When Facebook launched its first hardware products last year, the Portal and Portal+ smart displays, the company mostly touted its video-calling features as it faced off against Amazon and its Echo Show.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

We've shown you the best augmented reality headsets, and now it's time to show you the rest. These are the AR headsets you've probably never heard of or even seen. The AR headsets that, in some cases, have a shot at the big time, and may one day reach widespread adoption, and, in other cases, are unwieldily contraptions that look like something out of a weird science fiction movie.

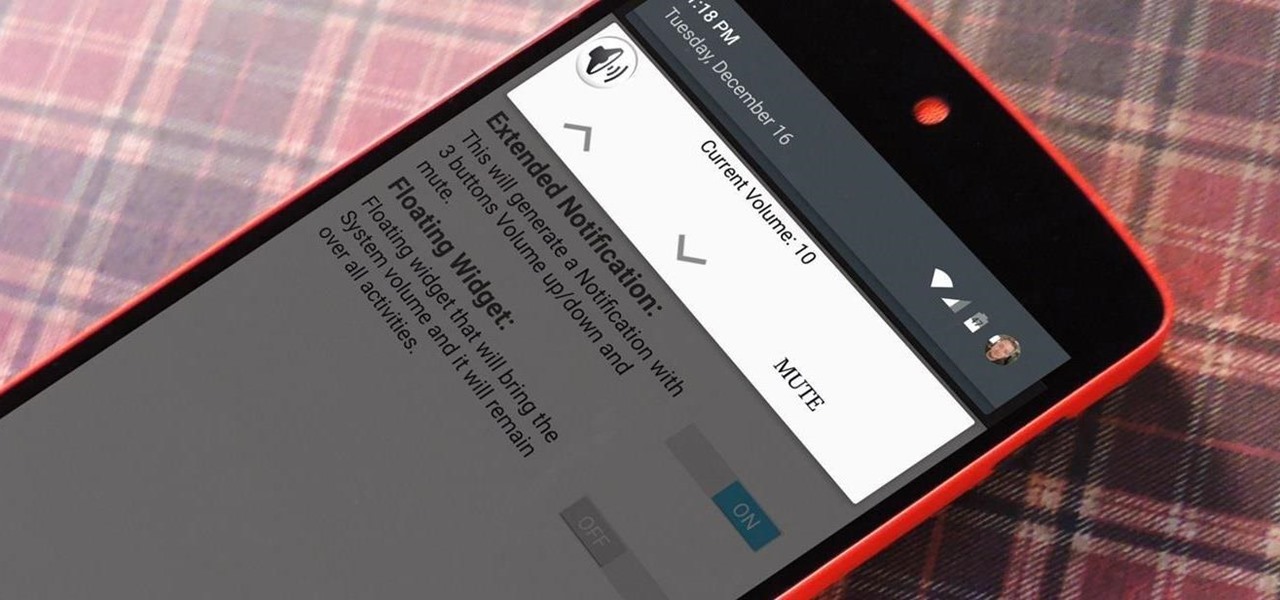
Putting your Galaxy S9 in Immersive Mode lets you truly enjoy the gorgeous display that Samsung is so famous for. You can't have it set on at all times, however, so you'll still have to deal with the status and navigation bars that cut the phone's aspect ratio down to that of a standard phone. But if you're willing to dig a little deeper, there are ways to go full Immersive Mode on your S9 for good.

With all the hype surrounding meteoric rise of Bitcoin (BTC), Litecoin (LTC), Ethereum (ETH), and Bitcoin Cash (BCH), it's easy to overlook the fact that you can send and receive cryptocurrencies as a form of payment. And thanks to Coinbase, sending and receiving digital coins couldn't be any easier.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as they have physical access to the computer.

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

HoloLens users will have a handful of ways to interact with the mixed-reality, holographic world. Gaze Input lets the user control a cursor in their field of vision. In other words, it's essentially a mouse that you control by looking around.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Microsoft's "Fall Update" to Windows 10, code named Threshold 2, has a lot of new tricks up its sleeve. It's the biggest update we've seen since Windows 10 was released this summer, and it's rolling out to all users right now.

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.

If you've ever taken apart an electronic device that uses physical buttons, you already know why these types of input methods are destined to fail. The rubberized contacts used in physical press-and-release buttons like those of a gamepad or keyboard are incredibly frail and can easily wear out over time.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Spider-Man hits the iPhone, iPod Touch & iPad! In Ultimate Spider-Man: Total Mayhem, you take control of Spidey, slinging webs and fighting crime. No longer do you have to stick to comic books, you can enjoy Spider-Man right from your Apple mobile device.

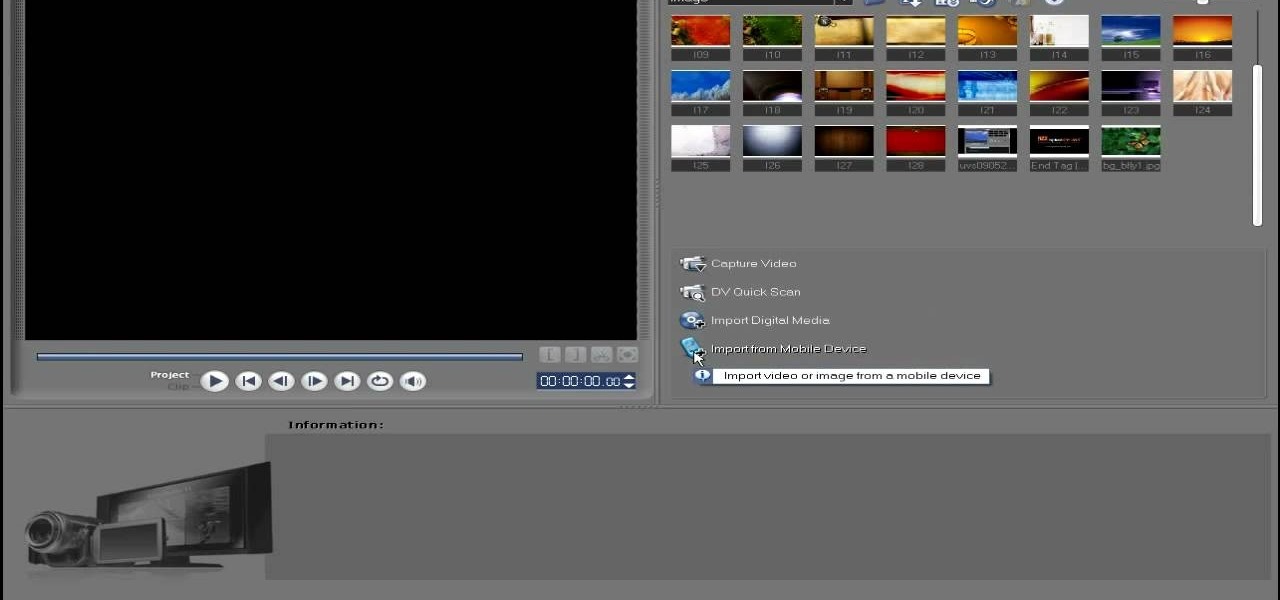
In this video tutorial, viewers learn how to import media from devices in Corel Video Studio. Begin by connecting your mobile device to the computer. It can be any device with a memory card or hard drive. Open the program and click on the Capture tab. Click on the option, Import from Mobile Device and select the device that you want. Select the file(s) that you wish to import and click OK. The program will then import the media to your selection window. This video will benefit those viewers w...

USB devices are ubiquitous and cheap nowadays, which means they make great raw materials for hacking and electronics projects. This video will show you how you use a USB host shield to hack USB devices and use them with MIDI controllers, game controllers, and other devices.

In this video tutorial, viewers learn how to put their iPod device into recovery mode using Z-Phone. The Z-phone application does not work on 1st generation iPod devices. Begin by unplugging the device from your computer. Then hold down the power and center button until the device\s screen goes completely black. Now hold the center button as you connect the device back to your computer. Finish by following the process in iTunes to restore the device. This video will benefit those viewers who ...

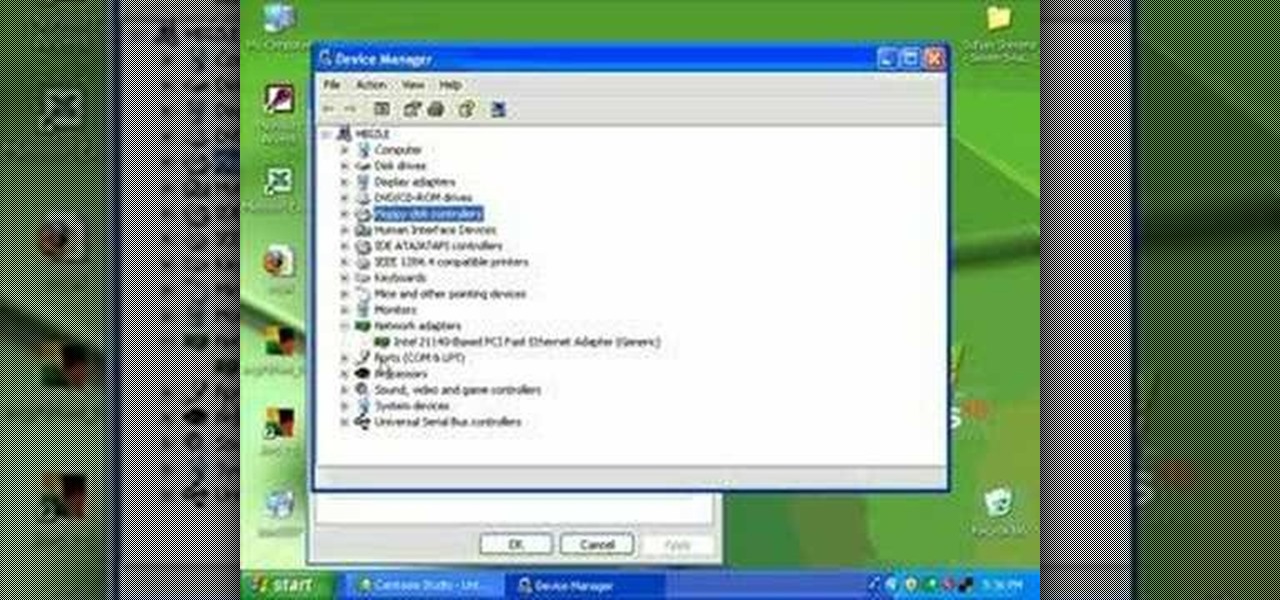
If your Windows PC has been running rather slow lately and you're not sure why - you may have unknown devices taking up space and energy. Check out this tutorial for details on how to detect and disable unknown devices in Windows Device Manager.

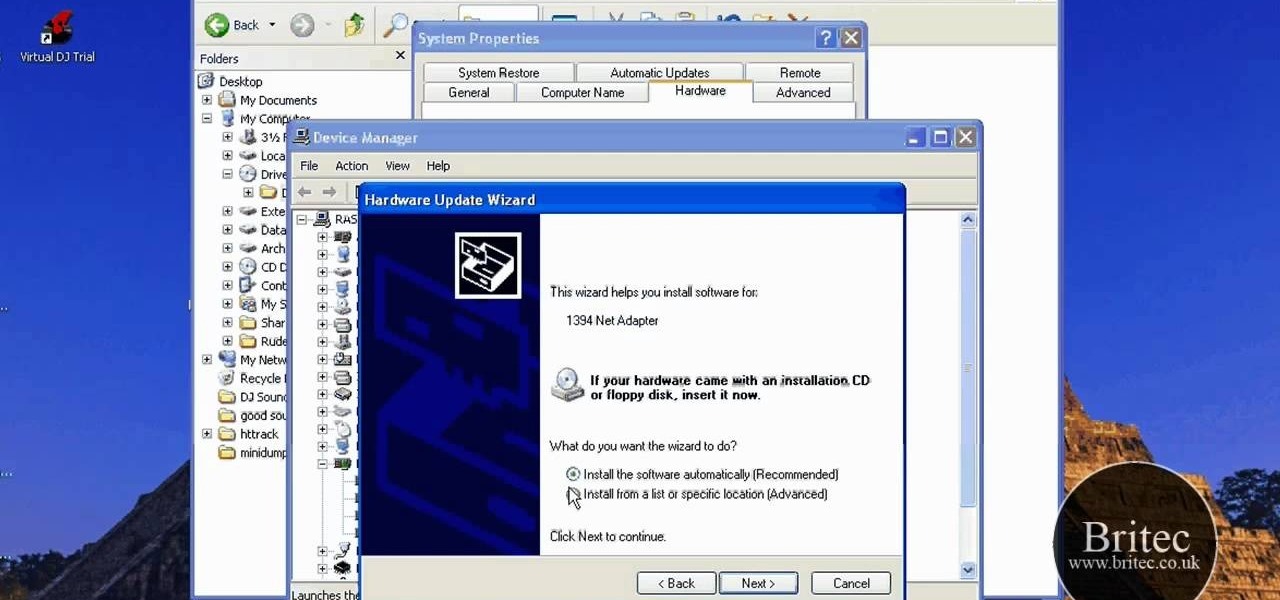
The beyourownit shows you how to remove and reinstall devices in Windows XP. The first thing he shows what to do is Right click on the My Computer icon and select properties then select then choose the hardware TAB. When you click on the Device Manager button, the Device Manager will appear where you can make changes to your computer. The user explains more to help you understand better. If you watch this video, you will find out how to reinstall devices in Windows XP.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to track a USB device.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

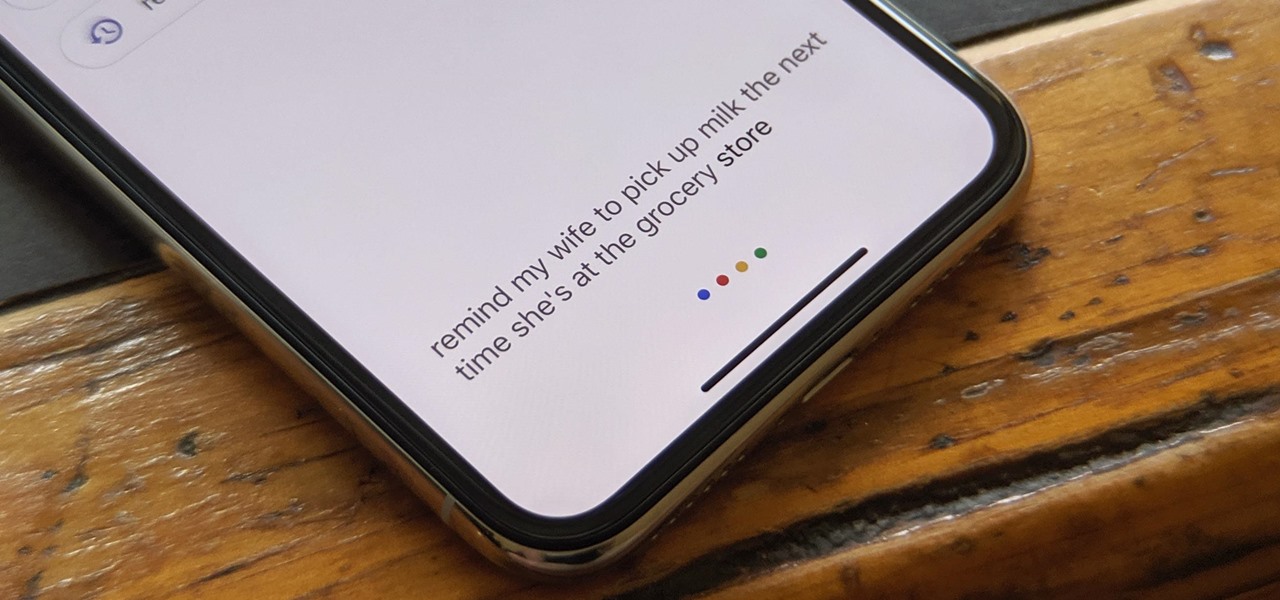
The Google Assistant is available almost everywhere. It powers smart speakers like the Google Home, it's built into Android phones, and it can even be installed on iPhones and iPads. So when Google adds a feature like the ability to send reminders to other people's Assistants, it's far reaching.

Your Skype contact list might contain a sea of names that make it tough to find a specific person you're trying to reach. The same goes for your loved ones and colleagues, especially if you have a common name like Jennifer or John. Knowing that, you might want to change your Skype display name to set yourself apart.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiring a bit of work to restore these messages.

Though not as flashy as Face ID and other features, Low Power Mode has become one of the unsung heroes of iOS. When you're away from a charger, enabling this feature will dial back performance and networking to help you eke out up to three extra hours of battery life. If your device is jailbroken, you can even automate Low Power Mode to ensure your battery never dips to critical levels while out and about.

While there are many awesome features in iOS 12, there's one that has got the best of me and my patience. Sending photos and videos in a text or iMessage. Yes, there are a few ways the process remains the same, but if you select pics and vids right from within the Message app, be prepared to be annoyed ... highly annoyed.

This time last year, computer vision company uSens introduced a stereo camera module capable of hand tracking. Now, uSens can achieve the same thing with just a smartphone's camera.

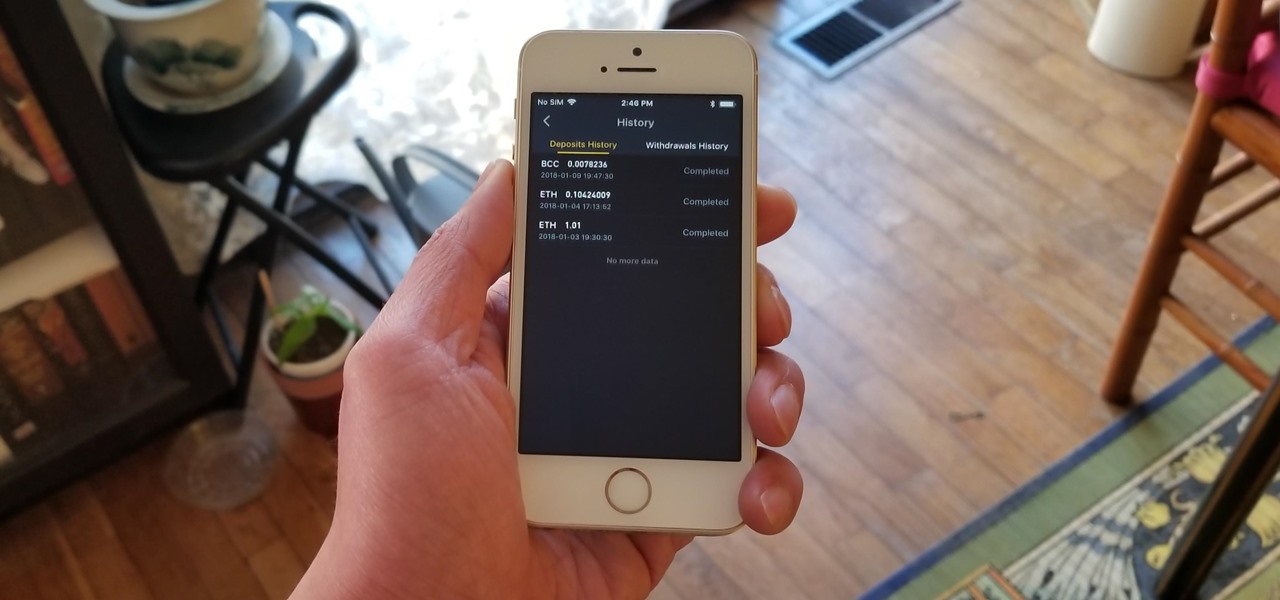
As cryptocurrencies gain mainstream acceptance, it's not far-fetched to think that we'll one day be able to buy alt coins like Ripple (XRP) and Stellar (XLM) using debit cards and bank accounts. Until then, we'll have to rely on using bitcoins and ethereum to buy digital coins. Thankfully, depositing and withdrawing cryptocurrencies with Binance is relatively hassle-free.

It finally happened. Magic Leap has given the world its first glimpse at its debut device, the Magic Leap One Creator Edition.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

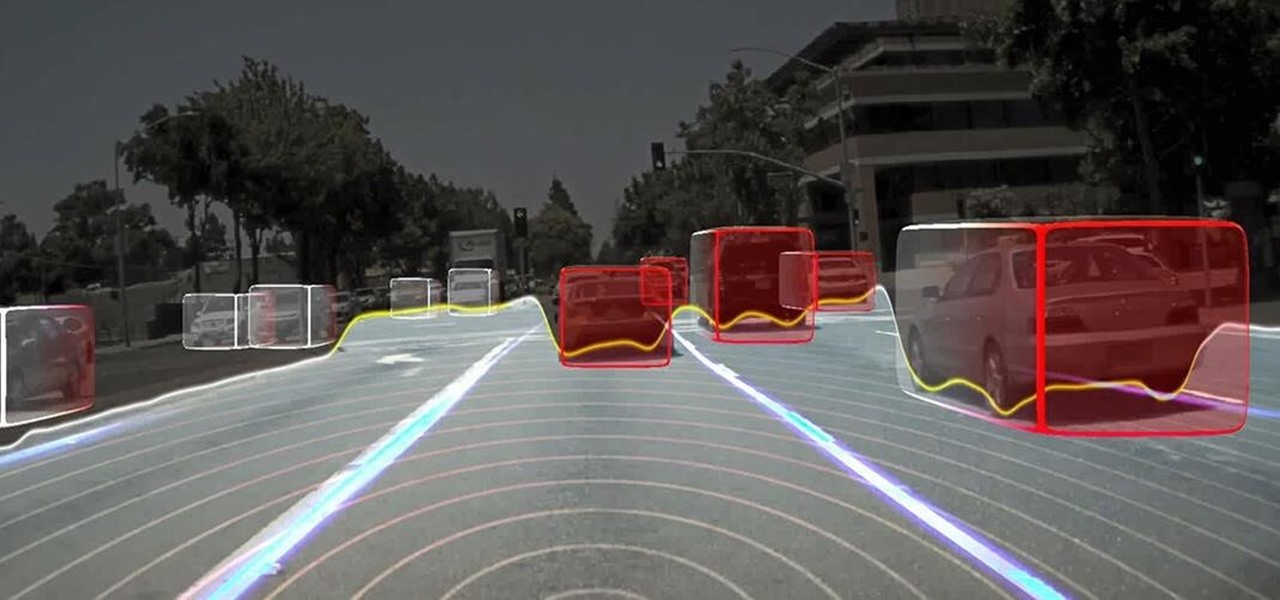
Long before Nvidia figured out how to embed neural networks in its graphics processor units (GPUs) for driverless vehicles, it and other chipmakers were already making the same kinds of devices for 3D games and other apps.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

One of the biggest hurdles for making touchscreen text input easy on the user has been finding a simple way to move the cursor around. With all the advancements in mobile technology, we're still left fumbling around with tiny arrow indicators or magnifying glasses when we need to add a letter to a word we've already typed. But thankfully, developer Ouadban Youssef has found a better way.