
News: Scientists Found an Antibody That Burns Belly Fat (In Mice)
Bone loss and belly fat may no longer be certain fates of menopause, thanks to new research from an international team of scientists.


Bone loss and belly fat may no longer be certain fates of menopause, thanks to new research from an international team of scientists.

Verizon Wireless executives recently cooked up a plan so devious that it could have only come from one of the four major US carriers. Apparently, they aren't satisfied with simply loading every Android device they sell with their own bloatware, so now they're reaching out to big brands to see who would be the highest bidder for a spot on your home screen.

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.

Living on a budget often means compromising what you want for what you need—or at least, for what's affordable. But that doesn't necessarily mean you have to compromise on flavor, especially if you know the right tips and tricks to make something spectacular out of the ordinary.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...

Still got stock? Many factory installed exhaust systems not only sound anemic, they actually are because they scrub power. The designers who are given the task of producing these pipes are often handcuffed by several different requirements that add up to one big compromise. Exhaust engineers are required to build systems that are quiet and that meet certain types of emission standards, but not all of the design concerns are driven by government regulations. Some are based on a perception of w...

The increasingly important world of white hat or "ethical" hacking is getting competitive. Thanks to growing salaries and opportunities for talented and trained coding pros who can infiltrate servers and safeguard networks against digital threats, demand for intrepid cyber warriors is through the roof, and it shows no signs of slowing down any time soon.
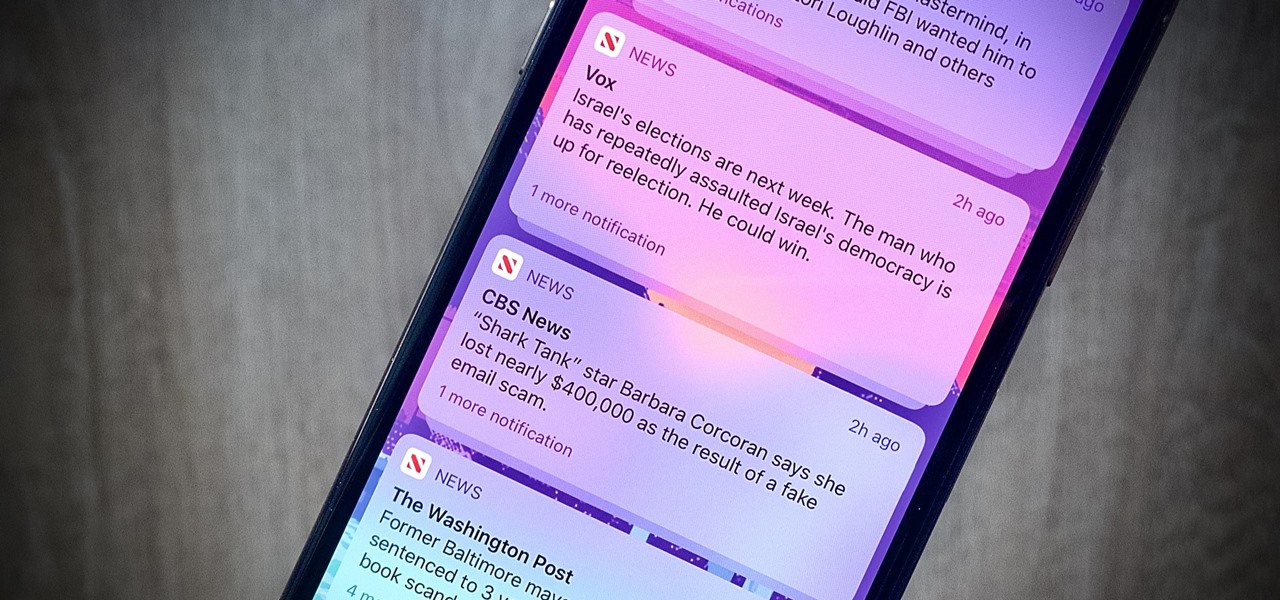
When left unmaintained, lock screen notifications can be an overwhelming, chaotic mess. Alerts coming in at a rapid pace can be hard to see because there are just too many of them, and your iPhone's screen sometimes can't even take it, falling asleep before you can read only a few notifications. If that sounds like you, there's an easy way to take back control of alerts — and your sanity.

The biggest change this year for iPhones comes with the cameras. All three iPhones get a new ultra-wide camera, which allows the device to capture more of what's in front of you. Not so new this year is the 64 GB base storage, which will fill up fast when shooting in 4K at 60 fps. A new feature will also add to your storage concerns, however, a feature that captures more video than it really should.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.
Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

The rumor that the iPhone 8 will ship with 3D camera system is not a new one, but a new analysis by Morgan Stanley's Charlie Chan lends credibility to the speculation. Now, it appears more likely than ever that Apple's next iPhone will ship with 3D capabilities, increasing potential for AR and VR integration in the future.

All you paying Spotify users are about to get another exclusive privilege besides getting out of all those annoying "Ever wonder what it would be like to have Spotify premium?" ads. The Sweden-based company is looking to lower the royalty fees they have to pay to major record labels for their music, by compromising on their policy that all their music be free to paying and nonpaying users. Spotify would for a limited time restrict access on major album releases to their paying subscribers.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.
Android phones may soon be able to send and receive iMessages thanks to a new open-source app called PieMessage.

Anyone who paid attention to the Lavabit shutdown had a feeling it was connected to Edward Snowden, the high-profile NSA whistleblower. Ever since the government's case against Lavabit went public in late-2013, people have put two and two together.

Since it was released last fall, Super Mario Maker has offered us a glimpse into the minds of some of the most evil people on the planet. The game, for Nintendo Wii U, lets players create their own Super Mario levels using a deep list of objects, enemies, and green pipes, which can then be uploaded for anyone to play.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.

The idle screen for the Chromecast is certainly beautiful. Full of many high-definition pictures taken of various parts of the world, it's almost a shame that we have to dismiss this screen in order to cast content.

Personally, I know life would be a lot easier if the people in it could just read my mind. Since that technology is currently unavailable, it's comforting to know that your air conditioner can be your personal telepathist with Sensibo.

Starbucks' app is the most used mobile payment app in the U.S. because it's well-designed and convenient. But if you use the iOS version on your iPhone, your username, email address, password and location data could be compromised because the app stores them in plain text.
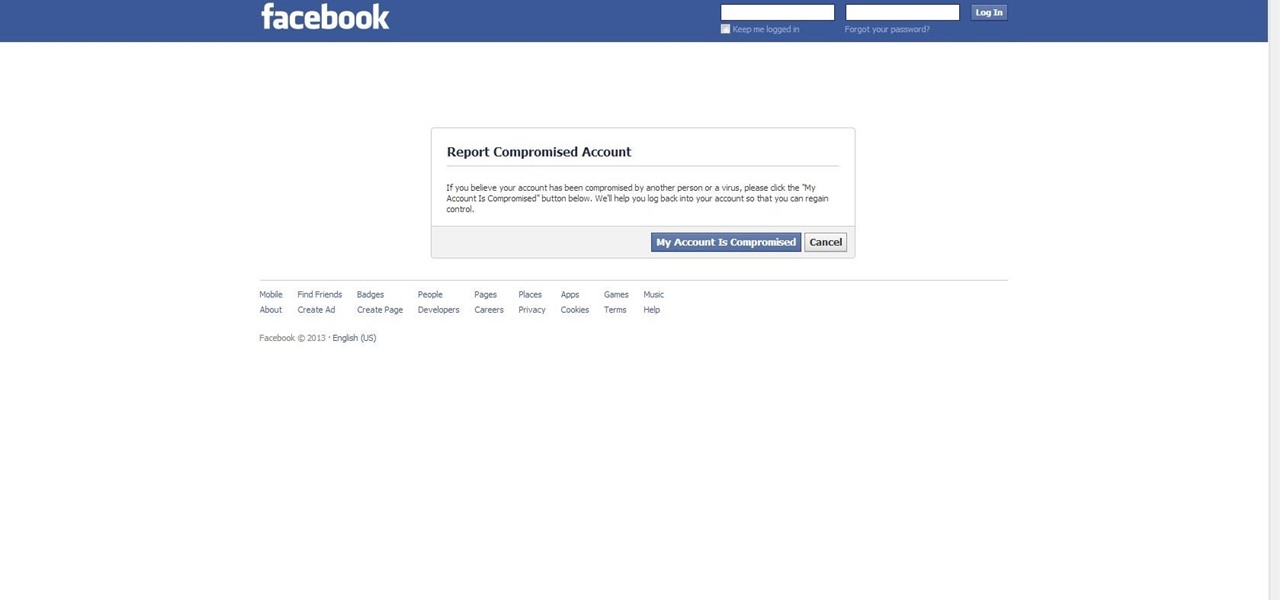
If your facebook account was hacked by someone and you really want it back this tutorial would help you get it back.

According to Nielsen, the average American spends about 34 hours per week watching television. That may sound like a lot, but when you factor in multi-screen viewing, it could be even higher—81 percent of Americans use their smartphones or another device while watching TV. It's the new picture-in-picture.

As with most things on the Internet, browser cookies can be either helpful or harmful, depending on how they're used. On one hand, they make your experience more convenient by storing information about sites you use frequently. On the other, they can help companies track you across the web or cause your computer to be more vulnerable to attacks on public networks.

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

After years of telling patients to finish any prescribed course of antibiotics completely, a group of researchers in the UK say it is no longer necessary, and could even be harmful if we want to preserve the antibiotics we can still use.