BitLocker. What is it? And what can it do for you? Well, it's a handy new feature built-in to Windows 7, and it can help protect all of your data from loss, theft, or hackers. It's the easiest way to make sure your documents and files are safe from the devil's hands.

In this tutorial, we learn how to make your first graph in Microsoft Excel. First, open a new graph and enter in your data. Click and drag down from the original date you enter to have the other dates automatically entered in. Enter the rest of your information, then highlight all the data. Go to the menu and click "insert", then "chart". Now, go through the chart wizard to select what kind of chart you want to make. When you are finished entering all your preferences, change your values so t...

If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 20th installment in his "Excel Statistics" series of free video lessons, you'll learn how to take raw quantitative (numerical) data and figure out how to group it into classes so that you can have categories an...
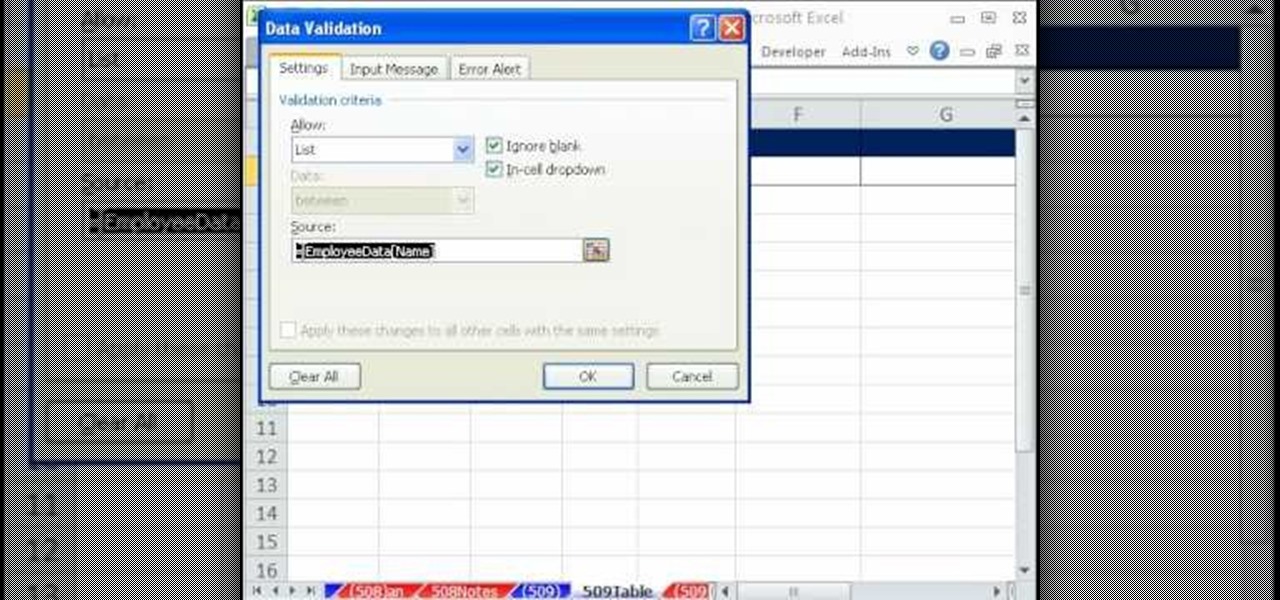
In this video tutorial, viewers will learn how to create a table for the VLOOKUP function in Excel. Create a dynamic table for the VLOOKUP function as well as a dynamic lookup area so that as you add new data or columns to the Lookup table. Create dynamic ranges using the Excel Table feature and Table Formula Nomenclature for the Data Validation drop-down list, the VLOOKUP table and the MATCH table. See an IF function formula that creates new labels as new columns are added to the lookup tabl...
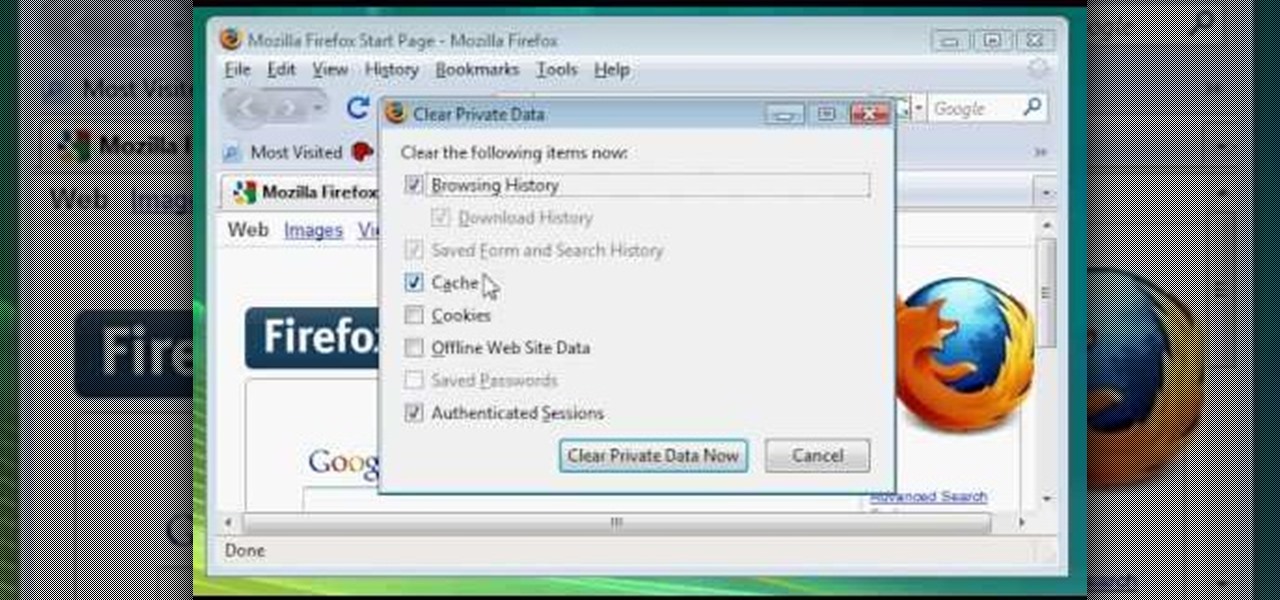
Here Danny Beales shows you how to quickly clear your Firefox cache and cookies. To clear your Firefox cache, do the following: Go to Tools Clear Private Data Select which data you would like to have cleared, and click on Clear Private Data. Your cookies and/or cache has been cleared. Remember to do this from time to time, because it will help speed up your browser's performance as well as keep harmful cookies from tracking your browsing.
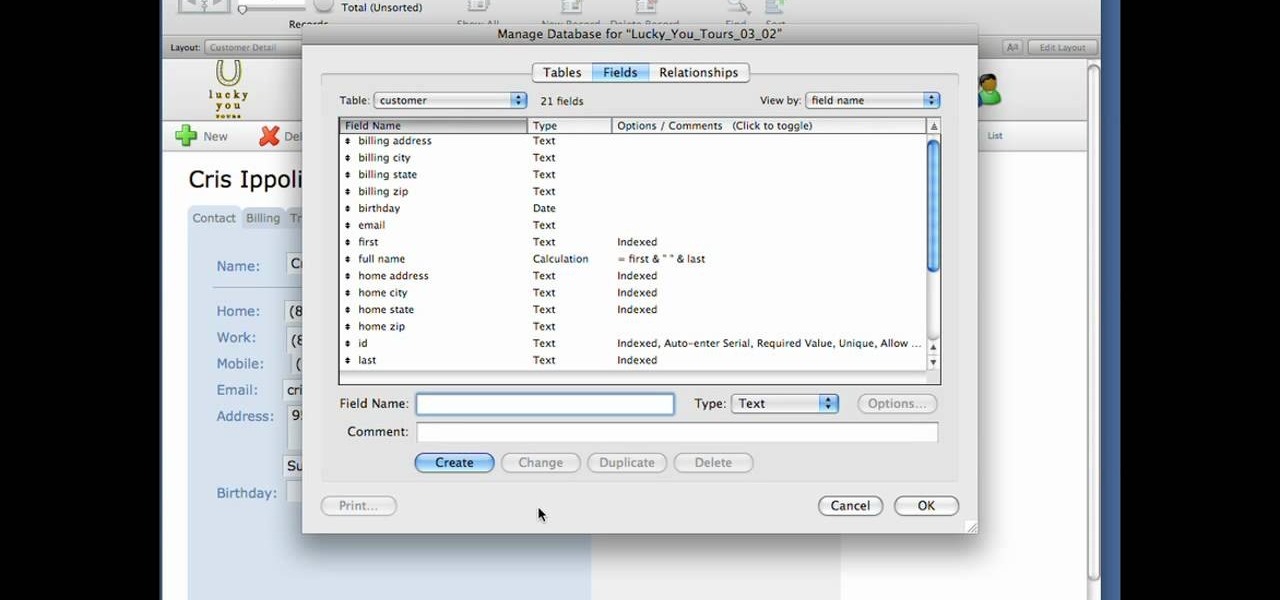
If your into data based business,then this one's for you. Text field's are very much important while making a data based solution in FileMaker Pro 10.You can go to file menu>manage>database and there is the field's tab. Text field is used for storing text and no other such use. Text field's can hold up to 2GB of information. It can help to store raw data and formatting information, i.e., color,point size as well as type face.

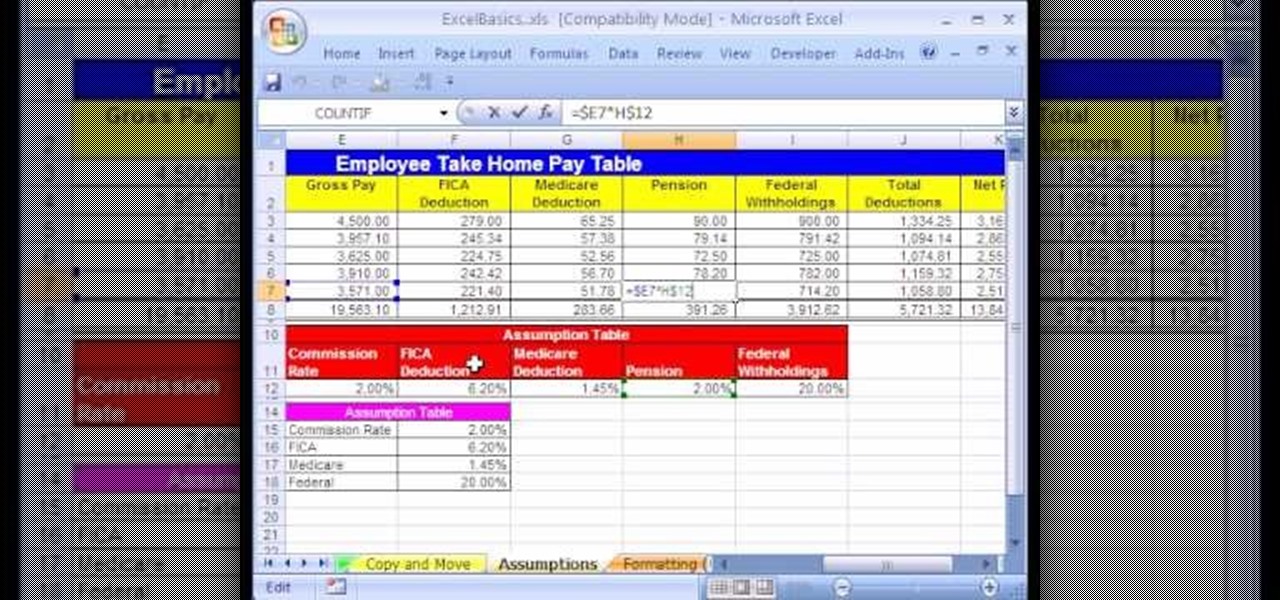
In this Excel basic video the instructor shows how to setup a spreadsheet and use cell references. Cell references are used in Excel to refer to other cells in a formula. When a formula contains data based on the cell reference the formula auto generates the result each time the value in the cell changes as the formula contains only the reference to the cell and not the actual data present in it. In this video the tutor goes on and shows how to write a few basic formulas using cell references...

MotionTraining gives an overview for using Microsoft Excel for beginners in this video. This video gives a rundown and overview of the basics of this spreadsheet program: from typing in the columns and rows, adding dollar signs to data, and how to make basic calculations. MotionTraining will show how to make text stand out with bold and italics, adding colors to your data, and how to make a grid appear during the printing process. Creating various charts of the data in the spreadsheet is also...

In this video tutorial, Chris Pels will show how to share data in between JavaScript and server-side code by using a hidden field in an ASP.NET page. Next, learn how to use the RegisterHiddenField method in server-side code to programmatically create a hidden field on the client. In addition, see how to programmatically create a HiddenField server control for sharing data on an ASP.NET page. Finally, use the RegisterArrayDeclaration method to create a container in server code for storing mult...

This easy to follow silent and accurate video will guide you quickly and easily through what you'll need, (like a Power Supply, a sound system that has a Subwoofer Pre-output and a High Input adapter, which may already come with your amp.) First learn what colored wires should be connected to simulate your PC starting. Then connect the amp to the power supply to simulate the car Head-Unit starting. Once the power issues are handled, the video assists you with connecting your audio input. It i...

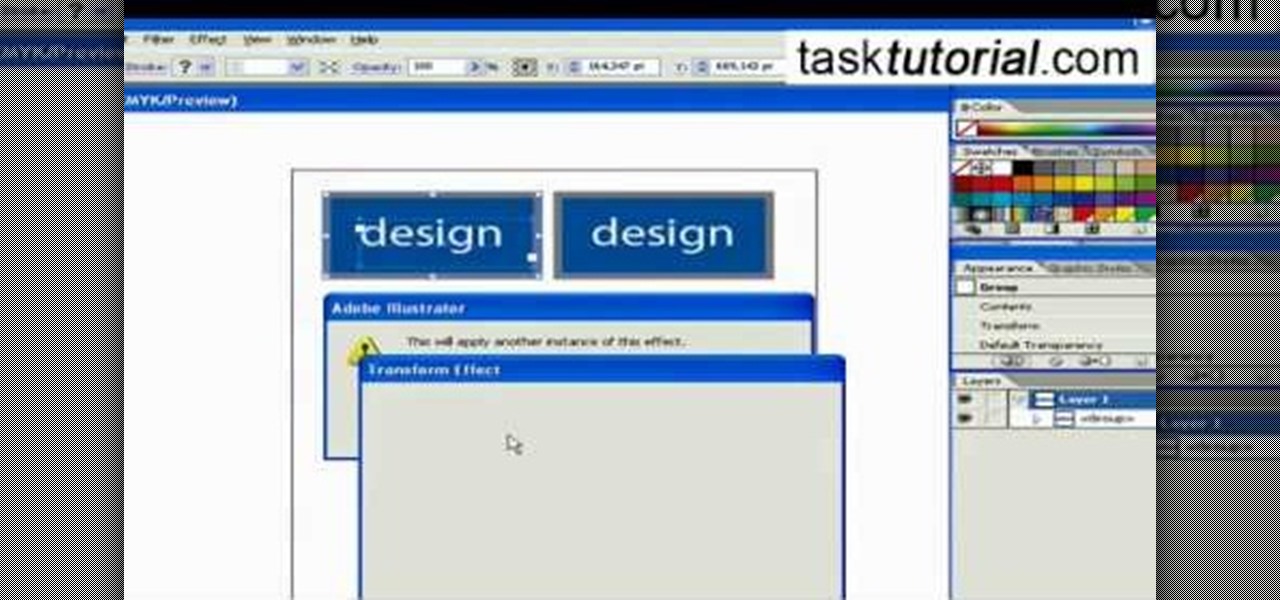
This video takes us through the procedure of creating a transform effect in Illustrator. First, choose a rectangular box and fill color in it. Input some text inside the box. The font and the color of the text can also be changed. Then position the text properly. Make a group of the shape and text. Now go to effect and choose transform. Transform is a very powerful effect which lets us create duplicates. Now select the number of copies, for example, one copy. Select preview. Now set the point...

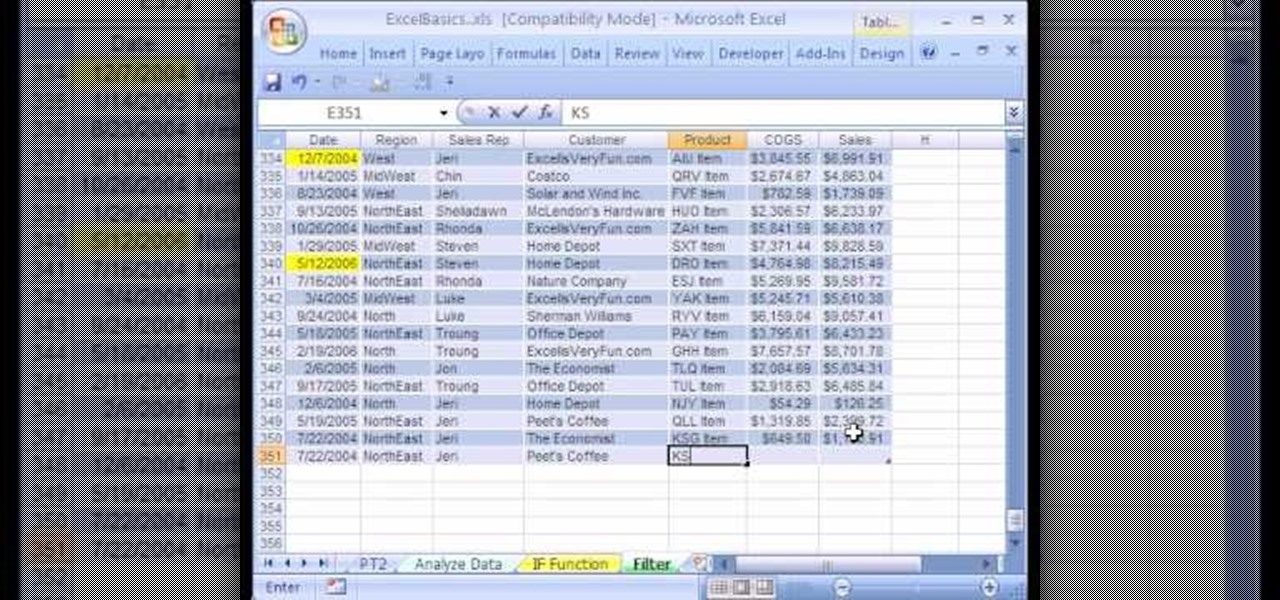
We're on sheet, tab, filter. We want to talk about filter, but we also want to talk about an Excel table or list. It is simply a data set with field names at the top, records in rows, no blanks anywhere and no other data sets touching this data set. When we convert to a table, it does a lot of amazing things. The new keyboard shortcut is "Ctrl T". If data is set up correctly, it will work. Click Ok. You can build a function based on a column of data, i.e. "Alt =" which is the shortcut for sum...

Materials needed: Altoid mint tin, 9 volt batter and connector, switch, 7812 voltage regulator, 12 volt computer fan, carbon filter and 2 pieces of screen. Wire the battery connectors. Solder all of the following: Negative connector to the switch, wire to the switch, ground wire of the voltage regulator to the middle wire, output for the 7812 to the fan, positive lead on the 9 volt connector to the input on the 7812 and the negative from the 7812 to the negative on the fan. Test. Put all the ...

So you want to make your own video game using Flash CS4 and Actionscript 3. We applaud your chutzpah. This video will walk you through what should probably be your first steps: importing a sprite character, making them move around in response to keyboard inputs, and making them animate depending on how they are moving. Once you have this established, you can move on to creating enemies to fight, environments to wander, and all the other elements that make a good game.

Have you ever wondered why your cat does wacky things like head butt you? Do you wish you and your cat could speak the same language? With input from an expert animal behaviorists, you can! In this video, Sara gives you the low down on why your cat is so aggressive, why he won't stop scratching your furniture, and how to interpret your cat's meows. Now you can finally understand what exactly is your cat is trying to tell you. Here you'll find a brief introduction to some common behaviors you ...

Data makes the world go round. It has gotten to the point that it's considered the most valuable resource, perhaps even more important than oil. Businesses use data to collect critical information about their users and improve their services; governments utilize it to improve things like public transportation; doctors analyze data to find more ways to save lives.

Data analytics is crucial to the operations of every modern business. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics. Experienced professionals that can project manage data initiatives are in high demand.

We know our Null Byte readers would like to see some iPhone-hacking scenarios on the site soon, but until we get some of those up, we understand that some of you actually use an iPhone as your primary phone. If that's you, and you would like an easier way to get information from point A (your iPhone) to point B (your computer) and vice versa, there's an all-in-one tool that can help.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

After reviewing the international plans for major US wireless carriers, it became obvious they're all pretty bad. Your data is heavily restricted, requiring a daily fee which can cost an extra $100+ on a seven-day vacation. That's when I learned about Google Fi, and how for most travelers, it's the best option.

Every step in the evolution of computing brings an in-kind leap forward in user input technology. The personal computer had the mouse, touchscreens made smartphones mainstream consumer devices, and AR headsets like the HoloLens and the Magic Leap One have leveraged gesture recognition.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

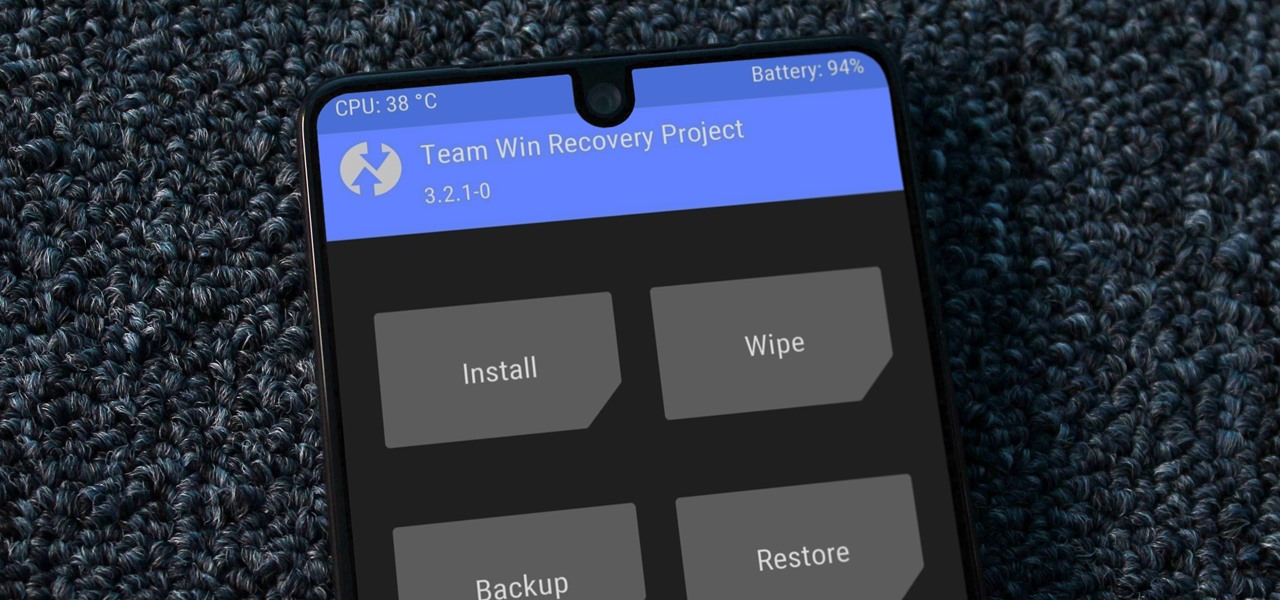
For modders, there are few tools more important than TWRP. TeamWin's custom recovery makes flashing mods like Magisk, Xposed, and custom ROMs incredibly easy, and it lets you root your phone at the press of a button. On top of that, it can make complete backups of your phone in case you mess up. That's why, for Essential users, this should be the first mod you add.

One of the main reasons Authy was able to top our list of the best two-factor authentications apps was its ability to transfer access to a new device. This feature ensures that whenever you get a new phone, you don't lose all your tokens. However, if the process is done incorrectly, you can leave your account vulnerable.

If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your account becoming compromised.

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.

Apple released the third beta of iOS 12 for developers on Tuesday, July 3. The update comes exactly two weeks after the release of the second developer beta, which introduced a variety of fixes as well as new issues, and just one week after the release of the public beta. Public beta testers received this iOS 12 update on Thursday, July 5, labeled as public beta 2.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

Chrome is the browser of choice for millions of iPhone and Android users, largely thanks to its user-friendly interface and native Google support. But with concerns over sharing private information with massive companies growing, many people are starting to want a little less Google integration in Chrome.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Verizon has long been king in the wireless provider market, but recently it has had to step up its game in the data department. A limited data plan — with supposedly superior service — was no longer cutting it for customers. Many of whom left to take up the sweet, sweet offers of competitors like Sprint and T-Mobile. This past fiscal year, Verizon had a net loss of customers in the first quarter. Something that has never happened to them before.

In a race to make self-driven cars mainstream, Intel announced today that they've bought Israeli microchip technology company Mobileye for $15.3 billion, setting the stage for Intel to dominate a large portion of the driverless market.

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

The highly anticipated VR headset hasn't been on the market long, but there's an issue that has some consumers, and even government officials, concerned about the Oculus Rift. You probably guessed the issue surrounds privacy and the extensive, not-so-secret way that it's collecting your personal data. The privacy concerns came about as various customers and media outlets took notice of the rather lengthy Terms and Services that pop up once you strap yourself into the Rift headset.

Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!