We're a little citrus-obsessed, and with good reason: lemons, limes, oranges, grapefruit: Mother Nature really packed those babies with flavor, from peel (which you can zest without special tools) to juice. Now executive chef Amanda Freitag of Empire Diner has come up with a way to make those lemons and limes give up even more flavor by applying a lot of heat.

Classic party games like Spin the Bottle and Truth or Dare, immensely popular in the '80s and '90s, seem to have been long forgotten and abandoned by today's youth. Today, new forms of party games are all the rage, a prime example being Cards Against Humanity. Yes, CAH is hilarious and fun, but the classics can still be appreciated, as long as we catch them up to the times.

April Fool's Day, aka National Screw with Your Friends Day, is finally here. You can always pull a conventional prank, like strategically placing a whoopee cushion on your mom's chair, but that joke has been exhausted generations before smartphones were around. We live in a day and age where smack cam is the new level of pranking, so it's time to step your game up, novices.

Clothespins are pretty innocent-looking, but with a mod here and a hack there, that innocence quickly turns into danger. Well, sort of. In this project, we'll be turning an ordinary spring-action clothespin into powerful matchstick and toothpick shooter that can shoot apples and lob fiery darts over 20 feet.

Why can't Thanksgiving be a celebration of fireworks, too? This year, it can be with an innocent looking pumpkin pie that erupts an insane fountain of flames and fire! In fact, the pie filling is actually a flammable mixture of sugar and potassium nitrate, which was made using the same process as my DIY smoke flares with fuses.

You know that guy who does the cheesy card trick to get the attention of all the girls at the party? Well, we kinda hate that guy don't we? But, if we could be that guy, it might not be so bad.

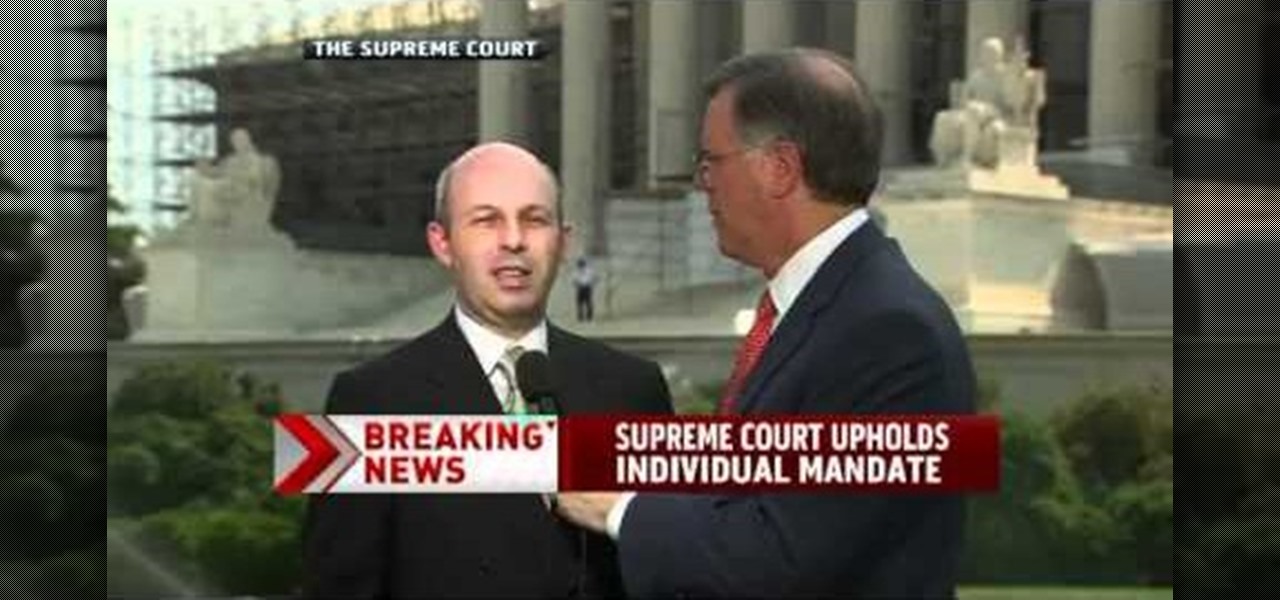
The big question this week would be the controversial Obamacare mandate. And heres the answer: Yes. Obamacare passes Congress' filters and is now an official OK. Texas college hacks drone in front of DHS — RT.

As the stigma of online dating fades and swiping potential suitors on your phone becomes the new norm, one very real issue that you may have to deal with is catfishing: the act of being deceived by a fictional online persona. Although dating apps do their best to weed out fake accounts, a few of them slip through the cracks and take advantage of innocent people just looking for a connection.

Rovio created one of the first mobile gaming hit franchises with Angry Birds, so perhaps it is surprising that, aside from a promotional mini-game developed with Zappar, the company has yet to adapt the game to augmented reality via ARKit.

My message to Russian hackers is this: LEAVE BRITNEY ALONE! Russian hacking collective Turla has been targeting governments and military operations in the United States, Europe, Asia, and the Middle East for the past decade. Now, it appears that the group is targeting everyday citizens — specifically Britney Spears fans.

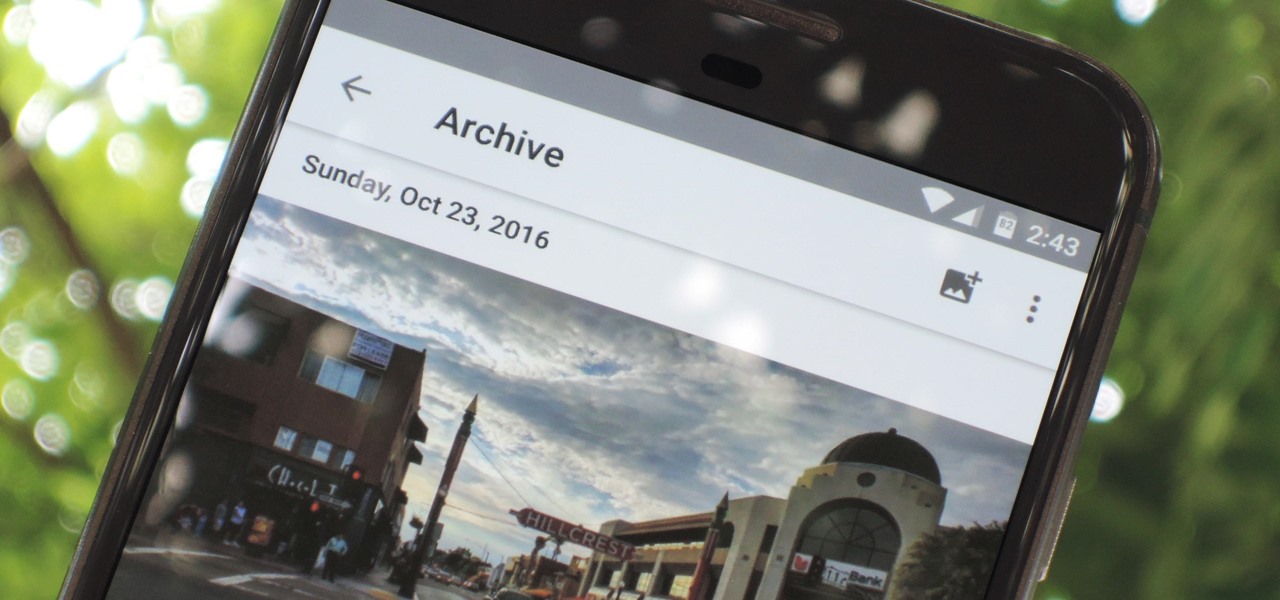
Google Photos just got a killer new feature that everyone should know about. Instead of one endless stream of every picture you've ever uploaded, there's now an "Archive" section where you can stash select shots.

Uber's chance at driverless domination may be ripped away as its legal battle with Waymo escalates. The company's self-driving program is now under threat of closure if the allegations of premeditated theft are proven

While clicking random links on the internet probably isn't the best idea to begin with, now you can rest easy knowing that your iPhone won't repeatedly dial 911 after tapping a malicious link in Twitter, Facebook, or other apps that use iOS's WebView.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

The shooting of Walter Scott (who was unarmed) has been dominating the news these past few weeks. Scott, who ran away from police officer Michael Slager after a routine traffic stop, was shot in the back and pronounced dead shortly thereafter. Unlike similar cases where a cop shoots an unarmed person, the police officer involved in this particular shooting is currently in jail, facing a potential murder charge.

Video games have come a long way over the last 30 years. In the late-'80s, Atari, Nintendo, and Sega were taking gaming from arcades to living rooms. Back in 1994, the Super Nintendo and Sega Genesis were in bedrooms everywhere, and over the next couple of years, were slowly being replaced by Sega Saturn, Nintendo 64, and the first ever Sony PlayStation.

Link shorteners like TinyURL and Bitly are great for Twitter (or anytime you're limited on space), but they're also great for hackers. It's easy to hide a malicious link in an innocent-looking shortened URL, which increases the chances that people will click on it.

The iPhone 5 will be here in no time. Pre-orders started at 12:01AM PST this morning and it's expected to start shipping in about two weeks. Verizon, AT&T, and Sprint are all handling unlimited data plans differently, so if you currently have an unlimited plan and are going to get the iPhone 5, you'll want to know what your carrier is doing before you upgrade so you don't end up with a very unpleasant surprise on your next phone bill. Verizon

I should start off by saying that this technique is of no real practical value, because this process is far more time-consuming than simply just manually trimming trees to meet your specifications. That said, it's an awful lot of fun to play with!

If you use Ubisoft's uPlay browser extension, you should probably get rid of it right now. An Information Security Engineer at Google discovered that the plugin has a hole in it that allows programs to be installed through uPlay, essentially letting anyone who feels so inclined to take over your computer. How the Exploit Works

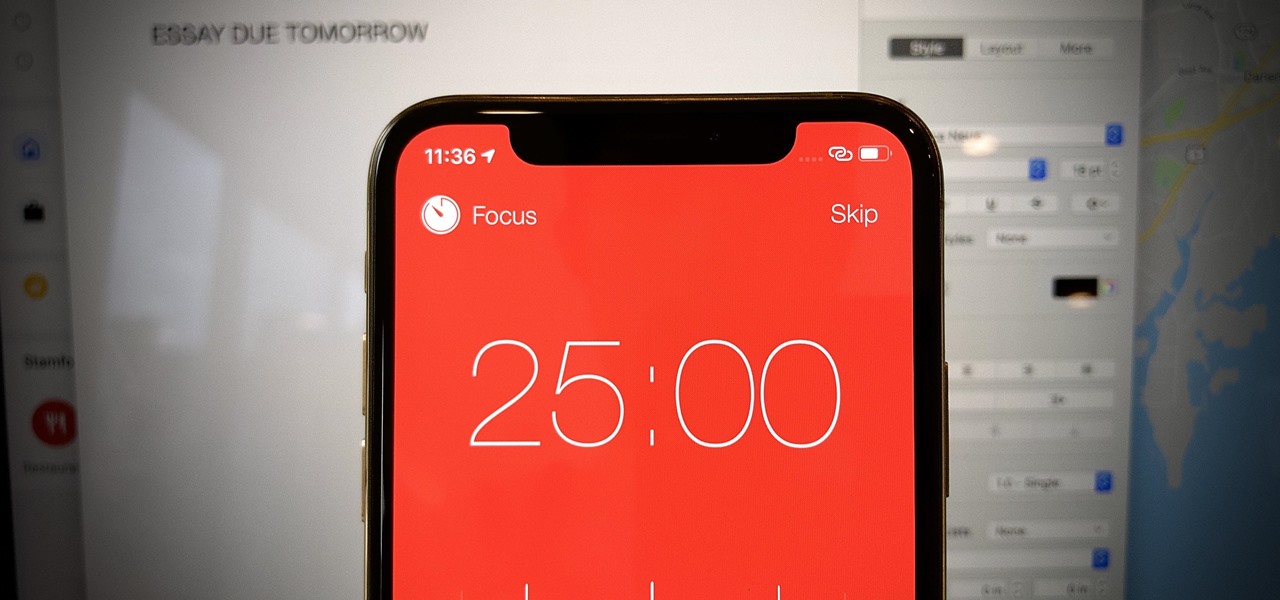
Procrastination is an ugly beast. At first, it seems so innocent to spend five minutes checking Reddit or Twitter. You'll get started on work right after. Next thing you know, it's 1 a.m. and that paper is due in seven hours. Before you start another YouTube video, know you don't have to be like Spongebob. You can be like me, taking control of your productivity with the right app.

A few years ago, the Hilton hotel group unrolled the Digital Key, a feature of the Hilton Honors app that allows you to unlock your hotel room with your smartphone.

We all know the internet isn't exactly a safe place. While plenty of its users are innocent and kind, you won't last long unless you treat every new screen name like a criminal (we're all this cynical while surfing the web, right?). Well, that cynicism is proven correct today, a post on Medium uncovered a group of scammers on the iOS App Store that are costing victims up to $400 a month.

As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.

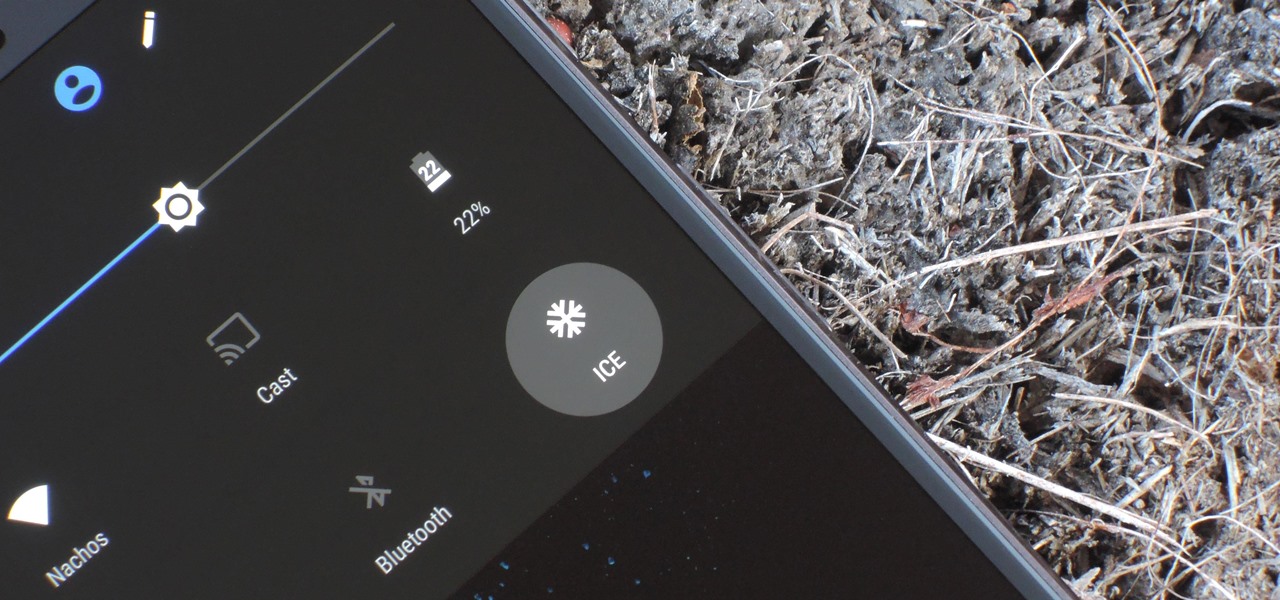
If you're ever in a major accident or have a bout with acute onset health problems, first responders will need to know as much information about you in order to provide proper care. For this reason, paramedics and firemen have been trained to search a subject's cell phone to find ICE (in case of emergency) contacts that know your allergies, blood type, and other vital details.

Guys, this has got to stop. It's not funny anymore. I'll defer to one of my all-time favorite people when it comes to my feelings on this unsavory subject:

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

Creativity and well thought-out planning are qualities to be admired when choosing a costume for Halloween. Going out in hordes to purchase the same 'ol outfits from a local costume warehouse means you're probably wearing the same thing as thousands of other people.

No matter how careful or decent you are, there will always be pictures or videos that you want to keep private. They say a picture is worth a thousand words, but if someone were to go through my photo gallery, only one word would be coming out of my mouth—"%@&#!!"

When was the last time you bought a CD? Most of us listen to music through a number of digital channels—MP3s, Internet streaming services like Pandora and Spotify, and satellite radio, to name just a few.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

Colorectal cancer — cancer of the colon or rectum — is the third most commonly diagnosed cancer in the US. To reduce the chances of a diagnosis we are all urged to stop smoking, keep our weight down, decrease our intake of alcohol and red meat, keep active, and get screened for colon cancer. But, new research has found something that participates in the development of colorectal cancer that might not be as easy to control: A strep bacteria that promotes tumor growth.

Facebook is testing a new feature in India. One that could help you protect your profile photos from being used on sites without your permission.

Google's Chromecast is quite literally one of my favorite inventions of the past five years, allowing me to kick back, relax, and enjoy the various forms of streaming entertainment it has up for grabs.

A little cooking mistake can lead to tough meat, spoiled food, and even a bacterial explosion in your kitchen if you're not careful. These five simple, easy-to-fix kitchen mistakes are some of the most commonly made in households around the world. Luckily, you can correct these innocent errors with just a few minor tweaks.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

HomePod and HomePod mini are excellent smart speakers if you're entrenched in the Apple ecosystem. They even offer ways to protect your sensitive information from friends and visitors who try to ask Siri to spill your secrets. But there's an extra layer of privacy you can put in place to make sure nobody gains access to any important notes, reminders, and calendar events.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.