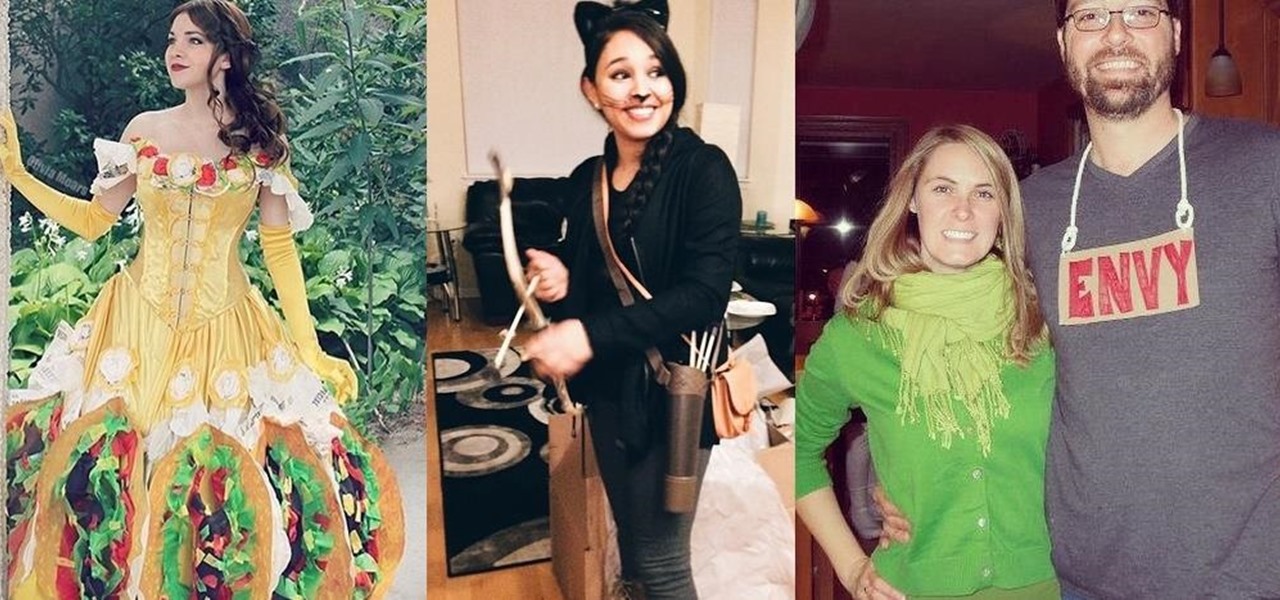Colorectal cancer — cancer of the colon or rectum — is the third most commonly diagnosed cancer in the US. To reduce the chances of a diagnosis we are all urged to stop smoking, keep our weight down, decrease our intake of alcohol and red meat, keep active, and get screened for colon cancer. But, new research has found something that participates in the development of colorectal cancer that might not be as easy to control: A strep bacteria that promotes tumor growth.

Even though HIV rates declined 18% between 2008 and 2014, 1.1 million people in the US are living with the infection. Part of that is because HIV is treatable, but not curable.
Nobody likes ads, especially when they're tailored to your browsing history like the promoted content posts on Twitter. These deceptive advertisements are injected into your feed, trying to hijack your attention with clickbaity headlines and distracting images. You most certainly don't need it, and I'm positive the Kardashians don't need any more publicity, they seem to be doing quite well.

Phase 2 of a Zika vaccine trial began in the United States this week, along with Central and South America.

A rose by any other name may smell as sweet, but one annoying invasive weed may hold the answer to treating the superbug MRSA. Researchers from Emory University have found that the red berries of the Brazilian peppertree contain a compound that turns off a gene vital to the drug-resistance process.

Tender is the name of the game when it comes to cooking damn delicious meat, but achieving that succulent texture isn't always easy.

Let's talk for a second about compound butter. No, scratch that, let's not. Because compound butters are too much work. You have to shape them and roll them and tie them and cut them... no thank you.

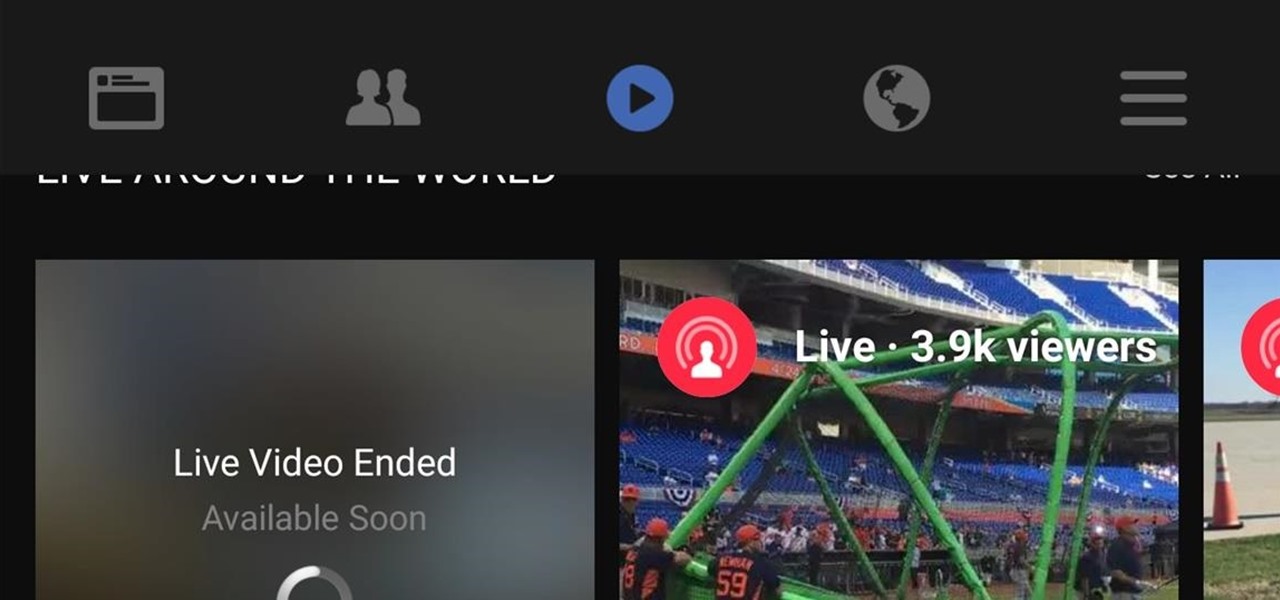
It looks like Facebook is adding a "Live" tab to the navigation bar for its Android app, and the feature has already been turned on for at least one user. A screenshot uploaded by Niko Steele shows the new feature, which lets you search for and watch live video directly on the Facebook app. Right now, you need to already be friends with a person who is streaming or be following a page or personality to receive a notification that live video has started. Some pages will post about an upcoming ...

Nintendo rolls out its first smartphone-specific game in the U.S. on March 21st, and the main protagonist is... you. Well, your Mii, and it's not a game, but a social app.

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1

When Lollipop was released, Android's lock screen got a huge makeover. But most of the changes were made for aesthetic purposes rather than functionality.

There are a number of ways to give your productivity a kicktstart, from taking a break from your distracting smartphone to just taking a break, plain and simple. Yet finding the motivation to start working doesn't require any effort at all—just a little bit of green.

In general, we never really put much thought into fonts, but they comprise a huge portion of our online experience. A whimsical mood can easily be set by using something like Segoe Script, but switch it up to Sentinel and you've got a more sophisticated feel all of a sudden.

Microsoft dropped a couple of huge bombs at their Windows 10 event Wednesday afternoon. Free operating systems and holographic glasses? This must be a Sci-Fi novel or a Hollywood blockbuster, because it reeks of fiction.

A shady practice in place by AT&T and Verizon Wireless—and possibly more wireless carriers—was recently uncovered. Outgoing data requests sent from devices on these service providers are being injected with a Unique Identifier Header (UIDH) that allows websites, the carriers, and potentially even government agencies to track your online activity.

Casting Angelina Jolie as Maleficent was a no-brainer on Disney's part. No one else could project beauty, elegance, and fear simultaneously just like the animated villain in Sleeping Beauty did. But what sets the character apart from other evil witches, or any other Disney character for that matter, is the sinister, yet gorgeous-looking horns and headdress. And with news that a Maleficent sequel is currently in the works, this will surely be a great Halloween costume this year.

Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.

Unlike other Android devices with soft keys, the LG G3 actually comes stocked with a few different styles, as well as the ability to adjust the button layout and combination. But while the customization options are great, the styles you can switch between don't add much flair or personality to your device.

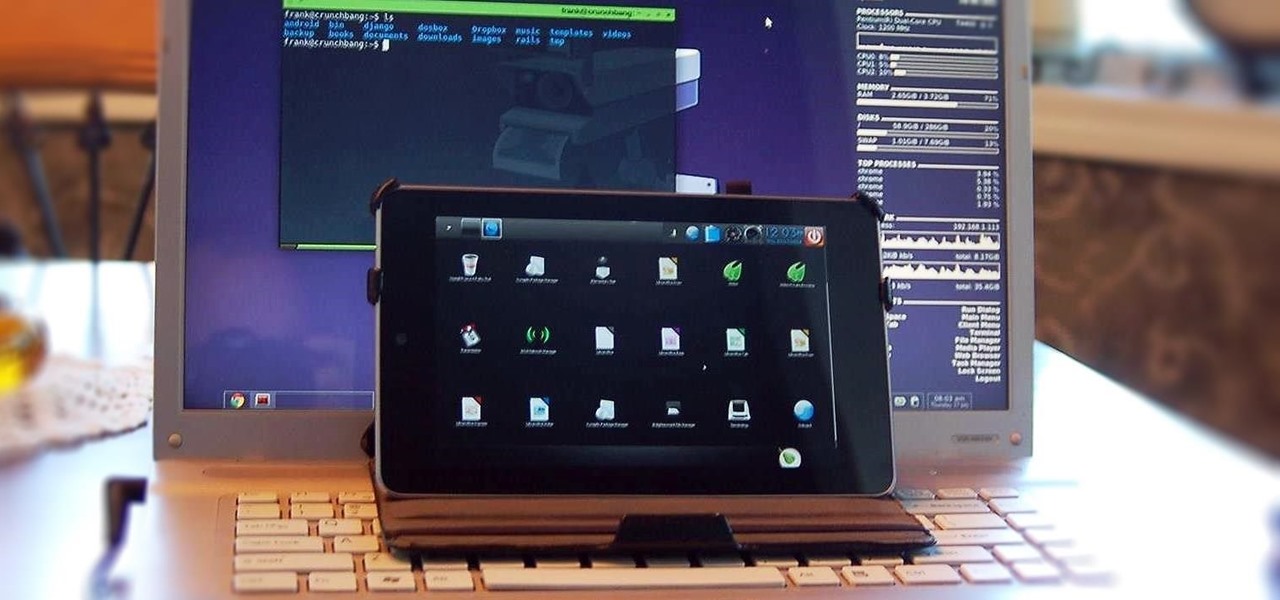
When people first learn that their Android device is capable of dual-booting different operating systems, e.g. Linux, they almost universally respond with, "That's so cool." And for those of us ambitious enough to actually try one out, we are typically filled with glee as we see Ubuntu, or something similar, boot up for the first time on our tablet or phone.

While AT&T and Verizon may not have had a chance to screw Note 2 owners with unrootbale devices—mainly because they've screwed us over by not issuing KitKat updates—it's safe to say that they can in the future. And while Sprint and T-Mobile subscribers have been able to root, the various methods can make the process somewhat confusing, especially for first-timers.

We've all walked into a restaurant with the best of intentions only to order something absurd, like a cheese-injected burger topped with bacon on a brioche bun. It's delicious for the few minutes it takes to eat the thing, and then you're left with a bellyful of regret and an inability to directly look at the numbers on your scale. Turns out that getting yourself to make healthy choices isn't as hard as one might think.

Whether you're on the john or sitting quietly on the bus to work, there's always time for a little video. And thanks to my favorite high school procrastination site, I'm going to be turning that little into a lot.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

In evolutionary times, we were far more likely to die from starvation than from diseases related to obesity. In those times, when food was available, it was best to stuff oneself.

Dianne Tice and Roy Baumeister gave a bunch of college students a questionnaire in which the students answered questions about their work habits. In a class which she taught, Tice also assigned a paper with a deadline which she said could be extended and observed which students availed themselves of the option to extend.

Assuming everyone knows of the recent "String of attacks" passed between Obama and Romney, I just want to talk about how useless this entire thing is. I'll try to be as un-biased as possible.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

Your desktop background image is feeling a little dull lately, huh? Fix that with some great background images for any sized computer screen. All you have to do is go to the website Desktop Nexus and find the one that fits your personality. This video shows you where to go and how to find your favorite backgrounds. All you do is search via the search bar on the site or browse around for cool backgrounds. Click "Enlarge" and it will scan you computer for the correct resolution, for the perfect...

This video will show you how to get rid of stretch mark scars and acne blemishes. Your treatment options depend on the type and severity of your scarring. One way to improve the appearance of a scar is through a collagen injection, given by your dermatologist. Corticosteroids can also be injected to a hypertrophic scar to flatten and soften the raised area. Another technique is laser treatment, which reduces redness and evens out the scar tissue. Skin surgery is used in severe cases to remove...

In this video, we learn how to draw a basic wolf using simple shapes. First, draw the head of the wolf looking down with it's mouth open. Next, draw two circles to show where the front and back feet will go. Next, draw the fur onto the animal, then draw in the fur. Next, draw in the details of the face and the paws as well. Take your time while you are drawing this and make sure to erase any unwanted lines are you are going along. Add in the fur to detail the wolf and give it more personality...

In this tutorial, we learn how to create a water garden arrangement. To start, have a box filled with foam and rocks, then place branches on the inside of the foam and rocks. Now, add in a few liatris branches at different sizes. Next, add in yellow daisies, green spider mums, foxtail ferns, ivy leaves, and any other plants and flowers you prefer. To give the arrangement a garden feel, make the plant out of order and make the plants and flowers at different levels and heights. Arrange the flo...

It's easy to learn to draw Pichu the Pokeman with this free tutorial! If you love this character and want to draw him, follow the lesson below and you'll have it down in a jiffy. Drawing Pichu is a lot of fun because this character has a lot of spunk and personality. Follow the guide and you'll know how to do the drawing, sketching, and coloring of this guy. When you know how to draw manga, you can have a lot of fun!

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

The big night is less than a week away, so how do you not have a costume yet?! In my world, Halloween is the night of all nights. It's the only day of the year when it's socially acceptable to dress and walk around like an insane person, eat too much sugar, and scare the hell out of total strangers. What's not to love?

It's that time of the year, y'all—when the air becomes crisp, the nights grow long, and people crave hearty, warm soups and stews. And of all the season's offerings, my hands-down favorite has to be chili: It's versatile, meaty, and above all else, it's damn easy to make. (Thank you, Lord, for the slow cooker. Amen.)

Nice people finish first—or is it last? Though you may have been told throughout your life that being kind pays off, there are some obvious advantages to getting mean. So whether you're driving towards a goal at work, or need to attack a task in your personal life, acting like a jerk just might help you get what you want.