinions with you on any subject you can think of. Now, the social media giant is expanding these options with the introduction of a new "Questions" sticker for your stories.

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

Here at Food Hacks, we're very fond of finding ways to regrow food. That means taking things like carrot tops and leftover bits from garlic, onions, chives, and other herbs and aromatics to create mini reusable herb gardens.

As Microsoft unveiled their new Windows Phone 8.1 software update yesterday, undoubtedly the most memorable takeaway was their showcase of Cortana. Competing directly against Apple's Siri and Google's Now, Cortana is Microsoft's entry into the digital voice assistant fray, and the official replacement to their search app.

There are a number of reasons why you might want to trick a web server into thinking you're on a different operating system (OS) or web browser. One might be that you want to test the mobile version of your website from your computer. Or perhaps for some reason a website is restricted to a certain OS or browser and you wish to circumnavigate that barrier. Today's guide shows you how to do just that!

Google Drive has been a gamechanger in the business world. First launched in 2006, Google Sheets has become much more than an alternative to Microsoft Excel. The powerful spreadsheet program is a boon for efficiency that's accessible wherever you have an internet connection—or when you have time edit offline.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

IFTTT is an application that allows you to automate certain tasks on your iPhone or Android. It can communicate with a myriad of apps and services on your phone by creating applets that perform actions automatically — actions you'd normally have to do manually. Finding those applets, however, can be a little difficult.

Welcome back to this series on making physical objects come to life on HoloLens with Vuforia. Now that we've set up Vuforia and readied our ImageTarget and camera system, we can see our work come to life. Because in the end, is that not one of the main driving forces when developing—that Frankenstein-like sensation of bringing something to life that was not there before?

Dutch filmmaker Anthony Van der Meer published his 2015 thesis short from Willem de Kooning Academy in South Holland online in December 2016. It's a brilliant piece of work that managed to be touching, alarming, and informative at the same time. His documentary, which already has over 6 million views on YouTube, covered the journey made by a stolen smartphone and how the theft and ensuing tracking affected all parties involved.

Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...

Fish is delicious, and as the Harvard School of Public Health points out, incredibly good for you. There are many studies that show regularly consuming a couple of servings of fish per week can help prevent heart disease and may well reduce your chances of stroke, depression, and getting Alzheimer's. After all, there's a reason why fish is called "brain food."
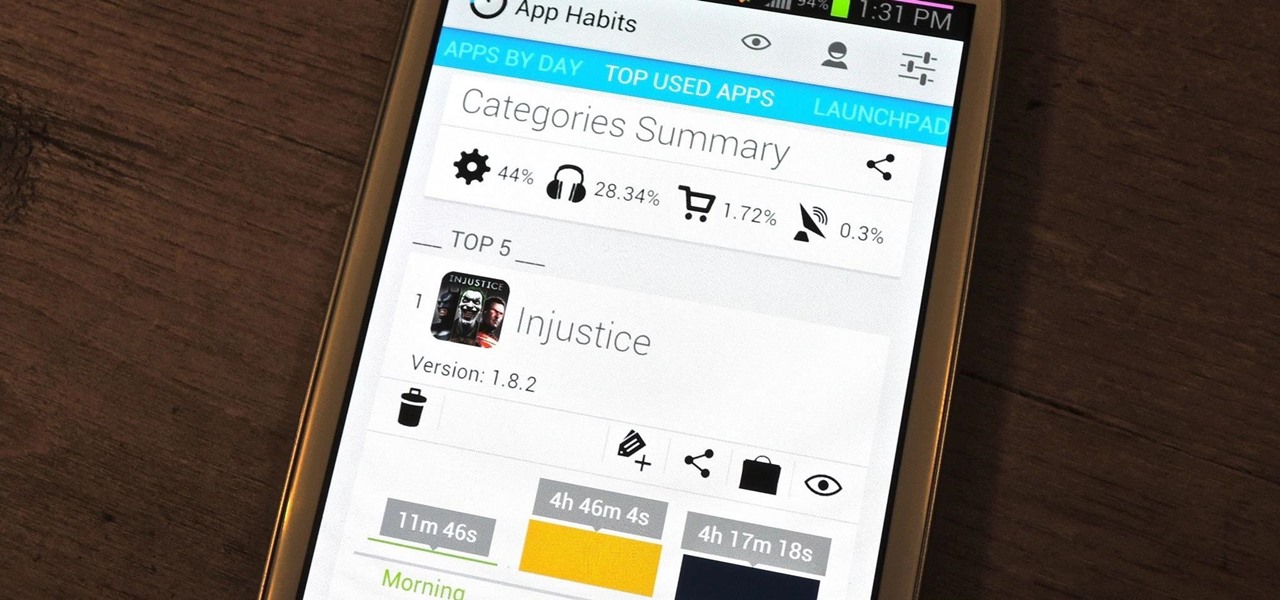
In today's dog-eat-dog world, every minute matters. Whether you're in school or working for the Man, a huge amount of your day is consumed by tasks, assignments, and other kinds of work. Then there's the time you spend playing video games, watching TV, or screwing around on your Samsung Galaxy S3.

Seemingly lost in the fanfare of the numerous features and specs of the Nexus 5 were a few highly innovative and handy add-ons—a low-power step detector and step-counting sensor—useful for tracking fitness data.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

The office of your physician, or your local hospital, is where you go when you need medical care. But it could also be where you could pick up a life-threatening infection.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

Yes, screen savers are fun to look at for a few seconds, but those animations actually used to serve a purpose beyond simple entertainment.

What's your top pet peeve? Open-mouthed chewing? Nail biting and knuckle cracking? The sound of silverware scraping? Or perhaps it's a bigger behavior, like leaving the toilet seat up?

Let's say you're flush with Google Opinion Rewards credits, or you just got a Google Play gift card for your birthday. This is a perfect opportunity to remove ads and unlock new features by upgrading some of your free apps to their paid counterparts, or to finally purchase that app you've been lusting after that doesn't offer a free version.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

There is never a dull moment when it comes to the internet. You can find practically anything you want, whenever you want it. To make that process even smoother and more direct, companies have created a bunch of apps designed to help you find what you're looking for, or enlighten you on a subject you may not have even thought of yourself.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Considering that nearly half a million brand new apps were published to the Google Play Store in 2015, you can definitely call it a banner year for Android development. In fact, it's getting to the point where we're a bit spoiled as end users, since we've grown to expect something new and exciting practically every week.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"