Removing the spider from your mountain bike crank is an important part of the cleaning process, allowing you to get at areas on the crank that you never would be able to otherwise. This video features a demonstration of how to do this for XT or XTR chainring spiders. For those who refuse to compromise while cleaning their own bike, this video is a must.

The Heron Pose stretches the thighs and ankles and improves posture. Learn how to do the Heron Pose in this video clip about yoga positions and moves. To do the heron pose you should work hamstrings & abs, extend leg & spine, straighten leg, don't compromise spine, and breathe properly. With this how to video you will be able to incorporate the Heron pose into your yoga routine.

You know he cares more about you than his precious video games; he just needs a little help showing it. This video gives tips for luring a boyfriend away from video games, by compromising his love of competition and skill-based games with other activities you can enjoy together as a couple. Watch this video dating advice tutorial and learn how to compete with a video game for your boyfriend's attention.
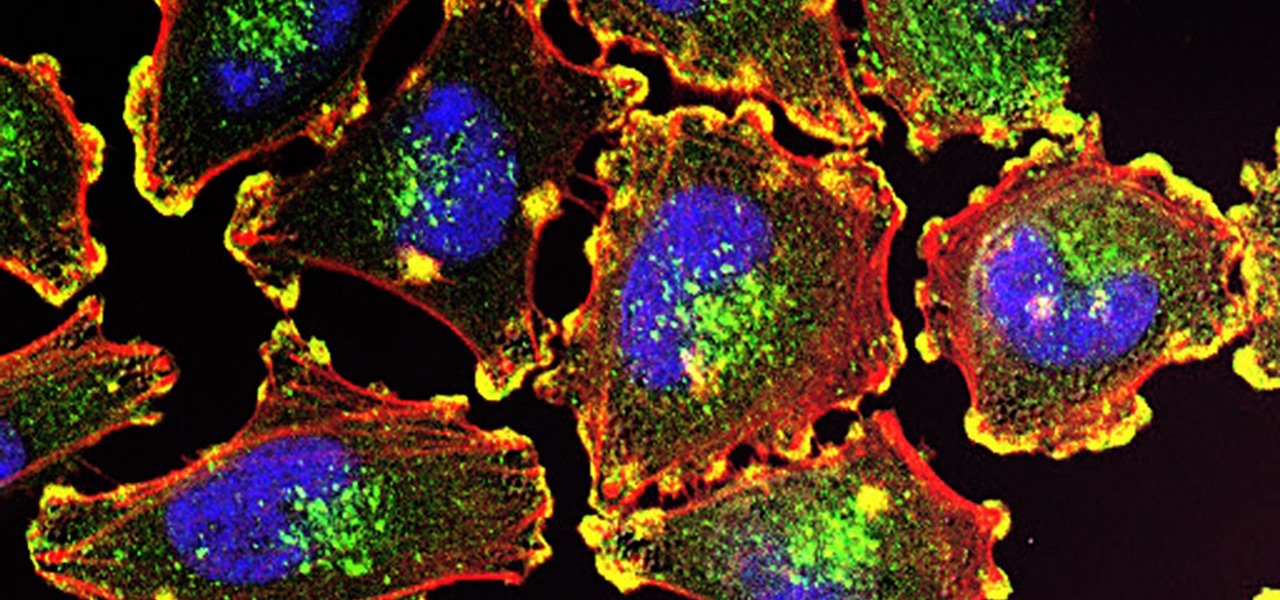
Activating the body's own immune system to fight cancer is the goal of immunotherapy. It's less toxic than chemotherapy and works with our body's natural defenses. The trouble is, it doesn't work for most patients — only about 40% of cancer patients get a good response from immunotherapy. But coupling it with another type of cancer therapy just might deliver the punch that's needed to knock out cancer.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

Hello everyone. I'm Calypsus and i've been around for a while learning from various tutorials, expanding my knowledge and this is one of the best platforms for newbies to sharpen the skills. Today i decided to register myself and contribute to this wonderful community. Since this is my first post, any kind of feedback is appreciated.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

Dr. Schultz explains how to get rid of spider veins. The best treatment for spider veins depends on where they are. 1. On your legs, the best treatment is injections. It takes one to several treatments after which you will then be advised to wear tight compression stockings for three days. 2. If the spider veins is on your face, the best treatment is lasers where they usually work the first time and is not painful. 3. See your dermatologist for a treatment to get rid of spider veins.

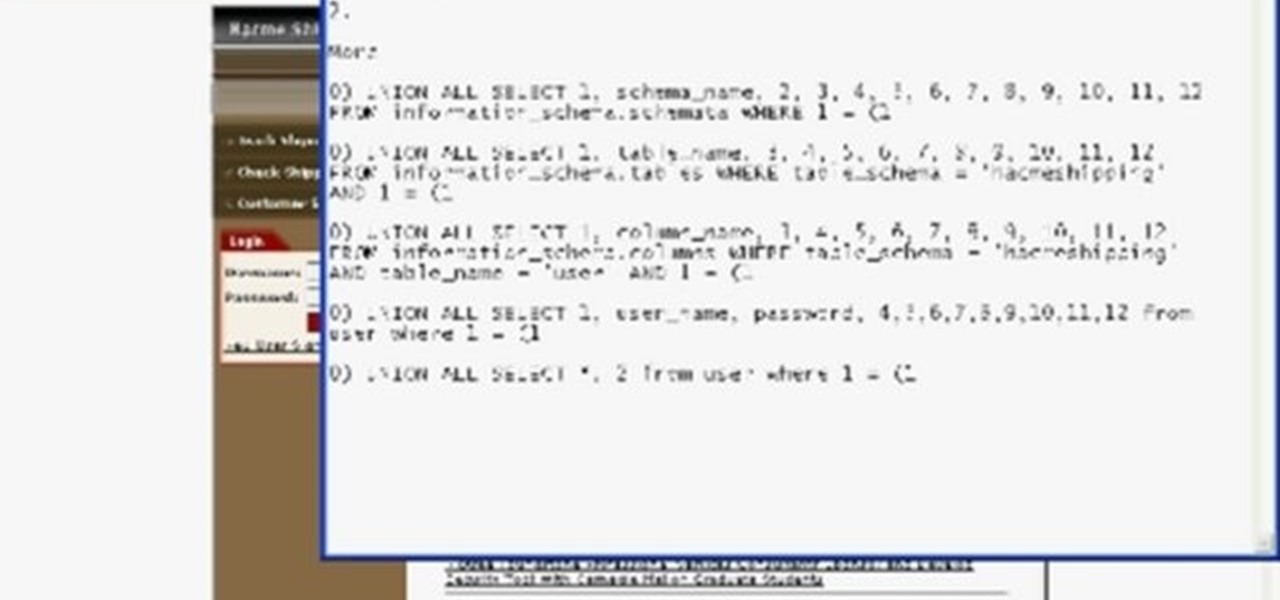
Foundstone Hacme Shipping is a web-based shipping application developed by Foundstone to demonstrate common web application hacking techniques such as SQL Injection, Cross Site Scripting and Escalation of Privileges as well as Authentication and Authorization flaws and how they are manifested in the code. Written in ColdFusion MX 7 using the Model-Glue framework and a MySQL database, the application emulates the on-line services provided by major shipping companies. This video will get you st...

Today, BitTorrent Inc. released the SDK for uTorrent Apps, which will allow software developers from around the world to create Apps for uTorrent, the popular bittorrent client. This video will show you how to download the SDK, install it on your computer, make an app, view that app in a browser, and then package the app and view it within uTorrent without compromising uTorrent's famous lightness. This is a big day for bittorrent fans around the world; download the SDK and start making uTorre...

Learn arm awareness in yoga without being in compromising and difficult poses. In this yoga how-to video Kira Ryder plays with using the cactus arm action to assist in creating the shoulder blade support in urdhva dhanurasana, upward facing bow pose, sometimes called wheel. Watch and learn how to work the cactus action movement to feel your arms while practicing yoga.

Check out this how-to video to achieve a simple blue smokey eye look with makeup. Apply your foundation and brow pencil prior to starting, or else you may have to compromise your simple blue smokey eye look.

In this video tutorial, Better TV shows you how to take a complicated fish dish and make it your own -- without compromising flavor. You will need: parchment paper, salmon fish, tomatoes, eggplant, potatoes, squash, raisins, zucchini, sugar, honey, kalamata olives, roasted peppers, basil, green olives, onions, garlic, parsley.

In most collectible trading card games players fail to realize the value of low-level creatures. They aren't sexy, but they can win you games when used correctly. This video will teach you how to build a Yu-Gi-Oh! based on three stars or less creatures that is still pretty damn effective.

In this video, we learn how to make pork shoulder barbecue. First, heat up the grill with charcoal until it's hot all over. After this, prepare your pork shoulder by placing the entire piece of meat into a brine. If the liquid is saltier than the meat itself, it will cause the meat liquid to draw into the meat. After this, inject the meat with flavors that you like. The pork shoulder is many muscles, so you have to make sure to poke the injection into several of the right spots. When you're d...

In this video Dr. Schultz will show you how to control extreme underarm sweating. If you suffer from extreme underarm sweating, despite regular use of antiperspirants, follow these steps: Make an appointment with your doctor so that they can give you a prescription for a topical antiperspirant called Drysol. This liquid is applied once a week, at bedtime, and is covered with cling wrap. After a few weeks you will see a significant reduction in the amount of underarm perspiration you experienc...

One day, your car may break down and you won't be able to afford to hire a mechanic, so what do you do... you look on the web for some how-to vehicle repair videos and become your own car mechanic, that's what. You don't need any advanced training to perform repairs and simple maintenance on your automobile, but you may need a few tools. Invest in the basic tools and you'll be prepared for just about any car malfunction you can think of. These tutorials will help get you on your way, as long ...

Purple and gold make for an eye catching color combo in the eye look in this how-to video. The cosmetics used by the demonstrator are: MUFE HD Foundation #110, MAC - Select Cover Concealer, MUFE HD Powder, Bare Essentials - Thistle Blusher, Bare Essentials - Heaven Blusher, Stila - Starlight Shadow, UDPP, MAC - Royal Hue Shadestick, MAC - Shadowy Lady, MAC - Noctournelle, MAC - Beauty Marked, Cargo - Toronto e/s, Bare Essentials - True Gold Pigment, Tarte - EmphasEYEs in Black, Two Faced - La...

This makeup how-to video shows a fast way to do the classic smoky eye, but designed for Asian monolid eyes, or any eyes with small or undefined creases. The cosmetic products used to create this look are a Black Pencil eyeliner, L'Oreal in Lush Raven (MAC 217), NYX in Latte Foam (MAC 224), Lancome in Daylight, Shiseido Mascara Base, Too Faced Lash Injection, and Maybelline Define a Lash Mascara. Watch this video makeup application tutorial and learn how to apply a quick and easy smoky eye mak...

This makeup tutorial teaches you how to apply makeup inspired by the astrological sign Sagittarius. The products used for this loook are Too Faced Shadow Insurance, MAC Nude cream color base, Urban Decay Peace eyeshadow on inner lid, MAC Sea & Sky Mineralized eyeshadow: dark blue on outer corner, light blue as inner highlight, Makeup Forever #92 Shadow in crease and under eyes, Too Faced Lash injection mascara, and MAC Missy Slimshine. With this how to video you will be able to re-create this...

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Well, you've shot one too many compromising photo and it's time to wipe your iPhone photo library. But, for some reason, this isn't the easiest thing to do. Well, with this how-to video, you'll learn how to get rid of those 212 photos of your niece in her sailor suit you thought looked adorable. Those cat climbing photos. Gone. That girl/boy you were recently dating. Bye bye. Delete at will and clear your iPhone photo library.

In this episode of Southwest Yard and Garden Curtis Smith shows you how to turn a steep slope into a usable garden. By building walls along the slope using serpentine designs he shows you how to obtain a compromise of both strength and artistic design. Starting with a good concrete footer and rebar you can construct a retaining wall strong enough to hold the weight of the slope. Materials such as wood and railroad ties can be used but may not stand the test of time as the weight of the soil c...

SQL injection is a type of code injection that takes advantage of security vulnerability at the database level. It's certainly not the easiest form of hacking, but if you're serious about turning a website upside down then this is the way to do it.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

Google, the company that rules the internet, is now testing a method to leverage its machine learning with its ubiquitous presence on mobile devices. The new model they're employing is called Federated Learning, and it hopes to apply artificial intelligence to Google's services on Android without compromising user privacy.

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

This video shows you how to change the background color and watermark in your Word 2007 document. Both settings are found on the Page Layout tab. The background color can be chosen from a wide palette. The most frequently used colors are immediately applied to the current page as a preview. You can also choose to add a fill effect, like a color gradient, by clicking the Fill Effects item in the Page Color list. The watermark feature allows you to add either a predefined notice, an image or a ...

In this video, Ed Kriston from AAA-Midatlantic explains how to winterize your car. He first talks about the fuel systems. The fuel pump and fuel filter are inside the tank, and lines and hoses run from the tank to the engine. He points out the fuel lines and injectors in the engine, and recommends that you make sure there are no leaks in the lines and hoses. He demonstrates how to remove and examine the air filter and shows one that is dirty that should be replaced. A dirty air filter will co...

Hacker Defender is one of the most widely deployed rootkits in the world. It is a user-mode rootkit that modifies several Windows and Native API functions, which allows it to hide information (files, processes, etc.) from other applications. In addition, Hacker Defender implements a backdoor and port redirector that operates through TCP ports opened by existing services. This means it is not possible to find the hidden backdoor through traditional means, like launching a remote port scan agai...

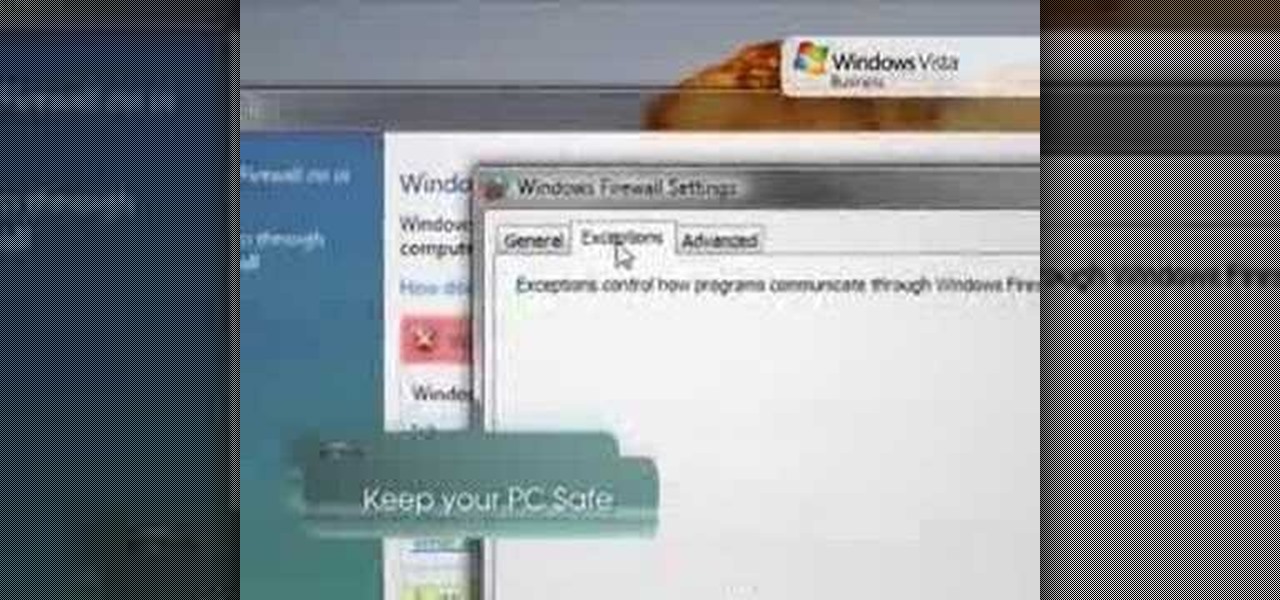
In order to keep your PC safe from annoying or potentially dangerous threats on the Internet, a properly-configured firewall is a crucial item in helping prevent your system from becoming compromised. The Windows Firewall in Windows Vista™ is the first line of defense in helping to keep your computer safe. By preventing your computer from being infected by malware, Windows Firewall is designed to be easy to use and is automatically enabled to protect your computer as soon as Windows starts. T...

Suffering from acne scars that are as noticeable as the pimples that caused them? You can find an effective acne scar treatment, from laser resurfacing to collagen injections. Here, the skin care and scar removal you may discuss with your dermatologist.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

Dirty, malformed, and outright mischievous text strings have long been the enemy of interactive website developers. Strings contain any combination of letters, numbers, spaces, and punctuation, and are entered into text boxes on websites by users. These strings in particular can do everything from highlighting XSS vulnerabilities to soliciting 404 error pages.