Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

One Instagram creator's augmented reality homage to Disney's deep bench of animated characters has earned him fifteen minutes of fame.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.
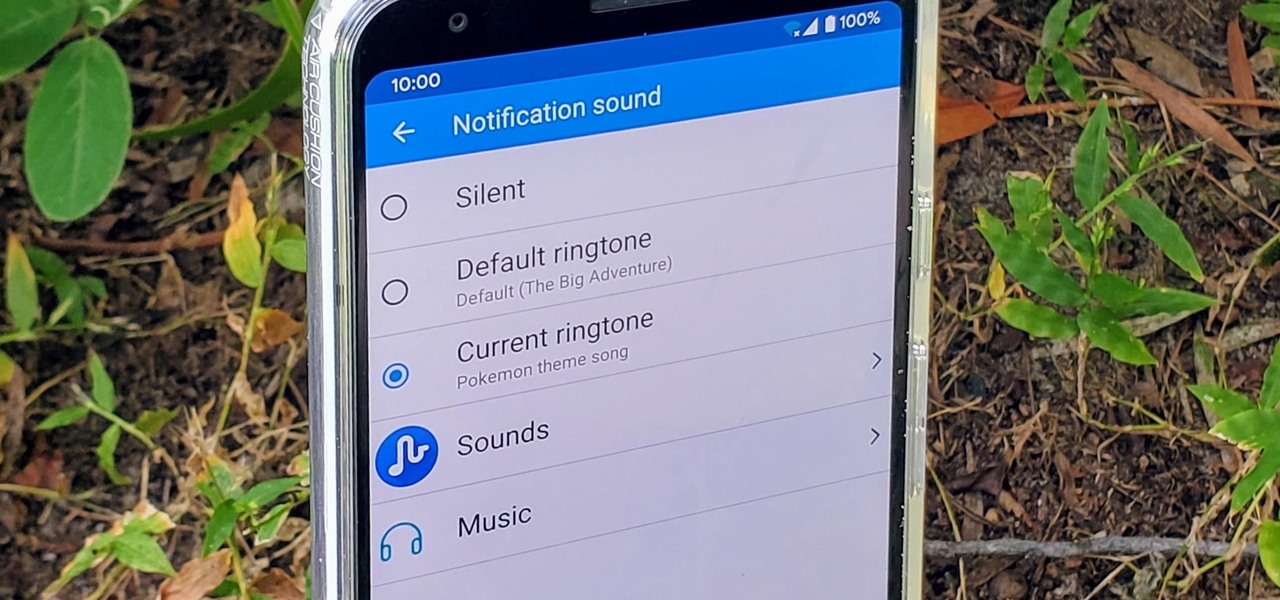
Have you ever walked around in public and heard the same handful of default ringtones over and over again? How do these people know who's calling without looking first? It's tough to tell when they all sound the same, but there is something crafty you can do to help with that. Using a different ringtone for certain contacts will allow you to differentiate between them instantly.
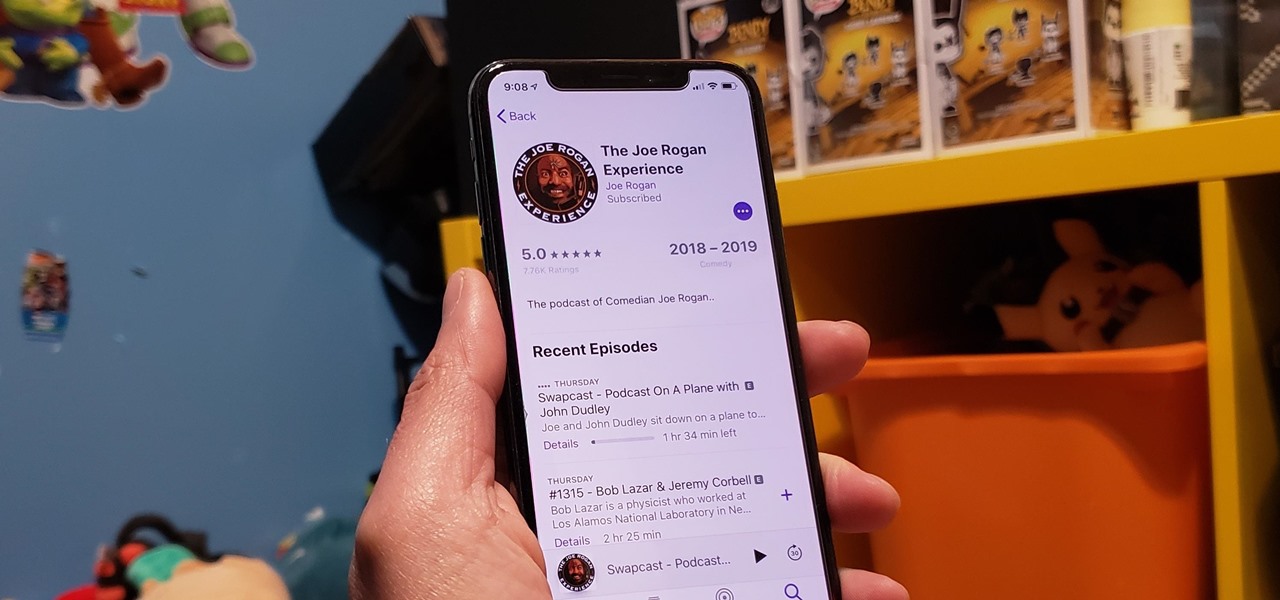
Ratings and reviews apply everywhere, from a restaurant you want to try to a new camera you're thinking of buying and games you might want to play. Podcasts are no different. Reading reviews of shows can help determine which are worth listening to, and your opinion is valuable to other people too. In Apple Podcasts, there are a few different ways to read, rate, and review shows.

While Google isn't ready to commit to a wide release of the AR walking navigation mode for Google Maps, the company has begun testing the feature with members of its Local Guides crowdsourcing community.

Your Instagram feed is jam-packed with interesting and lively photos, videos, and stories that largely offset the iOS app's comparatively bland user interface. If the interface's dull colors have always bothered you, you can splash on some much-needed color to better reflect your personality and tastes.

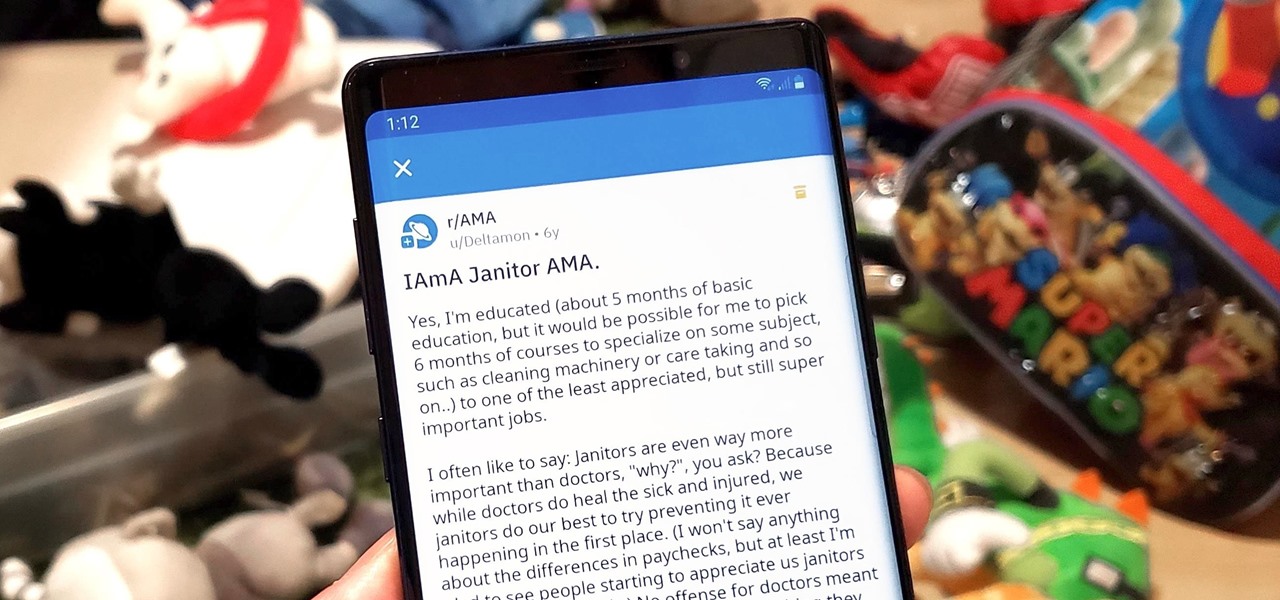
Short for Ask Me Anything, AMA threads are one of Reddit's signature features. They enable you to directly interact with a whole range of interesting personalities, from common folk with amazing life experiences to influential celebrities that help shape politics and culture.

Hollywood has already proven that it's on board with augmented reality, with examples ranging from Avengers: Infinity War to Ralph Breaks the Internet. But one startup wants to make the augmented reality content that's being used to promote TV and film entertainment smarter.

While most kids his age are busy playing Fortnite, 11-year-old Yumo Soerianto is developing augmented reality games. Kids like Soerianto are the future of the augmented reality field — they'll likely be coming into their own as professional developers right as AR technologies become lightweight and powerful enough to be contained in a pair of sunglasses.

Just in time for Women's Equality Day on Aug. 26, Treasury Wine Estates is breaking out a line of wines with augmented reality experiences that pay tribute to historically famous women.

Computer vision company Blippar has already dabbled with outdoor AR navigation, but now it wants to make it easier for people to make their way through indoor spaces with augmented reality.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Modern "mad men" are buying into augmented reality for marketing, with the two latest examples being trendy burger maker Bareburger and department store chain Zara.

We may not know what Magic Leap's product looks like. And we haven't received even a "save the date" for its launch. But we know that it will display mixed reality comics from Madefire when whatever it is arrives.

An update to the iFramed social media gateway app for iOS adds an augmented reality feature called JuxImage that gives its users Snapchat-like photo and video effects.

Antibiotics are one of our main weapons against infections. The problem is that many bacteria are becoming resistant to most of the antibiotics we use to treat them, and those 'superbugs' have created an urgent threat to our global health. A research group found a new way to hit a well known bacterial target and have developed a drug to hit it.

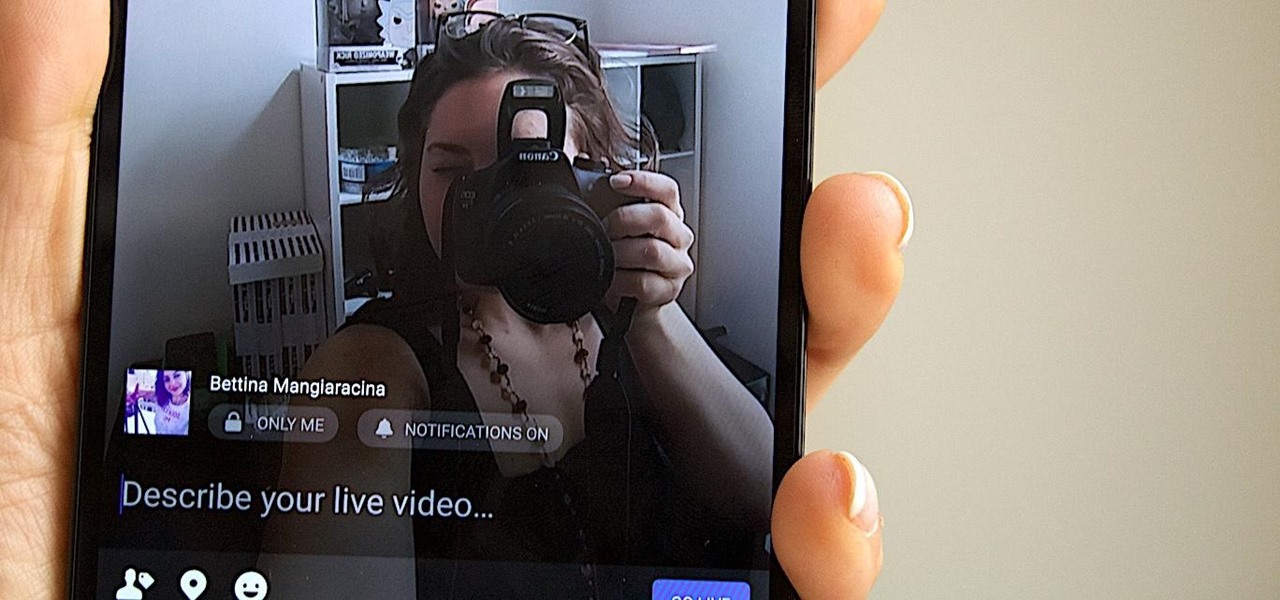
It looks like "going live" is another thing we all have to figure out how to do to remain relevant in this very Facebook-driven world. But why would you ever want to go live? That's really up to you.

The Centers for Disease Control and Prevention estimated that there were 212 million cases of malaria across the world in 2015, and 429,000 of those people died — mostly children living in Africa. Preventing and treating those infections has been a challenging world priority. That makes a new malaria drug discovery — published in Science Translational Medicine — incredibly important.

Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.

When your day sucks, all you want is a tall, ice-cold glass of beer at the end of it all. Nothing complicated about having some booze to temporarily drown your sorrows.

This morning, Google opened a pop-up showroom where anybody can visit to get a hands-on look at the new Made by Google hardware lineup. At 10 am the line at 96 Spring st, in the SoHo neighborhood of New York City, was growing but still manageable. As we waited to be ushered in, Google representatives came by to offer us coffee drinks prepared by a pair of baristas in the Peddler Coffee cart parked on the curb. "Now that's latte art," said the guy in line next to me when he saw that the foam-t...

It's hard to argue with the notion that wine and pasta are a winning combination. I mean, millions of Italians can't be wrong.

Mashed potatoes are a reliably tasty side dish, but they can definitely get a little boring sometimes. So if you're looking for that extra 'oomph' that goes beyond the classic butter and salt seasoning, try infusing your next batch with the flavor of baked potato skins.

I'm no coupon-cutter (I just don't have the patience for it, sadly), but I do love buying things in bulk to save a buck or two. And one of the staples on my bulk-buy list is chicken; I cook with chicken so often that trying to save money on it is a no-brainer.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

Hello NullByte! This will be my first How To series.

Video: . Being one of the most popular DIY/maker projects around, Musical Floppy Drives are nothing new. However, myFloppyDriveOrchestra includes a few unique features, which separate it from the crowd.

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

It would be an understatement to say that Supercell hit it big with Clash of Clans. The game has topped both Google Play and the iOS App Store for years and shows no signs of ever slowing down.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Using breadcrumbs in the kitchen is the perfect way to add crisp and crunch to the usual salad, entrée, or dessert. As chef and media personality Mario Batali once said, "There's almost nothing I wouldn't put homemade breadcrumbs on."

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

What type of person are you in group settings? Are you the social butterfly, eager to get to know everyone and interested in the people more than the setting? Or are you a wallflower, afraid to catch anyone's eye out of fear?

With Apple's Yosemite build of Mac OS X came Continuity, a feature that has allowed us to connect our mobile devices to our computers, letting us access apps, send text messages, answer phone calls, and more while seamlessly switching from one device to the other.

Google Play Music is one of the best streaming services out there. It allows users to upload as many as 20,000 of their own songs for free, then stream them all to any device without ever paying a dime. If you upgrade to their All Access subscription, you get these features in addition to an expansive on-demand library of songs (and beta-access to YouTube Music Key).

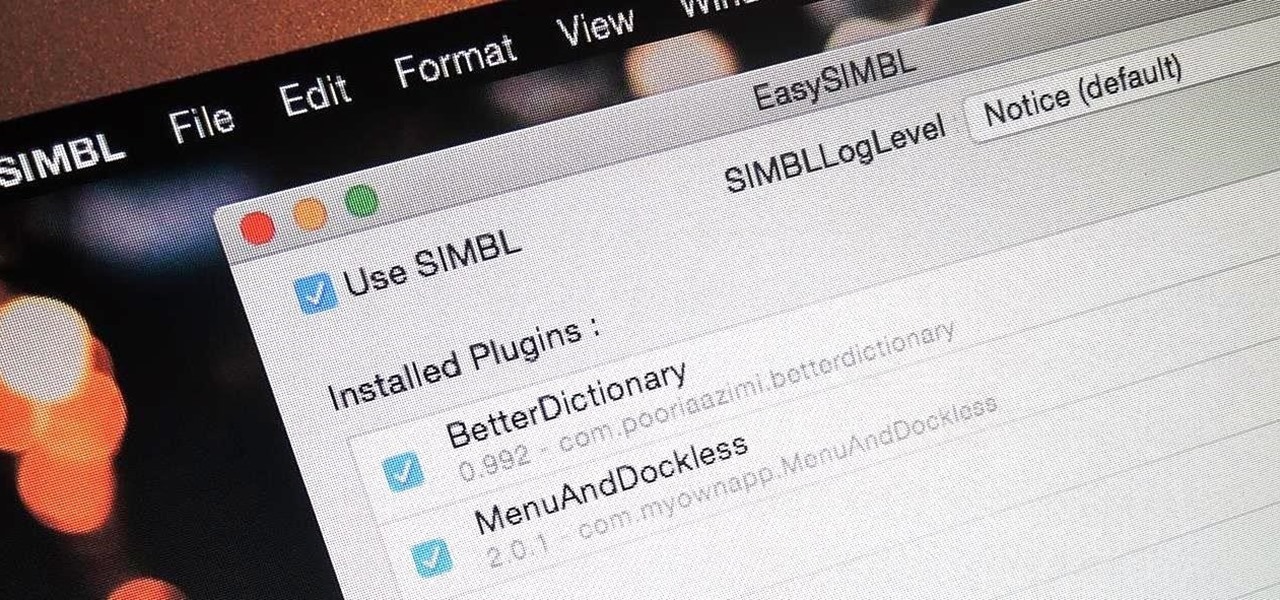
When you buy a Mac, you accept that you're giving up the customization found on Windows or Linux systems for a more fluid and secure machine. This is great for most consumers, but for those of us who'd rather opt for a tailor-made experience, there are always developers that can combine functionality with stability.

Are you a follower or a leader? No matter how you respond, we all know that leader is a more desirable position to hold. Great leaders typically share a few qualities—confidence, intelligence, and strength, to name a few—but one of the most intriguing is their appearance. With the right facial structure, and some well-rehearsed expressions, you can trick others into thinking you're leader material.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...