The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

While Unity is already the leading 3D engine for augmented reality content in terms of volume, the announcement of Project MARS, a new augmented reality authoring tool, at Unite Berlin in June promised to expand AR development to a whole new audience of designers and other non-coders this fall.

When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can usually be solved by wiping the data of the device using TWRP. However, it can be more severe than that in some cases.

With barely a whisper of augmented reality during the first day of its developer's conference, Samsung came out swinging on day two with the introduction of its version of the AR cloud and a partnership with Wacom that turns Samsung's S-Pen into an augmented reality magic wand.

Magic Leap just did something it didn't do during its recent Twitch hardware demo: show us some new demo footage of what augmented reality really looks like through the Magic Leap One.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

Just days after we found out that Apple is working on its own augmented reality headset, we now learn that the company is accelerating its AR headset efforts with the acquisition of Montreal-based hardware maker Vrvana.

During Google Developer Days, taking place now at the ICE Congress Center in Krakow, Poland, an introductory session on ARCore provides some insights on how the platform operates.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

Verizon customers who use the Samsung Galaxy S7, beware: a recent update installs new bloatware over your existing bloatware that installs new bloatware. Confused or pissed off? You should be, as this app can install new apps onto your phone without you knowing.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

I'm lucky enough to have internet access on my laptop practically everywhere I go because of my mobile hotspot plan. All I have to do is enable the personal hotspot feature from my iPhone and I can surf the web on any Wi-Fi enabled device. But of course, there's a catch.

Brought to you by Berocca® Video: .

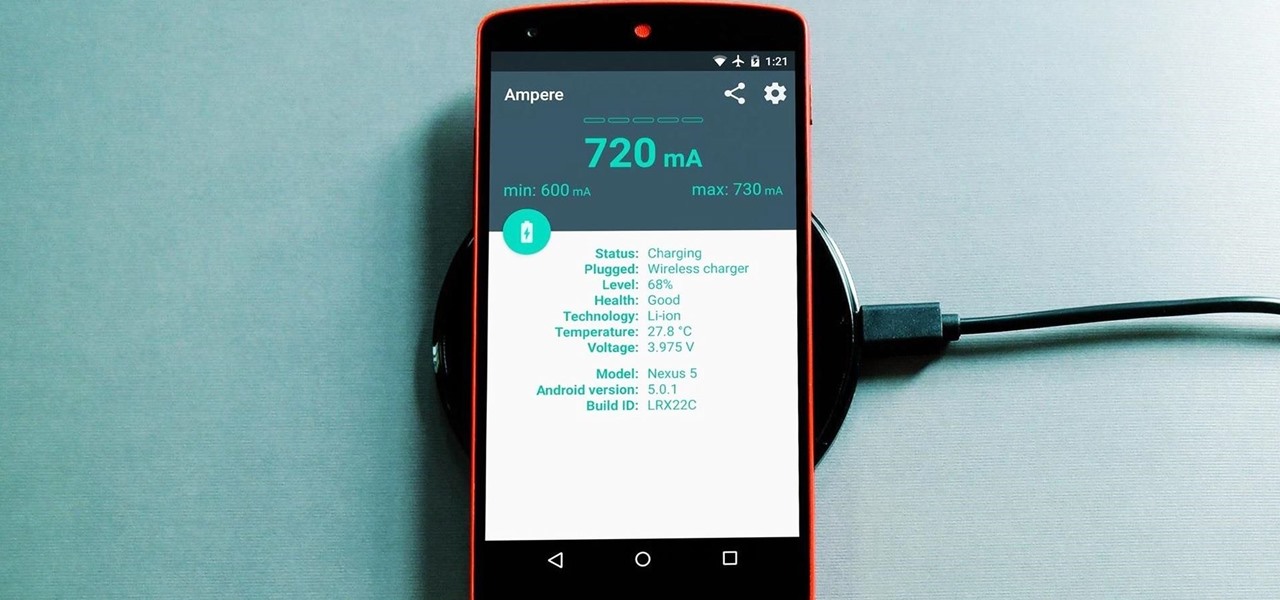
Not all smartphone chargers put out the same amount of current. The adapter in your car probably charges your phone a lot slower than the one plugged in at your bedside, and if you use wireless charging, it may be a bit slower still.

I've already showed you how to magically unlock your Samsung Galaxy S3 with the simple wave of a hand, but why stop there? Sure, you could go out and purchase a Samsung Galaxy S4 so you have Air Gestures that let you control the lock screen, SMS, sound, wireless, and more.

For the last three years, Apple has hosted its Worldwide Developers Conference at the San Jose Convention Center, but thanks to the COVID-19 pandemic, WWDC 2020 is now an online-only event. So what can you expect from the new virtual format and when and how can you watch the keynote and developer sessions?

It's not hard to let the new SARS-CoV-2 strain of coronavirus put pressure on our minds. Fear of catching COVID-19 is never far from the topic of conversation. But it doesn't have to be that way. If you're struggling with anxiety, stress, depression, or any negative emotions due to the virus's effect on our lives right now, you might find some solace in meditation.

Procrastination is an ugly beast. At first, it seems so innocent to spend five minutes checking Reddit or Twitter. You'll get started on work right after. Next thing you know, it's 1 a.m. and that paper is due in seven hours. Before you start another YouTube video, know you don't have to be like Spongebob. You can be like me, taking control of your productivity with the right app.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

Urgot is a unique champion who can deal out high amounts of damage early in his game, and eventually evolves into a tank/assassin hybrid who can be sent after important enemy targets. Here's a guide for building and leveling Urgot to take advantage of his capabilities to help your whole team.

Galio's strength on the Fields of Justice comes from his ability to tank, though he can provide a bit of team support as well. This guide goes over his strengths, and gives good advice when it comes to making an optimum build for the Sentinel's Sorrow for your next League of Legends game.

Vladimir the Crimson Reaper makes a good champion when you want a tank/caster hybrid. When he casts, he draws on health. His health and ability points are also symbiotic, improving one as the other goes up. Here are few tips on runes, masteries and strategy to make Vladimir a terror in battle.

A brief neurologic examination includes six sections: 1) mental status exam, 2) testing cranial nerves, 3) sensation exam, 4) testing strength, 5) deep tendon reflexes exam, and 6) coordination exam. Eve Bargmann, M.D., shows doctors how to perform this neurological examination on a patient. You will need to do a full neuralgic exam (not in video) if any abnormalities are found. But this is just a brief screening exam during a general physical exam.

Eve Bargmann, M.D., will teach doctors in this video how to perform an examination of the patient's heart and blood vessels. As with any examination, you should start out with inspection. Start off with the jugular venous pulse, then examine the heart by palpation and auscultation with bell and diaphragm of the stethoscope, and lastly examine the blood vessels.

In this video, doctors can learn how to perform a full cardiac examination on a patient. The very first thing a doctor should do is visually inspect the patient, because there's a lot that can be gained by simply examining by eye. You'll want to carefully examine the respiratory pattern of the patient, the nature of their precordium, the anterior part of their chest over the heart. Feeling the pulse is also necessary when starting out this heart exam. To learn more, watch the full video.

This week: a rigged game of skill & a simple sucker bet! Check out this video if you want to learn how to beat anyone in a simple game that can be played anywhere with coins and a napkin. Some might call it magic, others call it skill.

Jordon Schranz brings you this tutorial on drawing. Search WonderHowTo for Sessions Online School of Fine Arts for more drawing tutorials. The technique & craft of drawing isn't necessarily about inherent talent, it is something that comes with lots of practice. It is all about being able to accurately record what you see.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

On March 13, President Trump announced during a briefing in the Rose Garden that Google was building a COVID-19 screening website to help Americans understand if they might have the new coronavirus. If likely infected, the site would also include the location of a local drive-through testing site to visit. So how can you access the screening website?

Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.

The herpes simplex virus (HSV) can cause devastating complications for infected newborns whose mothers have genital herpes. Understanding risk and research can help you, and your baby, when the time comes.

Welcome back! Sorry for the dry spell, but I've been rather busy setting up some side projects! If you remember back to a few training sessions ago, we covered basic file I/O. This is a very important step in making our scripts applicable in a real life scenario, and today we're going to further these concepts.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

In the last iteration of how to train your python, we covered the concept of control flow and covered the booleans associated with it. Today, we'll be putting those to use as we discuss how to use if, else, and how to make conditional statements. So, Let's get started!

When it's most important for me to browse the web incognito, I always seem to forget to enable private browsing. If that sounds like you, it's time you stop making that mistake for good. Manually deleting the cache and browser history is a thing of the past, and as it turns out, so is manually switching to incognito mode.

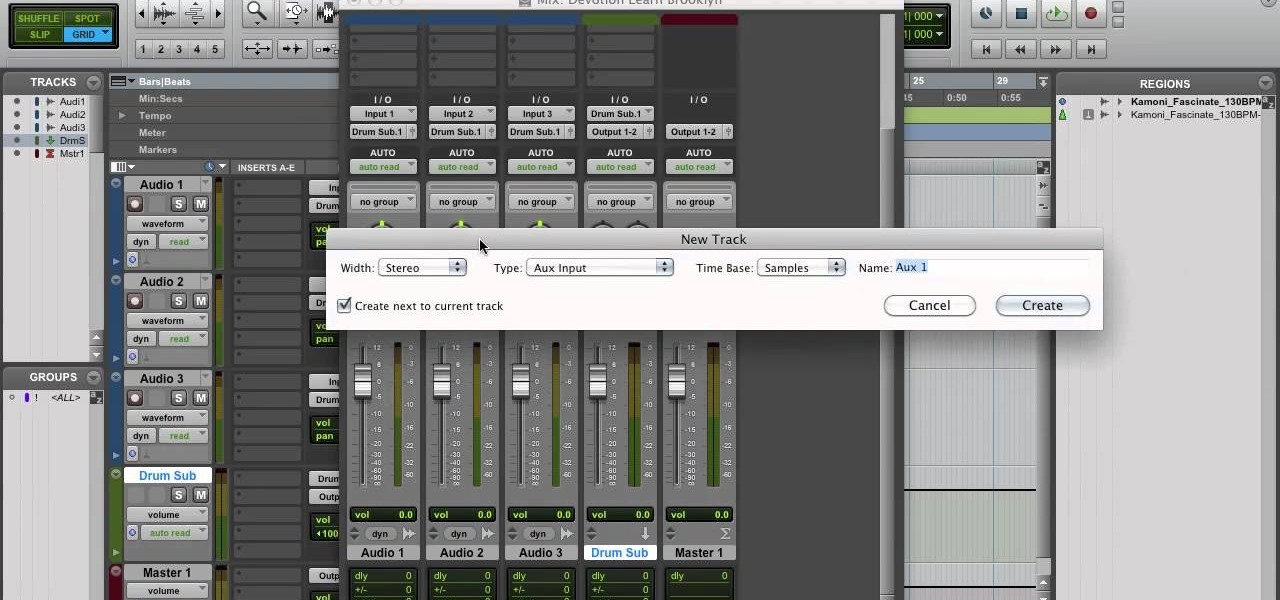
Move over Pro Tools LE— Pro Tools 9 is here! One of the most exciting things about Pro Tools 9 is that there's more tracks without having to have a Toolkit. Another great thing is being able to run Pro Tools without having to use Digidesign, M-Audio or any Avid hardware. Also, there's Delay Compensation Engine on a native system that doesn't require HD hardware or HD native. And this is just the beginning. To see more of the features in Pro Tools 9, watch this overview video.

Whether you're preparing for a thirty minute bout of interval running or for an intense weight lifting session, warming up is vital to building heat in your body so your joints are lubricated and there is less of a chance of injury. Warming up before exercising also boosts your metabolism so you get your heart rate up early and burn more calories during your workout.

Warwick is one of the champions your summoner can bring onto the Fields of Justice, whose speciality is jungling. This tutorial lays out the best items, glyphs and masteries to take advantage of his innate talents so you can ensure victory in your next League of Legends game.

Time to get started playing League of Legends! This recently released game is a completely free to play multiplayer online battle area game. Play a powerful summoner and pit your chosen champion against your oppnents and defend your tower! Here's an easy guide to getting started playing League of Legends.