Want to learn how to broadcast live & record from your game console while viewing game-play in HD - using the BlitzBox B1-HD (for under $100). THis is an easy way to record your PS3, PS2, XBOX 360 or Wii games.

With more digital content than ever, the search feature on smart TVs is essential. But typing is such a terrible experience when you're forced to use voice dictation or peck around with the remote control. Thankfully, there's a better way.

Software issues occur more frequently on jailbroken iPhones, though, they're usually minor bugs that can be fixed easily with a respring. But if your device freezes up, restarting is the only way to get back to normal, which also means having to re-enable your jailbreak. There is one way, however, to respring without interacting with the touchscreen and having to re-jailbreak.
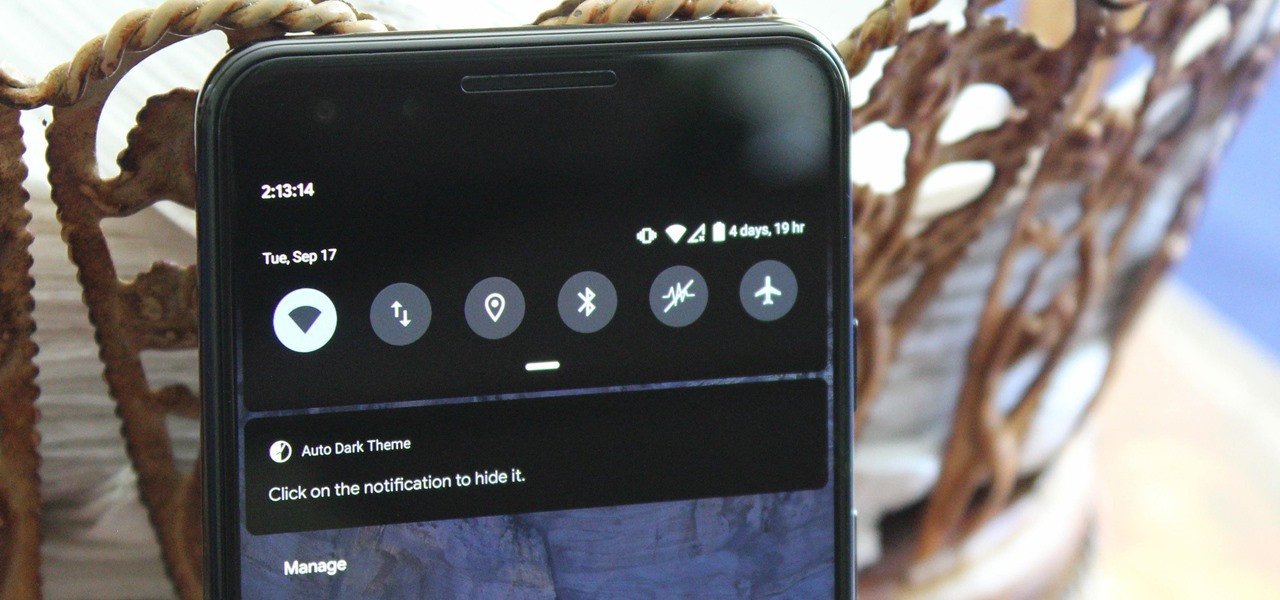
Android 10's new dark mode is a pleasure to behold for longtime users. Ever since OLED panels became widespread, we've been clamoring for the feature. But now that we have it, there's a new problem: it doesn't turn on automatically based on time of day. Thankfully, a simple app can turn dark mode into a true night mode.

Although early attempts at consumer smartglasses have employed trackpads and handheld or wearable controllers for user input, its the gesture control interfaces of the HoloLens 2 and the Magic Leap One that represent the future of smartglasses input.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Paying for street parking in New York City just got so much easier. Instead of searching for loose change or hoping you didn't forget your wallet, you can use a device you always have with you: your phone.

Headphone drama has been all the rage in the past year, with Apple killing off the headphone jack and trying to force AirPods upon its users (Apple, stop trying to make tiny, expensive, easy-to-lose earbuds happen. It's not going to work).

HoloLens users will have a handful of ways to interact with the mixed-reality, holographic world. Gaze Input lets the user control a cursor in their field of vision. In other words, it's essentially a mouse that you control by looking around.

Welcome to my tutorial where Voidx and I will be expanding on my previous article to provide more clarity into the logic of the code.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.

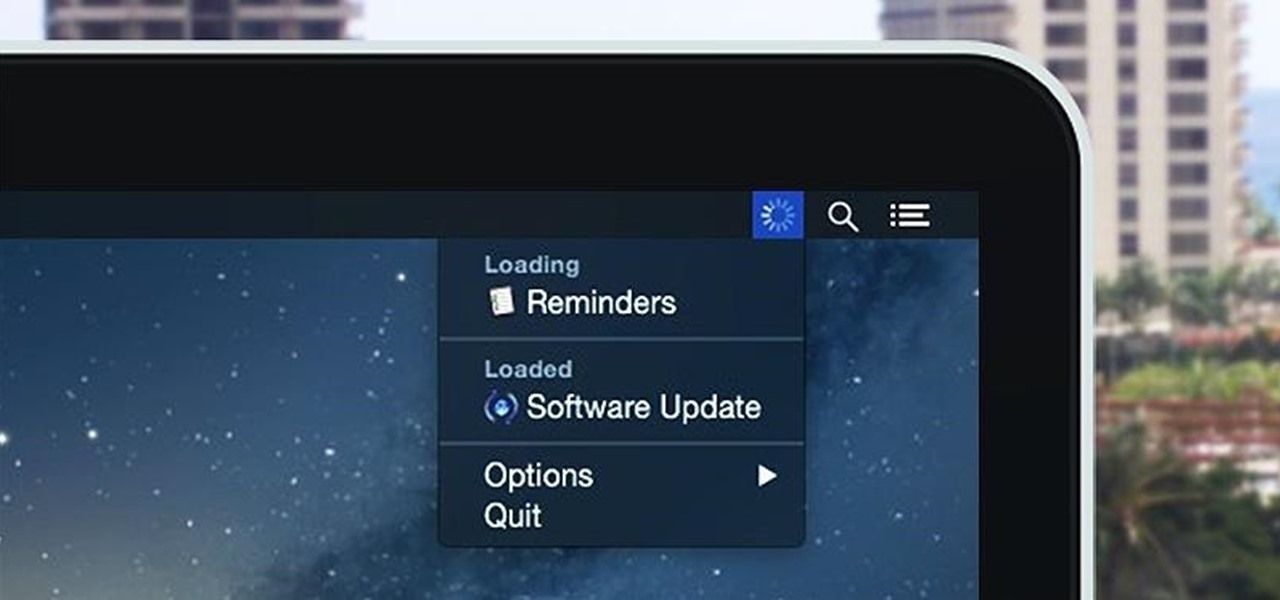
Monitoring your Mac with widgets can be the first step in identifying bandwidth issues, but finding the root of the problem can be a completely different story. Usually you will have to open up Activity Monitor in Mac OS X to look for apps hogging your bandwidth, but with Loading, you can get a detailed data usage report right from your menu bar.

The "Smart Keyboard" on the LG G3 has received a lot of praise for its ability to adequately analyze user keystrokes, provide adjustable sizes, and customize key placements, among other things. These features, combined with predictive text, swipe gestures, and autocorrect make the Smart Keyboard one of the most powerful typing tools available for Android. Now, it's easy to get it installed on your Samsung Galaxy Note 3.

Most variants of the Galaxy S5 come with the gesture-based Swype keyboard preinstalled. If you're into gesture typing, you probably already switched to this input method from the default Samsung keyboard (whose gesture service is nice, but it's no Swype).

With the Galaxy S20, Samsung has officially removed the Bixby button from its flagships. While it was a controversial key, in its later days, it did give us the ability to launch an app or custom action at the press of a button. There's still a way to do something like that, but now, you'll have to use the power button instead.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

A core concept that has resonated through societies of the world over the course the last few hundred years is "knowledge is power." And understanding that concept gives us the drive to push further forward and learn as much as we can on a subject. At the moment, that subject for us at Next Reality is the recently released information about Magic Leap's upcoming Magic Leap One: Creator Edition.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software.

If hearing the names of classic PC games like Commander Keen, Fallout, Master of Orion, and Wolfenstein 3D send you into a fit of nostalgia, then DosBox Turbo is the perfect app for your Android device.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

LG's arsenal of screen-off and screen-on tap gestures recently expanded into lock screen territory. Dubbed "Knock Code", this feature allows owners of various LG phones, like the G2 and upcoming G3 to unlock their phone with a series of taps on the screen. The most impressive part is that the screen doesn't even need to be on!

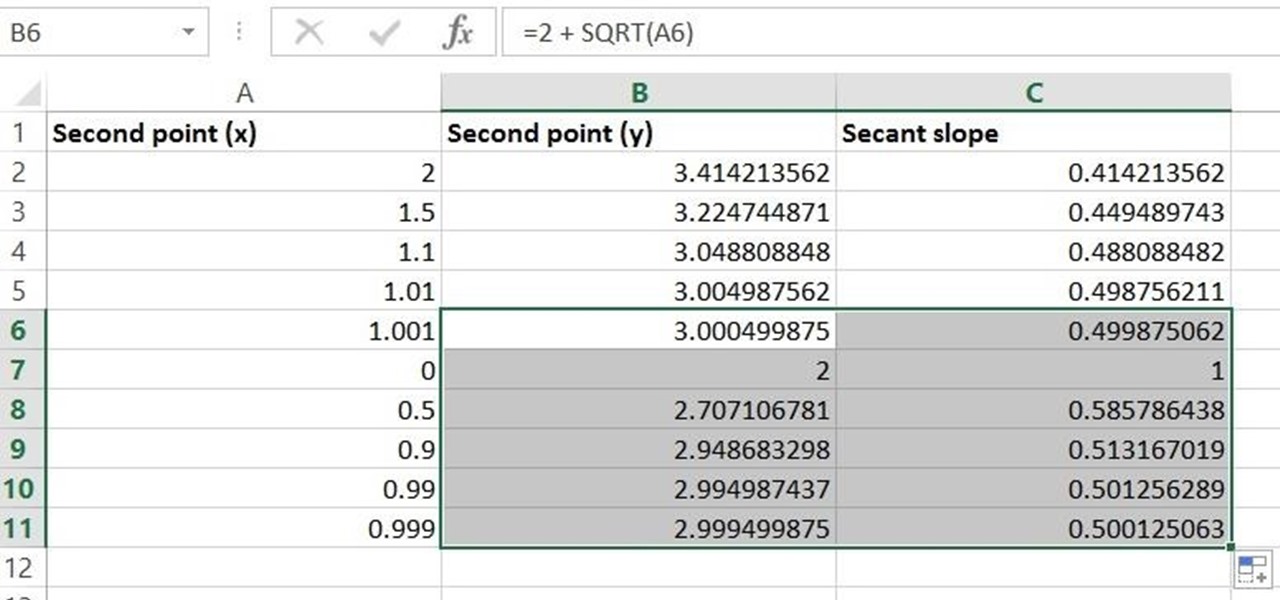
Given a function, you can easily find the slope of a tangent line using Microsoft Excel to do the dirty work. That is to say, you can input your x-value, create a couple of formulas, and have Excel calculate the secant value of the tangent slope. This is a fantastic tool for Stewart Calculus sections 2.1 and 2.2.

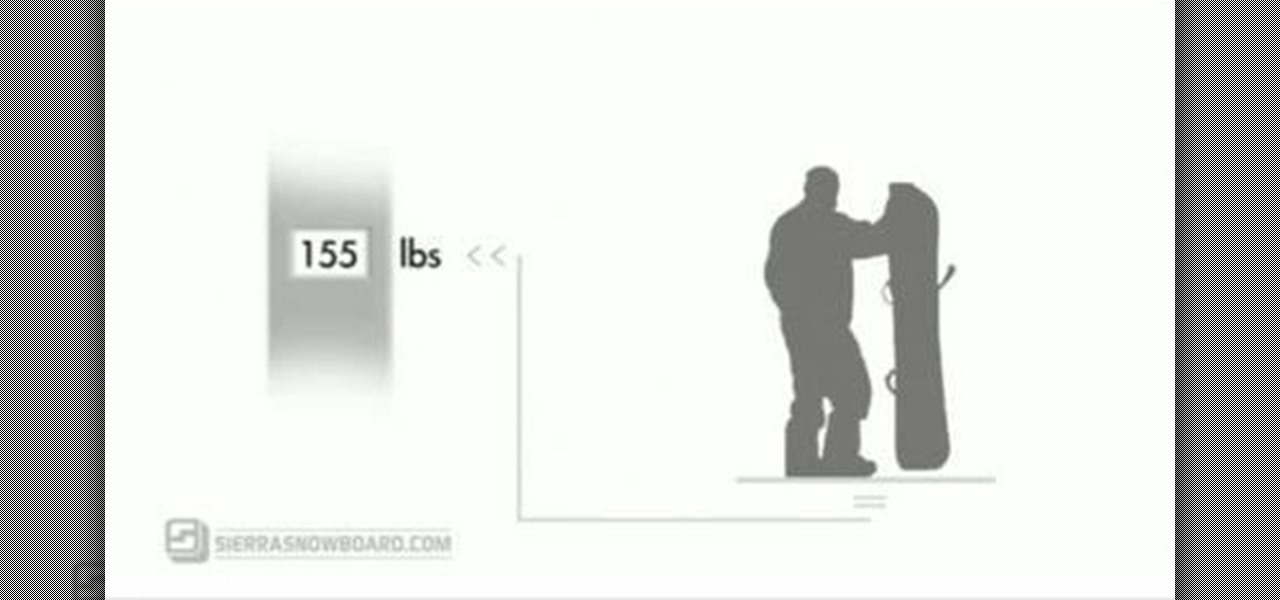
In this video, Sierra Snowboard gives us some tips on how to select the snowboard that's right for you. Each board comes in a number of different sizes, and most boards come with a size chart specific for that board. These charts can be vague, but are good starting points for selecting your size. One thing to consider is your bossy type. The weight of the rider is the primary factor in selecting the size of a snowboard. You'll notice that the height of a rider is not listed on a size chart. I...

Undo. Redo. These two actions are forever intertwined, but they're missing from the standard keyboard on Android. Accidentally delete a word, and there is no Ctrl + Z to undo this mistake. But there is finally a solution available on Samsung Galaxy phones.

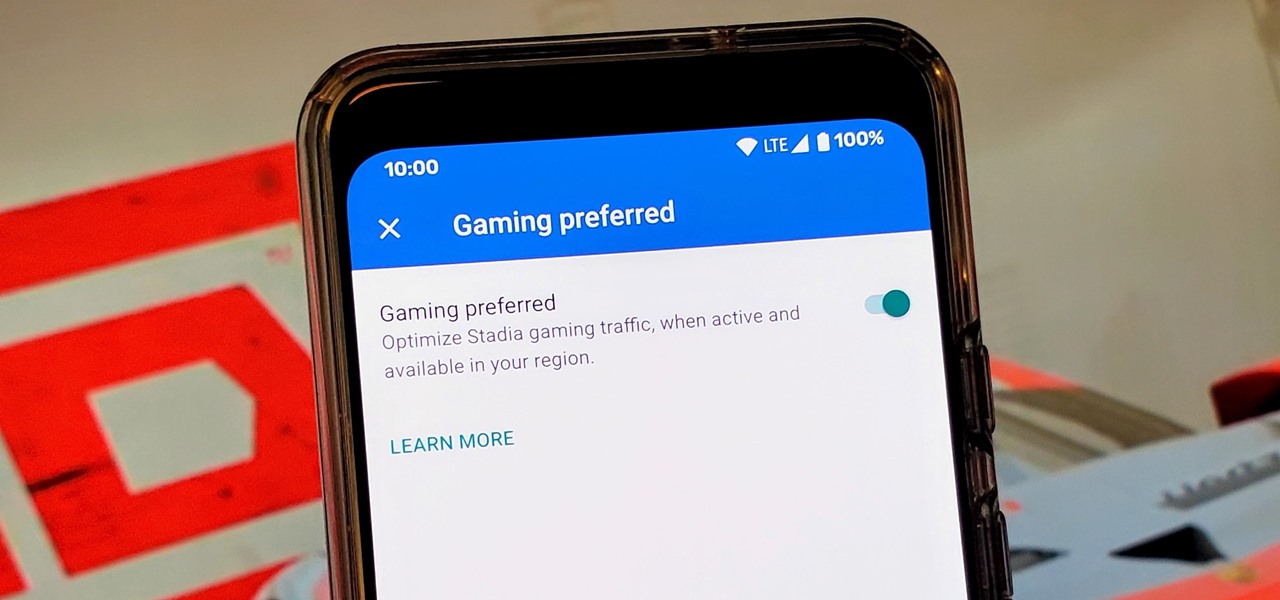
Although not quite as common today with the always-connected world we live in, you still might be having bandwidth wars in your home right now. If the internet connection in your area is mediocre, you know the feeling well. Google Stadia recommends having a 25 Mbps connection for playing in 4K, so you can expect to need at least that much to maintain a smooth, high-quality gaming session.

Your Skype contact list might contain a sea of names that make it tough to find a specific person you're trying to reach. The same goes for your loved ones and colleagues, especially if you have a common name like Jennifer or John. Knowing that, you might want to change your Skype display name to set yourself apart.

Last year at CES, RealMax blew away the AR headset competition with a prototype AR headset surpassing 100 degrees field of view.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

While there are many awesome features in iOS 12, there's one that has got the best of me and my patience. Sending photos and videos in a text or iMessage. Yes, there are a few ways the process remains the same, but if you select pics and vids right from within the Message app, be prepared to be annoyed ... highly annoyed.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to one that can complete your sentences.

One of the biggest hurdles for making touchscreen text input easy on the user has been finding a simple way to move the cursor around. With all the advancements in mobile technology, we're still left fumbling around with tiny arrow indicators or magnifying glasses when we need to add a letter to a word we've already typed. But thankfully, developer Ouadban Youssef has found a better way.

Thanks to the Edge variants, Samsung's Galaxy S phones are just a few millimeters off in body size when compared to the Note series, and just 0.2 inches smaller when it comes to displays. Now that the two flagship models are almost identical in size—with matching curved displays—there's really only one thing that separates the Note7 from the Galaxy S7 Edge: The S Pen.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...