Selling your old iPhone to make way for the latest generation? Before you get all Ebay happy, make sure to take a quick look at this video, which will demonstrate how to completely erase all data from your iPhone - including your contacts from the SIM card. Your friends will thank you for it.
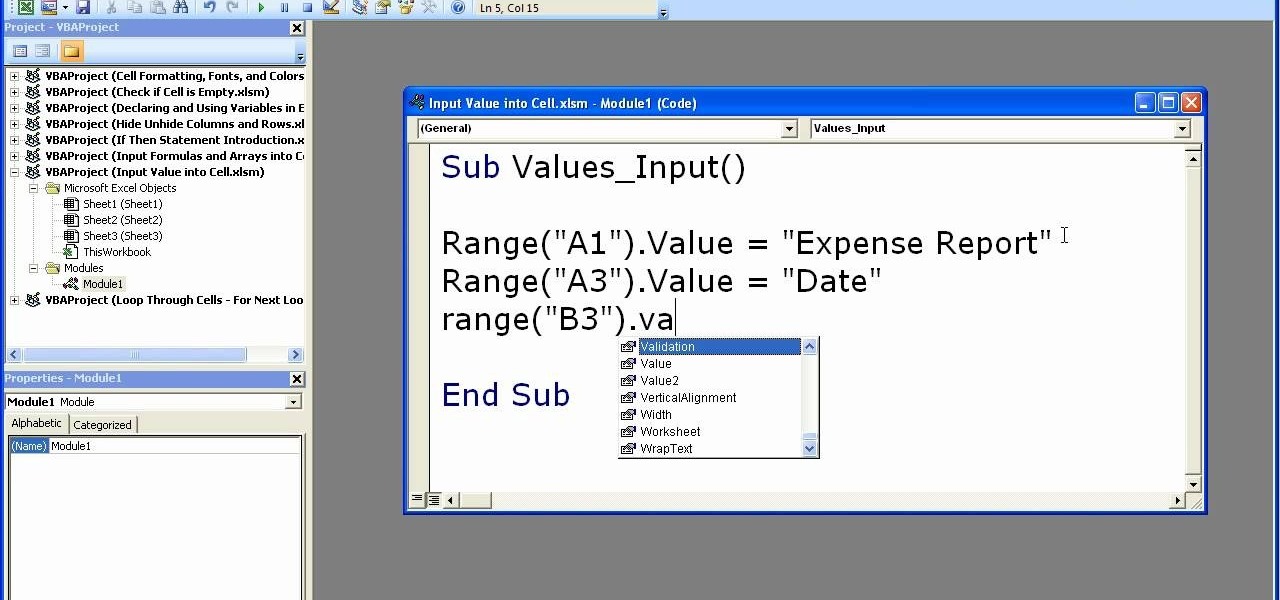
This video shows how to enter values into cells using Excel macros and Visual Basic. This includes a sample Expense Report that is used in this demonstration. In this demonstration, we will create the macro that inputs a title as "Expense Report", Three columns i.e. "Date", "Item" & "Amount", and the summery field as "Total Expenses", as well as the formulas located at the respective cells. Now, we're going to use two keyboard shortcuts i.e. "Alt + F11" to open-up the VBA window and "Alt + F8...
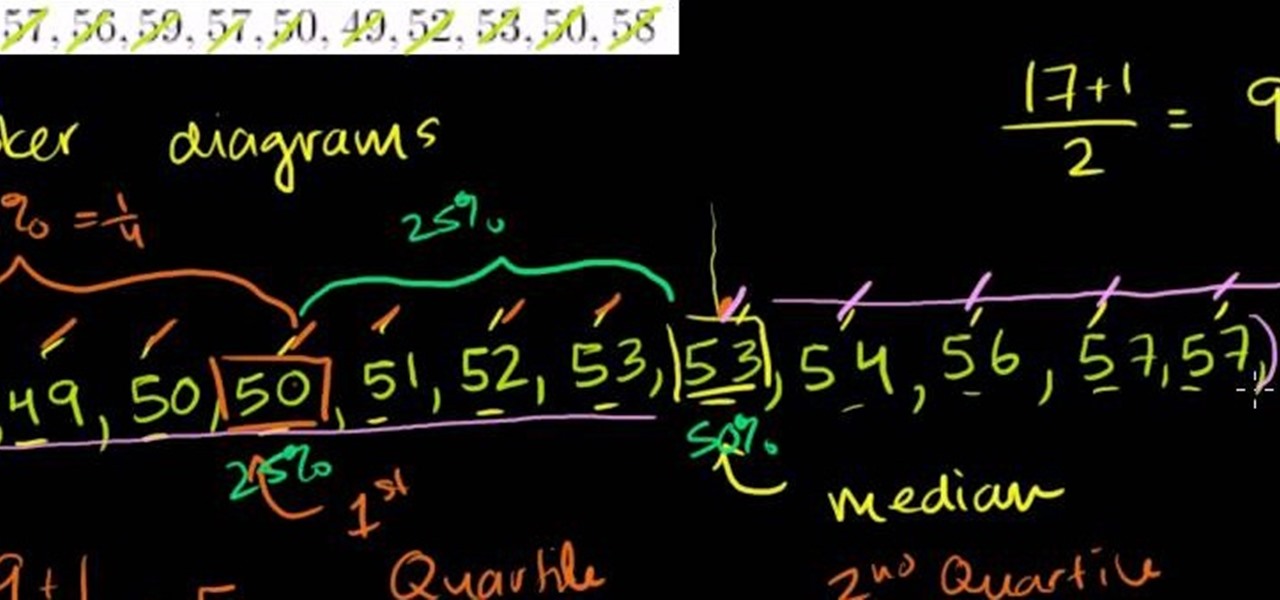
From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free statistics tutorials, you'll learn how to use visualize data by graphing it in a box-and-whisker diagram.

You may have lost your files but you needn't loose hope, too. In this episode of Lab Rats TV, Andy and Sean show you how to recover your deleted data (and your marriage!) using oranges. For detailed instructions on recovering your own lost data, take a look at this tech how-to.
Have sensitive data that you want to make sure you securely delete? Or maybe you're getting an external drive ready to recycle or to give to a colleague. In this video tutorial, you'll find instructions for securely emptying your trash and also securely delete the contents of an external hard drive. For more, and to learn how to remove data from your Mac computer securely, watch this video tutorial from Apple.

See how to use CSS and JavaScript to visually design style sheets for publishing XML and database data in Altova StyleVision, a visual style sheet designer for rendering XML and relational data in multiple formats. In this video, you'll learn more about how StylevVision interfaces with CSS and JavaScript.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 675th installment in their series of digital spreadsheet magic tricks, you'll learn how to do data validation using a custom logical formula with 2 VLOOKUP functions that will change when different products are entered. For example, if shirt product is entered, the data validation will let only values between $50 and...

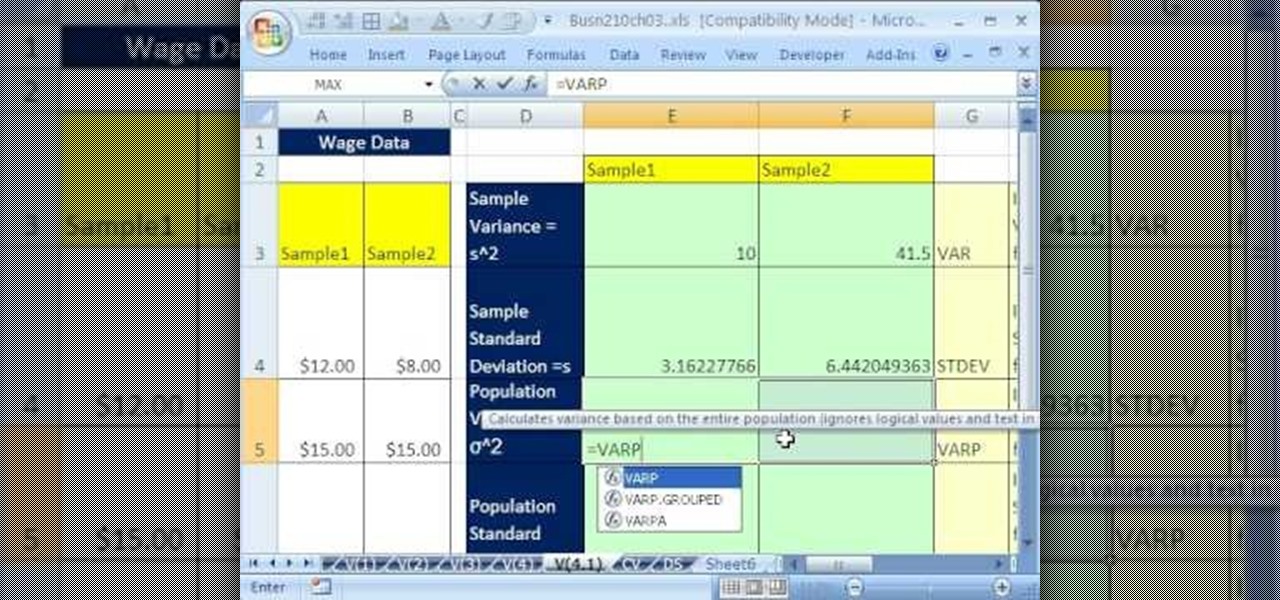
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 41st installment in his "Excel Statistics" series of free video lessons, you'll learn how to calculate deviations, variance and standard deviation for a sample and a population using Excel tables and the VAR, S...

In this video the man describes of the circuit bending of Yamaha pss 140 synthesizer. This is a good model it's a FM synthesizers. It got many songs , many cool rhythms,nice trumpets and it is working real nice.Here he states that it is important for power supply or else we don't need batteries.First thing we have to do is open the case and we can see the wires related to battery supply but he doesn't need batteries. Keep the case aside so that you can get free space. Remove the screws so tha...

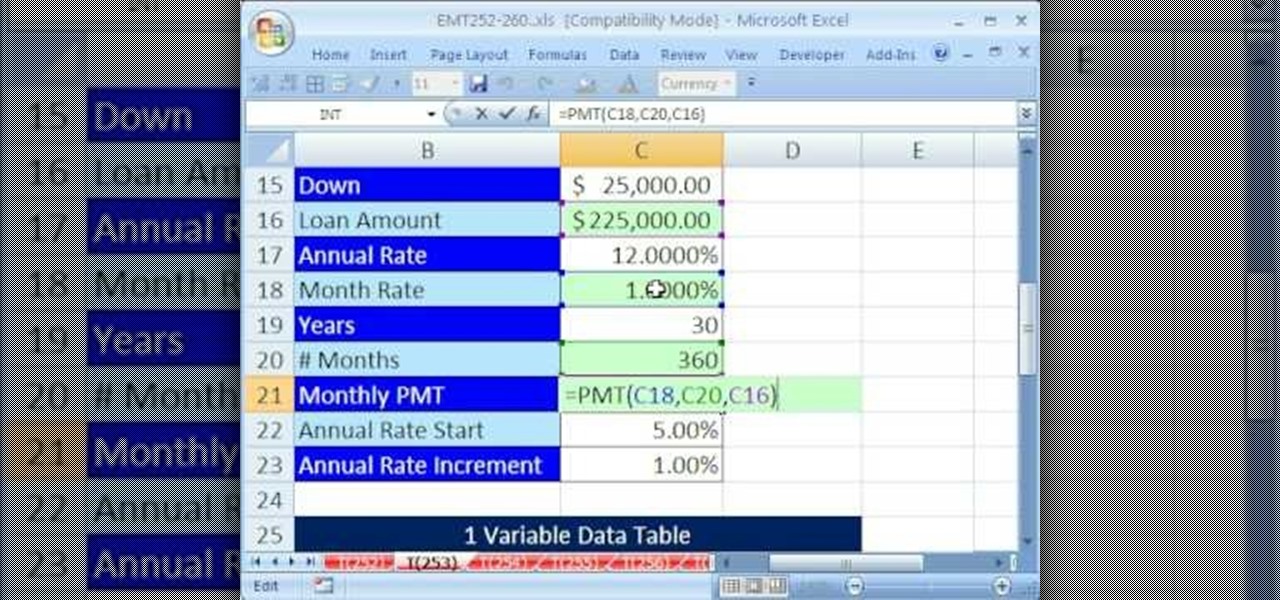
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 253rd installment in their series of digital spreadsheet magic tricks, you'll learn how to use a data table for what-if analysis. You'll also learn about the PMT and see the formula equivalent to a data table.

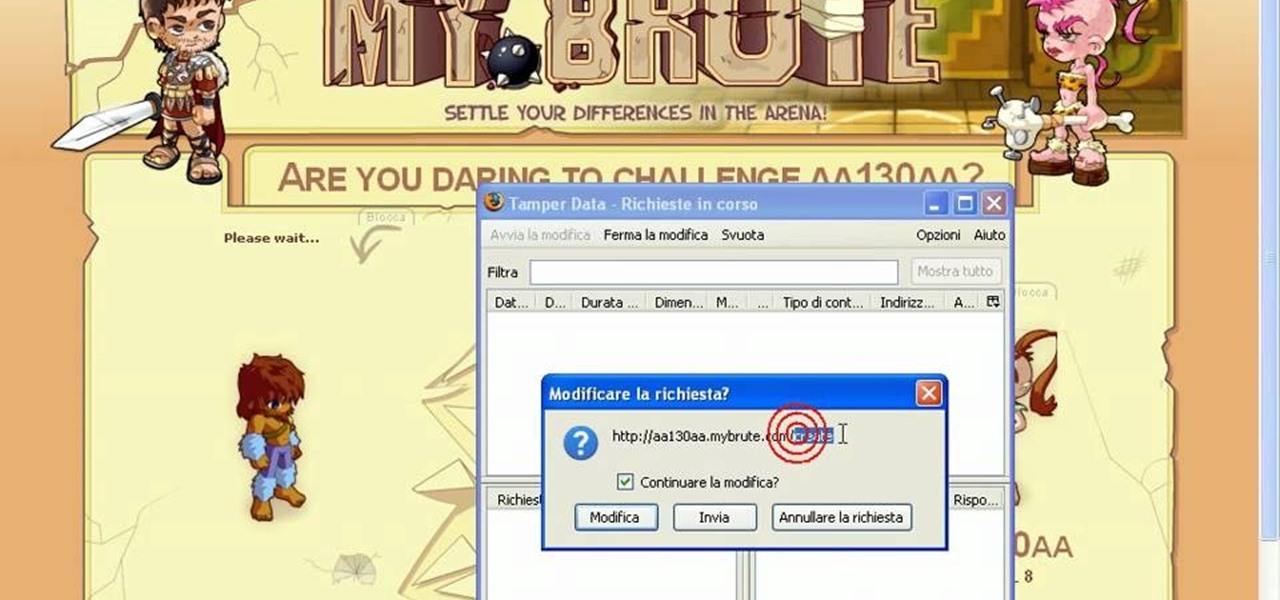
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to cheat MyBrute for a bear (05/08/09). This is the easiest way to get a bear!

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

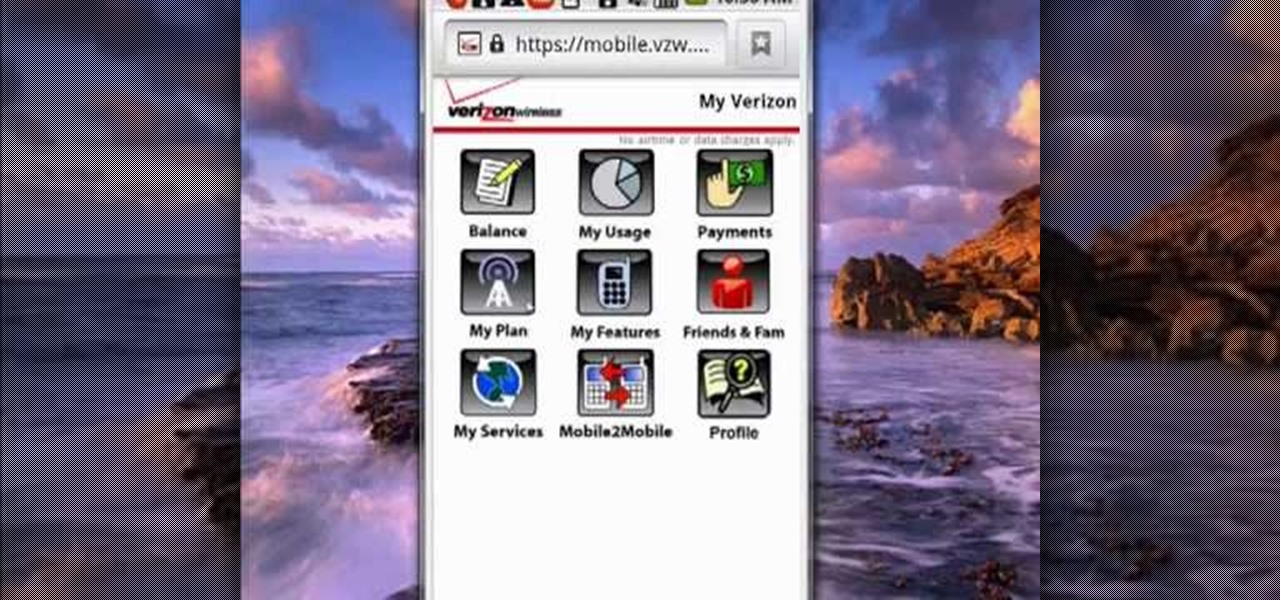
Want to monitor your Verizon Wireless service and data usage from an Android phone? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started keeping an eye on your own minutes and data transfers, take a look.

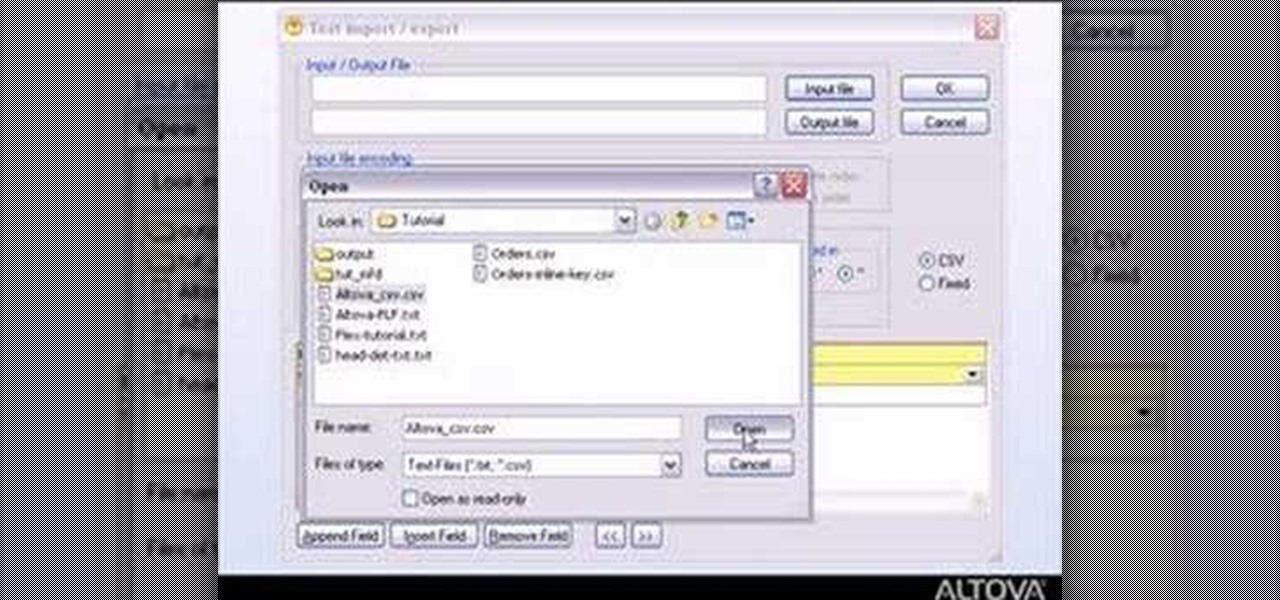
MapForce supports flat files as the source and/or target of any mapping involving XML, database, EDI, web services or other flat file data. In this how-to, you'll find instructions for mapping data from arbitrary text files (such as log files, CSV, fixed-width, and other legacy data sources) to databases and XML files.

MapForce includes support for the two most popular EDI formats, UN/EDIFACT and ANSI X12. In this how-to video, you'll learn how to use MapForce to map and convert data between EDI messages (X12 and UN/EDIFACT) and XML, databases, or text files. Learn to map EDI data with this how-to.

If you're new to DreamCoder for MySQL, one of the first things you may want to know how to do is export data from a remote MySQL database. Happily, this tutorial will walk you, step by step, through the process. To get started exporting MySQL data with DreamCoder, take a look!

In this Linux tutorial, you'll learn how to write data to, and retrieve data from, optical discs like CD-ROMs and DVDs as well as how to write .iso disk image files. Get started burning your own media under the Linux Mint desktop distrubtion with this how-to.

Before you go out to protest, understand what you are facing. Sometimes these demonstrations become infected with looters and rioters, which could mean interaction with law enforcement and potentially arrest. And if your phone is on you, it can be used as a tool against you.

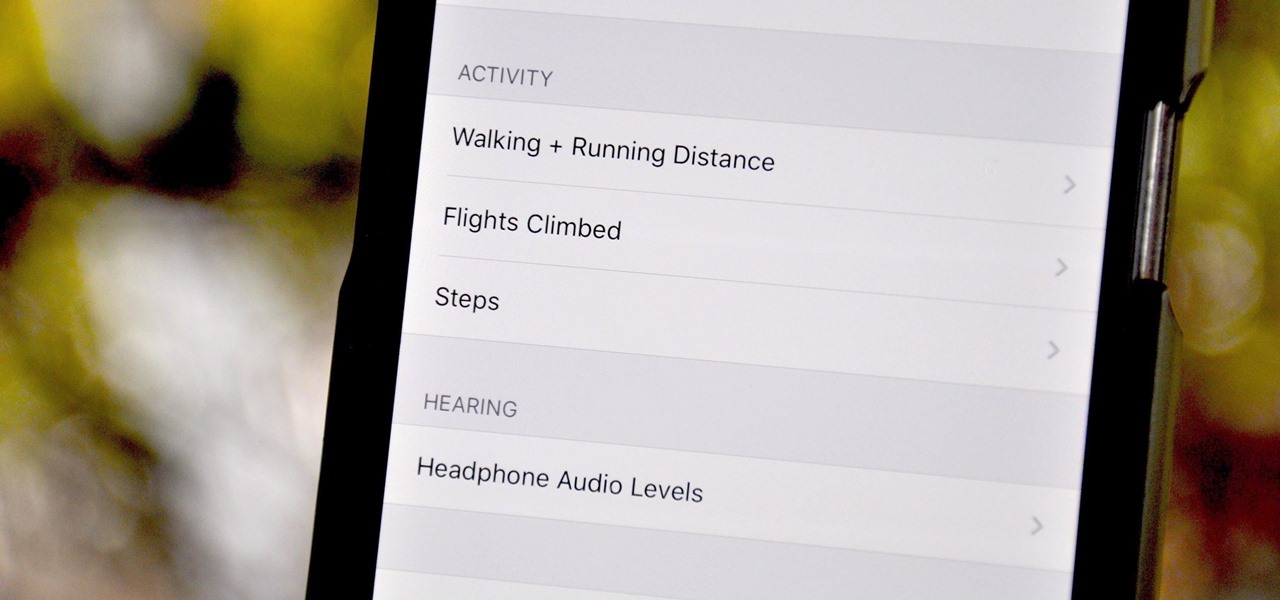
Your iPhone tracks how many steps you take, how far you walk, and how many stairs you climb each day. That may seem a bit frightening, but it's all for a good reason: the Health app stores this data so you can view your progress in one place. But interestingly, opening the Health app isn't the easiest way to view this info.

Android phones have supported keyboards and mice for a long time, and you've even been able to use physical keyboards with iPhone and iPad models. But iOS 13 and iPadOS 13 finally include official mouse support. That means you can use a wireless or wired mouse and keyboard with your iPhone or iPad, though, a futuristic peripheral that combines the two may be even better.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

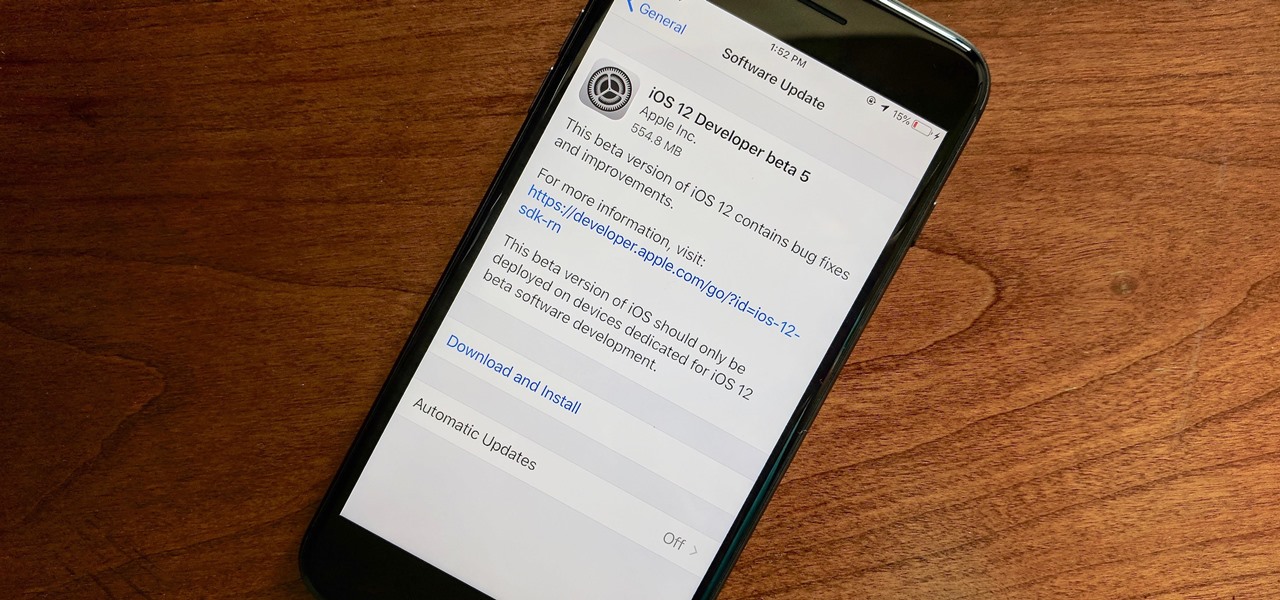
Apple released the fifth developer beta for iOS 12 on Monday, July 30, only 13 days after the release of dev beta 4 and 12 days after public beta 3. Until this release, Apple kept a consistent two-week schedule for developer beta updates, so we were a little surprised to see this one drop one day early.

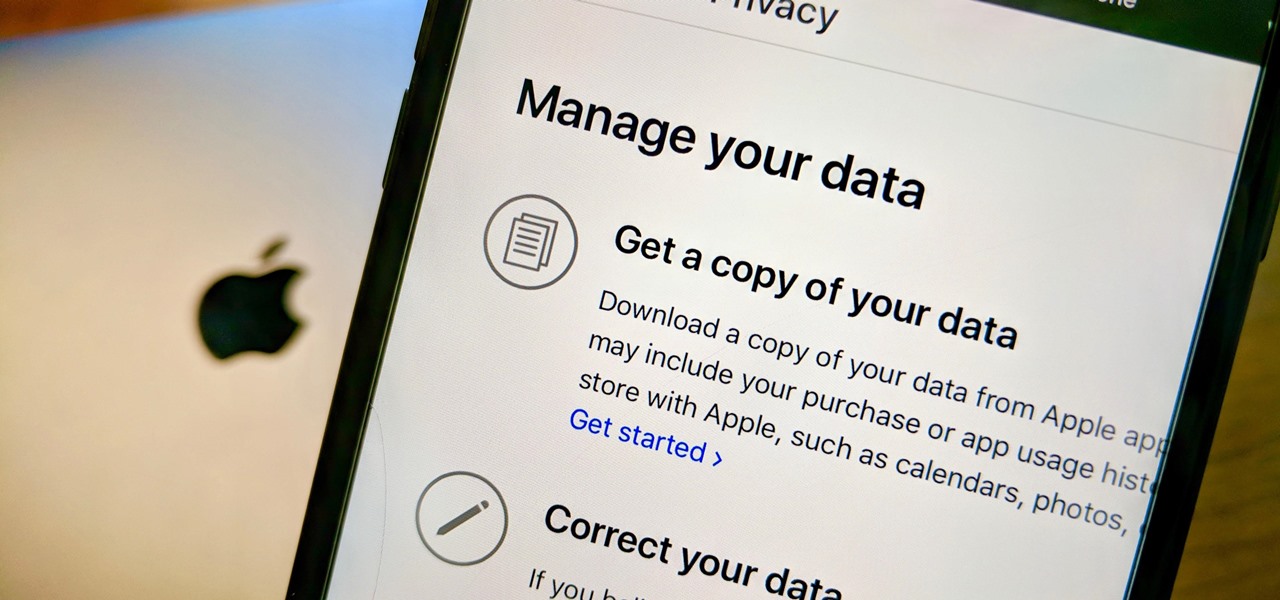
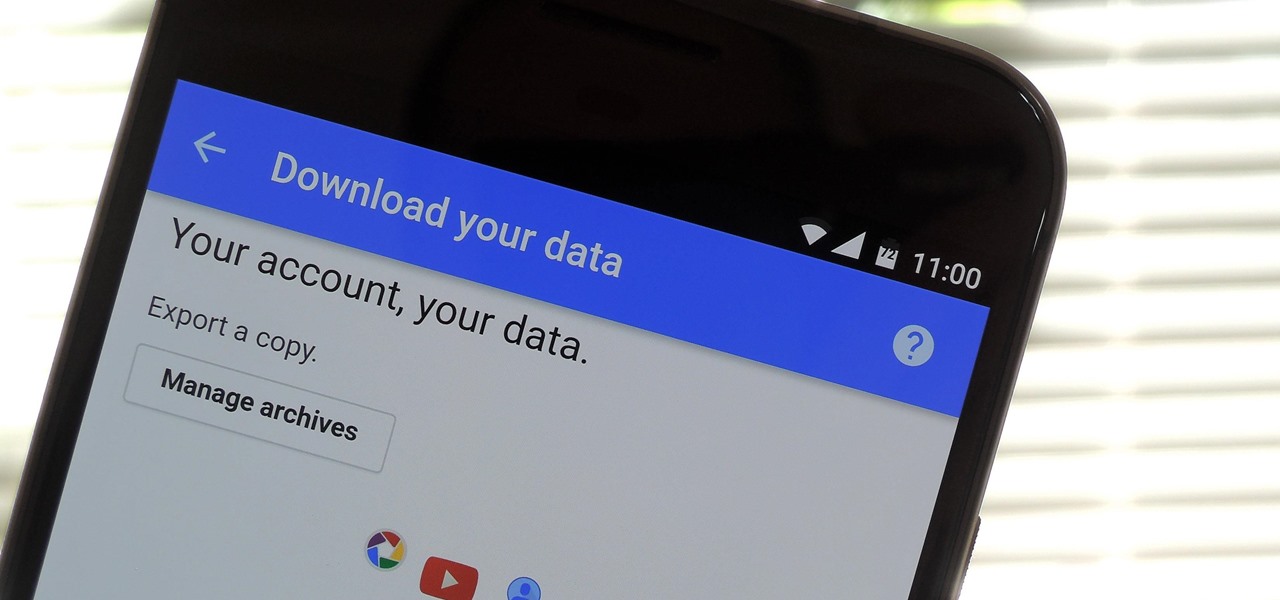
Personal data is a hot topic right now, and for good reason. Never before has the public been so on edge about how companies use their information. Services like Facebook and Google now allow you to download all of the data each has on file. Soon, you'll be able to see exactly the same for Apple as well.

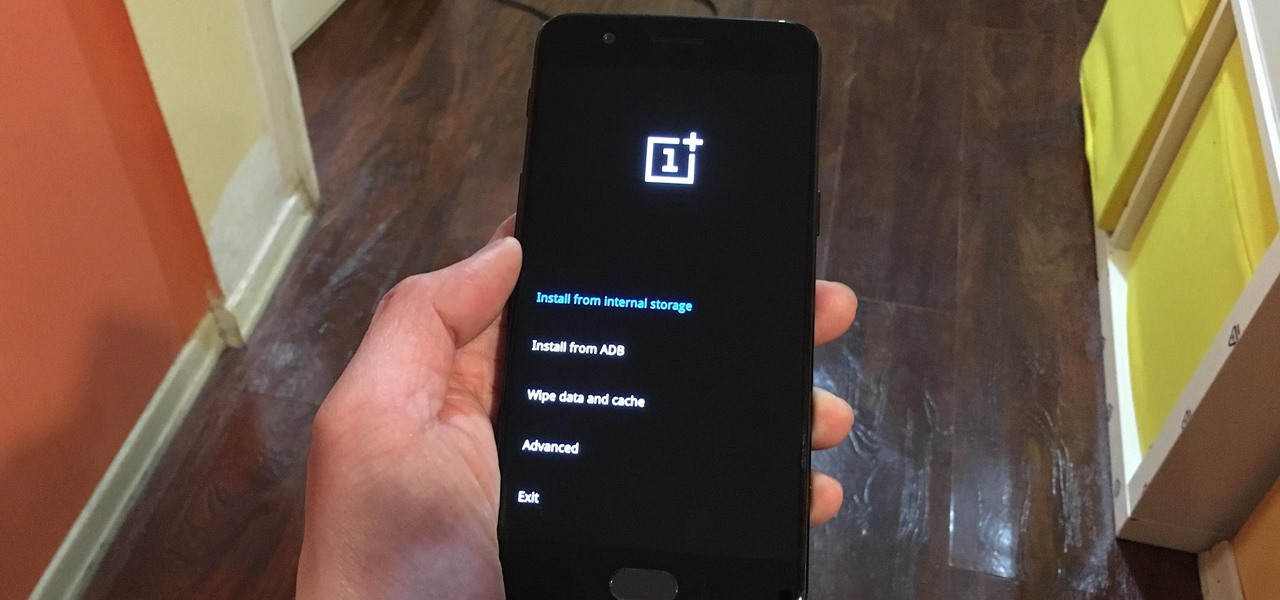
Both the OnePlus 5 and 5T have two pre-boot menus that every owner should know about: Recovery mode and bootloader mode. The recovery screen lets you wipe cache, perform a factory reset, or install firmware, which can help save the phone from a soft-brick. Bootloader mode, on the other hand, lets you send Fastboot commands via PC or Mac to lock or unlock your bootloader or flash images.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

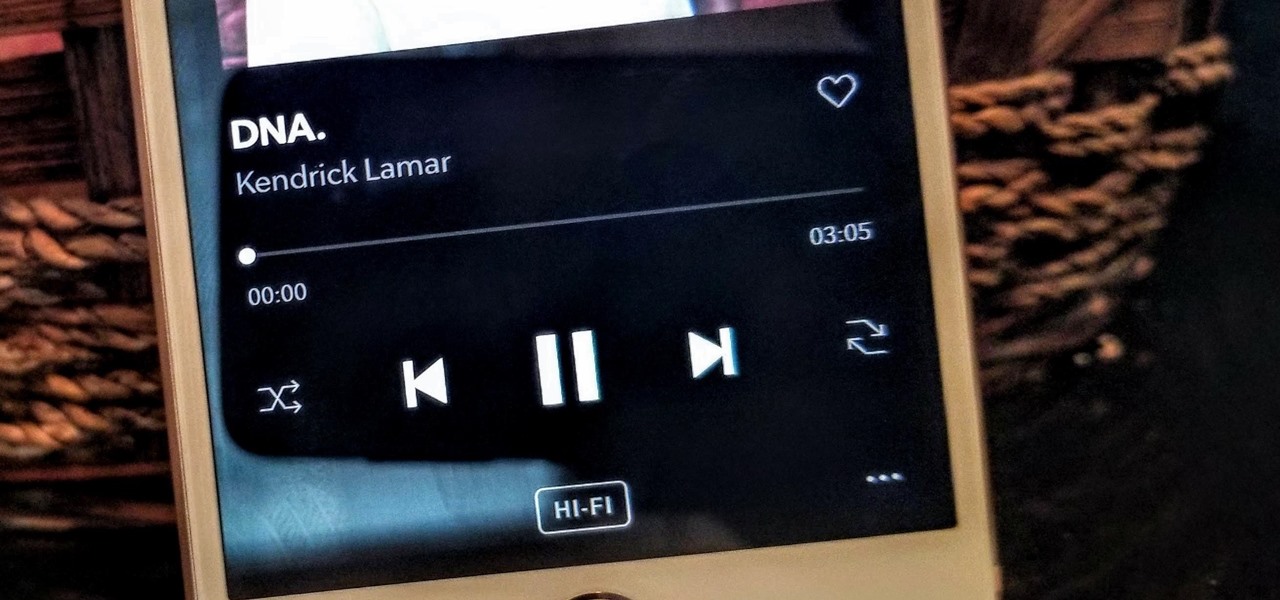
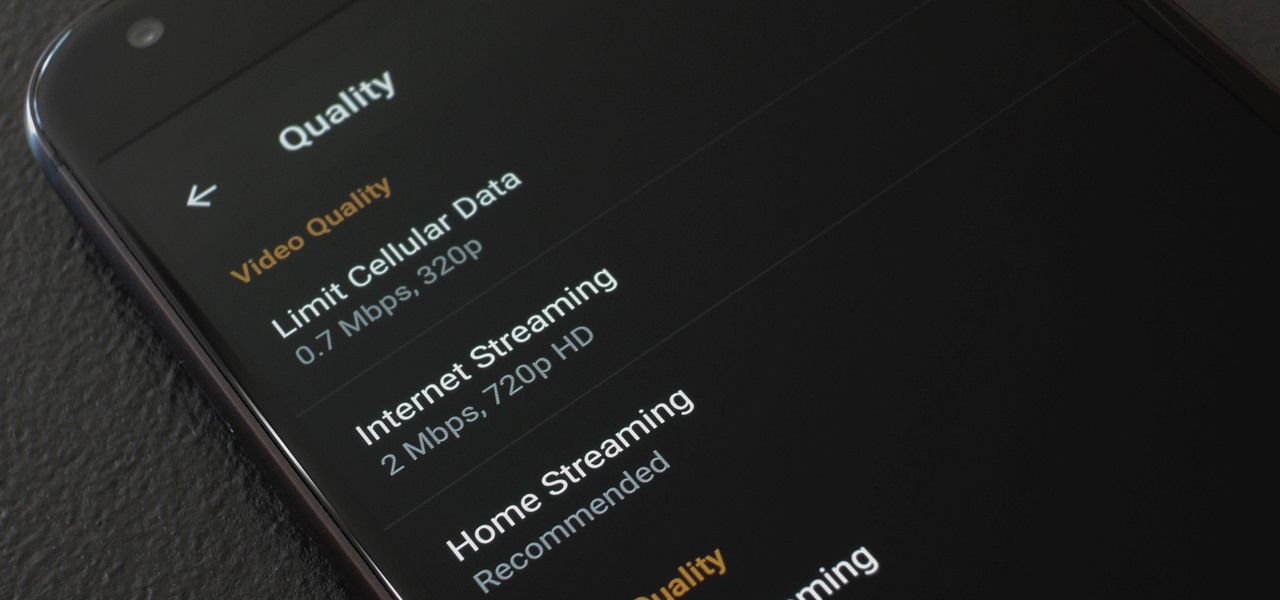
Thanks to their partnership with Tidal, over 30 million Sprint customers can access Hi-Fi audio on the go. And the Jay-Z-owned music service isn't limited to just Sprint customers — for $19.99/month, anyone can listen to lossless audio from their favorite artists. But streaming uncompressed audio files uses a lot more data than standard quality, so how do you use Tidal without hitting your data cap?

When you're on the go, Plex makes sure your media always stays with you. Just install the server app for Mac or PC and enable remote access, then you can stream movies and TV shows from your computer to your phone over the internet.

Research group OpenAI, a research institute co-founded by Tesla CEO Elon Musk, says it is possible to trick driverless cars' neural networks into mistaking images for something else.

Sometimes it's impossible to concentrate — let alone direct your personal assistant Siri — when someone is blasting music on their phone or talking to thin air. I mean I'm loud, but not that loud.

Welcome to the maiden voyage of our new Market Reality column. Each Friday, NextReality will give you a roundup of news briefs from the financial end of the augmented and mixed reality industry. We'll cover funding news, market analysis, and more.

If you're an Android user, Google probably has almost your entire digital life stored on its servers. Family pictures are backed up on Google Photos, your e-book library resides with Google Play Books, videos are on YouTube, chat logs in Gmail and Hangouts, starred places and location history in Google Maps, and so much more.

Data visualization has many applications in virtual and mixed reality, since a third dimension literally adds important depth to the represented information. A new app called HoloFlight is a good example of this, combining flight-tracking data and the Microsoft HoloLens to surround you with a look at every plane in the sky.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

As mobile devices become more and more popular, service providers have unfortunately resorted to capping data. What this means is that, depending on the plan you have with your ISP, you could have limits placed on how much data you can use for a set period of time. Once you've hit the limit, your ISP could drastically slow down or throttle your internet speed or charge you outrageous overage fees.

Well, this is my first article so if it sucks tell me...lol!! Story Time

After you have registered to this site,sign in then to start missions. Basic Missions

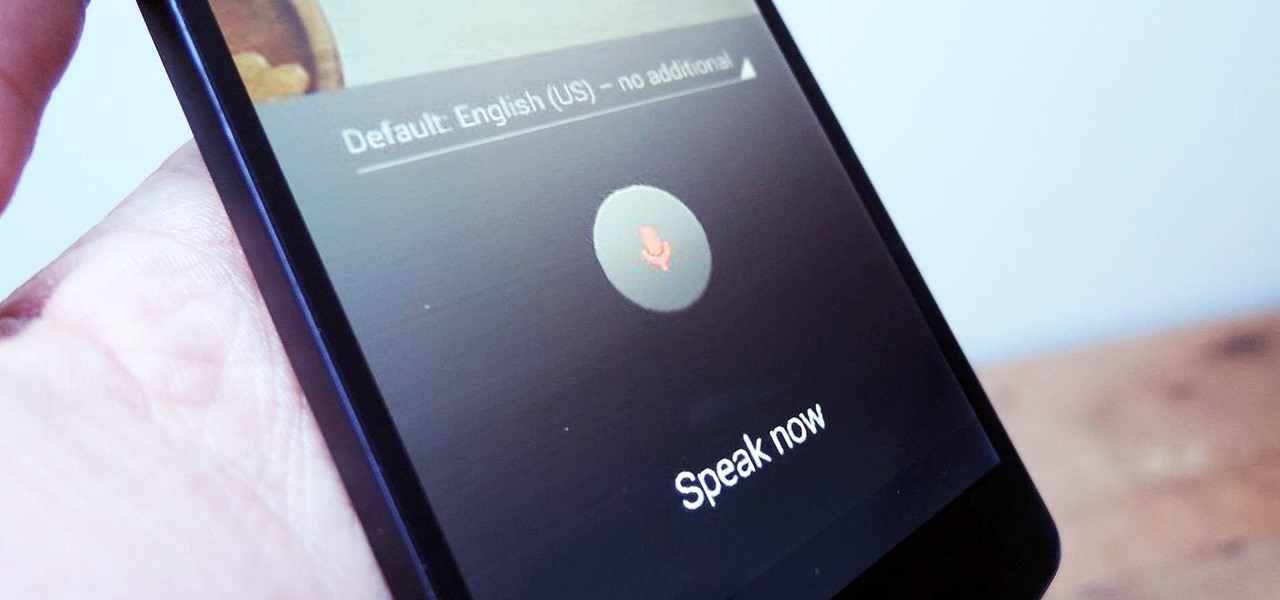
As smartphones become increasingly integral parts of our lives, so does data throttling. Personally, I try to save data any way that I can, so to stave off unnecessary usage, I use the GoogleOfflineVoice to limit the amount of data consumed by voice typing.

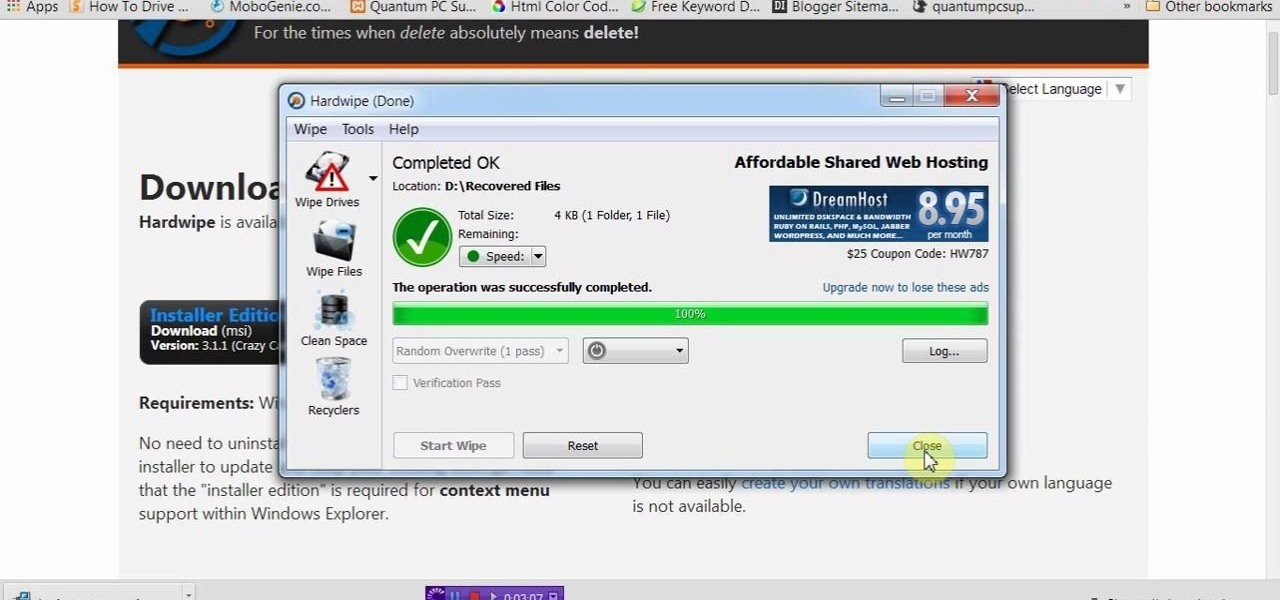
If you delete data by using Hardwipe tool, then it can't be regained by any means. The file or data will be deleted permanently. Watch the video and follow all the steps carefully. Employ the technique in your own PC.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.