
How To: Build a better body image
A better body image in six steps, and dieting isn't one of them. This video will show you how to build a better body image.


A better body image in six steps, and dieting isn't one of them. This video will show you how to build a better body image.

Know the right thing to say – and do – if your loved one suddenly finds themselves out of work. This video will show you how to console your partner if they lose their job.

This sun dried tomato pesto-stuffed pork roast is ready for the oven in ten minutes. Follow along and learn how to make this pork recipe. This cooking how-to video is part of Quick Fix Meals with Robin Miller show hosted by Robin Miller. Busy people everywhere face the same dilemma, how to get healthy weeknight dinners on the table when you've only got minutes to spare. Cookbook author, nutritionist and food journalist Robin Miller guides you through the landmines of getting food on the table...

For a health conscious change of pace, try a tuna burger! They are so easy to make, all you have to get is some canned tuna, which you probably already have in our pantry. This cooking how-to video is part of Quick Fix Meals with Robin Miller show hosted by Robin Miller.

This how-to video quickly outlines exercises to get your dog walking on a loose leash by your side. Put very basically, teach the dog what you want them to do! And secondly, stop reinforcing them when they pull! A clicker training method is used, but if you do not have one, you can always use a verbal marker like yes. However you will get much faster and reliable results by using the clicker. If you hold the clicker in the same hand as the leash, and keep the treats in the other hand, you wil...

Watch this instructional science video to observe the Barus effect in action. A dyed solution of POLYOX (polyethylene oxide - it is the stuff used as the lubricant on the strip found in all modern razors) is extruded from a 50 mL syringe. On exit, a marked swelling in the liquid stream several times the diameter of the orifice is observed. The effect is referred to as the Barus Effect, but it also goes by several other names including the Merrington Effect, Die Swell, and Extrudate Swell.

Yoga is an ancient practice that's excellent for relieving the body of stress and negativity. Learn a few chest and hip opening poses in yoga from a professional yoga instructor in this free video series.

Yoga poses are excellent for stretching, relieving the body of unwanted stress and improving balance. Learn a few balancing poses for beginners from a professional yoga instructor in this free video series.

Yoga offers poses for many skill levels, and seated or supine poses can put less stress on some joints and body parts. Learn seated and supine yoga poses from an instructor in this free yoga video.

Deep tissue massage can relieve stress and minor muscle pain. Our expert will show you how to give a deep tissue massage for the whole body in this free massage therapy video series.

The worldwide health crisis around the coronavirus has gripped the live events industry, particularly in the tech sector, with the cancellations of Mobile World Congress, the Game Developers Conference, Facebook's F8, Google I/O and now South by Southwest.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Considered by many (perhaps unfairly) to be a very public failure, Google Glass can add another plot point to its comeback story, this time as a tool to teach social skills to children and adults with autism.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.
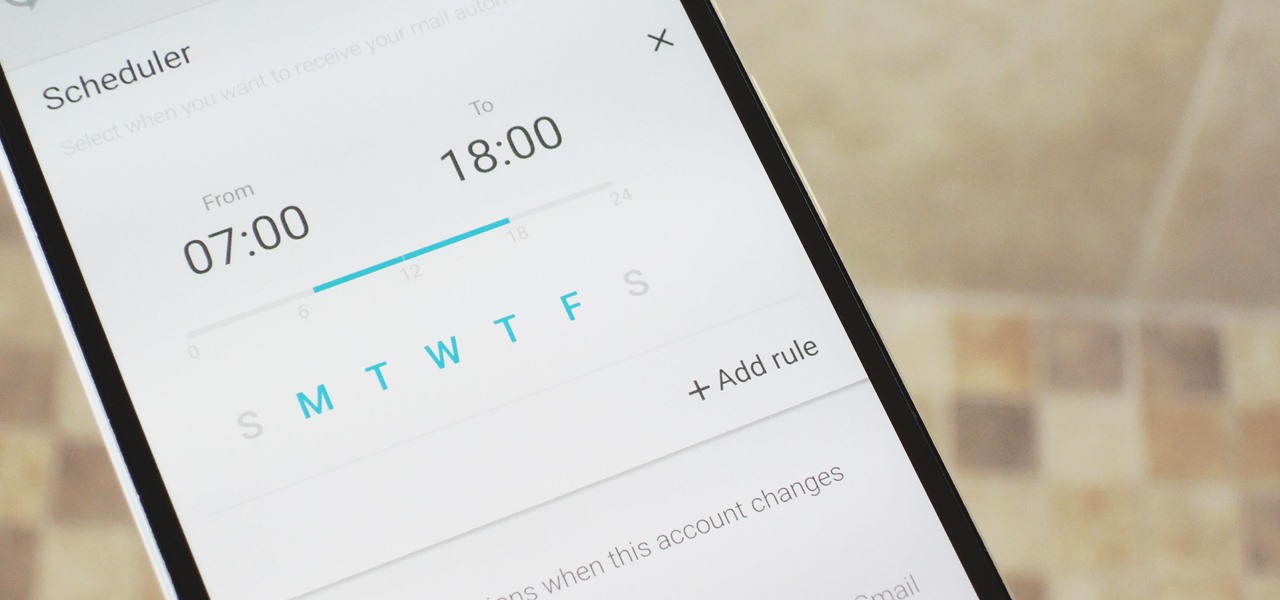
These days, when you're setting up an Android device for the first time, you'll be prompted to add extra email accounts directly to the Gmail app. It's really simple, too—just sign in with your work or exchange account, then emails from those accounts will be mixed in with your personal account in the Gmail app's "All Inboxes" view.

Instead of suffering through long, dull meetings with your supervisors and coworkers, you can turn those office table sessions into your very own psychological experiment.
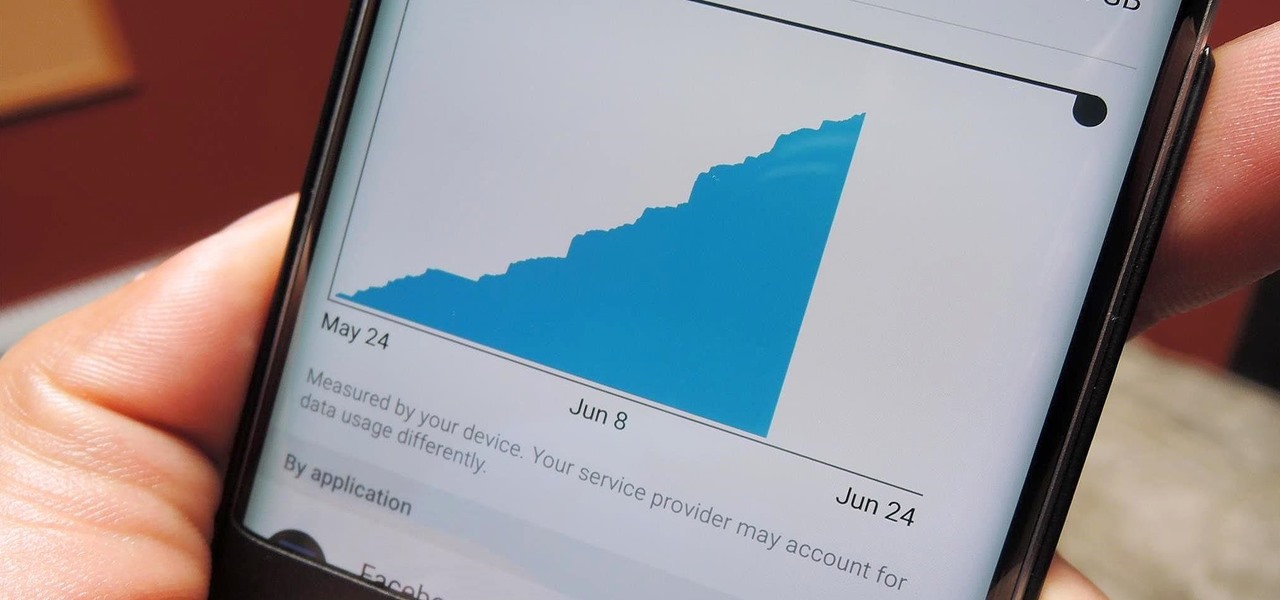
With all the stress that goes into booking flights and lodging, packing (and not forgetting) everything you'll need, finding pet sitters, and everything else that goes with a trip overseas, there's the added stress of staying connected while abroad.

Rather than reaching for aspirin the next time a headache strikes, try grabbing a drink of lemonade instead. Not only can it help ease your head pain, but it can also help relieve stress, anxiety, and depression. But not just any old lemonade will do the trick—reach for the lavender lemonade.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Our workdays are typically filled with one thought: get as much completed as possible. Whether you face an inbox filled with tasks or just a project or two, both our bosses and our inner workhorses encourage us to knock out as many tasks as we can each day. But is being super-productive the best course of action for our minds and our employers?

Like the buttons on your computer's mouse and keyboard, the Home key on your Samsung Galaxy S4 serves a vital function in navigating through your device. It can get pressed dozens of times a day, going through hours of use and abuse.

Until recently, brainwave-reading devices have pretty much only existed in science fiction. Sure, electroencephalography (EEG), the technology that powers these devices, has been used in medicine and psychiatry since the late 1800s, but diagnosing people's brains and reading their minds are two totally different things. The first EEG headsets available to the public were used mostly in gaming and even in fashion, but in the last few years, they've gotten a little more sophisticated.

Sadie demonstrates one of her favorite yoga poses, the one that looks the most ridiculous - the Lion Pose. The Lion Pose is a fierce posture that relieves tension from your neck, jaw, face and entire body. It is very simple to do and can be done anytime or anywhere you need to release excess tension. To do the Lion Pose, inhale deeply all the way down to your belly; on the exhale, stick your tongue way out and roar like a lion. You can do it quietly or more powerfully, whatever you feel you n...

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

Don't sit back and take verbal abuse! This tutorial will teach you how to dish it back out and craft the perfect insult.

Is your French up to par with Parisians? Can your Aussie tongue mingle with the local Australian natives? What about your old-style New York accent? If you're in need of improving your accents in different languages, then Amy Walker can help you out.

Everyone gets an upset stomach from time to time. The first line of defense in this high-tech age is still old-time remedies! Watch this video to learn how to sooth an upset stomach.

When a rod mounted in a hand drill is dipped into a liquid and rotated, for certain non-Newtonian fluids the liquid will climb the rod - sometimes to quite spectacular heights.

Don't let carpal tunnel get the best of you! Learn yoga positions and exercises to relieve stress and pain associated with carpal tunnel syndrome in this free alternative medicine video from an experienced yoga instructor.

The great thing about burritos is that you can make them to your personal taste and fill them with whatever you like. Today, we are going to fill the burrito with a few of my favorites. We have a base of black beans, rice, some sautéed green pepper and red onion, grated Monterey jack cheese, a little bit of sour cream and some salsa. But again, the fillings are versatile, it is the assembly of the burrito itself that we are going to concentrate on. he first key to making a great burrito, and ...

When watching stories in your Instagram feed, there's a high probability that you'll come across an AR filter that you'll want to try out for yourself. A quick browse and search in the Effect Gallery will bring up nothing in most cases. But all of that unproductive work isn't necessary because there's a faster and simpler way to get the AR effect in Instagram Stories, and it works all of the time.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

Magic Leap and Samsung are putting their money where their augmented reality plans are, with the former acquiring an AR collaboration technology and the latter funding a waveguide display maker.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

While Leap Motion has given makers a DIY solution for building their own augmented reality headset with Project North Star, a self-described "AR wonk" has taken the blueprints one step further by creating an untethered version.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.