While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

Matt describes the necessary steps to take before you begin to build your infrastructure. Find business and design requirements.

In this clip, you'll learn how to get started using HyTrust. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the process in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.
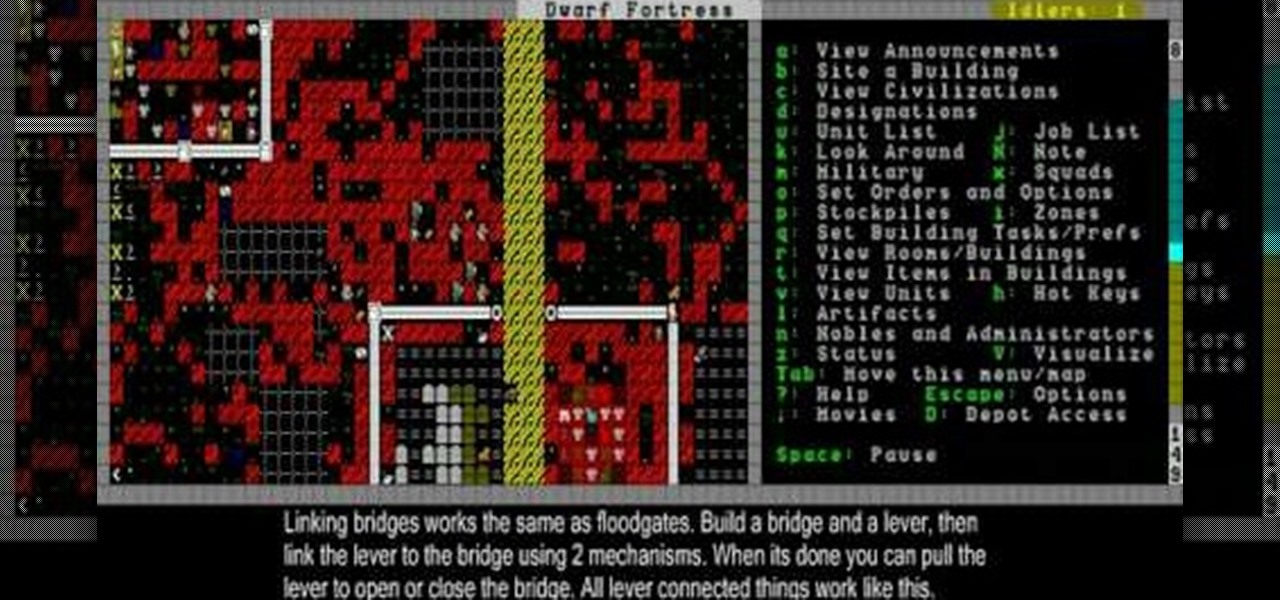
Magma is valuable but dangerous stuff in Dwarf Fortress, and this video will teach you still more about how to handle it. It also covers how to build bridges, floodgates, and levers that will link up and create effective dwarven infrastructure.

Now you've got a little bit of a fortress going, and it's time to continue building your infrastructure. This video will show you how to build bedrooms, farms, and stairs.
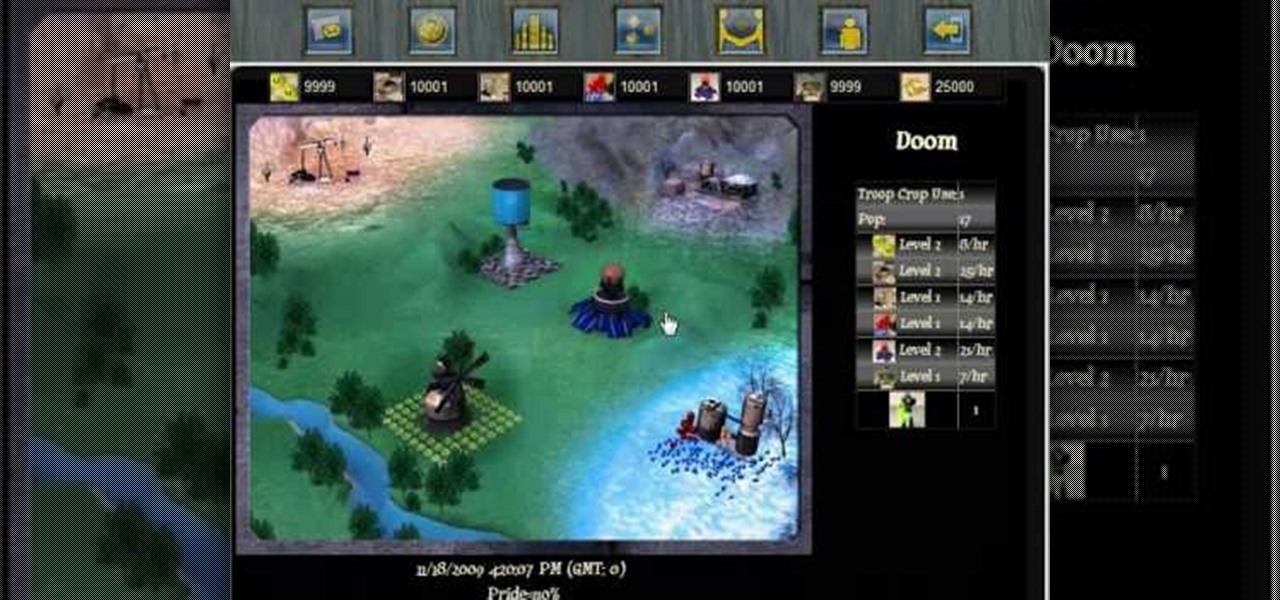
Settling a new planet will decrease your pride ratio, because your population will increase when you're settling a new planet. If you're not sure how to even settle planets...

In order to spy and gain intelligence on your Conrohl enemies, you need to make an intelligence agency. Then you recruit your spies to perform simple espionage.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to map networks with Spiceworks.

The ASP.NET AJAX Control Toolkit is a shared source project built on top of the Microsoft ASP.NET AJAX framework. It is a joint effort between Microsoft and the ASP.NET AJAX community that provides a powerful infrastructure to write reusable, customizable and extensible ASP.NET AJAX extenders and controls, as well as a rich array of controls that can be used out of the box to create an interactive Web experience. This video tutorial will get you started using it. Take a look.

This video includes instructions on how to get your PlayStation Portable (PSP) onto the BGSU wireless network.

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

According The Venture Reality Fund, the introductions of Facebook's camera platform and Apple's ARKit catalyzed increased activity among companies developing consumer applications.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

As we predicted this time last year, Magic Leap is finally moving from consumer entertainment hype to making a firm commitment to enterprise customers.

Have you ever been called a "noob" or "eZ" after some person kills you? have you ever said "you hack" or "you suck" after getting your butt kicked by another player? this wont ever have to happen again. It is actually possible to be very good at PvP in Minecraft, and you can also be good at it. Now, it is your turn to win in every battle you fight in Minecraft PvP.

Forget Waymo, Uber, Tesla, and other other heavily mediatized driverless contenders — German premium carmaker Audi AG has become the first OEM to introduce a Level 3 car sold in retail channels.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Cholera is rapidly spreading in Mozambique, with over 1,200 people infected. Since the outset of 2017, cholera has spread from the capital city of Maputo (pictured above) to three of its ten provinces. Health officials report other areas in the country are seeing case counts rise, and two deaths have been logged so far.

Japan is in the process of curbing its aging population and mature workforce. According to The Diplomat, the country's population has been declining at a steady rate. To meet future productivity demands in commercial and industrial sectors, local officials are turning to self-driving technology, including truck platooning, where three or five vehicles travel autonomously in a string formation. This practice, according to a study by MIT, can reduce fuel consumption by up to 20% (more about thi...

This is OSCAR, the Overly Simplified Collaboratively Actuated Robot. He's built from an old Roomba and an Android tablet, and he's about to make Google+ a lot more interesting. The robot is controllable by users in a Google+ Hangout, allowing the audience to interactively explore OSCAR's environment via his on-board camera.

If you're living or staying out in the middle of nowhere or a rural area outside of a big city or town — where there are no reliable cable, fiber, or wireless networks available — how can you get an internet connection? There are several possibilities, but they all come with tradeoffs, which we'll go over in detail.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

After North cut the base price of its Focals smartglasses, Vuzix is now testing the waters of a lower price point for its Blade smartglasses.

The debut of Microsoft's HoloLens 2 went off without a hitch, and now it's time to figure out if you want to hop aboard the updated augmented reality train.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

We are still months away from Google unveiling the new Pixel 3 and 3 XL. As rumors continue to trickle in revealing more about what it will look like and its specs, we've learned an important aspect — who is actually manufacturing them.

We've heard a lot about self-driving taxis, as car and ride-sharing companies compete to win the driverless gold rush. But FedEx wants to bring its enterprise into the mix, as the head of its freight division has asked the US government to develop laws for self-driving trucks.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

At a global security conference in Munich, philanthropist and businessman Bill Gates spoke about the next pandemic and a dire lack of global readiness. Here's how his statement could come true—and how to be ready when it does.

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

Chrome and Firefox are the leading third-party web browsers on the desktop platform, so it would make sense that they'd go head-to-head in a fight for living room supremacy.

By Zech Browning Shihan of Gyodokan Martial Arts. Step 1: "Storm Within the Calm - Putting It All Together - Part 1"

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

After three years and change, no one seems to be able to knock Pokémon GO off its augmented reality throne. Zombies, dinosaurs, and ghosts have all met defeat at the hands of the pocket monsters. Heck, not even the world's most popular wizard and Pokémon GO's developer can replicate the original's success.

Intel's RealSense family of depth tracking cameras has a new addition with a different set of sensory capabilities.