Using a popular movie character as a basis, and drawing in manga style, our video host shows us visually how to properly color in whatever hair you may be attempting to draw. Using first the primary color along each strand, we are then show that a lighter or darker version of the primary color should be utilized, right alongside the initial color. And then, to complete each strand and give the hair a varied and popping appearance, you should always outline each strand in a nice simple black. ...
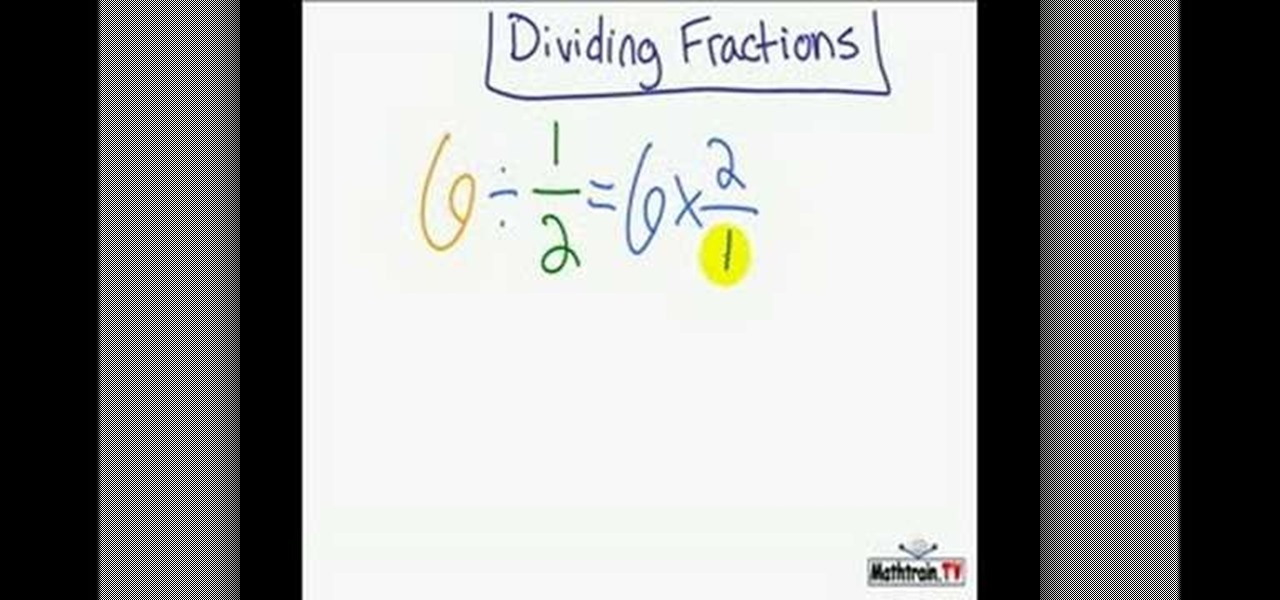
In this video title 'A Quick Look at Dividing Fractions', the tutor Phillip shows how to divide fractions. He says that division of two fraction is nothing but multiplication of the first fraction by the reciprocal of the second fraction. So essentially the initial division turns out to be a multiplication operation which is very easy to perform with fractions. He solves a small example to illustrate his rule. This video is a simple and easy to follow tutorial on how to perform division on fr...

Start with a nice firm pomegranate. Take the pomegranate in your hands and start squeezing it by pressing with your thumbs one of the other pushing into the pomegranate. Squeeze all around the whole surface of the pomegranate. As you press in using your thumbs overlapping each other you will hear the pomegranate seeds popping inside the fruit. Take the softened pomegranate and bite a hole into the side. As you bite the hole make sure you suck the juice as it begins to come out. Once you have ...

This experiment uses a ballistic pendulum to determine the launch velocity of a metal ball. This is compared to a measurement of the launch velocity found using projectile motion. You may wish to emphasize why energy is not conserved in the initial impact of the ball into the ballistic pendulum, but momentum is, and conversely why energy is conserved as the pendulum rises but momentum is not conserved.
This video is to get you started with the initial setup of the Doom 3 to Maya workflow. Topics covered (in order) are set up, export your first character ingame, texturing, animations on character cycles, load game models into Maya. Part 4 is a WMP video.
Installing Joomla on a Windows server can be tricky, on Windows running IIS even more so. Installing Joomla 1.5 in this scenario has caused many frustrations.In this video, we take the process step by step and jump over the hurdles that cause some people to wind up pulling their hair out. If you follow along closely, you will be up and running in no time, and if you haven't already tried to do this, you will wonder why people find it so difficult. There are some prerequisites to the steps in ...

All of us know by now that the pictures you see of actresses and models in magazines have been doctored beyond belief. After the initial photo shoot, retouchers quickly work their magic with thigh chub resizing (only in Photoshop do women not have cellulite), wrinkle reducing, and skin spot removing.

One of the worst-kept secrets in the tech world is Apple's plans for consumer-grade AR smartglasses, still unconfirmed publicly and only recently corroborated through a leaked account of an internal employee meeting.

Location services provider Mapbox is expanding the reach of its augmented reality development capabilities to include apps for automobiles as well as smartphone navigation.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Have you been noticing SpaceX and its launches lately? Ever imagined how it would feel to launch your own rocket into the sky? Well, imagine no longer!

The crime procedural show is the perhaps the most direct path to the average TV viewer's heart. Could the same hold true for augmented reality games?

The latest update to the Christie's app for iPhones and iPads extends its augmented reality capabilities to the famed private art collection of David and Peggy Rockefeller.

Augmented reality headsets with depth sensors, like the HoloLens, offer a much more immersive experience than the average smartphone at present, and one app demonstrates that in a uniquely entertaining fashion.

IKEA won't be alone among ARKit apps for visualizing home décor and improvements when iOS 11 arrives next week.

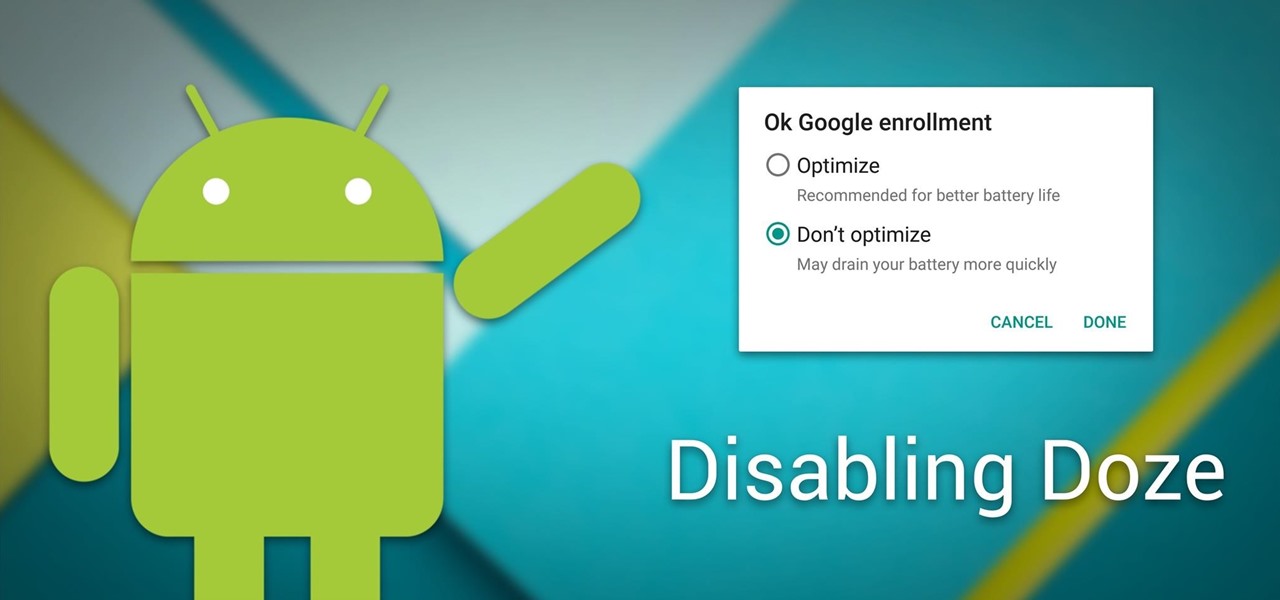
Android Marshmallow introduced a pair of new battery-saving features called Doze and App Standby, and according to the general consensus, both features are a rousing success. Average battery life has increased dramatically for virtually every phone or tablet running Android 6.0, so there's nothing to complain about here, right?

Five Phases of Hacking:- The five phases of Hacking are as follow:

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

bObsweep Standard and Pethair are made to easily transition between a variety of floor types, so they function efficiently in most spaces.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

For some homeowners, having a backup battery for their sump pump is important for making sure a loss of power doesn't cause a flood in the basement. And if you have yourself a standard new Basement Watchdog sump pump battery backup, before you can use it, you have to fill it up with the right amount of fluid. These batteries do not come with the fluid already inside, because it lessens the life of the battery. This video will show you the precautions and methods you should take in filling eac...

This video taxidermy tutorial shows how to make a wall mount sculpture of a white crappie fish. The initial fish is bedded into a soft clay mold, and then painted with fiberglass resin. When the mold hardens and dries, it can then be filled with whatever material desired to make the wall mount. Watch this instructional video and learn how to make a mold for a white crappie fish wall mount sculpture.

On Wednesday, as expected, Apple unveiled the next generation of iPhones, namely the iPhone XS and iPhone XS Max along with the more affordable iPhone XR, each equipped with a TrueDepth sensor.

A fresh batch of developer info has been revealed on Magic Leap's Creator Portal. On Thursday evening, the normally secretive company gave the general public perhaps the closest look yet at Magic Leap One's Lumin operating system.

With an eye toward future iPhone X-focused augmented reality functions, Apple's new investment in one of its components vendors will increase production capacity for the technology behind its TrueDepth camera, but could also apply to its future AR ambitions.

The staff at Next Reality News is legitimately excited about the prospects that Google's ARCore could bring not only to smartphones and tablets running Android, but also to Android-based hardware such as smartglasses.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Ever since the introduction of Google's SafetyNet feature, it's been an ongoing battle with apps trying to detect root access. For a while, there was a lot of back and forth between Magisk and certain apps. Pokémon GO was a high profile example of an app aggressively checking for anything related to root. Luckily, Magisk has made great strides to keep apps from detecting root for good.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

In about 27% of all car crashes, someone was using their cell phone. You may think texting is the big problem here, but many fail to realize that even the smallest smartphone interaction could spell disaster. Thankfully, Google Maps has rolled out an overdue feature that'll help ensure a safer drive.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

Excessive cell phone use was issue that Apple decided to tackle with iOS 12. Starting with the iPhone's 2018 update, a new "Screen Time" feature give you the ability to set App Limits to encourage more balanced usage, and there's another setting that gives you control over when certain apps can be accessed.

While there is a lot to be excited about when it comes to iOS 12 in general, iPhone X users will not just get the same new features and tweaks that all other iPhones will get — they'll get a few unique ones that will make the device even more desirable to those who don't have one yet. Also, iPhone XS, XS Max, and XR users will also see these benefits out of the box.

Now that ARCore is out of its developer preview, it's time to get cracking on building augmented reality apps for the supported selection of Android phones available. Since Google's ARCore 1.0 is fairly new, there's not a lot of information out there for developers yet — but we're about to alleviate that.

Peach trees and other related plants are susceptible to the devastation caused by fire blight, a contagious bacterial disease. Once contracted, infected trees have to be burned to contain the disease and prevent spread to nearby trees. Increasing resistance to antibiotic treatment has sent scientists in search of alternative ways to deal with the bacteria and prevent its catastrophic damage.

One of the big hurdles when equipping vehicles with sensors for autonomous driving is the cost. For example, the Light Detection and Ranging (LiDAR) sensors that power many versions of self-driving car technology are pricey, currently ranging from around several thousand dollars up to $85,000 per sensor—and vehicles often need multiple sensors to see enough of what is going on around them to drive safely.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.