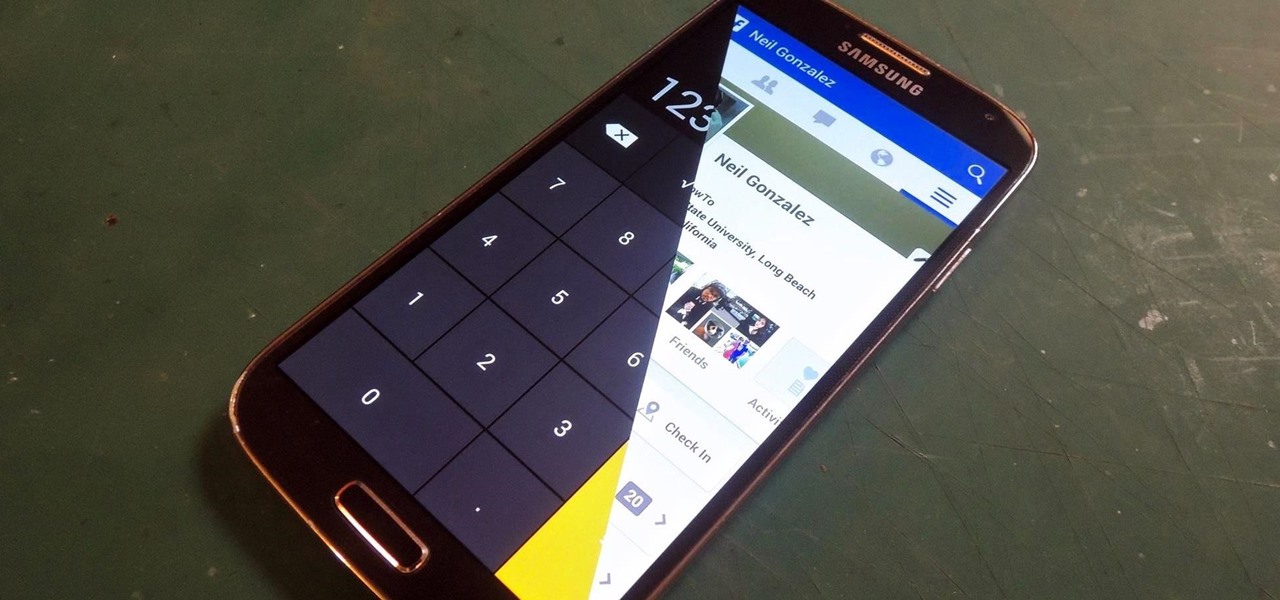
Trust can be a touchy subject in general, and is often required when sharing personal information—especially so when handing our phones over to others. You may not have a ton of secret or nefarious information on your device, but that doesn't mean you want your mom or snoopy coworker having easy access to your messages or Facebook app.
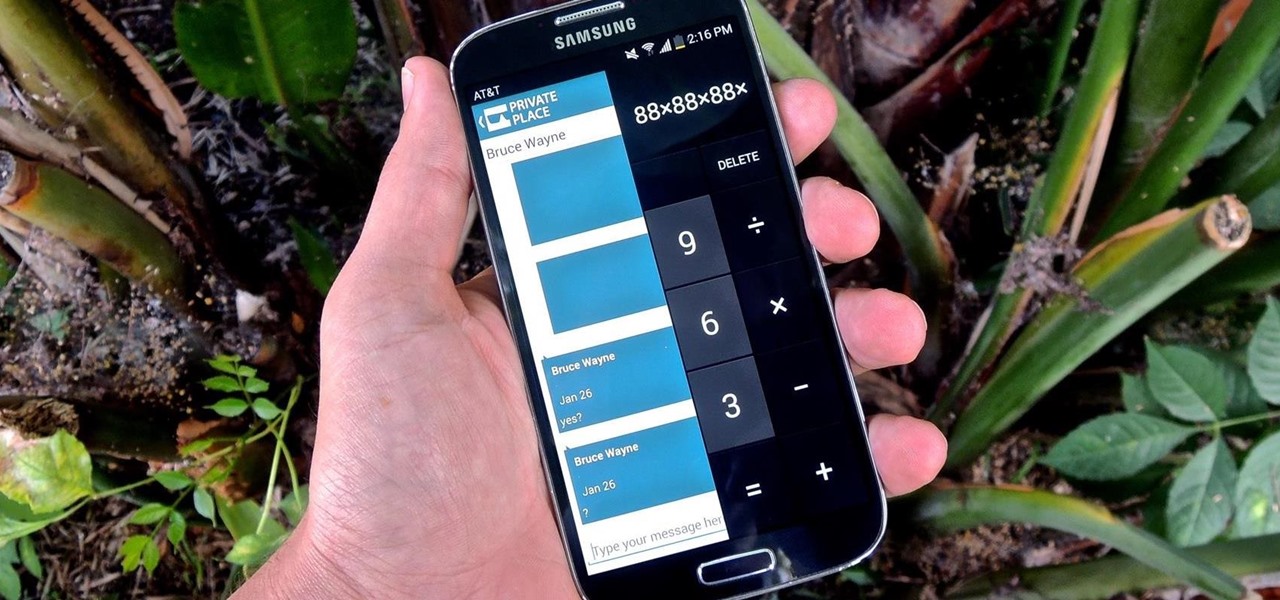
Whether you're a secret spy or just a regular person with a few secrets, you may want to keep certain information on your smartphone private, and it's totally possible on Android to do so.

There are plenty of good reasons to always make sure your knife is as sharp as it can be. Obviously a honed blade cuts better, but you're also less likely to hurt yourself with it. And have you ever tried to slice a tomato with a dull knife? You may as well just skip the extra step and crush it with your hands.

A couple of months ago at the Black Hat security conference, hacker Cody Brocious gave the hotel industry a nasty surprise when he figured out how to hack the locks made by Onity that are used in millions of hotels worldwide.

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

Want to disguise your URLs so that they appear suspicious? In the style of websites such as Tiny URL that take your original URL and give you a shortened one to post on your blog or twitter feed, Shady URL takes your original URL and gives you one that might convince people not to click it. Go to Shady URL and paste the URL you wish to disguise. Click submit, and on the next page it will give you a URL that looks, well, shady. It might include something about a mail order bride or an investme...

Yes, we know, most manga girls look innocent anyways (though the same isn't always true for their personalities), but this manga girl is truly adorable and friendly-looking. Of course, the big, bright childish eyes and pursed lips probably help with that.

The FBI is using informants to stir up fake terror plots, destroying lives in the process. FBI Terror Plot: How the Government Is Destroying the Lives of Innocent People | | AlterNet.

MIT scientist explains OLEDs by electrocuting a pickle. From Gizmodo:

Humans aren't the only ones who get to take part in the festivities on Halloween. We give our pumpkins human faces and dress up our pets, so why not include toys and stuffed animals in the fun?

The team behind the Pwn Plug, a little white box that can plug into any network and access it remotely, is at it again. This time, Pwnie Express is working for DARPA to create a hacking machine that looks like a power strip, cleverly called the Power Pwn. The device has wireless, ethernet and Bluetooth capabilities and can do a full-scale penetration test as well as bypass NAC and other security measures automatically. It has three modes: Evil AP, stealth mode and passive recon. In stealth mo...

Every day of the week, WonderHowTo curators are hard at work, scouring the web for the greatest and most inspiring how-to videos. Every Friday, we'll highlight our favorite finds.

The Black Swan hit theaters today, and everyone's raving about Natalie Portman's performance as Nina, the ballet dancer who must cope with her emerging evil side.

There's nothing more tedious, yet exciting, than watching surveillance cameras at work. They prey on the innocent and the unknowing. They protect businesses, workplaces, and homes. They catch criminals in the act, find hilarious anomalies, and are just darn cool when you're not the one that's supposed to be eavesdropping with them.

A lot of commonly used household items are actually poison for your furry friends. In this clip, learn all about which items can pose a danger for your dog or cat. It's not only chemicals that are bad for your pets, innocent seeming items like fruit, veggies, chicken bones, chocolate, human medications and many other hidden dangers exist as well.

Major chords are like happy kids' movies, which have an upbeat beginning, middle, and end to satisfy innocent minds and sugarcoat harsher realities.

The White Queen is played by Anne Hathaway in the new Tim Burton produced "Alice in Wonderland". This look is ethereal and innocent, but also strong and sad.

Blogger Jimmy R. demonstrates how you can embed hidden files into an innocent-looking JPEG image using the free 7-Zip and the Windows command line.

Get that very "right now" green smoky eye with some help from the professionals at Smashbox Cosmetics. By starting with cream liner Midnight Green and applying little smudges along the line, go back to smudge with your brush to create a smoky effect. Stand our this fall with vivid color and this soft, not-so-innocent makeup look.

Lauren, AKA QueenofBlendingMUA has joined the ranks with the other YouTube makeup gurus. Lauren is a makeup artist with a large collection of eye makeup video tutorials. Her eye makeup look span from everyday makeup to creative, more expressive party looks. Check out this makeup tutorial video to learn how to create a matte orange eyeshadow makeup look. Search QueenofBlendingMUA on WonderHowTo for more beauty videos.

This video will help you feel more comfortable approaching someone new to spend Valentine's Day together. It can all start with a simple and innocent question. "What are you doing on Valentine's Day?" This really will work equally well for men asking women out or women allowing men the opportunity to ask them out. This could be just the encouragement you need to take the first step in starting a new relationship or just getting to know someone whom you have found interesting. The best part to...

In this video you'll learn how to end the cycle of those pesky fleas and ticks. You'll learn exactly what to use and what to do to stop these external parasites from invading your home or living on your poor innocent animal. After watching this video you'll be able to enjoy a flea and tick free enviorment.

Any medical student should be able to perform a basic cardiovascular exam. This medical how-to video tutorial outlines the guidelines to perform a basic cardiovascular exam. Always begin by by observing the patient from head to toe. Inspect the face for signs of cyanosis. Note visible scars or pulsations in the neck and edema in the feet. This video is intended for medical professionals only.

Take it up a notch next Halloween by re-creating a classic princess with a naughty twist! In this two-part tutorial, learn how to steal the look of sweet & innocent Disney princess, Snow White and transform her into one hot retro pin-up model! Makeup & hairstyling is gone over by makeup & hair specialist Iris with a step by step process. Take seven short friends with you as dwarves and your look is complete!

Sure, princesses are pretty and always get the prince. But they're so naive and innocent and innocence is no fun. Have a little fun this Halloween by dressing up as the infamously evil sea witch Ursula from "A Litt'e Mermaid."

Got something to hide? Learn how to censor or "GMask" an image simply by using the Mosaic option in PhotoFiltre to pixelize the entire thing or just a small (Naughty!) area. It's not that difficult to protect the identities of the not-so-innocent, especially after following the instructions in this video.

Butterflies are usually sweet and innocent, but not in the downpour that is Heavy Rain. In this PS3 walkthrough, see what's up with the Butterfly and if you're ever going to catch the Origami Killer. See how to beat Chapter 3 - The Butterfly.

Learn how to remove ink stains from fabric. Getting ink out of fabric is a tricky business, often best handled by a dry cleaner. If you want to try it yourself, though, here's what to do.

There's nothing more maddening than opening the office fridge and discovering your lunch is gone. Put an end to the stealing with some of these strategies. This video will show you how to deter coworkers from stealing your lunch.

If you're looking to pull off a great prank for Halloween, this next tutorial will show you a classic prank. It involves using a candy dish and your hand.

So you're not a wee little kid in elementary school anymore and you miss handing out those heart sticker-closed envelopes featuring cute messages of Valentine's greetings (and hoping that your crush will notice you drew in an extra heart on his card). How do you celebrate Valentine's Day then?

Peter Answers is a fun website online that you can use to play pranks on your friends. This site is easy to access, free and requires no downloads.

Have something you want no one else to find? The best hiding places are in plain sight. Follow these steps to create a shockingly sly storage space.

Learn how to play "You're Not Sorry" by Taylor Swift, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

Grab your acoustic guitar, strap, and your pick and check out this free guitar lesson. This video tutorial will teach you country rock guitarists how to play a Keith Urban song. Not just any Keith Urban song, but one of his greatest: "Stupid Boy." And just so you know, here are the lyrics to go along with this instructional guitar lesson:

Learn how to convince someone to go skinny-dipping. The trick to getting someone to skinny-dip with you is to make them think it's their idea.

Halloween is a time that embraces blood, gore, and using blood and gore to scare innocent civilians. So if you're in the pranking mood this Halloween, check out this video to learn how to do a funny ketchup splattering prank that'll leave fake blood all over your victim's clothes and on the floor.

Welcome back, my rookie hackers!

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.