Every year, 100-200 people in the US contract leptospirosis, but usually 50% of the cases occur in Hawaii where outdoor adventurers are exposed to Leptospira bacteria found in freshwater ponds, waterfalls, streams, and mud. That's why it's so alarming that two people in the Bronx have been diagnosed with the disease and a 30-year-old man has died from it.

BlackBerry has formally announced the arrival of its flagship, the KeyOne, during Mobile World Congress 2017 in Barcelona. The all-Android KeyOne looks distinctly BlackBerry, with its 4.5" screen and physical QWERTY keyboard. Here's the lowdown on this elegant handset that hearkens back to BlackBerry's heyday, which had previously been known by its code name, the BlackBerry Mercury. Aluminum Unibody with Physical Keyboard

A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

Over 1.2 million people in the US are infected with human immunodeficiency virus (HIV)—and one out of eight of them don't know it. Even after decades of intense research into the virus, there's still no cure for it. One of the big problems is that the virus hides out in certain cells of the body, resisting treatments that kill it.

Using mathematical modeling, researchers suggest weather and warming created the "perfect storm" that drove the Zika outbreak in 2016.

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

We like our Egg McMuffins around here, albeit homemade with our preferred ingredients: whole wheat (or homemade sourdough) English muffins, a slice of thick Tillamook cheddar cheese, a meat, perhaps, like Canadian bacon, and finally—that perfectly-fried, perfectly-shaped egg.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

You might be familiar with the use of zucchini blossoms in cooking and maybe even know how to make herbal simple syrups. But if you really want to show off as someone who knows how to use flowering plants in food, try adding some flower water to your cooking/baking repertoire.

If you open your refrigerator door and find leftovers there, then you are fortunate—even if you don't realize it right away. Leftovers are the ultimate budget hack because they maximize the value of your meals; and it's a smart way to save money while making the most of your food purchases.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - at my blog, here - https://techkernel.org/2015/12/11/embed-metasploit-payload-in-apk-easily/

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

Arcade games have always been more about chance than skill (at least when I play them). Whether you're at a children's party at a Chuck E. Cheese's or drinking it up with your pals at a barcade like Dave & Buster's, you'll find similar games that hold the golden ticket to fun and cheap prizes that no one needs—boy, do you want them.

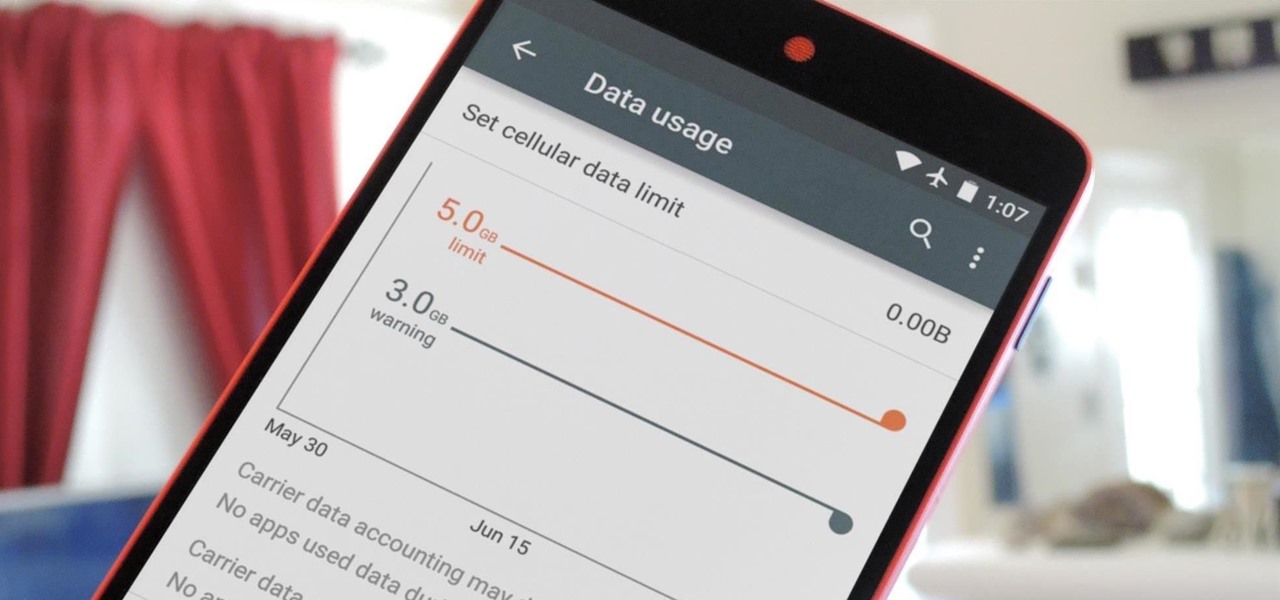
Ever watched Netflix on your phone only to realize an hour later that you forgot to turn Wi-Fi on? That's a whole lot of data used.

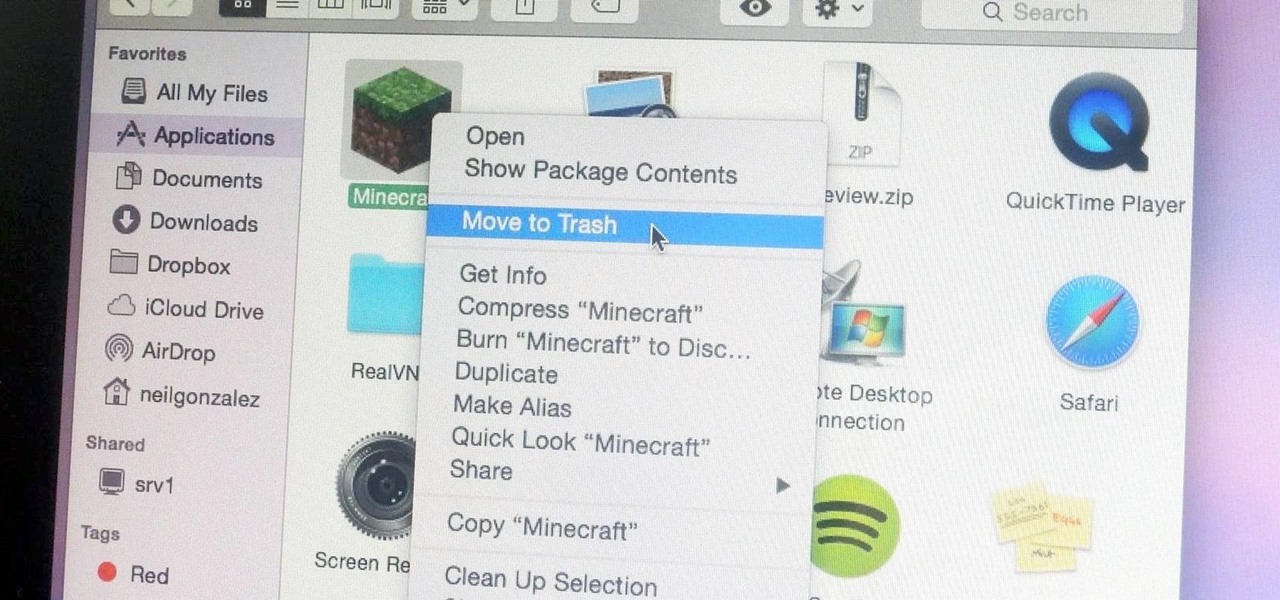
Uninstalling an app on your Mac isn't as straightforward as you would think. When you drag and drop an app into the Trash, then empty it, the main app itself may be gone, but many associated files and folders are left behind. So how do you get rid of them? There are a couple of ways.

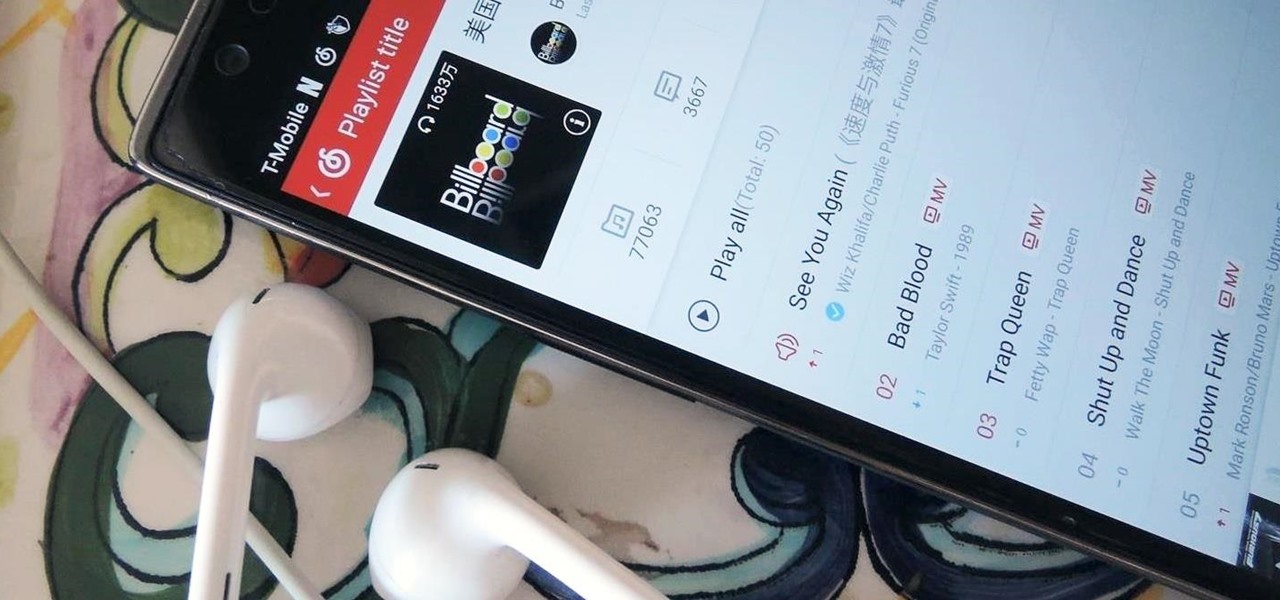
We recently lost Grooveshark, the free music streaming service that supplied users with a huge catalog of free music anytime, anywhere. Since its shutdown, I have been scrambling to find a half-decent alternative, and my expectations were more than exceeded when I found NetEase Music.

The gag reflex: it can interfere while in the dentist's chair, upon seeing another person throw up, or even just getting a whiff of a disgusting, stomach-twisting scent. Every time this reflex kicks in, it stops us immediately, inducing a choking, gagging, coughing fit.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

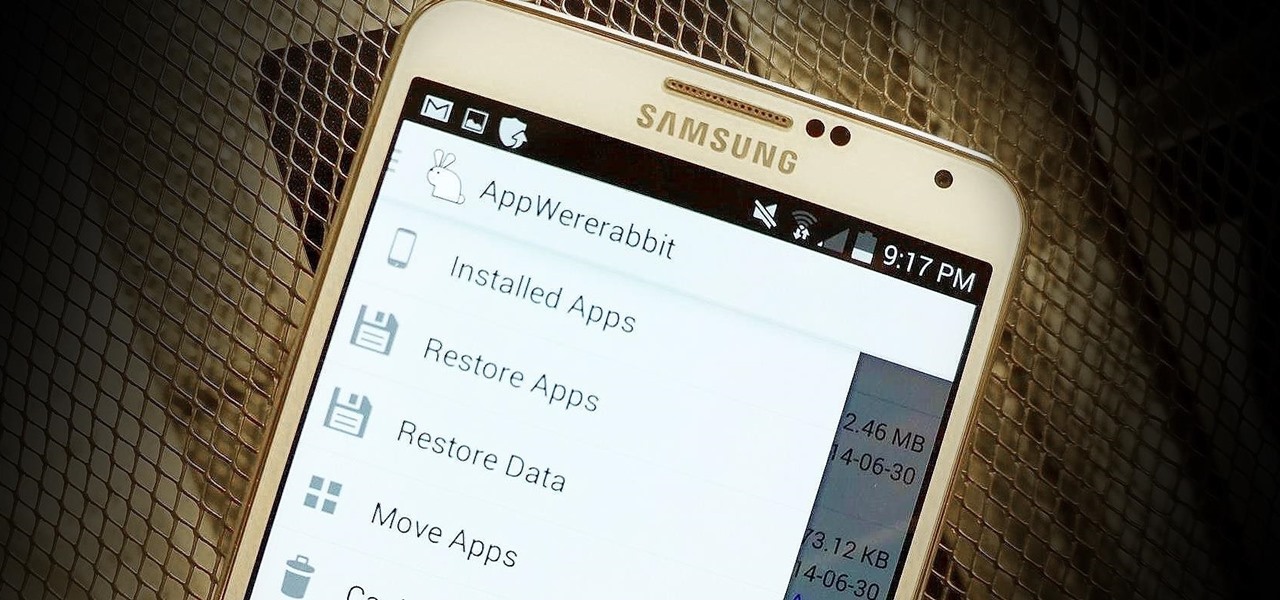
There are over 60-something Android apps cluttering my app drawer. While I'm constantly on the look out for new mods and apps to install, the default way of managing them is cumbersome and just feels unintuitive. I mean, who on Earth would wants to individually manage each app on their device?

Boozing it up at work might have been okay back in the days of Mad Men, but today, employers prefer that their workers stay sober. What you and your bosses probably don't know is that a little drinking on the job can actually increase your creative capacity and problem-solving skills. Alcohol Can Enhance Your Creativity at Work

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.

Today's project will show how you can convert your laptop, smartphone, or tablet computer into a makeshift projector—just in time for March Madness! It's super cheap to build, and can add a little bit of creative fun to your next sports party.

You may or may not have heard the term "greebles" or "kit-bashing" before, but if not, they may sound like nonsense. Particularly 'greebles', which sounds more like the name of a small, gremlin-like creature. However, I assure you that they are very important in prop-making, and if you can master them both, you'll be able to make intricate, great-looking props in hardly any time!

Here's how to make dry-ice at home, or wherever you feel like it! All you need is a pillow case, and a CO2 fire extinguisher.

If you've rooted your Motorola Droid chances are that you are enjoying the results, but are concerned about the consequences if you phone updates or in any way become incapacitated since your phone manufacturer will not be pleased with what you've done to the phone. One way to ameliorate these fears is to back up your phone. This video will show you how to use Nandroid to make a backup of your rooted phone.

This video demonstrates how to make natural fiber rope using Douglas iris, a plant which is found along the Pacific coast from Santa Barbara from to Oregon. Before beginning, you should know that Douglas iris is poisonous when eaten, but it should be safe when you are handling it. The plant blooms every spring and dies every winter and has a brighter green color on top and a duller green towards the stalk, with a dark purple tint near the roots. You should collect plants which have died from ...

To start you will need a craft bag. They can be found at Michaels but they can be difficult to find. Take the bottom flap of bag and fold it over. The bags will be cut down to 4 and 3/8. You will next need your pink pirouette cardstocks, one will be 5 3/4 x 3 5/8 and it will be scored at 1 1/4. That will be the back of the bag. The other pirouette will be 4 1/2 x 3 5/8 and it will be the front of the bag. On the front Pirouette you will use your stamp on the front right hand corner as close t...

Mikey shows you how to use the cyclic controls on a 6-channel helicopter radio controller. Cyclic controls move a helicopter forwards and back, as well as side-to-side. If you're comfortable with using the rudder controls, you're ready to move on to the cyclic control, usually found opposite of the rudder controls on the radio controller. The control is easiest to use while the helicopter is in the regular orientation, with the tail pointed towards you. Mikey also demonstrates how to use the ...

How to change the outdrive gear fluid on your boat.

Childhood obesity is becoming a national epidemic. If we don't improve what our kids eat soon, the next generation will have a significantly shorter lifespan. Instilling good eating habits when kids are young makes it much easier for them to stay healthy as they grow older.

Do you have a bunch of flawed beads left over after you make your crafts? You know the ones, the chipped, cracked, sharp ones that don't make the cut and usually get tossed in the garbage? Why not make those into something lovely, where the cracks don't matter? In this two part tutorial, learn how to turn your discarded beads into a beautifully shiny wind chime for your backyard. This chime is unique and makes a lovely noise in the wind. Let's get crafting!

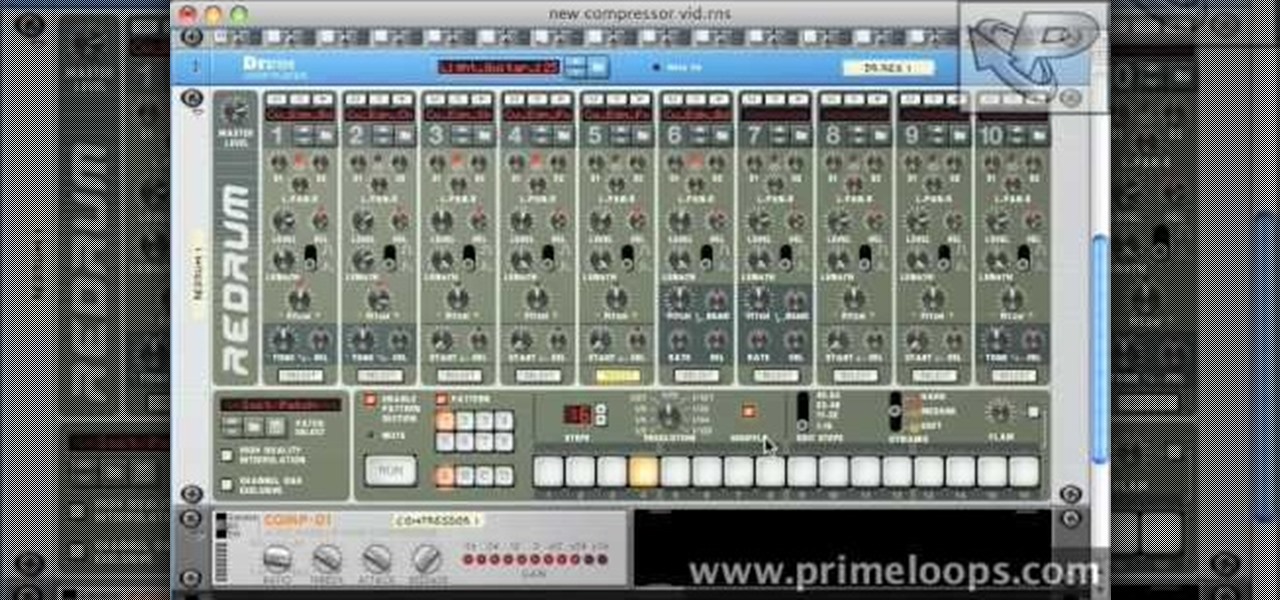
This tutorial video will show you what the purpose of compression is and how compression works through its parameters. Your instructor illustrates a drum beat and a plucked guitar line. Beginning with how to compress the drum beat, take (download) a drum sound pack without compression and to add compression using the software right click on the drum machine, choose create, and then choose combo on compressor. The virtual compressor has all the dials and adjusters found on any basic compressor...

In this tutorial from the TyingItAllTogether Channel, you can learn how to make double and quadruple looped pendent knots. These knots are commonly found in Celtic designs. Once you learn how to create these knots, you can use them in arts and crafts projects for necklaces or bracelets. To begin, the double looped knot is done by taking a piece of rope and folding it in half, allowing the two sides to be next to each other. With one side of the rope, loop it around the other side of the rope,...

Now you can find your IP address if you need it and you don't know it, it very easy. Or if you have problem with a person on the internet, now you can discover who that person is. You can find her/his IP address and after that you can find her/his real name. But after you find the IP that you were looking for, you have to check if the person who own this computer is in your network, because if you want to find his/her name, the program works only if the owner is on your network. So if you are...

Make sure to detonate the bomb growth in this level for the Xbox 360 game Darksiders, section Twilight Cathedral - Revisit Scalding Gallow. Upon defeating Tiamat, War will find himself back out front of the cathedral. Go speak to Vulgrim to learn about Serpent Holes. These allow you to "fast travel" back to previously visited places, as long as you've found Vulgrim in these places. Make you way back to the Scalding Gallow and go talk to Samael who sits on a throne in the middle area where you...

Learn how to locate the assassinate the Templar Captain of the Guard. Locate him in the Limassol Marketplace in Mission 4 on the Sony PSP. The Templar Captain is as good as dead with his location so boldly announced on the map. A word of caution: if you make a ruckus approaching him, he will be backed up by annoying archers on the rooftops. Once you've found him and carried out the deed in any way you see fit, return to the Safe House for the next objective. For more info, watch the whole gam...

Make your Icy Tower score the highest ever. Break records. Impress friends. Rule the game! How? Cheat Engine, a simple hacking program.