A continuation of my earlier science testing in Minecraft, I worked on a few things requested and retouched on TNT as there was suggestion of possible (and confirmed) altered circumstances.

The enterprise-focused category of augmented reality doesn't often get the headlines due to its relatively sedate profile as a mostly factory floor and training-based tool.

After facing delays due to the COVID-19 pandemic, the Olympic Games are underway in Tokyo, but a surge in cases worldwide has taken the spectator out of these spectator sports.

After receiving $100 million in funding in 2018, smartglasses maker Rokid is going the crowdfunding route to finance its latest product.

If you thought Snap's Spectacles were limited to a couple of demos, you haven't been paying attention.

The debut of the augmented reality version of Snap's Spectacles came with several examples of how the wearable can allow creators to transform the world around them.

Apple's Tapback is a great way to react to iMessages you find funny, surprising, confusing, and anything in between. However, in group chats, keeping track of who reacted with which Tapback can be difficult; iOS often just shows you how many people reacted but excludes many of the names. Luckily, there is a way around this — it's just a bit hidden.

During the Tuesday launch of Google I/O, the company's CEO, Sundar Pichai, pulled off a Steve Jobsian "one more thing" move near the end of his keynote address that was simply stunning.

HomePod and HomePod mini are excellent smart speakers if you're entrenched in the Apple ecosystem. They even offer ways to protect your sensitive information from friends and visitors who try to ask Siri to spill your secrets. But there's an extra layer of privacy you can put in place to make sure nobody gains access to any important notes, reminders, and calendar events.

After years of testing and modifications, the US Army is moving forward with its customized version of HoloLens 2 from Microsoft.

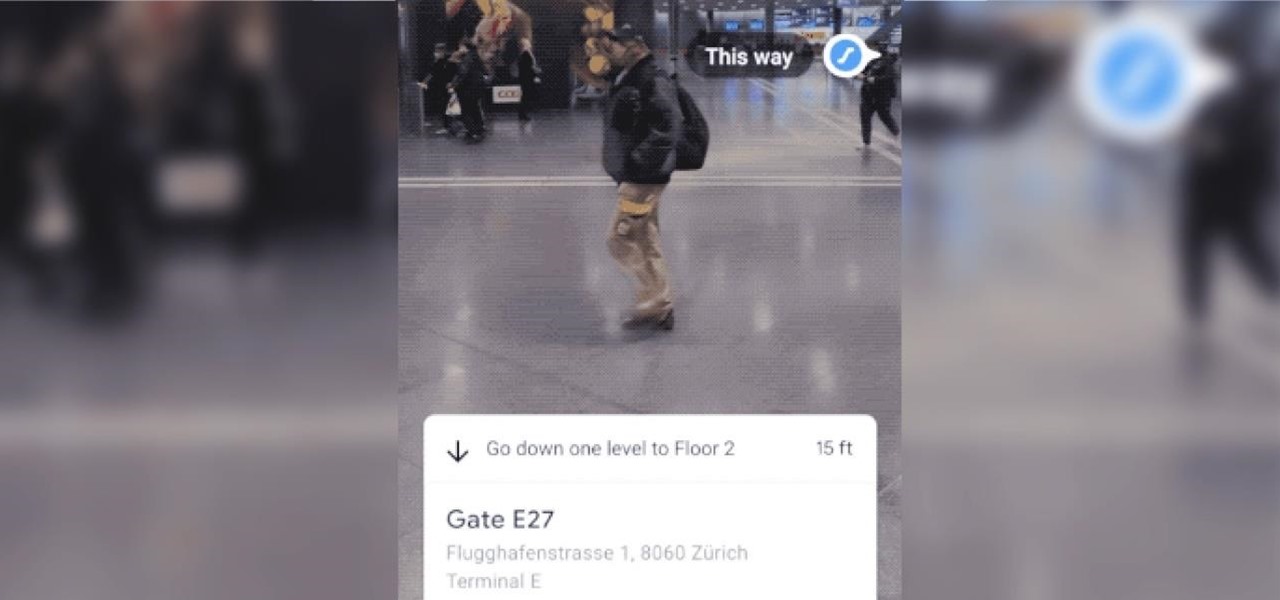
The AR walking navigation feature in Google Maps, which is arguably one of the most useful mobile augmented reality to available to consumers, is about to get even more indispensable for travelers.

With more digital content than ever, the search feature on smart TVs is essential. But typing is such a terrible experience when you're forced to use voice dictation or peck around with the remote control. Thankfully, there's a better way.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

For those not used to it, working from home can be a difficult transition. Everything around you can be a distraction, and distance from your boss and coworkers means less pressure and incentive to get things done. So it's not surprising to see a major drop in productivity during a period of self-quarantine, but your phone can help you stay on track instead of sidetracking you.

Up until Android 5.0 Lollipop, the actual text of incoming notifications would scroll by in your status bar. These ticker style alerts didn't pop on screen or interfere with what you were currently working on, but you could still read the message. They were replaced by the new "heads up" alerts, but you can still bring them back.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

This week's Magic Leap Lumin OS update contained a number of goodies, including iris authentication, and a way to stream to Twitch from the device.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Indian startup Dimension NXG is launching augmented reality headsets into India's consumer market with a bold idea: focusing on immersive computing in education on the high-end. The plan is to give a new kind of AR headset to schoolchildren in remote Indian villages, starting from class 5 (age 10) until graduation.

Many popular apps automatically share your personal data. While I have accepted a certain amount of data collection from Google, to know companies such as Facebook perform this without my consent bothers me. After some researching, I've found a great solution, and it doesn't require root.

In the technology space, there are certain brands you grow to depend on. Whether it's due to a long, multi-decade track record of success, or new innovations that blow you away, some tech names accrue a rare kind of brand equity with users that's difficult to earn.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

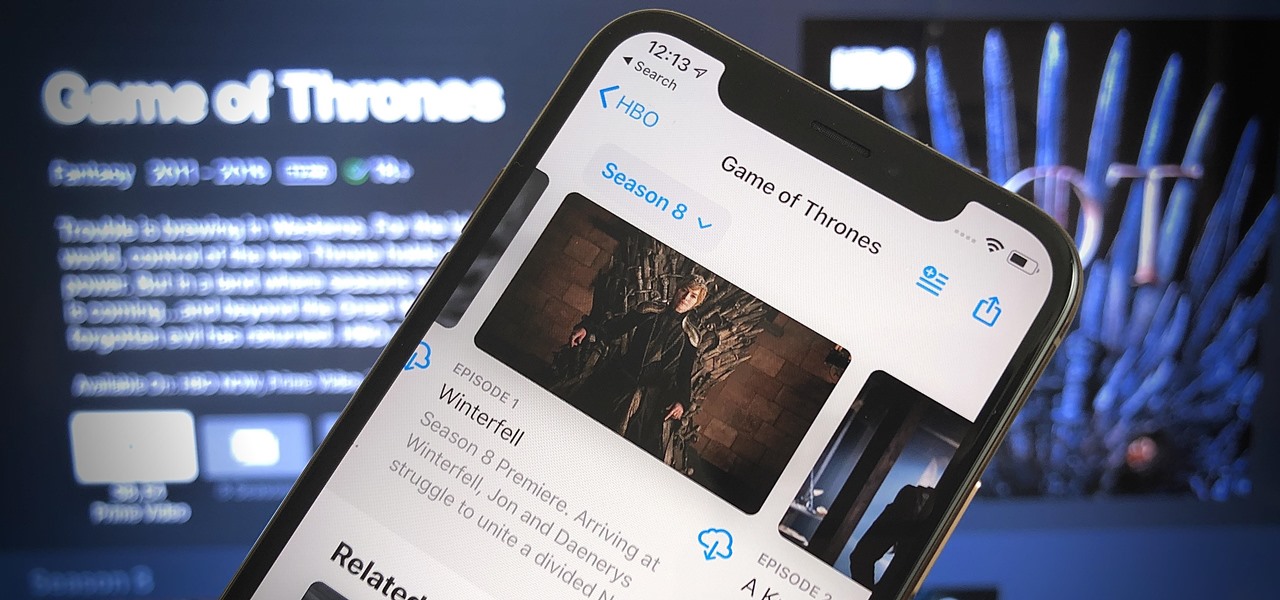
If you're a Game of Thrones fan and would like to watch the latest season offline on your iPhone, or if you need to catch up on previous seasons, there is no current support on HBO Go or HBO Now to download episodes for offline viewing. But that's only halfway true because there is a legal, official way to download HBO content on your iPhone, it's just not obvious at all.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

When it comes to rooting and modding any Android device, ADB and Fastboot commands will quickly become your two new best friends once you realize the power they have. From unlocking your bootloader to flashing any file you could ever want — if you're serious about the modding and customization game, you'll want to become acquainted with these commands as soon as possible.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Now that the dust has finally settled on Microsoft's big HoloLens 2 announcement, the company is circling back to offer more granular detail on some aspects of the device we still don't know about.

While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission.

Android 9.0 Pie moved the status bar clock from the right corner to the left to accommodate phones with notches, but there's one major downside for Samsung users: since no Galaxy phones have a notch, all this did was take away space for the notification icons that would otherwise start from the left corner.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

The main draw for Google's Pixel series is the software. It rocks a clean version of stock Android instead of a heavy OEM skin like TouchWiz, it gets frequent prompt OS updates, the camera software is downright amazing, and it has perhaps the most fluid UI of any phone. But an understated advantage of the software is how dead-simple it is to modify with root-level tweaks.

While the iPhone XS and XS Max come equipped with 4 GB of random access memory, and the iPhone XR with 3 GB of RAM, Apple's latest flagships are still susceptible to occasional slowdowns in performance in iOS 12. This can be fixed by clearing RAM, but the process is now a little trickier compared to iPhones with Home buttons.

If you've been getting that "Please update from the iOS 12 beta" alert continuously in iOS 12 public beta 9, Apple just issued a fix for it Friday, Aug. 31, with iOS 12 public beta 10 — just in time for Labor Day weekend. This marks the second update this week as dev beta 11 and public beta 9 were released on Monday. It's also just one day after Apple announced its Sept. 12 event.

In a surprise twist, Apple released iOS 12 public beta 8 to software testers on Thursday, Aug. 23, right alongside iOS 12 dev beta 10. The release comes as a bit of a shock, as the company released iOS 12 public beta 7 just three days earlier. The official build of iOS 12 now feels closer every day.

We're nearly there — Apple released the seventh iOS 12 beta to developers Monday, August 13. While not totally unexpected, beta testers understand the struggle of predicting the next update, as Apple has switched haphazardly between two-week, one-week, and irregular release schedules for both the developer and public betas.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

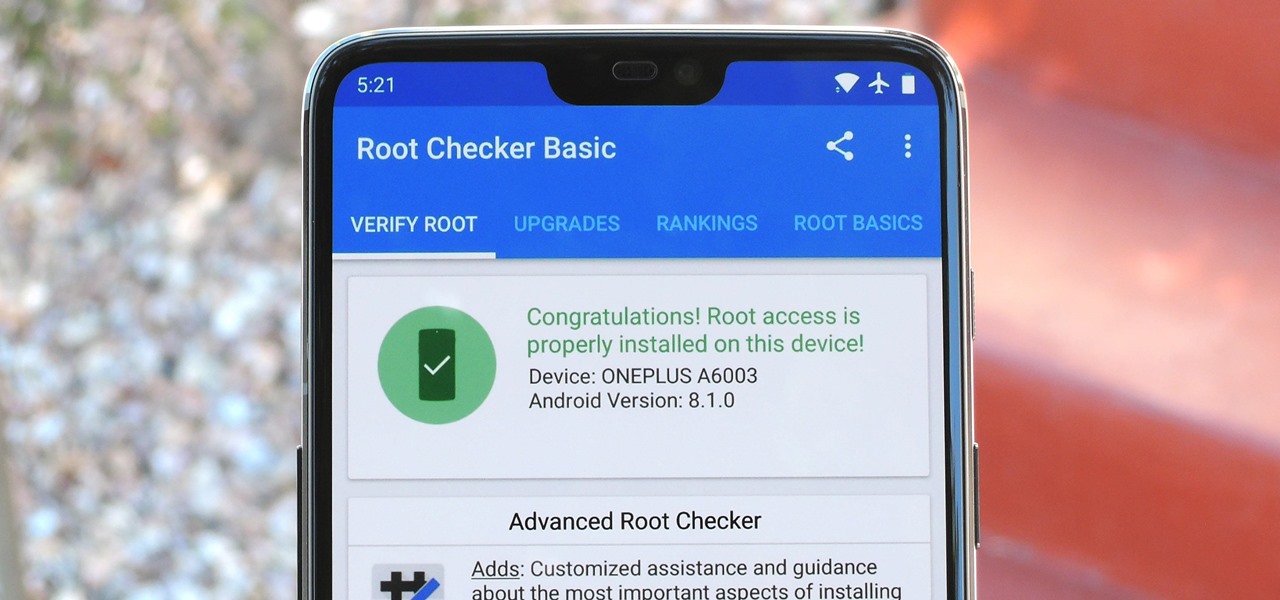
Year in and year out, OnePlus flagships top our list of the best phones for rooting. Why? Primarily because rooting does not void your warranty, and OnePlus goes out of their way to make the whole process as easy as possible.

Apple's goal with iOS 12 is to smooth out the problems with its famously flawed predecessor. Of course, change isn't for everyone, and by iOS 11.4.1, Apple had a pretty stable thing going. If you're not digging all the bugs and new features included in iOS 12, here's how to downgrade your iPhone back to iOS 11.4.1.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.