How To: Create and edit charts in Numbers '09
Check out this informative video tutorial from Apple on how to create and edit charts in Numbers '09.


Check out this informative video tutorial from Apple on how to create and edit charts in Numbers '09.
Check out this informative video tutorial from Apple on how to work with Excel users in Numbers '09.
In this tutorial series Mike Lively shows how to convert Wordpress into the Adobe Flex 3 application Flexpress.
John explores some ideas on how you might use VoiceThread, a newcomer in the diverse Web2.0 space, that allows you to post pictures and video online and get input from others through voice-enabled comments. VT has some really cool possibilities for the educator. For now, at least, you can get a Pro-account as an educator and set up identities to use for students in your classroom. Teachers can also use VT to post presentations with narration.
In this video, Jonathan Cohen demonstrates how to surf the web using a BlackBerry 8800. The explains how to start up the Internet on the cell phone, how to input an address, and give some hints on using the browser.

With the Galaxy S20, Samsung has officially removed the Bixby button from its flagships. While it was a controversial key, in its later days, it did give us the ability to launch an app or custom action at the press of a button. There's still a way to do something like that, but now, you'll have to use the power button instead.
Every iPhone since the 5S has come equipped with a microchip called a motion coprocessor, which collects data from integrated accelerometers, gyroscopes and compasses, and can then transfer that information to fitness apps that track physical activity. Essentially, the chip knows whether you're running, walking, sleeping, or driving — but what if you don't want it to?

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

A major software tool first promised during the reveal of the HoloLens 2 earlier this year is finally available.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.
It's not easy staying fit and healthy these days with addicting phones, oversized portions, and long workdays, to name just a few things. To succeed, it takes work, commitment, and an understanding of your mind and body — and your iPhone can help you with some of that. While Apple pushed its Screen Time tool to help curb unhealthy smartphone habits, its "Health" app can help with everything else.

In case you hadn't heard, Google is now a legit cell service provider. Google Fi has its pluses and minuses, but the biggest upside is in the pricing. Depending on how much data you typically use, there's a good chance you could save a lot of money without sacrificing coverage by switching to Fi.

With the iPhone XS, XS Max, and XR, Apple introduced dual-SIM capabilities to iOS, made possible by eSIM technology. If you recently picked up one of these three new iPhones and need to utilize your eSIM while traveling abroad, you might want to take a look at the data plans offered by GigSky.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Another AR cloud savior has emerged this week in Fantasmo, a startup that wants to turn anyone with a smartphone into a cartographer for spatial maps.

A core concept that has resonated through societies of the world over the course the last few hundred years is "knowledge is power." And understanding that concept gives us the drive to push further forward and learn as much as we can on a subject. At the moment, that subject for us at Next Reality is the recently released information about Magic Leap's upcoming Magic Leap One: Creator Edition.

Chances are, you just point, shoot, and share photos and videos on your iPhone without a second thought about how your privacy is affected. It's fairly easy to do so since the Camera and Photos apps that Apple provides seem so innocent. But there are a few things you need to know when it comes to shooting media, sharing it, and even deleting it.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.
Most of the free apps you'll find on the Play Store have ads. These ads are personalized — in other words, they're for products and services Google believes you might be interested in. The way Google knows about your interests is by collecting data from your smartphone, including your location and app usage. While personalized ads have their advantages, the collection of data is unsettling.

While augmented reality is a means for presenting news to their audiences to some media outlets, Bloomberg is interested in how the technology can improve the way journalists work.
It seems almost every carrier now has an unlimited data plan, and free Wi-Fi is now available in more places than ever before. If you want to be connected, it has never been easier — but that still doesn't mean that everyone can stream as much as they please.
If you just installed the iOS 11 beta on your iPhone, you're automatically sending your location data to Apple — even if you don't want to. Luckily, there's an easy way to prevent Apple from seeing this data if you don't want them to.

As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.
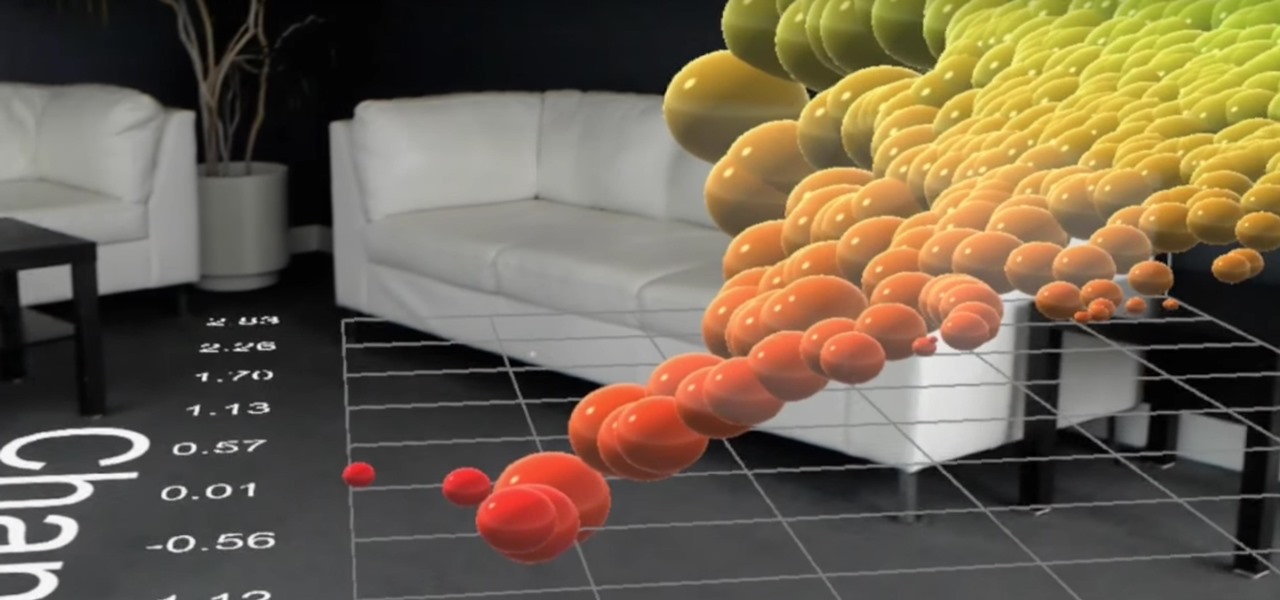
HoloLens developer Michael Peters of In-Vizible has released quite a few videos since receiving his HoloLens last year. Many of his experiments are odd and funny, but some include serious potential approaches to data visualization. In the videos embedded below, you'll specifically see stock market information beautifully rendered in different ways to help understand the data.

Everyone loves sharing pictures and quick video clips with Snapchat, but while the service itself is tons of fun, the Android app is one of the worst on the market. For one, Snapchat takes terrible photos even on high-end Android phones. And to make matters worse, the app is a notorious data-sucking battery drainer.

Ever since the update that turned Google Keyboard into Gboard rolled out, a lot of people have been noticing that word suggestions and auto-correct features are downright slow. The issue seems to affect users with multiple languages installed more than anyone, though it can also happen if you have a midrange phone or older device with only one language installed.

Our future technology has a lot of amazing possibilities, and few have more promise than augmented and mixed reality headsets. But these advancements come with several concerns over privacy, and if we don't understand them, we may lose control of our own data without even knowing.

If you tend to go over your data allotment each month, or are constantly afraid you will, Verizon Wireless is giving you chance to relax a little bit with up to 2 GB free data for two months.
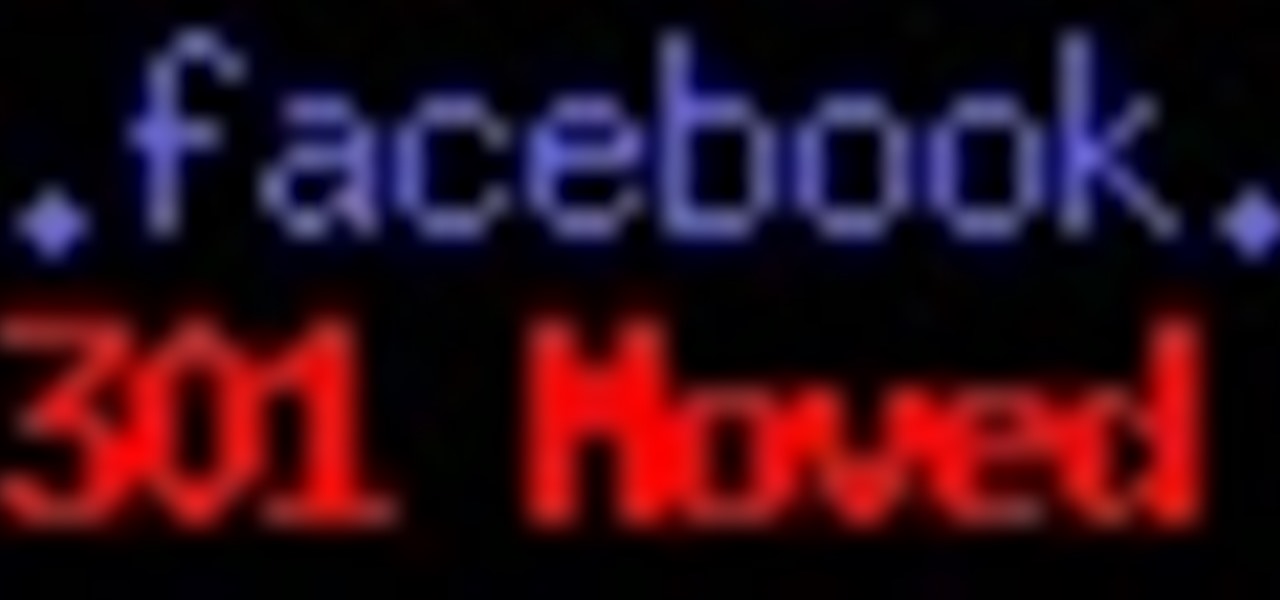
Hey everyone, this will be a quick post. Facebook does not use HTTP Strict Transport Security (A header that tells the browser to only use HTTPS when communicating with the server) on subdomains of facebook.com. That means, if someone uses facebook in a different language, the browser will attempt to connect using HTTP first. An attacker can intercept that request and serve a different page, including a fake login one.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.
Before I start a series on remote exploitation, I think we should learn the basics of Perl. Perl, Ruby, C, C++, Cython and more are languages that some penetration testers just need to learn. Perl is a great language for multiple things, sadly, like many other scripting languages, it is limited by the environment in which it is designed to work in.

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...
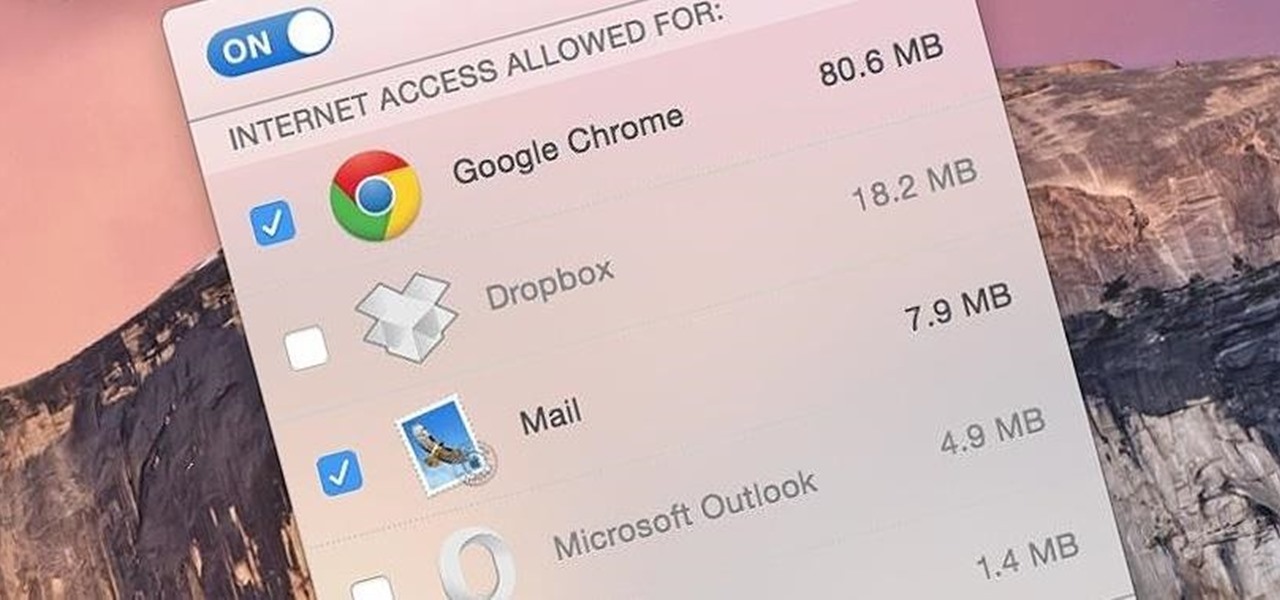
I'm lucky enough to have internet access on my laptop practically everywhere I go because of my mobile hotspot plan. All I have to do is enable the personal hotspot feature from my iPhone and I can surf the web on any Wi-Fi enabled device. But of course, there's a catch.

Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.
Recently, a group of Duke University students got together to tackle an age-old problem with mobile devices. You see, mobile data coverage isn't exactly ubiquitous, and many folks have restrictive mobile data plans, which means internet connectivity is not always an option.
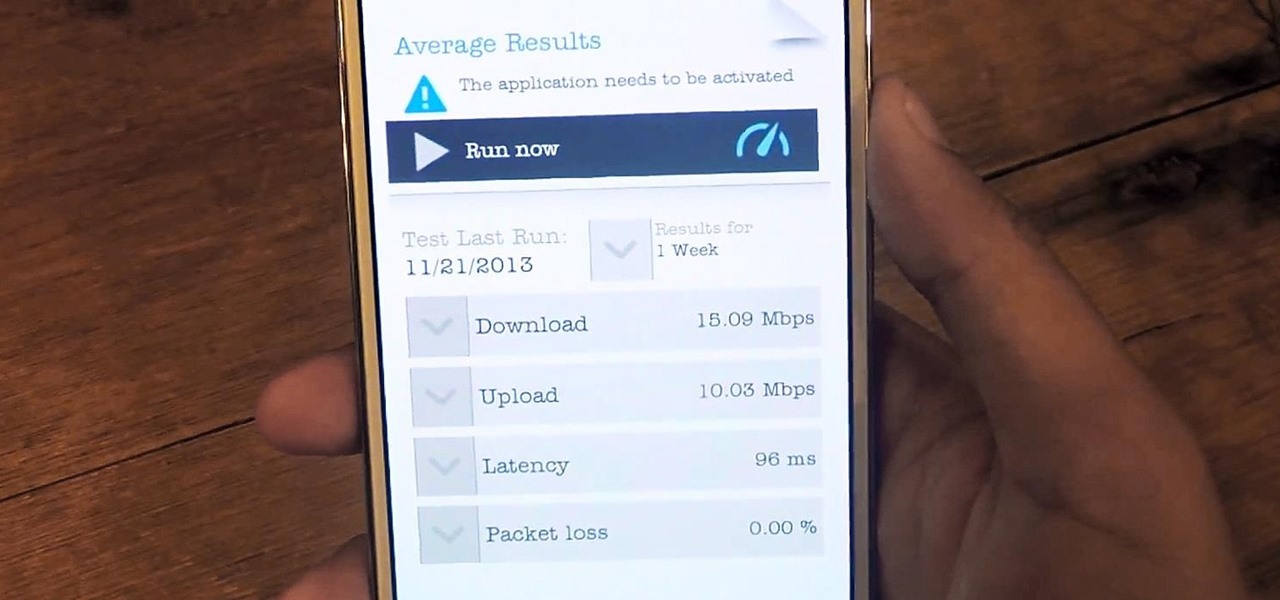
As the protectors of all things good, the Federal Communications Commission is usually busy behind the scenes pissing off Slim Shady, giving out fines for indecent nipple exposure at certain halftime events, and warning the NSA about losing any "confidential" phone information they steal from us.

If your clock will not respond to input, or does not regulate temperature, you will probably have to replace your oven electronic control board. You can follow the steps in this video to help you do this easy repair.

Free stuff is pretty cool. Free internet is even cooler—and free internet that is actually free is the coolest. If you would rather avoid sitting in a Starbucks and having to listen to hipsters discuss the proper length of cropped jeans, then this should be of interest.

Tons of iPhone 5 users with Verizon Wireless hit the message boards last week complaining about their phones sucking down massive amounts of cellular data when they were actually using a Wi-Fi connection. Of course, that means Verizon customers could have been getting charged for cellular data they weren't actually using.

This video tutorial is in the Education category which will show you how to calculate standard deviation with TI graphing calculator. First you got to enter the data in to the calculator. Go to stat and click on enter. This will edit a list. Now you type in these numbers: 50, 20, 33, 40 and 55. Then press stat and click on enter. This will bring up the 1-var stats page. Press the "2nd" button and L1, because all our data is in L1. Click on enter and you will get all the data that you will nee...