
How To: Create Service Files with Systemd
Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.


Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

Desktop users have taken advantage of dual-booting operating systems for decades now. If your core system software is lacking in any regard, dual-booting a secondary OS can give you access to those features that you're missing out on.
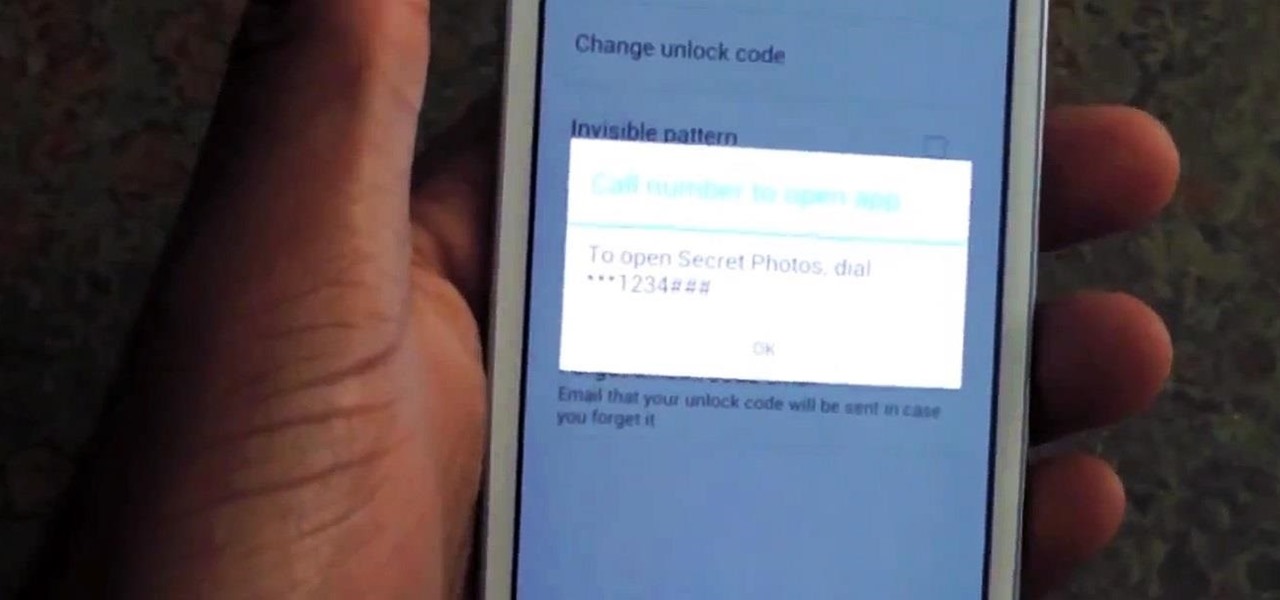
Whenever a friend borrows my Samsung Galaxy S3 to browse the web or make a quick call, I always pause to make sure there's nothing incriminating on it. I'm no superfreak, but some of my friends are, so I have more than a few photos on my device that I wouldn't wish upon anyone. I like to avoid these kinds of looks.

Caller ID is great to have, but there are certain situations where you don't want the person you're calling to have your number. People who sometimes use their personal phones for work may not want clients knowing where to reach them outside of work, and anytime you're dealing with Craigslist, it's better to be safe than sorry.
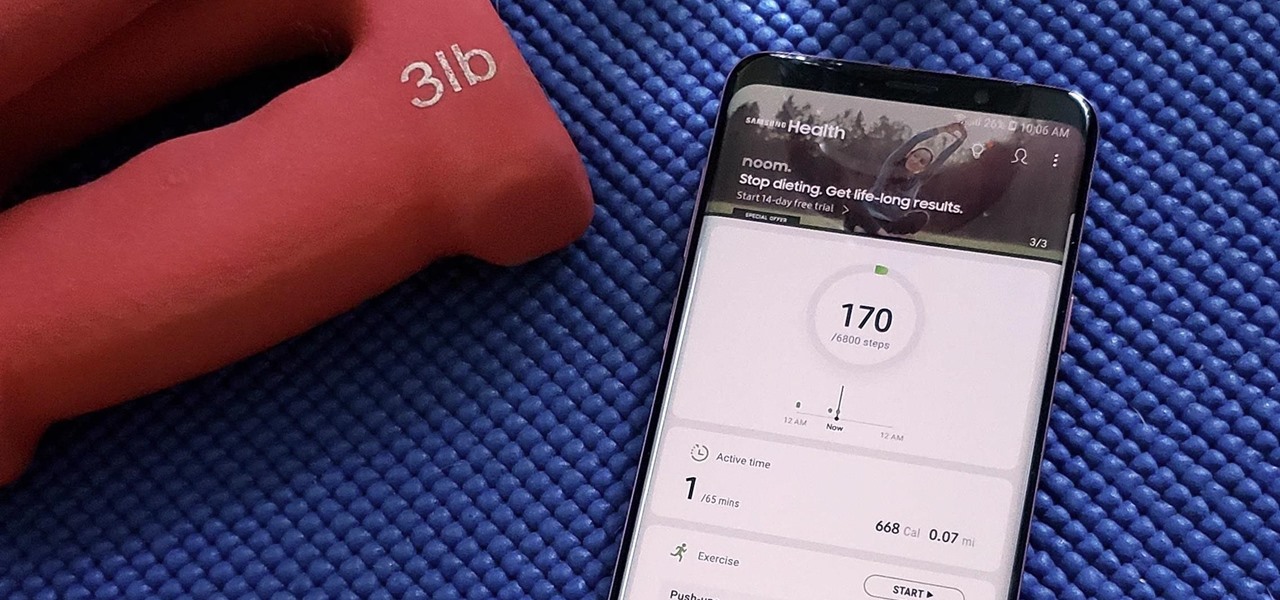
Samsung Health has become one of the most comprehensive wellness apps thanks to features that cover everything from step counting to nutrition logging and symptom diagnosis. But because the app has so much to offer, it can be easy to overlook some smaller, but useful features.
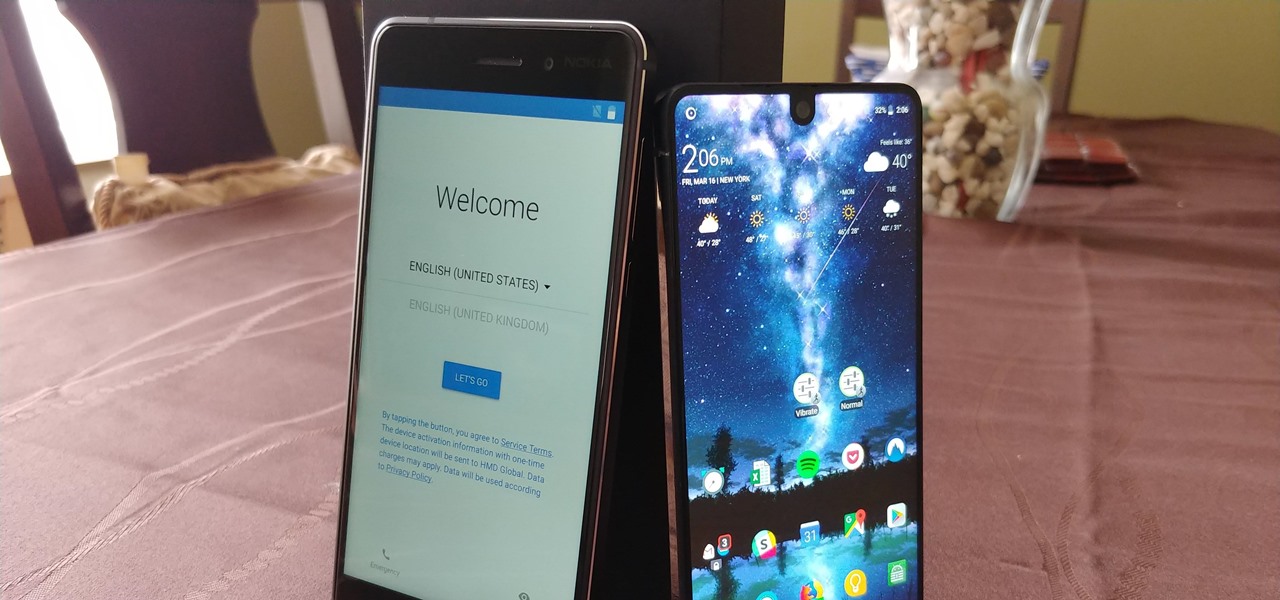
Setting up a new Android phone can be a pain. Although Google has some automated features, it does not restore everything. When it comes to transferring certain types of data like files and SMS logs, it's even trickier. By following our steps, you can be sure that you all your data will follow you to your new device.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

In case you didn't know, Android has an awesome hidden settings menu called "Developer options" that contains a lot of advanced and unique features. If you've ever come across this menu before, chances are you just dipped in for a minute so that you could enable USB debugging and use ADB features.
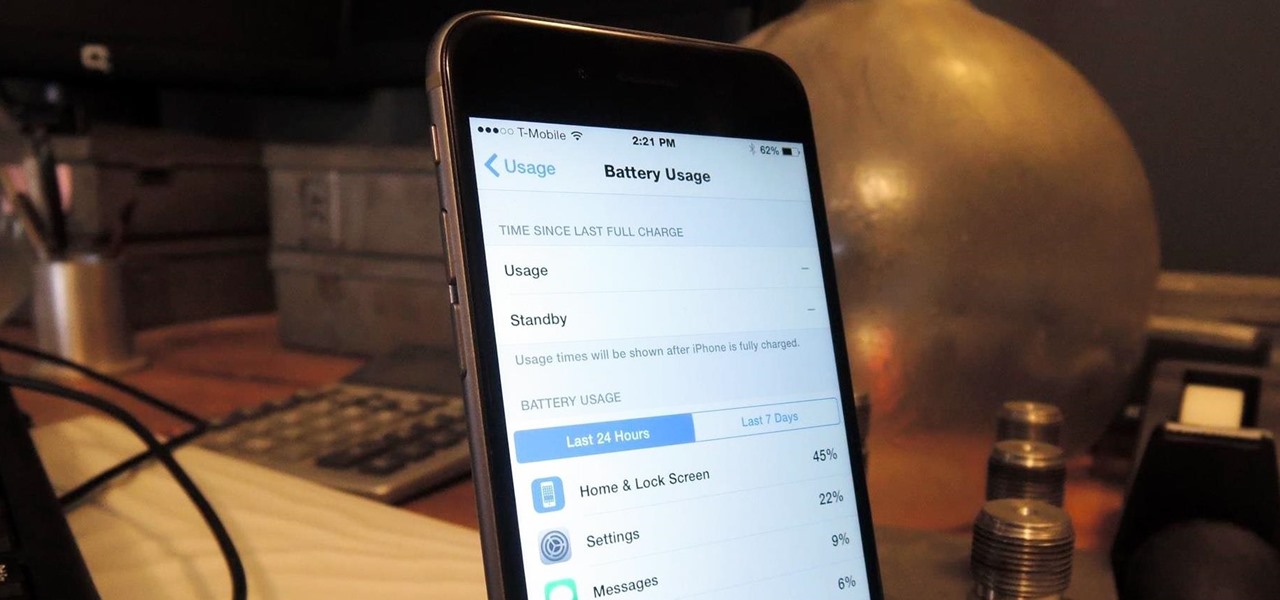
The new iPhone 6 and 6 Plus are supposed to last a lot longer in your pocket with improved battery life, but that doesn't mean that iOS 8 will be that friendly on your older iPhone model. All of those awesome new features could be killing your battery, but with some simple tweaking, your battery life concerns will be a mere afterthought.

There's a lot of cool features rumored to be included in next year's HTC One 2 (M8), the follow up to the flagship HTC One smartphone, including a fingerprint scanner, Android 4.4 KitKat, and Sense 6.0, but it's just too far away to get really excited about yet.

I get along with most of my friends just like anyone else. We chat on the phone, go out drinking, and play video games—and we choose who to hang out with and when. That same sort of freedom is hard to find on Facebook.
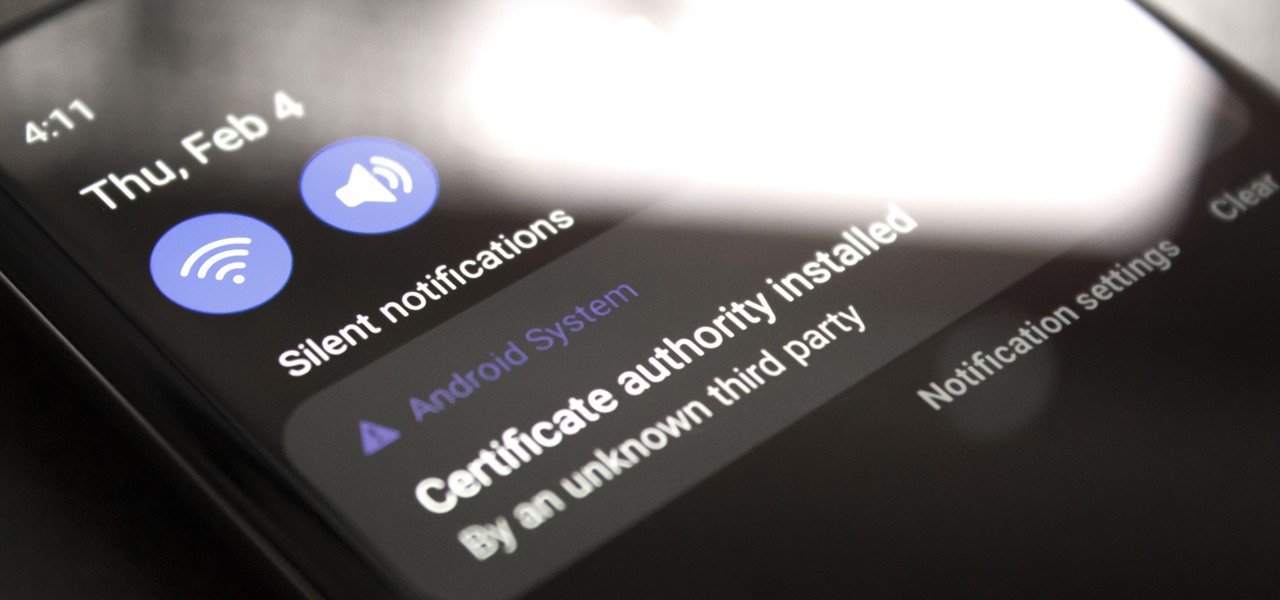
If you're using a VPN-based ad blocker with full HTTPS functionality on a Samsung phone, you'll get a notification informing you there's a third-party security certificate in use. No big deal, except it shows up every time you restart the phone. Samsung isn't alone in this type of annoyance, either.

Even if you pay for YouTube Premium, you are not exempt from ads. YouTube will stop adding pre-roll and interstitial ads, but content creators still have their own advertisements baked into videos. These product placements can be even worse than ads, and they're not the only annoyance embedded into videos. To put it nicely, YouTube is starting to have a problem with distractions.

There's an official way to install apps onto your Android phone using basically any device that has internet access — heck, you can even download new apps from an iPhone and they'll install in seconds on your Android device.

At the beginning of every year, Samsung drops a fantastic phone in the Galaxy S series, and then tries to top it with the Galaxy Note series in August. This year, Samsung had their work cut out for them. But they managed to improve on their predecessor and properly challenge Apple's best.

After testing a series of Android 8.0 builds, Essential hit the reset button and jumped to Android 8.1 Oreo. The beta program didn't last long, as Essential has now released the official 8.1 update to the masses. The features from the 8.0 betas are all still there, plus a few goodies specific to the updated version. We'll highlight the standouts here.
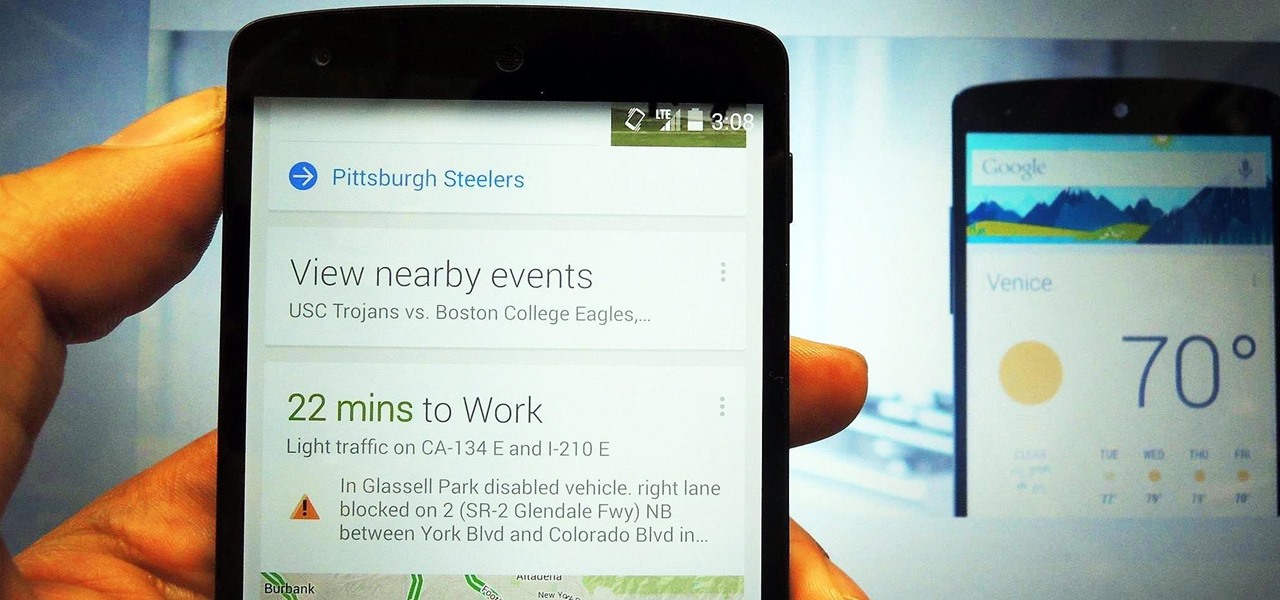
The launch of Android 4.1 Jelly Bean was also the launch of Google Now, a service that was supposed to one-up Siri, the resident personal assistant for iOS devices. Google Now offered enticing features, but its launch went unnoticed by a great many Android users.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.
Welcome back Hackers\Newbies!

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.
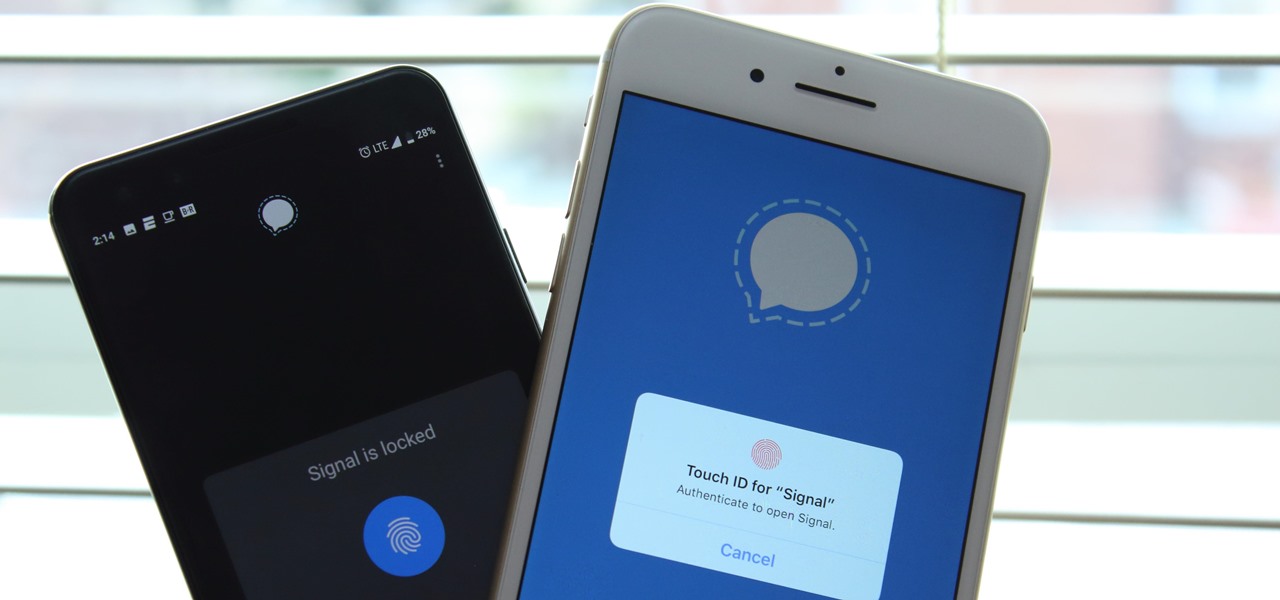
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through the process.

SalaryExpert.com or Salary.com are two great Websites designated to informing people of expected salaries of particular job fields, so people know what to expect when offered a salary. Know what salary amount to expect when being offered a job in a particular job from a career adviser in this free video on job guidance.

This video is about a particular pool or snooker game shot technique called "Shooting or Going around the Angles." The presenter, with a alias name of 'Forcefollow', first describes a particular 9-ball pool game situation that would require this technique, using a computer generated picture image to show an overhead view of the pool table, with the pool balls in question placed at certain locations within the table and showing the various angle trajectories paths of the desired ball to be str...

So you just upgraded your Mac to OS X Lion and it greeted you, not with a friendly welcome video as Snow Leopard did, but instead with a tiny clip informing you that the Apple powers that be, have decided to reverse the 2-finger scroll direction, without even asking if you'd like to!

I received an email today, informing me that Google would be adding the +1 button to Google AdSense ads. Google's Inside AdSense blog explains the details further. You will be able to see that your friend has +1'd the ad, along with any of your other contacts. The recommendations will be used to create more relevance for you, as the user.

Minecraft might still be in development, but that doesn't mean a creative guy like Notch doesn't have time for other projects. A few months ago he and his company Mojang announced their second game, a digital collectible trading card affair called Scrolls. A simple title (perhaps too generic if anything), but it's not the name of an extant game, and it's appropriate given the visual style and card-based gameplay of the game itself.
Our class had been assigned interviews with political representatives from different branches. In these interviews we asked questions that we had generated about their career position, advice to young activists, our government system, getting involved, and their opinion on certain laws. Here are the results from the two interviews that were done.

As hard as you try to protect your valuable information with strong passwords and anti-doxing measures, there's nothing you can really do when someone else gives up your goods. And that is the case with the recent Global Payments breach.

Grand Theft Auto 3 was the biggest video game of the last decade, by far, introducing open-world adventure games to consoles, a genre that now rivals shooters and sports games for market dominance. A huge map, decentralized narrative, and myriad of interlocking quests and objectives that happen in a flexible order all became hallmarks of the "new" genre, along with the ability to shape the morality and reputation of your character. And most importantly, all of the quests and stories are compl...

The community here on Null Byte has always been great and helpful in sharing their know-how, even before I took up admin duties in this World. I jumped at the chance of leading Null Byte because I enjoy teaching and informing people on all of the important need-to-know things out there, but more so than that—there is a deeper reason.

Okay, stop me if you've heard this one. You have a document that you want your co-workers' advice on. You attach said document onto a mass email. The first reply comes back with an edited version of the document. You begin to make changes, but another email comes in, with yet another edited version. Soon you're drowning in a desktop folder full of mismatched documents, all with the same name.