Even with display sizes increasing by the year, smartphone screen real estate is still at a premium. We want the content we're viewing to take center stage, and this leaves little room for functionality beyond the focused app.
When Yahoo! purchased the home screen replacement app Aviate back in January, many were wondering if the internet giant intended to continue development of the launcher or if the transaction was just another acqui-hire.

Netflix releases monthly reports on major ISPs relating to how well their service works on each provider. The purpose is to educate the public on their choice of service provider, but since many of us hardly have any choice at all when is comes to an ISP, it backhandedly works to shame them (if they're even capable of feeling shame under all those millions of dollars).

As I begin my move across the country, I find myself dodging all kinds of Craigslist scams, particularly in the apartments and housing classifieds. Fortunately, I've discovered a little trick that will tip me off to a scam before I lose $1,000 in a fake security deposit.
Back in college, there were many instances where I'd have to meet up with a partner that I was randomly paired with in order to work on a project or to study for an exam. Besides the awkward interactions, the most difficult part was always figuring out where we would meet off-campus. I live here and they live there, so what's reasonably halfway?

With the the general computer users understanding of Information security rising (at least to the point of not clicking on unknown links), and operating system security getting better by default. We need to look for new and creative ways to gain a foothold in a system.

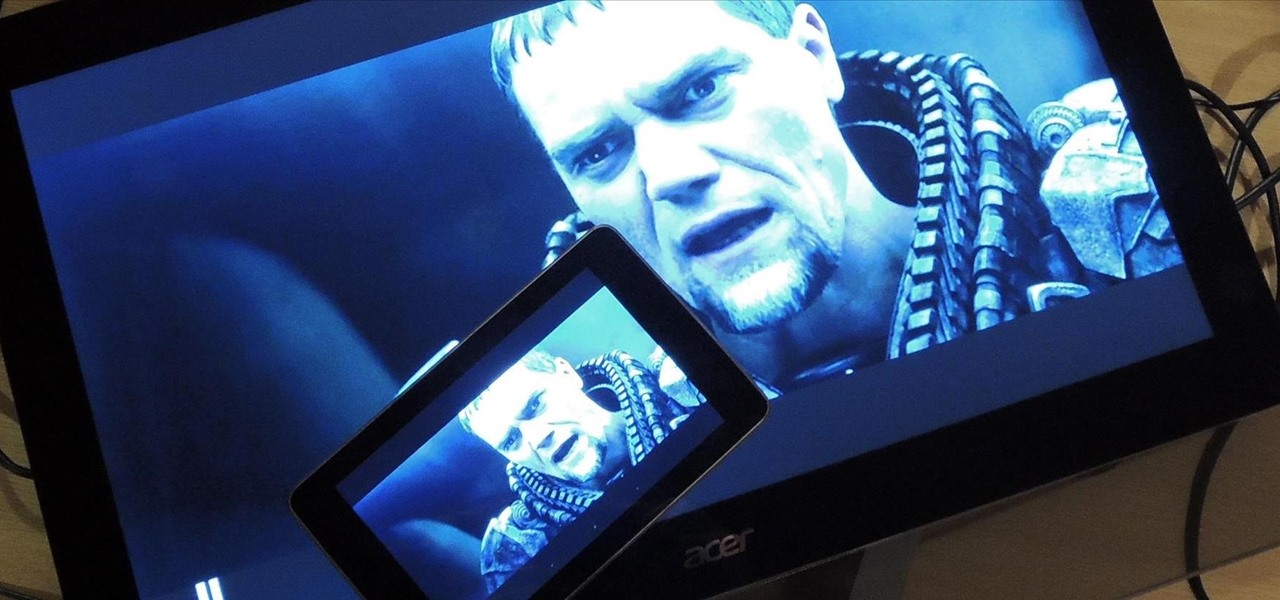
It's been a great week for Chromecast owners. First, Google released the development kit, allowing devs to install the casting code into their apps. Then, CyanogenMod dev Koush updated his AllCast app to support the Chromecast. That means you can shoot personal movies, music, and photos directly from your Android device over to a Chromecast-connected display.

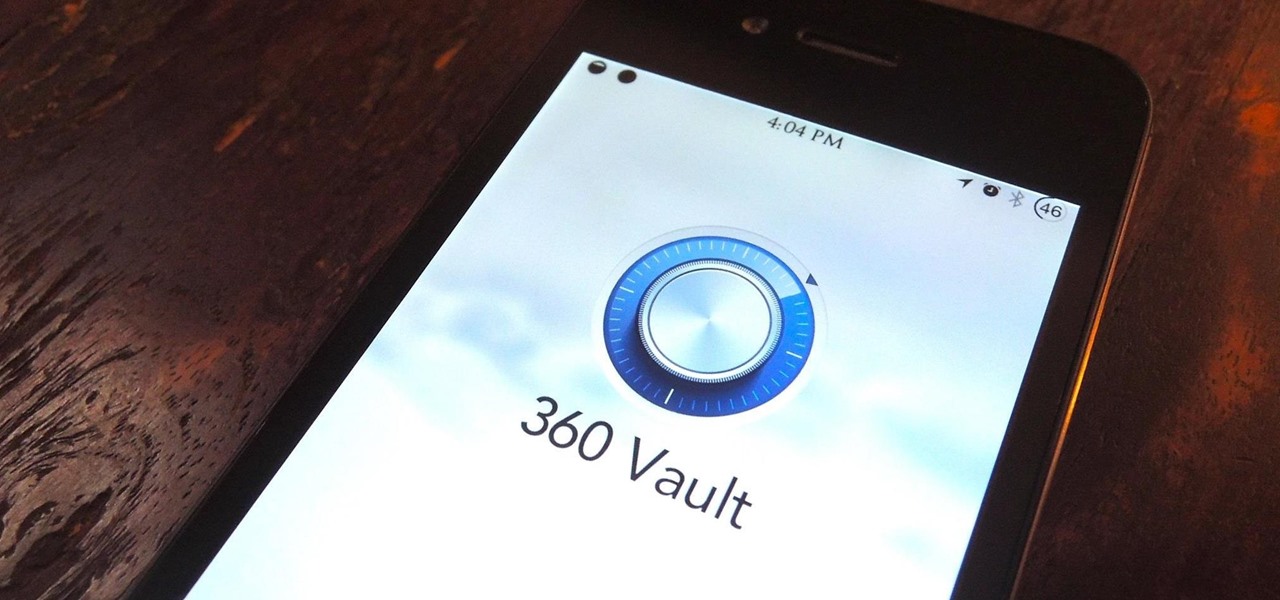
Let's be honest for a second; we all have sensitive material on our phones that we wouldn't want anyone else to ever see. Maybe it's to protect ourselves or someone else, or maybe it's none of your business why I don't want you to see pictures of my bachelor party. Regardless, sometimes we need to keep things hidden and safe.

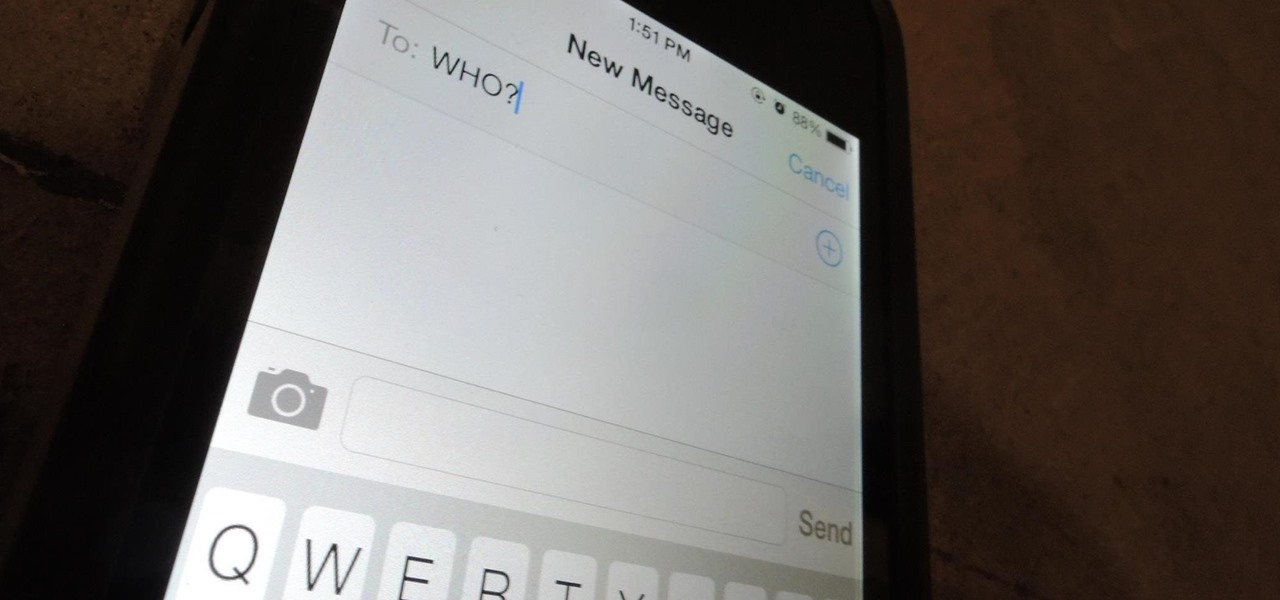
If you're a ladies man like me then this next tip could save you from sorely embarrassing yourself. Here's the problem: You think you are texting Kelly M from New Year's when you're actually texting Kelly F from that one bar. Needless to say this could cause a problem with your relationships.

Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time they want—without triggering the "camera on" light. Yeah, that means those Justin Bieber lip sync videos you recorded weren't just for your private collection.

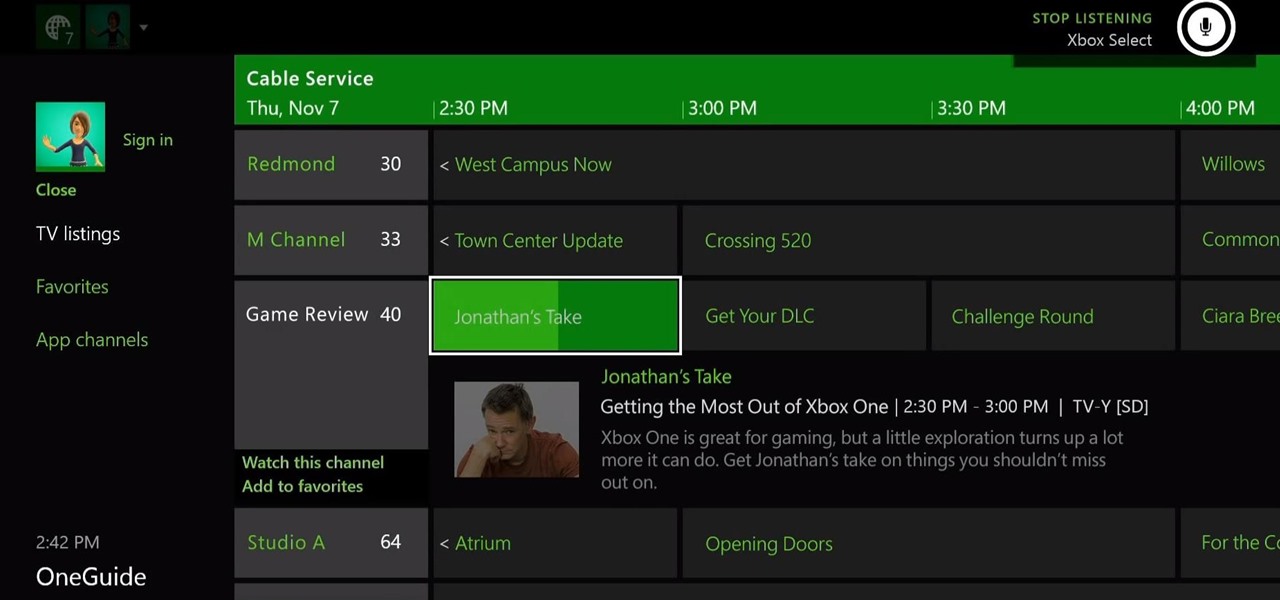
The Xbox One is the quintessential jack of all trades. It can be your browser, music player, gaming system, and cable box, but in order to benefit from all of these goodies, you're going to have to set it all up.

Don't be greedy, sharing is caring. If you have a brand new Xbox One, let some friends and family in on the action by getting a few extra controllers. You can connect up to eight controllers on one Xbox One console. Now that's a gamer party waiting to happen.

I'm still amazed by all the things some people just don't know. Script-kiddies often refer to Metasploit if someone asks them how to hack a computer because they think there's simply no other way. Well here I am today trying to increase your set of tools and -of course- skills.

Gaining remote access to a phone isn't only for super hackers and spies. There are plenty of times when the average smartphone user would want to have remote access to their device.

A lot of computers come with a ton of pre-installed software from the manufacturer, some of which you need and some of which you could most certainly live without. And over time, you may have downloaded and installed a bunch of programs and apps that you probably can't even remember. Now, you could go ahead and uninstall everything that you don't think you need, but then you run the risk of removing something that could really mess up the system. When I open up my Programs folder, I feel like...

A car is stolen every 33 seconds in the United States, and from that, the percentage of vehicles recovered in the first day is a whopping 52 percent. Over the next week, that number rises to around 79 percent, but after those initial seven days are up, it's unlikely the vehicle will be found.

There are a variety of ways to speed up your body’s ability to heal. Things like keeping the incision clean, resting, nutritious foods and physical therapy will get you feeling strong quickly. Avoid negativity, as it may actually slow down your recovery. No one likes to be laid up in bed after surgery. Follow the advice on your “get well soon” card and be back to your old self in no time.

In these instructional videos you’ll learn what to expect during typical Lomi Lomi massage session. Expert massage therapist Kelley Welch offers tips and advice on the benefits of Lomilomi treatment, where to find a qualified practitioner and how to prepare for your session. She also explains the philosophy of Lomi Lomi, the importance of breathing exercises and demonstrates massage techniques for different regions of the body.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

You don’t have to wait to get to the golf course to practice your strokes. You’re swing path and swing plane will improve by doing these exercise and ultimately leave you with a straighter hit. This drill can even be done inside.

Watch this instructional welding video to solve some basic problems you may run into with beginning MIG welding. This video provides tips and solutions to initial clogging issues. Set your voltage and wire feed speed correctly to avoid problems when beginning metal inert gas welding.

This video tutorial shows how to use a Roarockit Thin Air Press for teaching deckmaking. The glueup is done in one session. See how to build a skateboard with the Roarockit Thin Air Press!

Before starting a boxing training session it is important to wrap hands properly. A boxer's hands are useless if not properly cared for. Learn how to wrap hands in this boxing video tutorial.

Like every other instrument, drums need to be properly tuned in order to get a great tone. In this 3 part how to video,"Sarge" shows you how to do the initial tuning on a tom tom drum. Follow the steps in this tutorial and soon your drum will sound like a pro's.

Tom from Chi Town Custom Cornhole walks the DIY cornhole board builder through the steps to making a custom cornhole board. This how-to video features preparation and initial cuts.

In this math lesson you will learn how to graph linear inequalities. Let’s graph the following inequality: 4x + y > 4

In this math lesson you will learn about simple interest and compound interest. Whenever you want to borrow money from a bank, you have to pay interest at a certain percent rate. The main difference between compound and simple interest is the fact that the simple interest is paid only on the principal, while the compound interest is paid on both the principal and the accumulated interest The simple interest is given by the following formula:

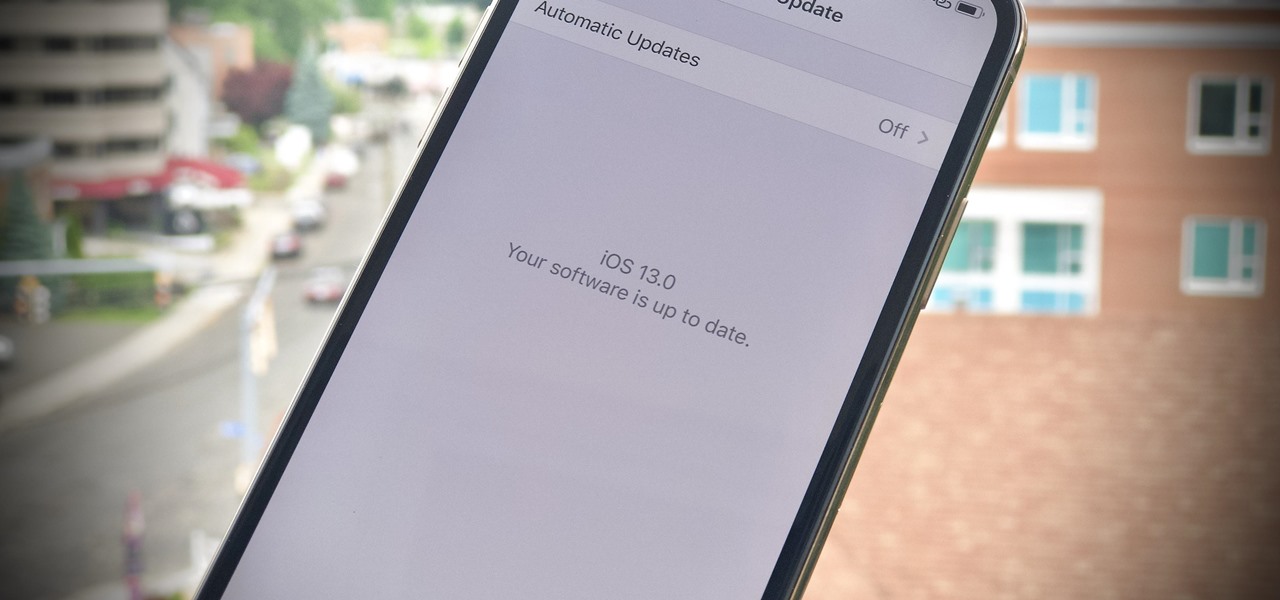
There's no doubt iOS 13 has dominated the talk around the Apple community this month. Since the announcement and release of the first developer beta, we iPhone users have had a treasure trove of new features and changes to explore and discuss. Now the fun continues with iOS 13 dev beta 2. Who's ready to start up the conversation all over again?

The first developer beta for iOS 13 is available to install on iPhone models, but the process for doing so may be a bumpy ride. Apple has not included configuration profiles for the developer beta yet, and many developers are having issues installing iOS 13 even with macOS 10.15 Catalina installed. Plus, since this is the first beta, there are a lot of problems with old and new features to work the kinks out of.

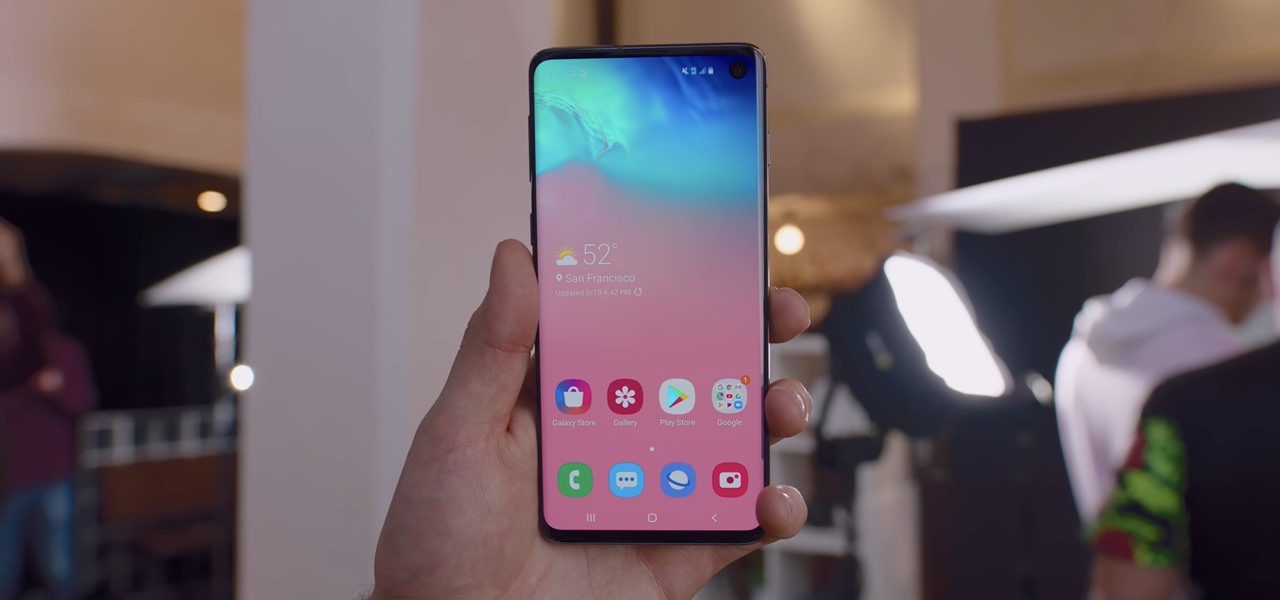
The Galaxy S10 has finally been revealed to the masses, and it certainly doesn't disappoint. As the flagship to herald the tenth anniversary of the venerable Galaxy S line, the S10 has kept popular and familiar design elements like the immersive Infinity Display while employing new features like more advanced cameras to set a new standard for other OEMs to follow.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

The holiday season is almost over, bringing the year to an end, and what better way to end it than with some tonsil hockey from the dime across the room on New Year's Eve?

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Safari's private browsing mode on your iPhone won't sync to other Apple devices or remember your search history, AutoFill data, or visited webpages. Still, it doesn't stop anyone who accesses your iPhone from opening your private tabs. If you don't want anyone snooping through your private tabs, use Chrome instead so you can lock the tabs behind biometric authentication.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

It's open season on Zoom, the video conferencing platform that has grown in popularity during the COVID-19 pandemic but has come under fire due to privacy issues.