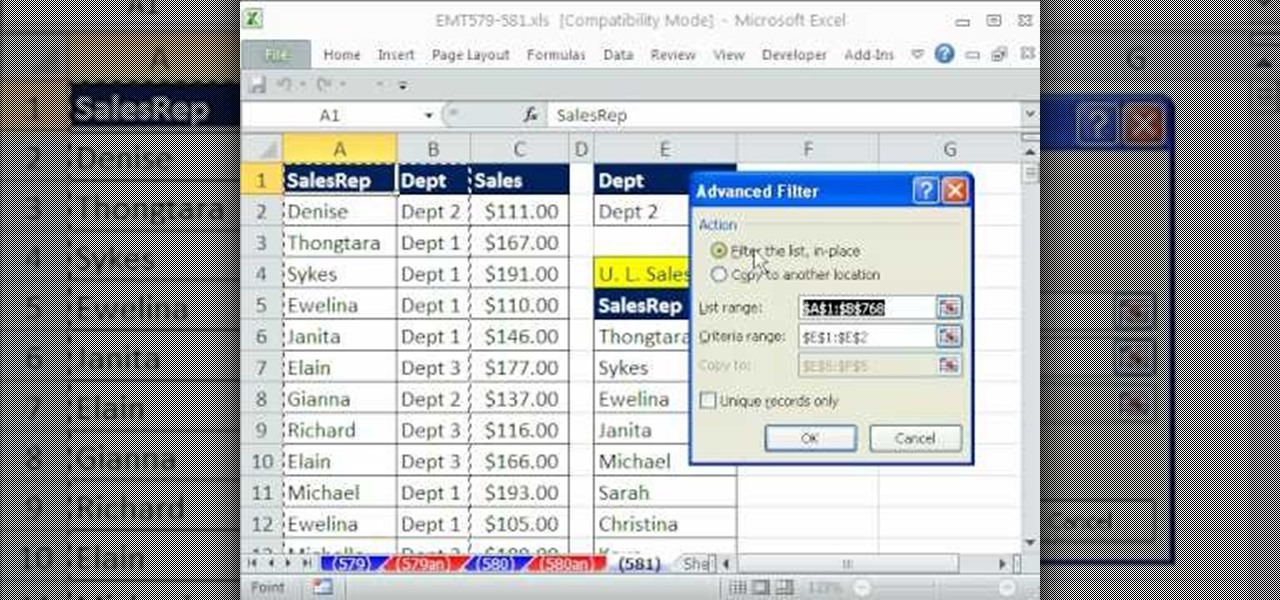
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 581st installment in their series of digital spreadsheet magic tricks, you'll learn how to use the advanced filter tool with criteria to extract a unique list of employees for each department from a huge data set with transactional records.
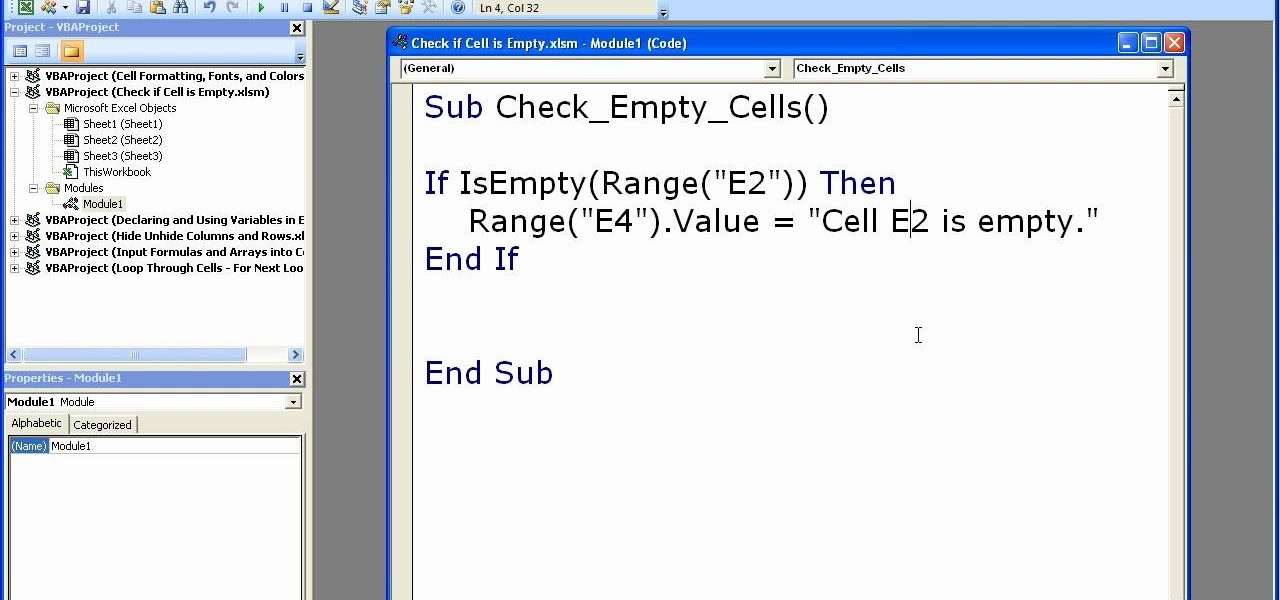
Microsoft Excel is used to store and work on data by storing them in rows and columns in tables. You can use a macros to check if a cell is empty. To do this you have to know two short cuts. The first is the VBA Window short cut which is Alt + F11 and the other one is View Macros short cut which is Alt + F8. So open an Excel spread sheet and insert some data into a small table. Now create a macro for this tutorial. You can use and IsEmpty() functions to check if a cell is empty. Use this func...
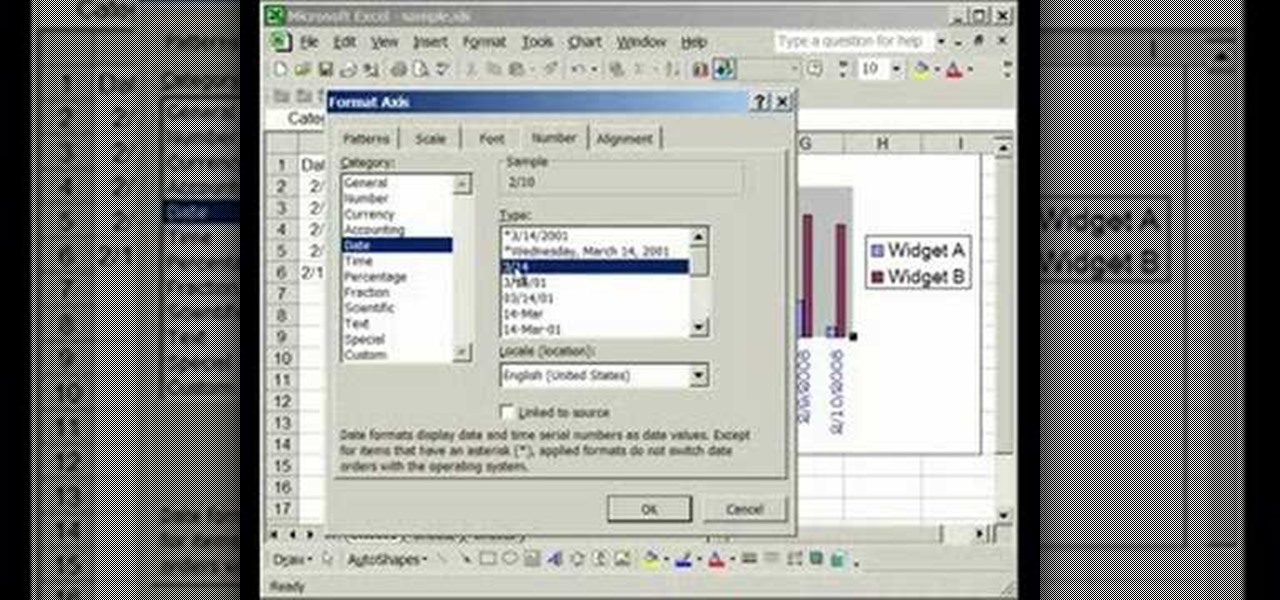
This video is about formatting the charts in Excel especially the x and y axes. The video begins by selecting a chart and right clicking the dates at the bottom of the data points. The format axis window pops up and by making changes to the style, color and the weight of lines given in the patterns tab, you can change the way the x-axis looks like. You can also change appearance of characters appearing close to the x-axis by selecting options in the font menu. You can also change the format o...

RAID, or Redundant Array of Independent Disks, lets you divide and replicate data among multiple hard disk drives for information storage security. This video tutorial demonstrates how to install Ubuntu in a RAID 0 array. Before starting, you'll need at least 2 hard drives and an Ubuntu alternate installation CD. RAID 0, or striped disks, let's you install an operating system, such as Ubuntu, on a partition, while using others for data storage, as illustrated in this instructional segment.

Open Microsoft Office Excel. Across the top notice letters (columns), along the sides are numbers (rows). The columns and rows can be extended by highlighting sections and right clicking and choosing the high of the row. You can also select to add a border, and change the orientation of your cells.

In this Computers and Programming video tutorial you will learn how to delete temporary internet files in Internet Explorer 8. The video is from FreeComputerRepair. Click on Start -> control panel ->network and internet connections -> internet options. Now the internet properties dialog box opens up. Here you go down to browsing history and click ‘Delete’ button. This will open up the Delete Browsing History window. Here you check all the data that you want to delete. If you don’t want to del...

In this video the instructor shows how to create charts and graphs in Microsoft Word. First, open the Word document and select an area to insert the charts. Now go to the Insert tab in the ribbon and select the Chart icon. The Insert Chart window opens up with various chart templates. There are various categories of charts like Line, Pie, Bar in the left hand side. In the right hand side you can see the sample charts available and you can select any of them that you want. Now it transfers you...

This video demonstrates how to reformat a hard drive and perform a clean installation of Windows XP operating system. The tutor first advises to make a back up of everything, including the drivers and my folders. He explains various methods by which one can take the backup of the data in a system. Now he shows how to format the C drive where you can now install Windows. He also shows software that is used to take the backup of important data before formatting. This video shows how to reformat...

Custom optioned installation includes the following: Copy the files to an external hard disk before starting your installation, then you will reinstall your programs by hand by using the windows easy transfer and transfer the data into the hard disk.

In this tutorial, Mike Lively of Northern Kentucky University gets you started in getting the Adobe Air Content Management System up and going.

For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and management of data in a system's database. The Attack, known as Sql Injection, manipulates Sql statements before they are sent to the Sql Server, allowing the Attacker to create, change, or retrieve data stored in the database.

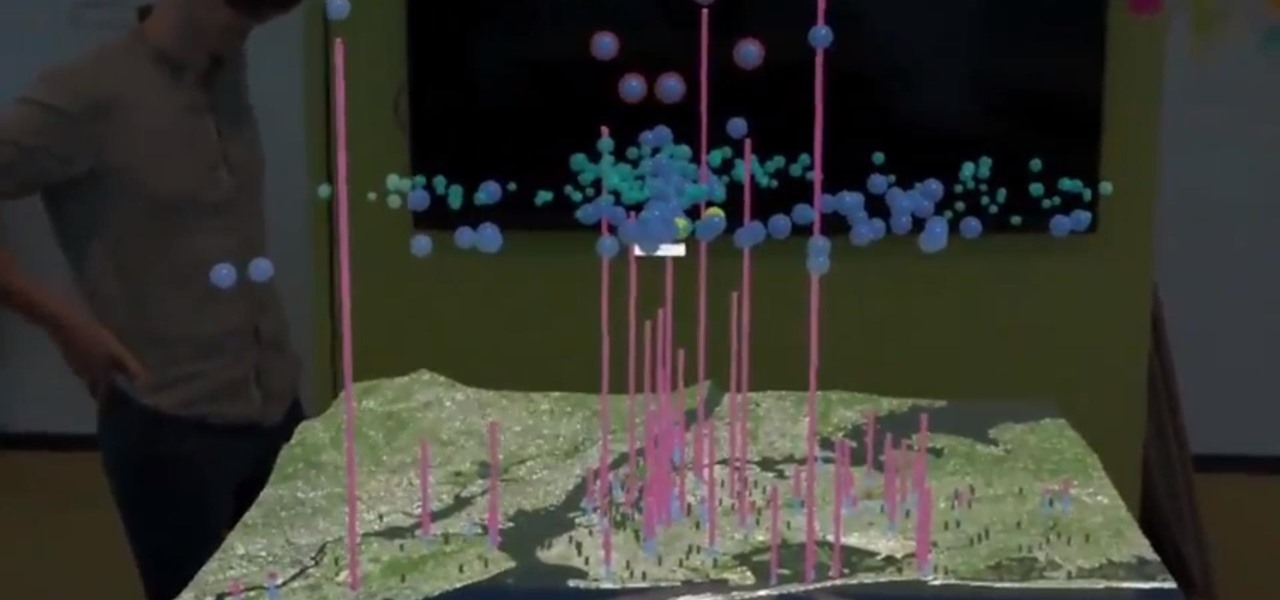
We're living in the age of Big Data. As the primary force behind everything from targeted marketing campaigns and online search algorithms to self-driving cars and even space exploration, massive sets of complex data stand at the heart of today's most exciting and important innovations.

If you have a limited mobile data plan on your iPhone, you know how tricky it can be to stay within your given allotment. Large app installs and updates, 4K resolution videos, and photo backups can waste precious data resources in no time. And apps like Apple News, Facebook, Mail, and Netflix eat data like it's candy. But you can nip the problem in the bud by restricting data hogs from your cellular network.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

Google just released the first version of the next major Android update. Early Android 11 builds will only available as developer previews, so you can't just sign up for the beta program and install the update as an OTA for the first couple months. That said, it's still pretty easy to get.

Apple's ARKit has built a considerable lead in terms of features over Google's ARCore, but Google's latest update to ARCore adds a capability that makes the platform a bit more competitive with ARKit.

Like last year's beta release of Android Pie, Google has allowed the Android Q Developer Previews to support some non-Pixel devices. Announced at Google I/O 2019, there are 15 non-Pixel smartphones eligible for the Android 10 Beta, including 2017's Essential PH-1.

Project Fi, Google's MVNO, is running a new promotion on the latest and greatest from LG. From July 16 until the 29th, whenever you order and activate the LG G7 ThinQ or LG V35 ThinQ, you will receive a $300 service credit. When you do the numbers, that equals a minimum of three free months of service.

Earlier this year, with the Developer Preview, we got a tantalizing glimpse of Google's upcoming Android 9.0 Pie and a whole slew of new features that comes along with it, such as iPhone X-like gestures and improved security features, to name a few. With its announcement at Google I/O, Android Pie just got a lot more accessible.

Setting up a new Android phone can be a pain. Although Google has some automated features, it does not restore everything. When it comes to transferring certain types of data like files and SMS logs, it's even trickier. By following our steps, you can be sure that you all your data will follow you to your new device.

This month, the power of artificial intelligence will be coming to more augmented reality developers as a leader in the game and 3D software development space and a major force behind the current school of cloud-based AI have officially announced a new partnership.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

When most people first become aware of Kodi (formerly known as XBMC), they hear about its ability to stream illegal content. But the real Kodi community knows that it's much more than just a haven for pirated material — it's an all-in-one media player that addresses the majority of home theater needs, particularly for those that decided to cut the cord.

While Meta Company has agreed to a settlement in its lawsuit against a former employee and his company, they find the tables have now turned on them in the form of patent infringement allegations from another entity.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

If you've ever wanted to live in the Matrix—or at least the iconic digital rain data visualization that Neo saw when realizing he was, indeed, the "one"—you can now do that with the Microsoft HoloLens. Just download The Red Pill.

North American users get a raw deal when it comes to Sony devices. For some reason, the critically-acclaimed Xperia lineup of smartphones is hardly ever available here, whereas in Europe, the Sony Xperia Z series is one of the most popular flagship devices around.

Welcome back, NB community, to my series on sorting. I introduced in my last article the concept of complexity. When I say complexity, I'm talking about time complexity.

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

Welcome back my friends !! Today we'll go through the second part of this C# series

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

You encounter this problem many times, when you plug your flash drive, and suddenly you find that all your data has become shortcuts everywhere!!!

Hello guys, today I wanna share how to create a drag and drop with listbox using VB.net. Just copy and paste the following code under public class.

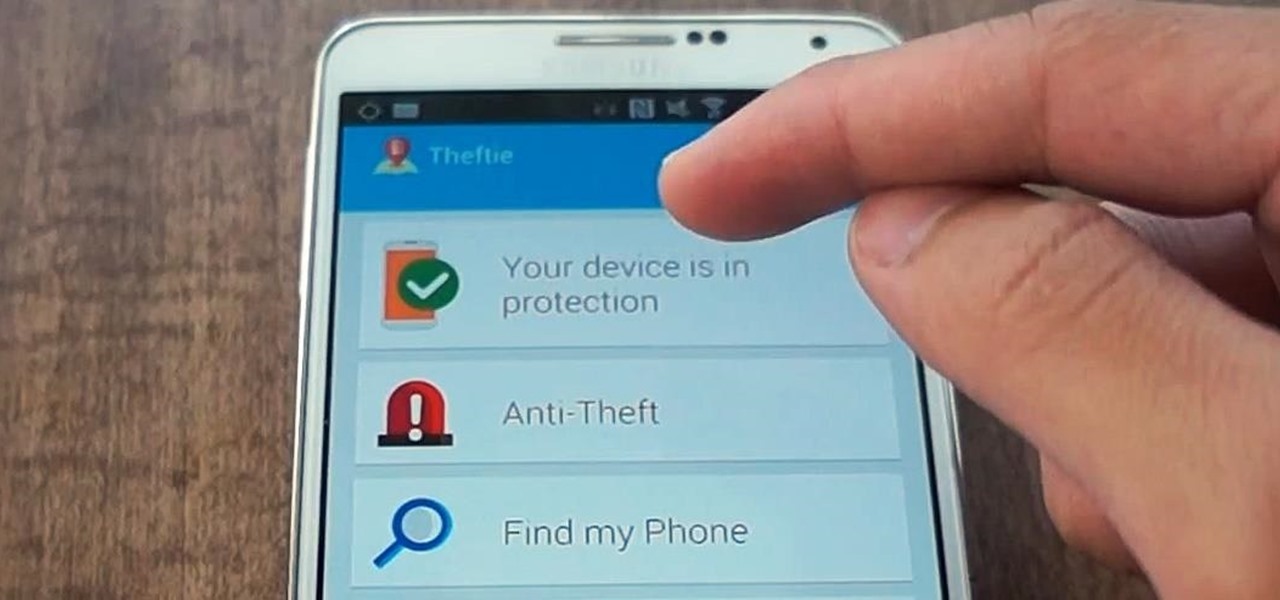
When you misplace your Android device, finding it with the Android Device Manager, or even better, Whistle Me, can help you find it no problem. But what about when your phone is not just hiding under the couch cushions? Your worst nightmare just came true. It's officially gone.

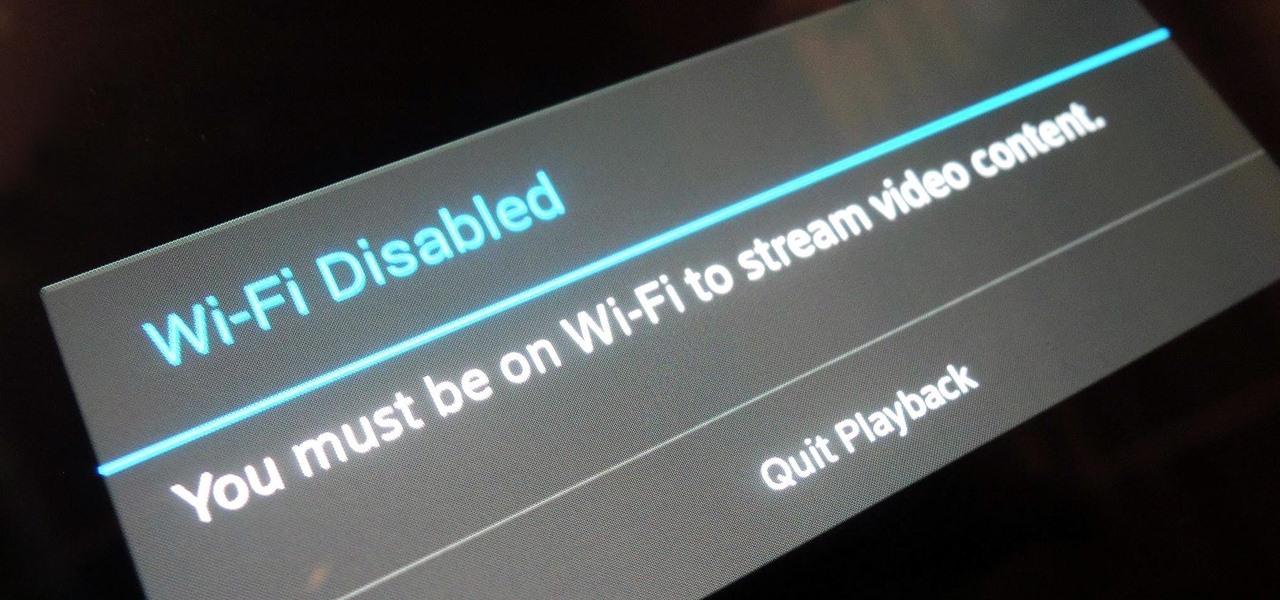
For any multitude of reasons, some apps require you to be connected to Wi-Fi in order to function properly. This could be because they would rather you have a stable connection to enjoy their content, or that they don't want users complaining about the amount of data being guzzled from carrier data plans.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

Welcome back, my greenhorn hackers!