Can't say we didn't see this coming — Apple released iOS 12 public beta 7 on Monday, August 20, the same day it seeded the ninth version of the beta to developers. While the two betas may have different names, public beta 7 and dev beta 9 are virtually identical, so public testers shouldn't feel as though they are missing out.

From day one, my favorite thing about the Magic Leap One has been its portability. It's so well designed that it just screams to be taken out for a walk through the city. Alas, Magic Leap says the device is (currently) designed to be used indoors, preferably in settings containing few windows or black surfaces.
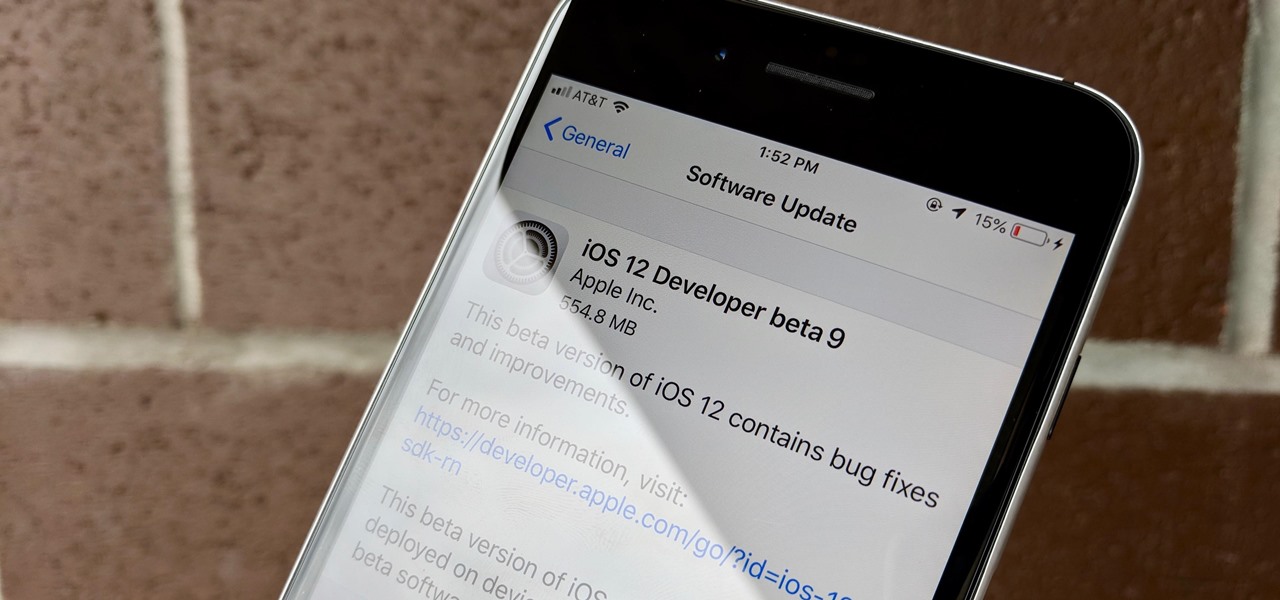
Apple released iOS 12 beta 9 to developers on Monday, August 20. The company seeded the update just five days after releasing dev beta 8 to testers, itself a quick replacement for the problematic beta 7. This update was followed closely by public beta 7, confirming Apple's new same-day release schedule for both developer and public betas.

By now, you already know that the Magic Leap One ships with an array of apps to immediately get you accustomed to operating in your new spatial computing reality. The first one we're going to focus on is Screens, an app we told you about previously, but only now have managed to try for ourselves.

UPDATE: The ported APK covered below is now obsolete because Fortnite beta is officially available for all Android devices!

If you're anything like me, when you first find a good song, album, or playlist on Spotify, your initial reaction may be to share it with your family and friends. While there are the usual share methods available in Spotify that are available in other streaming music services such as Apple Music and Google Play Music, Spotify goes one step further with QR-like codes users can easily scan.

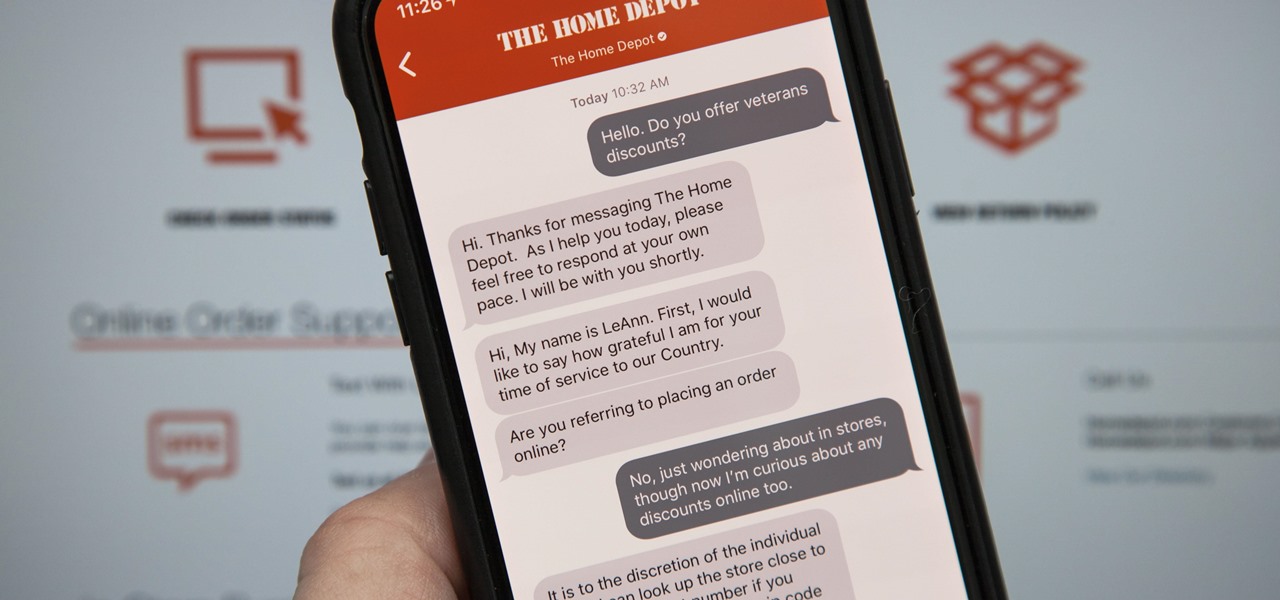
Apple first announced Business Chat, a new way for customers to communicate with companies, at WWDC 2017. While Business Chat did not arrive with the initial release of iOS 11, Apple pushed it out in iOS 11.3 so companies can offer customer service in a whole new way, and it works pretty much the same in iOS 12 and higher as it did back then.

Magic Leap's recent flurry of patent applications prompted us to look around for any trademark movements from the company, and it turns out that the Florida-based company has been quite busy.

For the unaware, RED is a company that specializes in high-end cameras and other recording devices. RED's cameras are used to shoot some of Hollywood's biggest films and TV shows. Their modular designs make them ideal for the user who does a lot of mixing and matching — and has a wallet to back their work up (their WEAPON 8K VV starts at $79,500).

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.

It's been nearly two months since Samsung kicked off the official Galaxy S8 beta program for Android Oreo. The Korean manufacturer recently announced that the beta is ending on January 15, so it's time to move on to the official build. Today, an official (non-beta) build of Oreo for the S8 has leaked.

Augmented reality is beginning to leak out into the mainstream world. This is thanks, in part, to ARKit and ARCore. These releases turned the current smartphones owned by millions of Apple and Android users into AR-capable machines. And while there are definitely some awesome use cases for mobile AR, the real future in AR is headworn.

While Animal Crossing's emphasis has always been on making friends with the animals that populate your world, each subsequent game following its initial release has stressed relationships with human players more and more. In Animal Crossing: Pocket Camp, making human friends is a crucial part of the process with the inclusion of market boxes, Shovelstrike Quarry, and giving "kudos."

Apple released the iOS 11.2 update for the iPhone to the masses early morning on Dec. 2, and here are all the new features and important bug fixes you need to know about.

Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, and now they have an official root method.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

The last quarter of 2017 brought us some downright excellent smartphones. Between the iPhone X, Pixel 2, and Note 8, consumers have more fantastic options than ever when choosing a new device. It's now the perfect opportunity for Samsung to set the tone for 2018 smartphones with their exceptional S9 and S9+.

Just when you thought Google Glass was dead, it turns out there may be a second life for the often ridiculed device that won't relegate it to the staid confines of factories and repair jobs.

There was a time when building a website required coding knowledge. Eventually, software came along that made the process easier, and then services like Squarespace made it dead simple for even a technical novice to design a website.

In this chapter, we want to start seeing some real progress in our dynamic user interface. To do that, we will have our newly crafted toolset from the previous chapter appear where we are looking when we are looking at an object. To accomplish this we will be using a very useful part of the C# language: delegates and events.

If competition in the augmented reality space was a spectator sport, then ARKit, ARCore, and HoloLens dominate the prime-time broadcasts on ESPN.

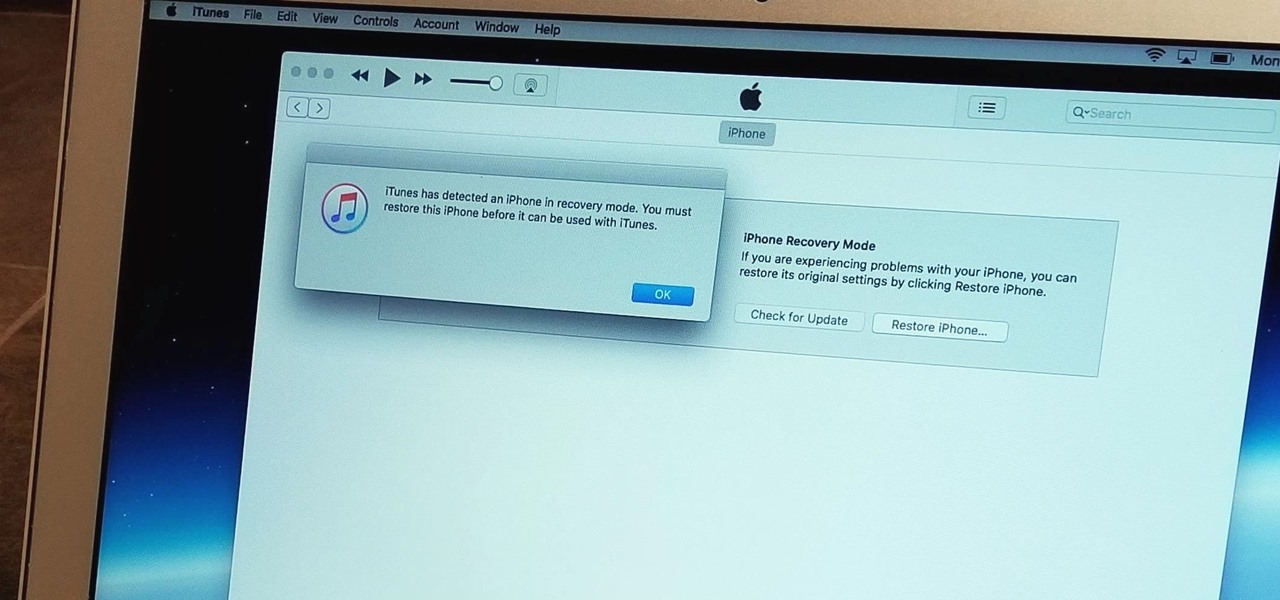
With the iPhone 8, 8 Plus, and the exclusive iPhone X, Apple has come full circle in transitioning its users away from the home button present since the first iPhone a decade ago. This gives us a window into Apple's design philosophy moving forward, but it also presents some new problems, especially when it comes to entering and exiting DFU mode in iTunes.

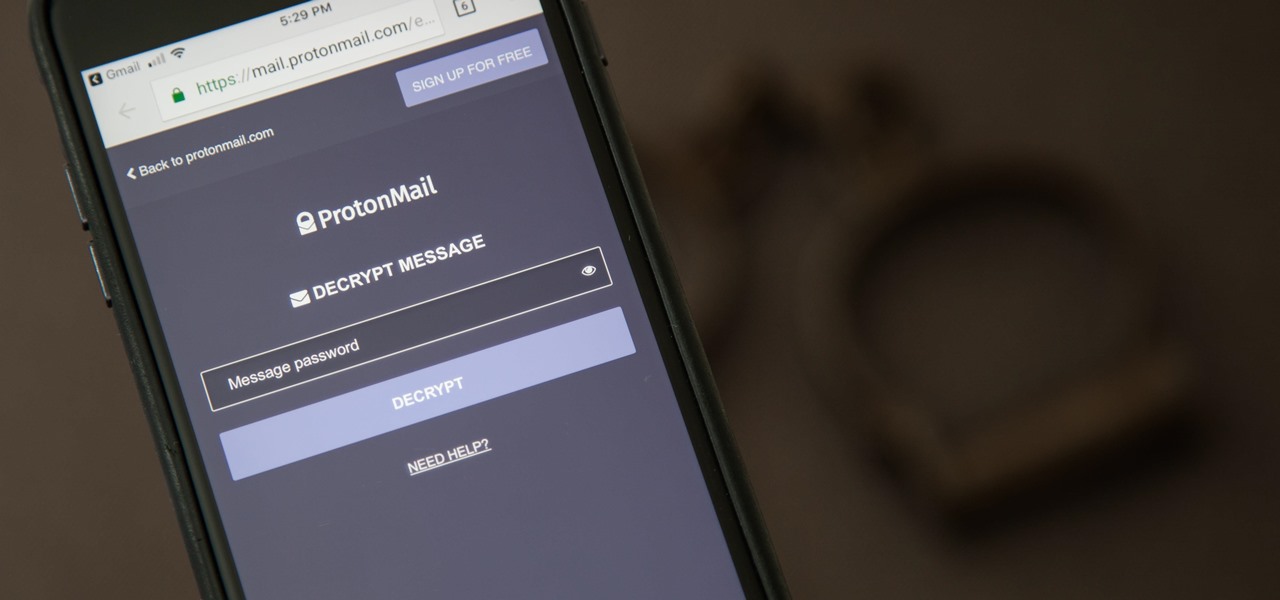
It can be hard to get all of your friends, family, coworkers, and acquaintances to jump on board with the more-secure email system ProtonMail, but that doesn't mean you can't still send them encrypted emails. Best of all, they won't even have to install any other apps or extensions to read or reply to the messages.

When Apple announced their ARKit platform in June, they immediately staked the claim to the largest augmented reality hardware platform, with millions of iPhones and iPads compatible with iOS 11 becoming AR devices this fall.

When the climate changes, so do all the things that rely on the climate, including people, plants, and pathogens. A European study recently took a broad look at what kind of microorganisms are most likely to be affected as climate change heats, cools, dries, and wets the world around us.

On the surface, iOS 10.2 might look the same as iOS 10.3, but there's one big difference between the two versions: iOS 10.2 can now be jailbroken! Jailbreaking your iPhone means gaining access to thousands of tweaks and mods which greatly enhance the iOS experience, so this is great news for the power users out there.

A recent study offers information that might help combat a deadly virus that affects an estimated 300,000 people each year in West Africa.

How can a drug used to treat cancer be effective against viruses, too? The answer lies in the drug's shared target — specifically, cellular components that control the activity of genes. A new research study showed that one such type of drug, histone methyltransferase inhibitors used in cancer clinical trials, has activity against herpes simplex virus, too.

For a company more associated with debugging computer programs, Google's parent company, Alphabet, is making a name for itself by taking on the real thing — mosquitoes.

Flu vaccines can help prevent us from getting or suffering the most severe effects of the flu. But, each vaccine only protects us from three different strains of the flu. If we don't have a vaccine against all types of flu, it leaves us open for an epidemic with a flu virus we didn't expect.

Malaria is a massive worldwide health problem. The Centers for Disease Control and Prevention estimate that 212 million cases of malaria occurred worldwide in 2015 and 429,000 of the infected people died.

Sex makes the world go 'round, and when it does, so does gonorrhea. Finally some good news on the growing menace of drug-resistant gonorrhea — a large, long-term study shows a vaccine may work in reducing the incidence of an increasingly dangerous infection.

The Raspberry Pi loads an operating system from whatever SD card you insert, allowing you to keep different operating systems on separate SD cards depending on which OS you wish to run. A tool called BerryBoot cuts down on the number of SD cards needed by providing the ability to boot multiple operating systems from a single SD card, similar to Boot Camp for Mac computers.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Seeing that wonderful blue verified badge on Twitter really adds something to your public persona, doesn't it? That's why, when I found out that the average person could get verified on Twitter with the right tools, I jumped on the chance to add that little blue check to my own personal account.

Move over whole wheat — white bread may be back in style after a new study shows that it may be your gut microbes that decide what kind of bread is best for you.

Ford's appointment of Jim Hackett as its new president and CEO reflects how the company is largely pinning its long-term survival hopes on its driverless business. Following his previous role as head of Ford's Smart Mobility division, which overseas Ford's autonomous driving activity, Hackett will help the company take a more self-driving direction as a whole.

Mixed reality display manufacturer Realfiction has developed a 64-inch display capable of delivering 3D holograms without a headset.

Water makes up about 60% of your body weight. Whether you like it plain, flavored, bubbly, or in beverages or food, we all need water daily to avoid dehydration and stay healthy. For communities in need of clean drinking water, new research using bacteria may offer a simplified, lower-cost method for boosting potable water supplies.

Pertussis, or whooping cough, is a highly contagious disease that can be life-threatening for young children. New research backs a recommendation that all pregnant women receive a pertussis booster with each pregnancy, as it can help their infants fight off the infection.