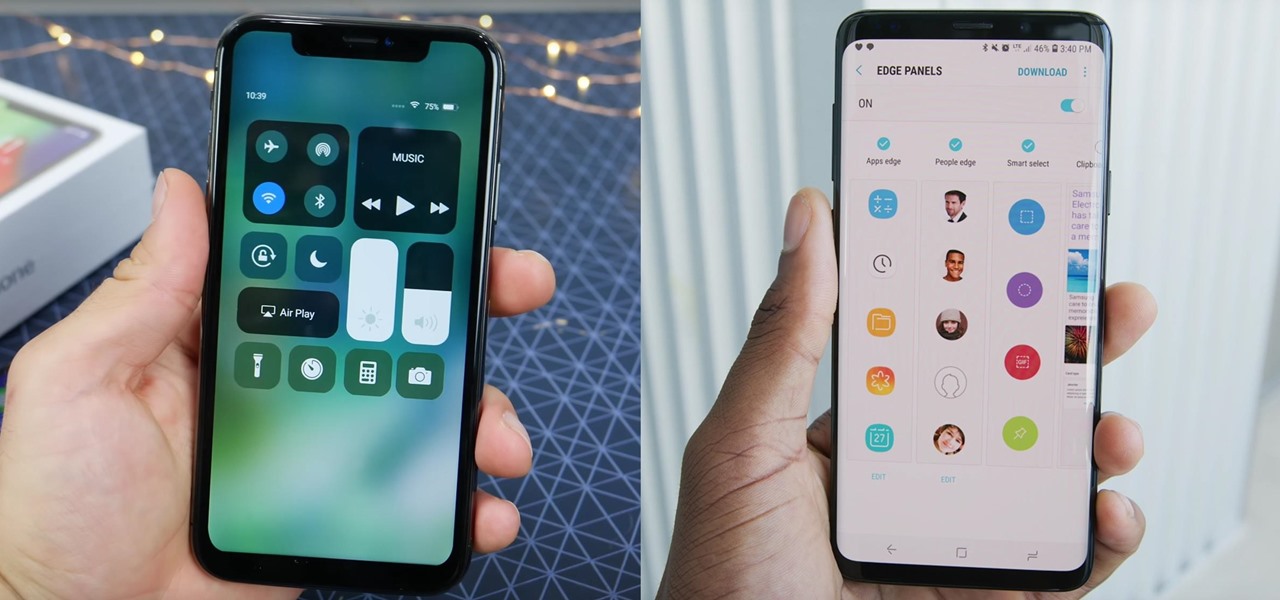
The wearables space experienced its "big bang" moment back in 2015 when Apple released its first wearable device, the Apple Watch. Although the device was initially dismissed by some as an unnecessary charm bracelet packed with frivolous tech, in very short order, the public learned just how useful the Apple Watch can be.

Are you here yet? When will you arrive? How long until you get here? How far are you? Hurry up! When you're meeting up with someone or a group of people, you may get flooded with messages like that. Instead of trying to answer them mid-trip, you can send them your status from Apple Maps, so they know precisely when you'll arrive, and they'll even get updates if traffic is holding you back.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Despite being at the helms of the RCS push, Google Fi has yet to support the new messaging protocol. It would've made too much sense if the Google-created MVNO was one of the first to support the feature Google's been pushing on other OEMs and carriers for years, but alas, they haven't. Well, better late than never — Google has finally announced support for RCS Universal Profile on Fi.
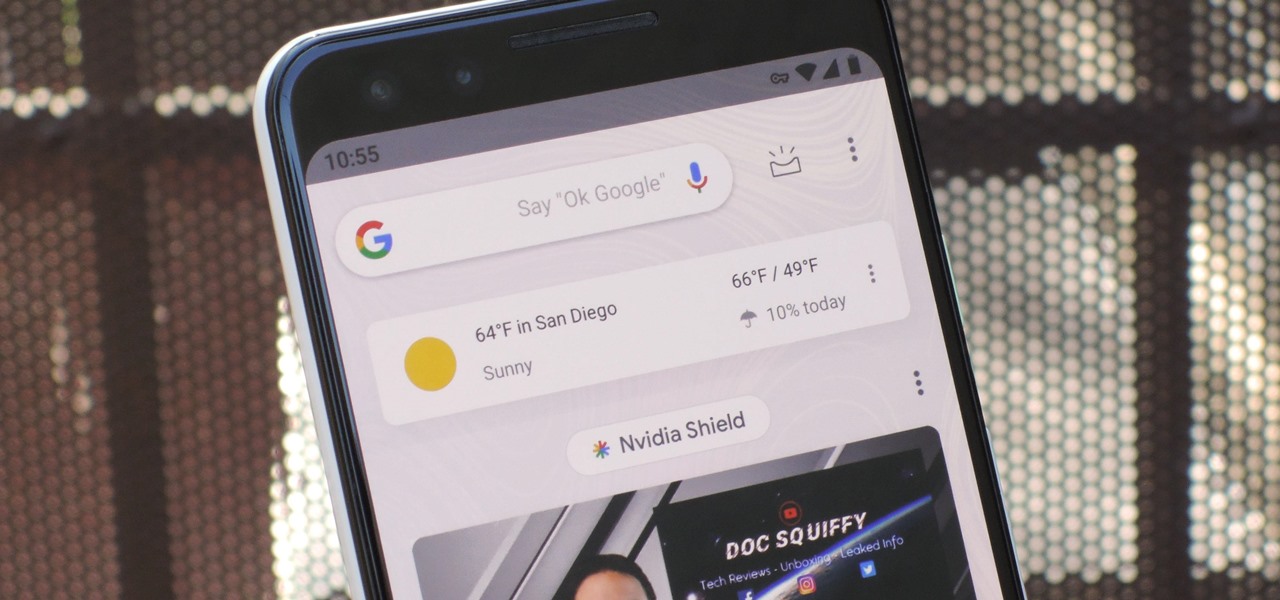
One of the most useful features of the Pixel Launcher is access to the Google Discover page. Initially, this feature was exclusive to Google's launchers, forcing users to give up the customization of apps like Action Launcher if they wanted the quick access to relevant news and updates it provided. Fortunately, this is no longer the case.

Even with all the success HMD had with reviving the Nokia brand in 2017, it seems their second year is shaping up to be even better. Nokia has been steadily releasing sequels to last year's lineup, most with the new minimal bezel design language. The Nokia 7.1 is just their latest creation.

The iPhone XR is the best bang for your buck option among the 2018 iPhones. Splitting the XR and XR Max right in the middle with screen size, it makes small compromises to to keep the price low. However, with the release of the Galaxy Note 9, Samsung has their own formidable middle option as well, the Galaxy S9+.

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.

For a while, YouTube Red original content was a joke, lagging behind other services like Netflix and Hulu in terms of quality, so breaking down the paywall didn't seem necessary. However, with series like Cobra Kai turning heads, it's a good time to start using Red. Luckily, Android users can get all of this content for free, and without rooting.

It doesn't matter how cool or groundbreaking a particular technology is, if it doesn't offer the promise of big returns on investments, you'll have trouble drawing interest from both Silicon Valley and Wall Street. That's why we're increasingly seeing existing augmented reality players doing everything they can to focus in on revenue generation, which was the message coming from Snap Inc. this week.

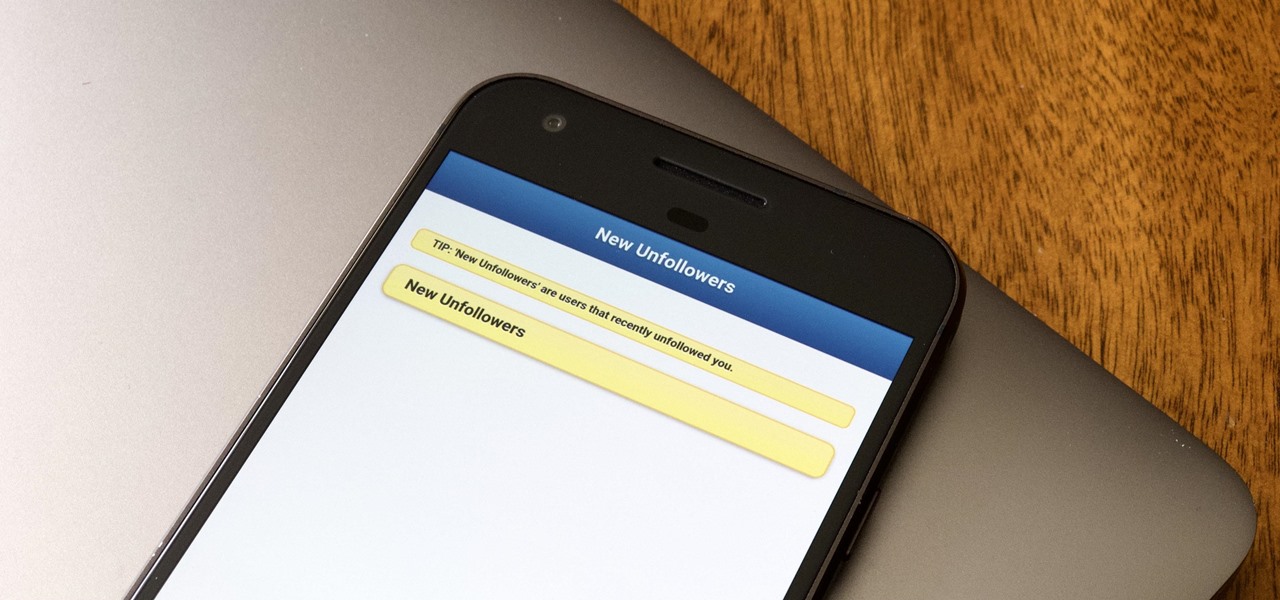
Followers are everything. After all, you need someone to listen to your tweets about last night's episode of your favorite TV show. But what about when people unfollow your account? Not only have you lost part of your follower base, you have no idea who left. Luckily, there are tools out there to help you learn just that, even if Twitter itself won't give up the info.

During Mobile World Congress 2018, OEMs started to introduce the world to Android Oreo (Go edition). Android Go offers smooth performance on entry-level specs, allowing for genuinely good cheap phones. At first, the US only had one Android Go device, but it looks like a second will join in the near future, the Nokia 1.

For the unaware, RED is a company that specializes in high-end cameras and other recording devices. RED's cameras are used to shoot some of Hollywood's biggest films and TV shows. Their modular designs make them ideal for the user who does a lot of mixing and matching — and has a wallet to back their work up (their WEAPON 8K VV starts at $79,500).

So, you want to install the Oreo beta on your Galaxy Note 8 but you're not sure if it's stable enough. It is a beta, of course, so waiting until others have tried it out sounds safer. Well, over the past five days, I've used the T-Mobile version as my daily driver and there are a plethora of new features, as well as a few glitches. Let's take a look at the bugs, performance, and battery life.

So you're thinking about downloading the Galaxy S8 Oreo beta, but you're not sure if it's stable enough to use. It is a beta, of course, so you might want to wait for others to give it a try. Over the past ten days I've used the Galaxy S8+ running Android Oreo as my daily driver, running down the best new features. Let's take a look at the bugs, the performance, and the battery life.

With four major carriers, buying an iPhone X or iPhone 8 can be more complicated than you'd think. While Apple has its own iPhone upgrade program, AT&T, Sprint, Verizon, and T-Mobile all have versions of their own. Which plan you choose depends on your needs and, of course, your carrier. However, getting around to upgrading can be challenging to say the least.

For as long as 14,000 years, the First Nations people of the Heitsuk Nation have made their home along the Central Coast of the Canadian province of British Columbia. Among the territory's inlets, islands, rivers, and valleys lie a clay deposit on the north side of Kisameet Bay, near King Island. For as long as most can remember, the tribe has used the clay as medicine. Now science says microbes that live in that clay may have important antibacterial properties.

Full disclosure — I have almost zero Street Fighter experience. The first time I played the game was at Barcade, way back in ... 2017. Yes, to the shame of gamers everywhere, this reviewer is a Street Fighter noob.

It is not just a bad summer for ticks — it has been a bad decade for the spread of tick-borne infections. New surveillance from the CDC reports rapid expansion and increase in cases of babesiosis, a sometimes life-threatening disease, in Wisconsin.

The Raspberry Pi loads an operating system from whatever SD card you insert, allowing you to keep different operating systems on separate SD cards depending on which OS you wish to run. A tool called BerryBoot cuts down on the number of SD cards needed by providing the ability to boot multiple operating systems from a single SD card, similar to Boot Camp for Mac computers.

A new dating app has arrived, and it'll finally land you a date with your celebrity crush ... kind of. The app — Dating AI — uses face search technology to help you search for potential love interests that resemble a celebrity you're attracted to.

The ability of one microbe to adapt is giving it a whole new career as a sexually transmitted disease. Usually content with the back of the throat and nose of those who carry it, the dangerous pathogen Neisseria meningitidis has adapted to cause an illness that looks a lot like gonorrhea.

Rumors that Apple is honing its automated car technology have skyrocketed. Thanks, now, in no small part to some enterprising members of the media who leaked the names of Apple's self-driving car team to the public.

In a disturbing turn of events, Uber has been tracking oblivious iPhone users even after they removed the application from their phone. Two years ago, the situation escalated to such an extent that CEO Travis Kalanick earned a slap on the wrist from Apple mogul Tim Cook.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

When we talk about driverless technology, the go-to companies are usually Waymo, Uber, or Tesla. However, traditional automakers like Ford and GM are also staking claims to the driverless and advanced driver assistance spaces.

A new study confirms that antibiotics can prevent surgical intervention if your child's appendix becomes inflamed, potentially saving his or her life.

As drug-resistant bacteria become more commonplace, researchers are looking for new antibacterial strategies to disrupt disease-causing microbes. Some scientists are working to create new drugs, while others are trying out drug combinations. Another group, however, are ditching pharmaceuticals altogether and experimenting with non-drug alternatives.

If you want to appreciate the value of microbes, look no further than a chunk of cheese. Because cheese roughly traces back to the Neolithic Era, we might say the earliest cheesemakers were the first humans to manipulate microbes—without even knowing it. Now, thanks to microbiologists and the long tradition of cheesemaking, we know a lot more about the microbes that make our favorite types of cheese possible.

Although their effectiveness is waning, antibiotics remain a front-line defense against many infections. However, new science reveals using the wrong antibiotic for an infection could makes things much worse.

After California college student Luis Ortiz blacked out and was taken to the hospital in 2015, doctors were startled to discover the reason his brain was swelling—a one-centimeter long, wriggling tapeworm living within a ventricle in the middle of his brain.

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

Maybe you decided to make your own pumpkin pureé because of all the buzz about canned pumpkin actually being squash (which, by the way, is a load of bull: it's made with ugly pumpkins, but pumpkins nonetheless). Or maybe you just wanted to be that person that proudly proclaims that they made everything from scratch for their Thanksgiving feast this year (ahem, me).

If you want to become a food Instagram star, you may want to consider having babies. Well, to be more specific, you might need Mike Chau's two adorable children, Matthew and Samantha.

While you can't turn art into a formula, the film industry has managed to come stupidly close. While many storytelling principles still stand across mediums, successfully crafting a compelling, immersive narrative in virtual reality requires a brand new rulebook. Through trial, error, and success, writer/director/editor Adam Cosco figured out the right rules to follow (and break) in "KNIVES"—his latest 360-degree short film. The film tells an old-fashioned tale of a woman, Kelsey Frye, strugg...

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

Making yogurt at home doesn't sound like an easy task at first. We initially saw it as detailed, hands-on, and precise—a process that required special equipment, specialized (and expensive) live-culture bacteria, and loads of yogurt knowledge.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.