Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

The headphone jack is becoming outdated technology in smartphones — that's what many manufacturers would have you believe. For the convenience of the audiophiles out there, we recently published our list of all phones that have removed the 3.5 mm jack. But what did each company gain inside their flagship phones by removing this supposedly antiquated port?

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

When shopping for a new smartphone, you'll encounter comparisons and spec sheets that are filled to the brim with values like mAh, GB, and GHz. To the average consumer, however, these values are meaningless, so we end up looking at which device has the specs with the highest actual numbers.

There is much to be learned about Apple Music and the revamped Music application introduced in iOS 8.4. Throwing their hat into an already competitive field with other companies like Spotify, Tidal, or Rdio, this is a bold move on Apple's part. So, before you consider signing up for the new streaming service, let's take you through all the changes and features you should know about before doing so.

Apple's newest mobile operating system, iOS 8, is out for the general public, and we've got a rundown on the best new features you can use on your iPad, iPhone, and iPod touch. While there's not a huge visual change as there was from iOS 6 to iOS 7, there's still plenty of cool new features in iOS 8 to be excited about.

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

Lidar, a technology first used by meteorologists and aerospace engineers and then adopted in self-driving vehicles, has slowly crept into consumer electronics over the last five years. If you have a Pro model iPhone or iPad, there's a good chance it has a lidar sensor, and you're likely using it whether you know it or not.

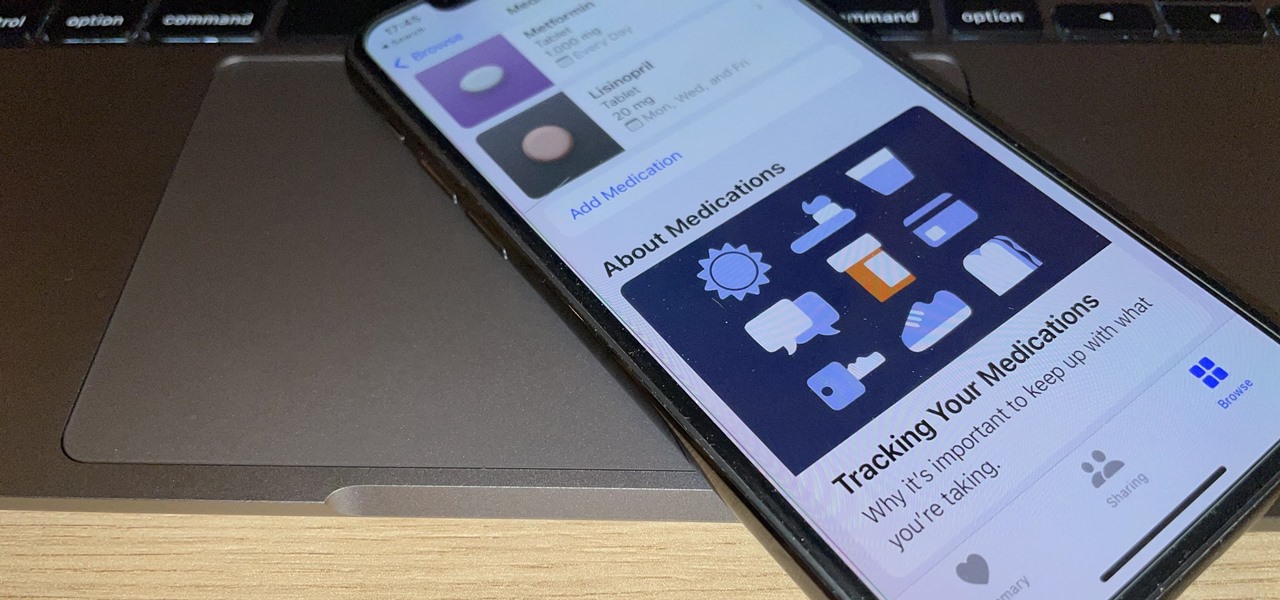
You've probably already been using iOS 16 on your iPhone for months, but there's a good chance you haven't found or explored everything the new software has to offer. Health-related features are usually the first to be ignored or go unnoticed, but they're essential to know about even if you don't plan on using them right away.

It's super easy to add filters, adjust levels, and crop images using the default photo editor on your smartphone, but there's rarely any built-in tool for removing the background in a photo. A third-party app can help isolate people and objects in your pictures, and we've found a free one that's easy to use, works with high-resolution images, and is available for Android, iOS, iPadOS, and the web.

Apple released the third developer beta for iOS 14.5 today, Tuesday, Mar. 2. The company promptly pulled the update from the developer portal, before finally making it available for all shortly after. The update was surprising to begin with, since Apple released it at an unusual time, and was only available as a download from the dev portal, without any OTA option.

Samsung's stock Galaxy Themes system leaves much to be desired with its restrictive and expensive theme packs. Back in the day, the gold standard for Android theming was CyanogenMod Theme Engine. And while it no longer exists, a successor has emerged to fill the void.

The Home button on an iPhone does a lot. That's not necessarily news for anyone who's ever owned an iPhone with a Home button, but what you might not know is that it's capable of so much beyond the standard everyday functions. So if you have an iPhone 7, 8, or the new SE model running iOS 13 or later, keep reading to learn about 17 secret Home button tricks you're missing out on.

Apple's scheduled to show off the first look of iOS 13 at WWDC 2019 on June 3, but what will the new operating system hold for iPhone? Rumors suggest that many features initially planned for iOS 12 will show up in iOS 13, codenamed "Yukon," and dark mode will be the big ticket item this year.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

You might think you need to buy a thousand dollar phone to get a great experience while streaming movies and TV shows from services like Netflix, Hulu, and YouTube, but that's just not true anymore. While phone prices keep rising and the midrange segment now ranges from $300–$500, there are still cost-effective options that come with top-notch displays and media features.

It is almost indisputable that smartglasses and head-worn displays are the future of augmented reality. However, at this precise moment, they are still a very niche market.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

I was in college, and my 15-inch Sony Vaio laptop was my prized possession. It was my first PC and probably the most important thing I brought with me to my dorm — it was both how I completed my assignments and my primary source of entertainment. How could it turn its back on me in my time of need?

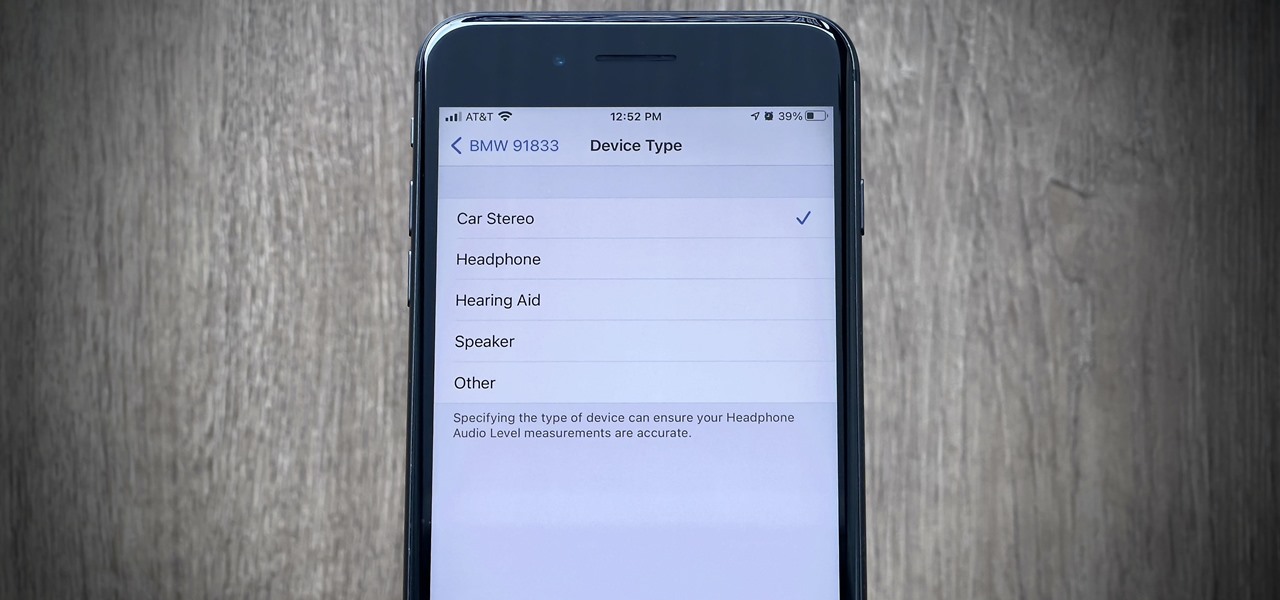
Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

While music may not technically be a "universe language," it is the one language listened to by all. There are over 1,500 music genres today—rap, classical, rock, jazz, trap, hip-hop, house, new wave, vaperwave, charred death, nintendocore... and the list goes on. And if you're like most people, you now probably listen to the majority of your music on your phone.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

My first encounter with a phablet was late last year with the AT&T version of the Samsung Galaxy Note 2, having never touched or even seen its highly-acclaimed and pioneering predecessor. Initially, I was a bit overwhelmed by the enormous screen and taken aback by the dated stylus, which brought up ugly memories of my dad using his ten pound PalmPilot.

Visual Voicemail revolutionized phone calls and the voicemail system when Apple introduced it with the original iPhone. Now, thanks to iOS 17, Apple has done it again with its newest calling feature, Live Voicemail. This feature uses speech-to-text technology to show you voicemail transcriptions on the incoming call screen in real time, helping you decide if it's important enough to answer the call.

Apple Notes has received many improvements over its lifetime, but noticeably absent year after year was the ability to easily add quick links in notes to other notes for reference. The latest software updates for iPhone, iPad, and Mac finally address this with a simple note-linking tool.

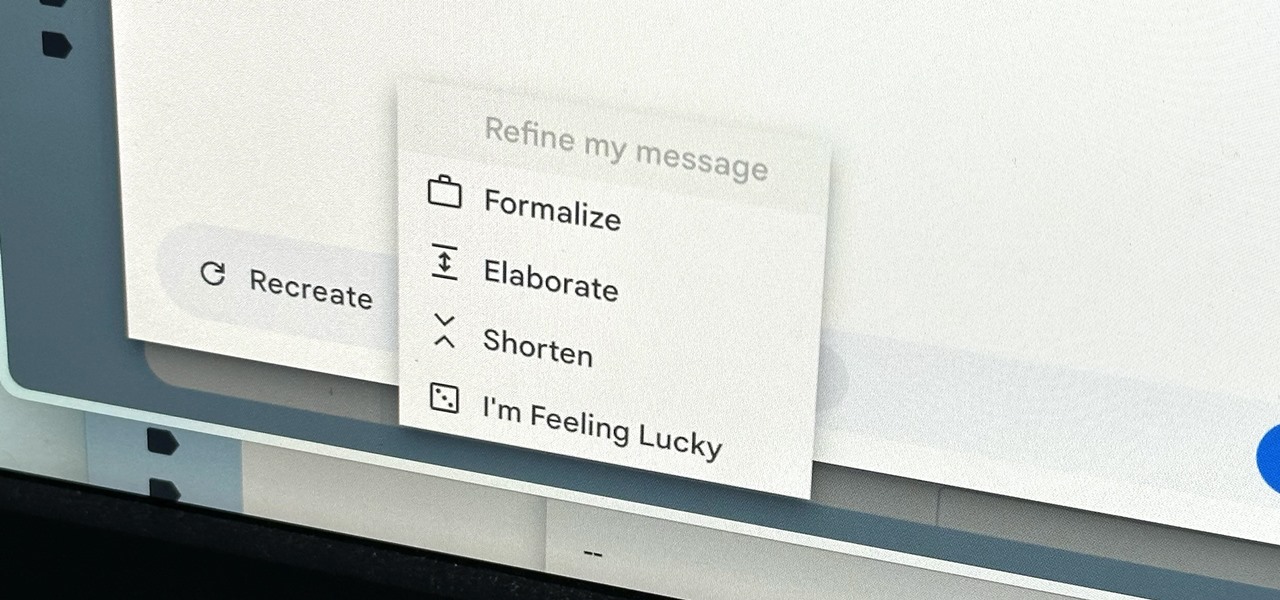
Thanks to rapid advancements in the field, generative AI can do some amazing things already, from generating text, images, and video with just a prompt to automating tasks and developing new products and services. Now, artificial intelligence can even help you craft emails directly in Gmail.

If you're tired of the default yellow link colors in your Notes app, which I find hard to look at in light mode, there's a way to change them to another color on your iPhone, iPad, and/or Mac running iOS 17, iPadOS 17, and/or macOS Sonoma 14 and earlier.

Outside of iPhone releases, software updates are arguably the most exciting aspects of iOS life. It's like Christmas morning when your iPhone installs an update, as you dive through your device to find all the new features and changes Apple thought to include. With iOS 14.4, there are at least 10 such new additions just waiting for you to explore.

You can't get the same gaming experience on your iPhone as you would on a PlayStation 5, Xbox Series X, or gaming computer. The processing power is less, the controls inadequate, and there are many on-screen distractions, all of which make mobile gaming less enjoyable. While you can't fix many of these issues, there is a way to prevent some problems, and that's thanks to Guided Access.

The moment arrives when you finally pop a shell on the web server you've been working on, only you find yourself in a strange environment with limited functionality. Restricted shells are often used as an additional line of defense and can be frustrating for an attacker to stumble upon. But with enough patience and persistence, it is possible to escape these restricted environments.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's literally over 100 ways to make iOS on your iPhone genuinely unique, some of which are hiding in plain sight.