Android phones have supported keyboards and mice for a long time, and you've even been able to use physical keyboards with iPhone and iPad models. But iOS 13 and iPadOS 13 finally include official mouse support. That means you can use a wireless or wired mouse and keyboard with your iPhone or iPad, though, a futuristic peripheral that combines the two may be even better.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's more, you get a phone with an easily unlockable bootloader, which is the first step to rooting.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

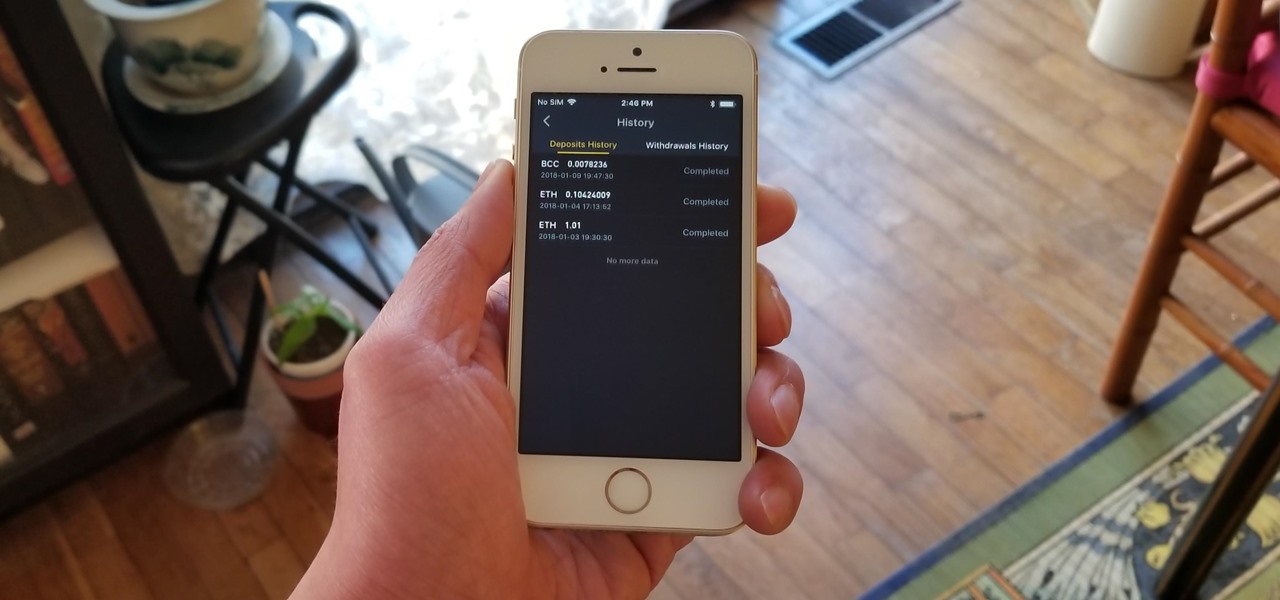
As cryptocurrencies gain mainstream acceptance, it's not far-fetched to think that we'll one day be able to buy alt coins like Ripple (XRP) and Stellar (XLM) using debit cards and bank accounts. Until then, we'll have to rely on using bitcoins and ethereum to buy digital coins. Thankfully, depositing and withdrawing cryptocurrencies with Binance is relatively hassle-free.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

One thing that makes Signal Private Messenger better on Android over iOS is that you can better secure the app with a password or passphrase. Best of all, you don't need to install an app locker to get this working — you can do it right from inside Signal.

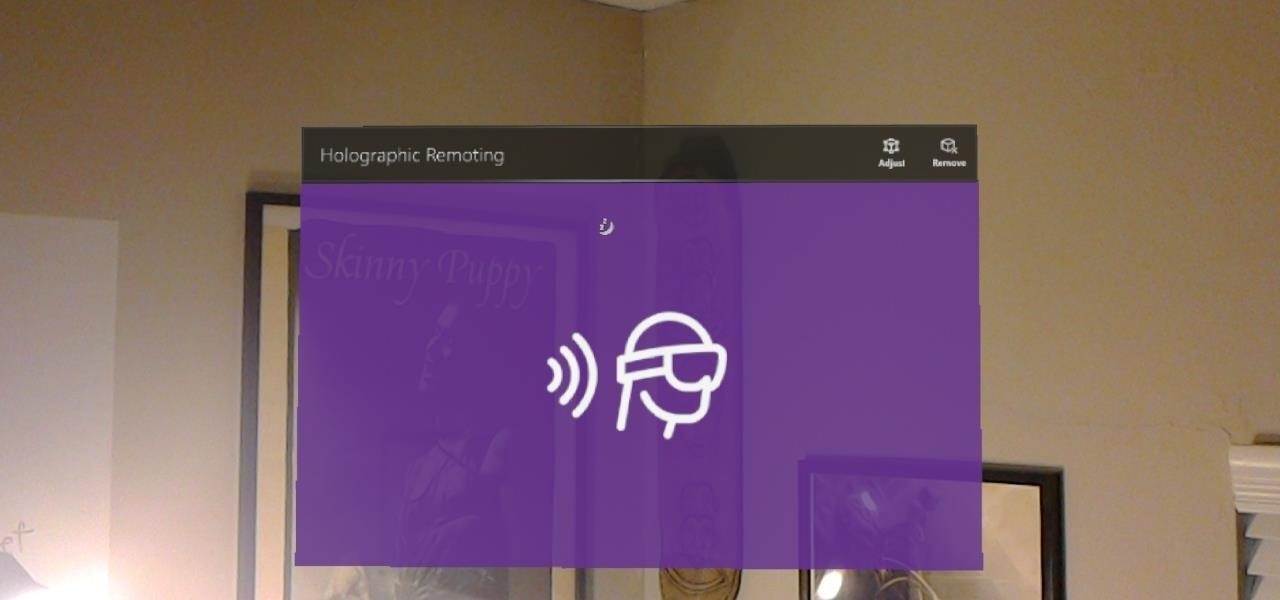
Way back, life on the range was tough and unforgiving for a HoloLens developer. Air-tap training was cutting edge and actions to move holograms not called "TapToPlace" were exotic and greeted with skepticism. The year was 2016, and developers had to deploy to their devices to test things as simple as gauging a cube's size in real space. Minutes to hours a week were lost to staring at Visual Studio's blue progress bar.

Locking individual apps on your Android device gives you an added layer of security by safeguarding app data from unwanted attention. I personally prefer using an app locker over a standard lock screen because my kids play with my phone, and they've completely disabled it after inputting the wrong PIN. So app lockers give me the right balance between giving my children access to my device, and the security of locking down my data from would-be intruders.

If you have a mobility impairment that affects your hands, arms, or manual dexterity, a smartphone's touch-based interface can almost be a barrier between you and the mobile internet. Eye-tracking software requires too much computing power for today's smartphones to handle, so it might seem as though there's no good way to interact with an Android device.

Thanks to Project-Infrared, there's now a pretty straightforward way to add motion tracking to the HoloLens: Connect it to a Kinect.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

I'll give Samsung credit where it's due—the stock keyboard on the Galaxy S5 is actually pretty nice. There's a dedicated number row that resides at the top (something that the Google Keyboard needs a hack to achieve), and various settings exist to make switching between languages a breeze.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

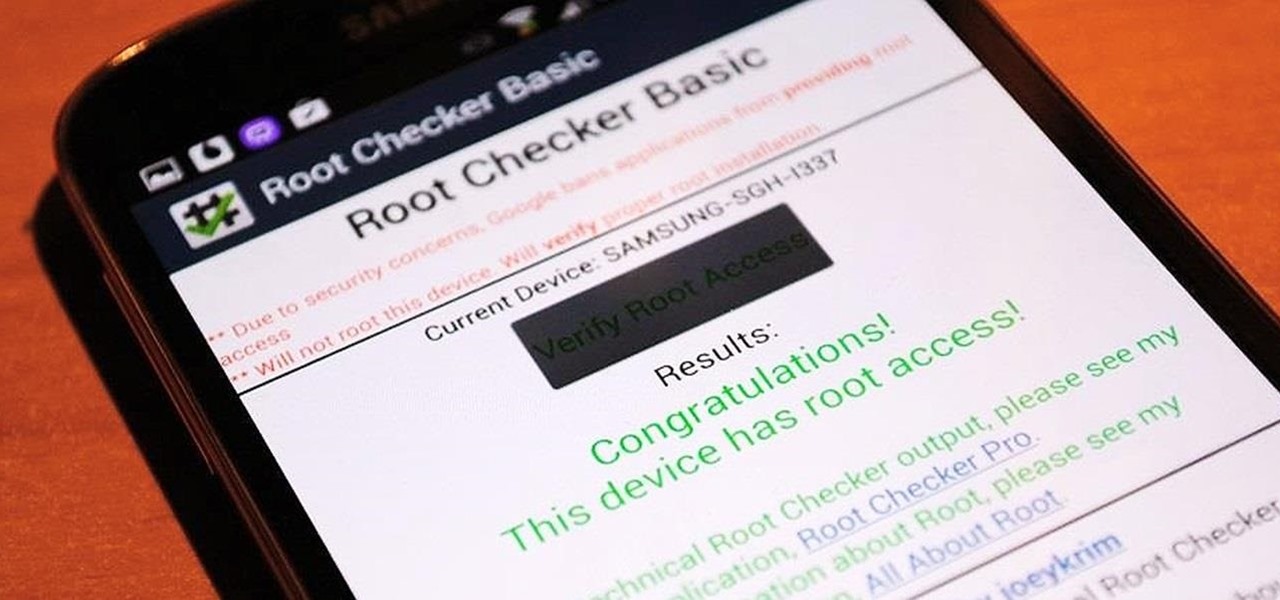
Rooting is usually the first thing on the to-do list whenever one of us softModders gets a new Android device. Unfortunately our efforts are sometimes hindered by certain obstacles; a common one is a locked bootloader.

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

Everyone in the world uses tablets these days, so it's no wonder that the Samsung Galaxy Tab has different languages built right in. To change your language on the Android tablet, all you need to do is navigate to the Settings menu.

Have you ever gotten the error message, "BOOTMGR is missing" on your PC? Well, if you have check out this video. In this tutorial, learn how to remedy and fix this problem in no time.

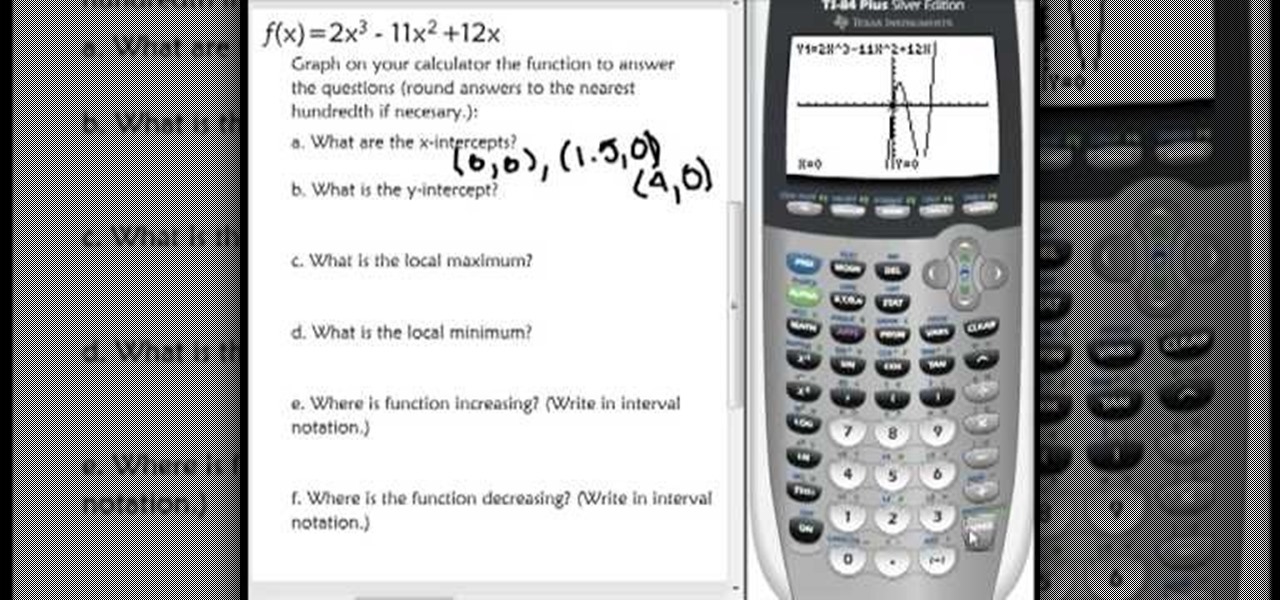
In this video the teacher shows us how to use a TI-84 plus graphing calculator to graph a function, adjust the view window, and determine the values of several types of critical points on the graph such as x-intercept, y-intercept, local maximums, and local minimums. After entering the function in the Y= editor she presses the ZOOM button and selects Z-Standard this adjusts the view window to a range of -10 to 10 on both axis. To find each of the critical points requested the teacher uses the...

Autotune your voice using MixCraft 5MixCraft 5 is the latest version of the program. The program is an instrumental, video and voice editor. We will be using the audio track. Use your best mike and record a short voice recording. Add a songy tune to it to get the full effect. Go to effect, autotune bst. Use the preset. Input auto is soprano voice, auto correct, left select pitch reference, vibrato on 0 or .1. Format amplitude at 130. Set pitch to 0. Natural vibrato needs to be at a 90 degree ...

In this video from PCRescueRepair we learn how to record streaming audio from any website using audacity. To get audacity just go to google, type in audacity, click on the link for audacity, and download audacity to install this on your computer. Also you need the LAME mp3 encoder which is on the audacity website. Now he takes you through the steps to do this task. Go into audacity and from the drop down change to stereo mix from microphone. On output adjust to max. and on input adjust the vo...

View the absolute value of a number as its distance from zero. When you take the absolute value of a number, you always end up with a positive number (or zero). Whether the input was positive or negative (or zero), the output is always positive (or zero). For instance, | 3 | = 3, and | _3 | = 3 also. This property that both the positive and the negative become positive makes solving absolute-value equations a little tricky. But once you learn the "trick", they're not so bad. Let's start with ...

Looking to change your YouTube Favorites to an mp3 to carry them with you everywhere? In this video, learn how to do so with the help of a download from dvdvideosoft.com, and this tutorial. Instructions for are listed below as listed by videomaker, vakama380:

CC, which stands for "carbon copy", is a familiar phrase in email, but can also be used in business letters and legal documents. This can be especially useful for letters you want to spend up a company or organizational chain, letting each recipient know exactly who else received the same document.

Does your child always come home with a full lunch box? Most likely they don't like what you've been packing. Give your children’s brown bag lunch a healthy punch – one they won’t trade away!

If you're not technologically savvy, don't stress. You probably want to jump right into the game, so check out this video on how to properly install your Playstation 3.

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

After exiting the mobile market, Microsoft has redirected its efforts to better integrating their services with Android. Thanks to a partnership with Samsung, that Windows integration is even better if you have a Galaxy phone.

There are a number of reasons you'd want to delete your Skype account. You may have decided to move away from the app in favor of another service like WhatsApp or FaceTime, or perhaps you want to erase your account due to an online hack. Regardless of why you might want to delete your Skype account, doing so isn't quite as straightforward as it appears.

Describing how and why the HoloLens 2 is so much better than the original is helpful, but seeing it is even better.

The iPhone's notification system has drastically improved over the years, but it could still use some work. The notifications, while useful, are all monochrome, making it hard to distinguish which app posted each alert, and that's not even mentioning the drab overall look. This is where jailbreak tweaks can come in handy.

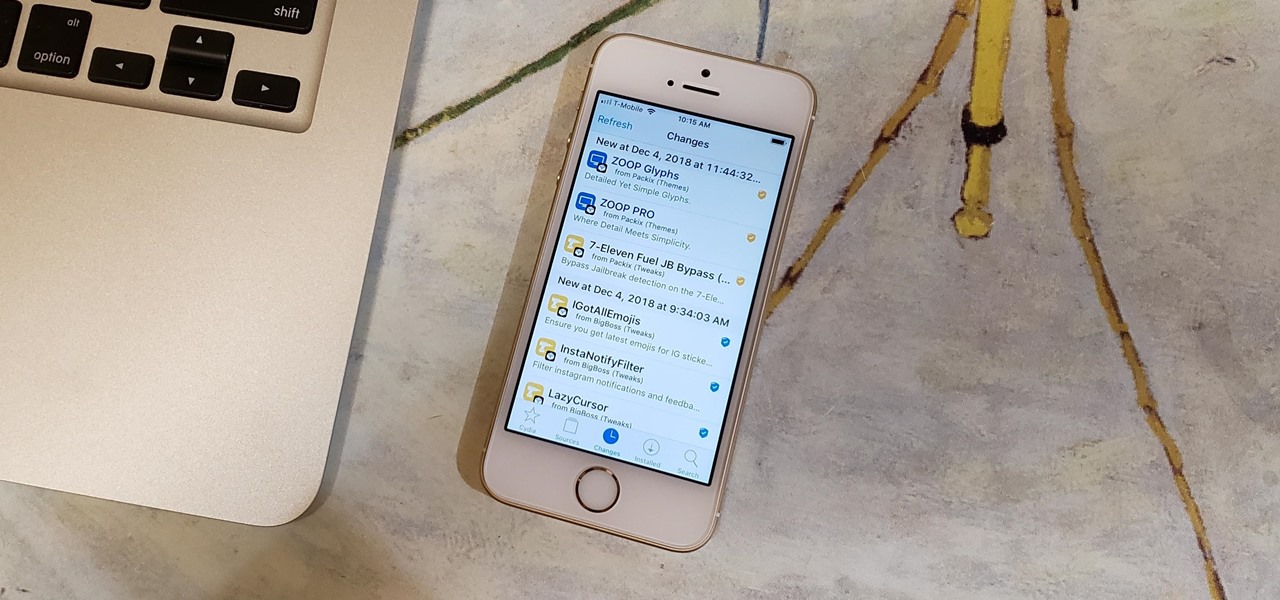
Apple has done a fantastic job of instantly patching iOS exploits through constant firmware updates to keep hackers at bay. Because of this, jailbreaking has largely been pushed to the fringes, resulting in a myriad of tweaks being abandoned by developers which, in turn, have been rendered incompatible with later jailbroken versions of iOS.

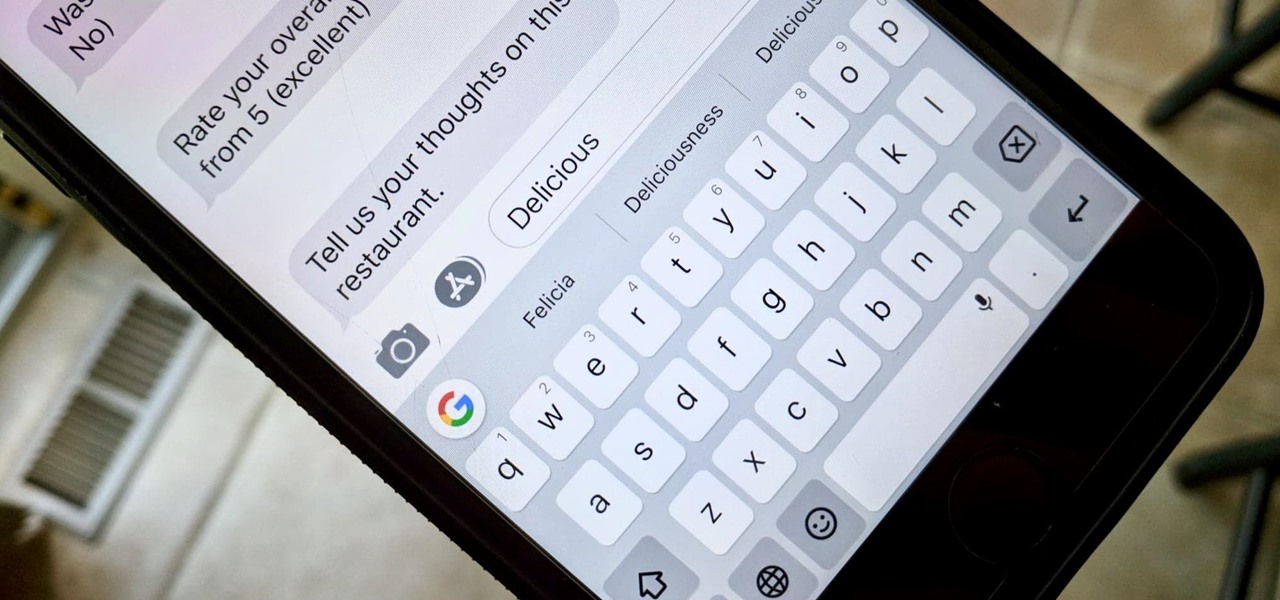
Predictive text is a common feature in most mobile keyboards these days. However, many times, its guesses are way off, sometimes hilariously so. As absurd as it can be, predictive text can also continuously suggest the same wrong word over and over. Thankfully, Gboard offers users a way to quickly remove these suggestions for good on both iOS and Android.