The Galaxy S6 won't hit shelves until later this spring, but that didn't stop the Android community from working its magic and pulling a handful of apps from the device's stock firmware. Several of these apps rely on framework elements that aren't present on current-generation Samsung Galaxy devices, but the new version of the Smart Remote app can be installed without much difficulty.

Using breadcrumbs in the kitchen is the perfect way to add crisp and crunch to the usual salad, entrée, or dessert. As chef and media personality Mario Batali once said, "There's almost nothing I wouldn't put homemade breadcrumbs on."

Eye contact is key in conversations, job interviews, and honesty, and it can help you access others' thoughts and spot heavy drinkers. Locking eyes with someone can even help you fall in love, whether you know them or not.
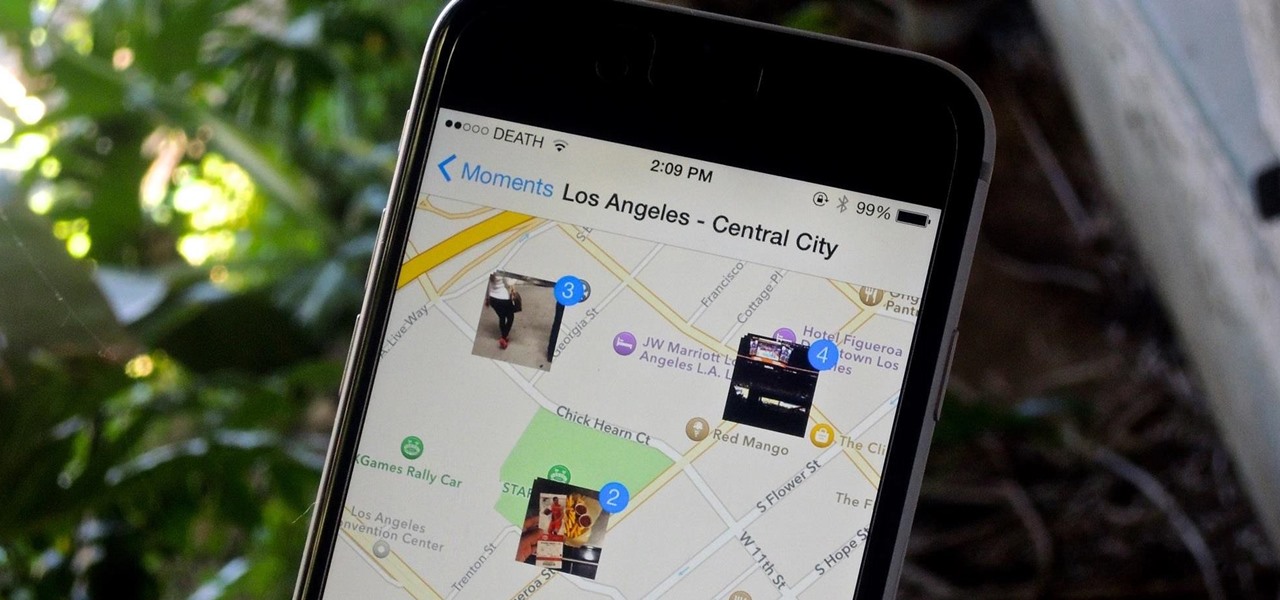
Location Services, a native feature on iPhones since iOS 6, is used to pinpoint your approximate location using a combination of GPS, Bluetooth, Wi-Fi, and cell tower information. Apple uses this on their smartphones for many useful reasons: so that you can tag locations in Instagram, get better directions in Maps, and check for matches based on your location in Tinder.

We've all been there: facing a lengthy, complex word that ignores the phonics we were taught in elementary school, unsure of not only its pronunciation, but also its meaning. These words, from autochthonous to esquamulose, are both terrifying and impressive. After all, if someone knows how to use them—and even say them—they must be quite smart. Yet before you begin stuffing every email and presentation with verbose prose, you might want to reconsider what others perceive to be intelligent.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

One of the most mind-blowing meals I ever ate occurred when I was 12 years old. The main course and sides were good, if unmemorable, but my jaw dropped during dessert when my friend's mother whipped out a blowtorch—as in a bona fide welding torch from the hardware store—to finish off the crème brûlée.

When Google announced its new Android TV platform, one of the features they advertised was a home screen that automatically reorganized your apps based on how frequently you used them. Unfortunately, this feature either didn't make the cut, or is still under development, since the home screen on the Nexus Player always remains static.

Finding the right theme can be a pain. Some are too gaudy or simple, while others look like they were thrown together as a joke. So why not try your hand at making your own?

The camera in CyanogenMod, CameraNext, takes some pretty impressive shots when compared to those offered by HTC Sense and Sony Xperia, but it doesn't have many of the features that make it a real competitor. Even the Color OS version of the OnePlus One has received better reviews when comparing low-light shots, which implies that it's not the camera sensor that's lacking, but the software.

We've all heard the cliches: always look at the glass as half full; a smile can change your entire day; and there's always a silver lining.

Cooking rice, pasta, and other grains in water is so boring. There is a much better way to guarantee they will have your mouth chewing something seriously tasty: cook them in something that isn't water. Alternative liquids such as stock, milk, juice, or even tea will give bland dishes a fresh new flavor boost. If you're not sure how your dishes might taste, never fear: we tested them out. Before getting started, be sure to read this article first so that you know why it's important to rinse y...

If you're the de facto tech support person in your family or circle of friends, you know how frustrating it can be to have to hold someone's hand and walk them through every troubleshooting step. Luckily, several options now exist for you to remotely access a Mac or Windows PC, which effectively skips the middle man and lets you get straight to fixing the issue yourself.

Samsung phones have a pretty nifty little feature called Smart Stay that will prevent your screen from turning off while you're actively using your device. Trouble with this is that it's exclusive to Galaxy devices and it uses a ton of battery since it monitors the front-facing camera to detect when you're facing the screen.

The future: that time that lies ahead, unknown and overwhelming. Whether you're an obsessive planner or someone who can't think more than two days ahead, considering the future can be frightening with all of the "what ifs." Don't let the future keep you awake at night—in fact, the less you think about what life holds in store for you, the better off you'll be.

If you've ever taken apart an electronic device that uses physical buttons, you already know why these types of input methods are destined to fail. The rubberized contacts used in physical press-and-release buttons like those of a gamepad or keyboard are incredibly frail and can easily wear out over time.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

You've found the perfect tree — or so you think. As hard as we try to display an ideal tree each year, both plastic and pine can disappoint, especially when you're shopping on the cheap.

With its white Apple logo on a plain black background, iOS 8's animated boot screen isn't very interesting. While there is no built-in way to change this boring animation, you can customize this boot screen animation if you have a jailbroken iPhone, and the process is fairly easy. You can even create your own using your favorite GIF file.

Decisions are rarely easy to make, and there are countless ways to mull your options over. You can sleep on it, pluck flower petals, make a list of pros and cons, or even follow the advice of a psychic. Yet to make the best decision possible, you might want to consider holding off until a certain time of the day—or even until you feel specific emotions. The state you find yourself in has significant impact on each decision you make.

No one wants to appear stupid. Whether you rely on lengthy, complicated vocabulary to show your smarts, or enjoy highlighting your speedy mental math skills, everyone prefers emphasizing intelligence over hiding it.

One of the few areas where Android lags behind iOS is a comprehensive backup solution for apps. Root tools, such as the popular Titanium Backup, are capable of backing up all of your apps and their data, but not everyone wants to root their device and potentially run into issues with voided warranties.

Hate slogging through pages and pages of weighty books and lengthy work documents? You may not be able to depend on speed-reading apps, but with the right font, you can increase the number of words you scan each second, speeding up your reading pace exponentially.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

When Android 5.0 rolls out to the Nexus 5, several changes and new features will come along with it. The over-the-air update is already rolling out, and if you don't want to wait, you can get it right now.

On mobile devices, the Notification Center received a huge facelift when iOS 8 was released, but it wasn't until Yosemite that its Mac OS X counterpart received the same amount of love—especially the much needed ability to add custom widgets, like a FaceTime dialer.

It's pretty logical for your MacBook to sleep when you close its lid, but under certain circumstances, you may not necessarily want this feature to kick in.

Can you tell when someone is shooting you a fake smile? Even though fake smiles are easy enough to see through, we all still do it, attempting to show others just how happy we are when we're really feeling less than fantastic. Unfortunately, every smile we fake makes us a tiny bit more miserable.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

As much as app developers would like to simplify things with icons and visual cues, text is still a huge part of a smartphone's interface. Much of our media consumption is text-based, and while Google's Roboto font is a beautiful typeface, a little variety here and there certainly wouldn't hurt.

I have never been a morning person, and that's a trait that I don't think is going away. Combine my distaste for early hours with being a heavy sleeper, and it adds up to a lot of alarms being dismissed in a haze, with no real intention of ever waking up.

I may not be a parent just yet, but I've dealt with enough worrisome mothers to know that keeping a watchful eye over your child is of the top-most importance. Since most people cannot afford to stay right by their child's side 24/7, developers are always looking for ways to make the pain of stepping away a little less stressful for parents.

Garlic isn't just a food, it's a legend. It's been found in the pyramids of Egypt and is referenced in the Bible. Hippocrates, the father of Western medicine, prescribed it regularly, and it was given to the first Olympic athletes in Ancient Greece to enhance performance (take that, Lance Armstrong). And, of course, it's famed for its ability to ward off evil, whether it's in the form of vampires, demons, or werewolves.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

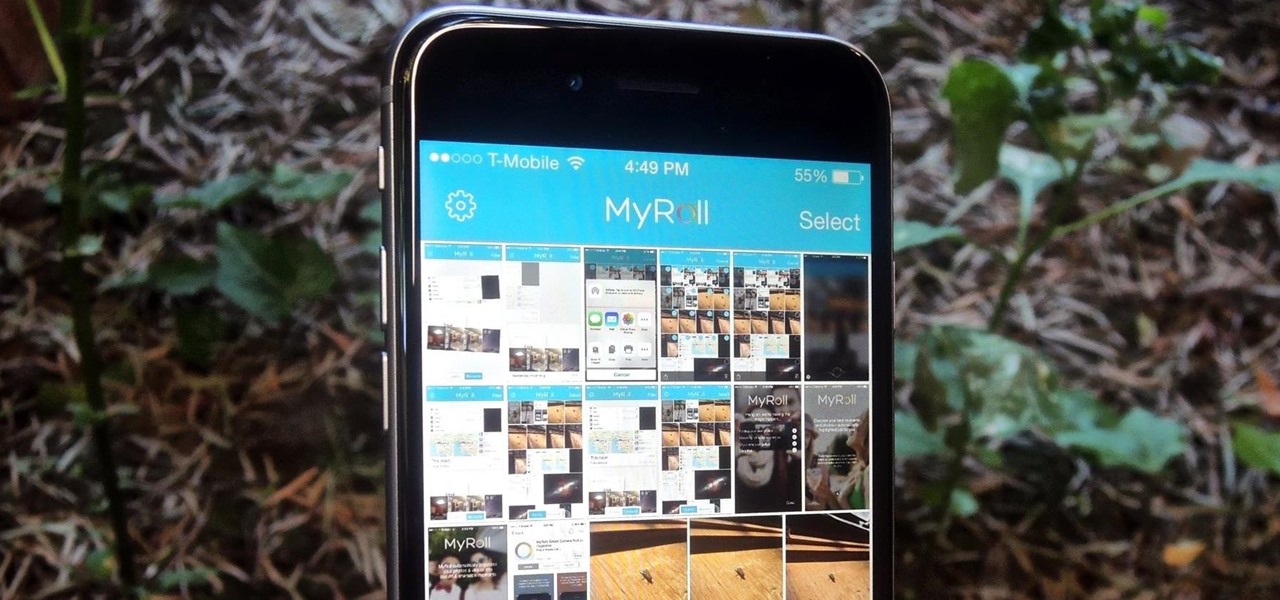
While there isn't a "Camera Roll" anymore in iOS 8 for your iPad, iPhone, or iPod touch, the photos that were once in it are not missing—they're just not as convenient as they once were. In the upcoming iOS 8.1 update, Camera Roll will be making a comeback, but we've found something better that you can use right now—even after Camera Roll returns!

The world of spices can be bewildering. They promise to make your food more flavorful if you know how to make the most of them. Unless you know a couple of essential tricks, however, it just seems like you're adding bits of colored powder to your food.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

One of the best ways to reduce clutter and enjoy the new iOS 8 wallpapers on your iPhone is to use the little-known trick of hiding all of your main home screen apps. This trick effectively moves your apps off the main home screen and over to additional home screen pages, or in your dock, making your main home screen beautifully clutter-free.

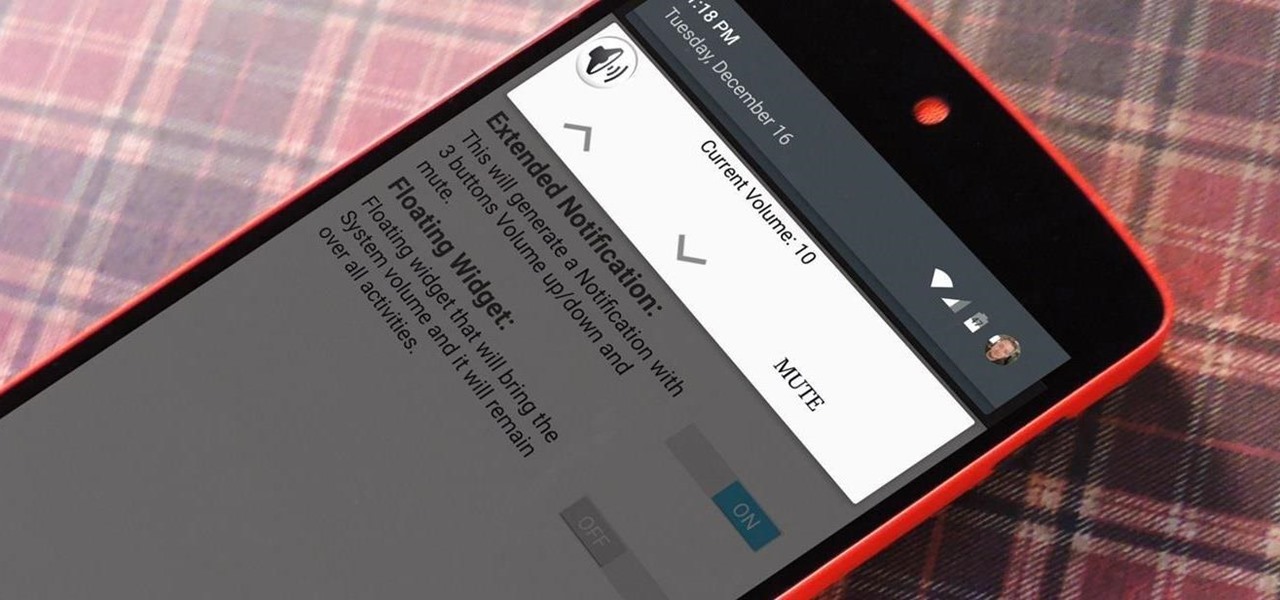
Your phone's volume panel is one part of the user interface that usually goes unnoticed to themers and developers. With themes capable of changing the look and feel of the fingerprint scanner, keyboard, and other system apps, this central aspect of the UI seems to get lost in the shuffle.

As soon as third-party keyboard compatibility was announced for iOS 8, Apple loyalists and the newly curious both looked to the popular Android third-party keyboard developer, SwiftKey, to see if they'd be offering their services to iOS.