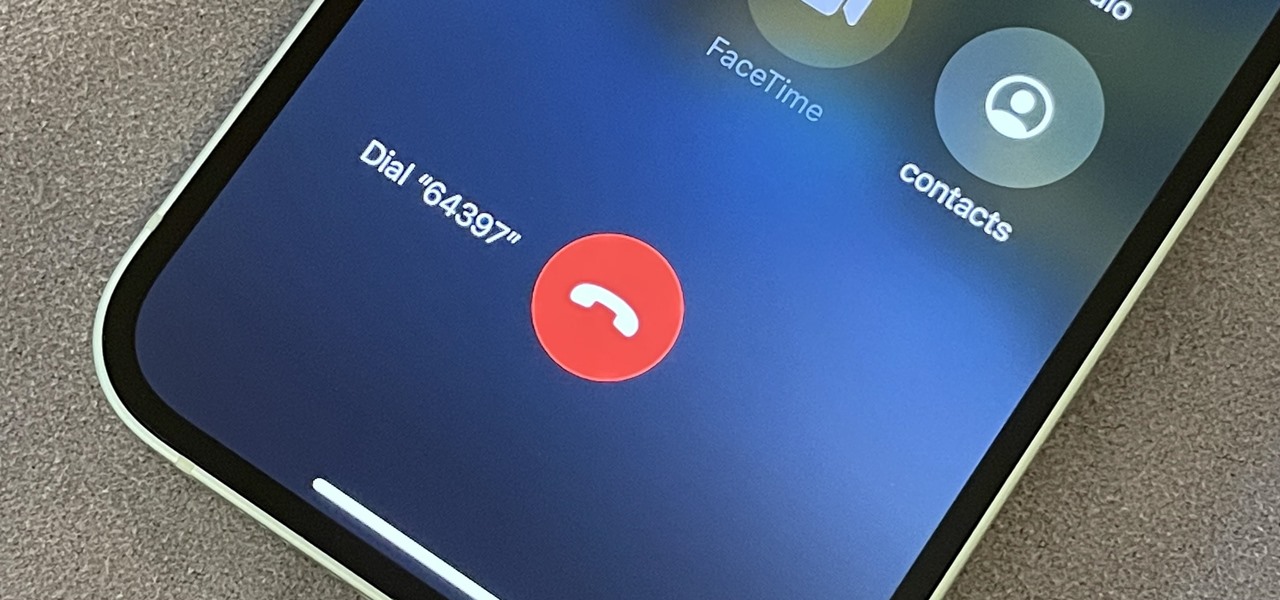
Automatic phone menus are the worst. You call the number, listen to prerecorded prompts, press button, listen, press button, listen, press button, listen, until you're routed or connected to the right extension, directory, menu, person, or whatever. But you can bypass these automated attendants to get right to where you need to go by setting up a simple shortcut on your iPhone.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.

The Snapdragon version of the Galaxy Note 20 and 20 Ultra — the one sold in the US — can't be rooted. Without root, the level of customization is limited. Such a large group of Android users shouldn't miss out on mods, and they don't have to.

Privilege escalation is the technique used to exploit certain flaws to obtain elevated permissions relative to the current user. There are a vast number of methods out there to go from user to root on Linux, and keeping track of them all can be difficult. This is where automation comes into play, and a privilege escalation script called Linux Smart Enumeration is one to take advantage of.

Sudo is a necessity on most Linux systems, most of which are probably being used as web servers. While the principle of least privilege is typically applied, sudo misconfigurations can easily lead to privilege escalation if not properly mediated. Which brings us to SUDO_KILLER, a tool used to identify sudo misconfigurations that can aid in privilege escalation.
Beta testing for Apple's big upcoming iPhone update, iOS 13, is well underway. So far, each of the four beta versions we've seen brought new features and changes to the table, many of which were never even mentioned by Apple during WWDC in June. Now, it's time to do it all over again, as Apple just released the fifth developer beta for iOS 13.

Although the Clock app in iOS has undergone some design changes over the years, you still can't set more than one timer on your iPhone. Oddly enough, Apple's own HomePod speaker added this feature, mimicking the timer on Amazon's popular Echo smart speakers. Fortunately, through Apple's Shortcuts app, there's a clever hack to set multiple timers — without using a third-party timer app.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings change, interface update, or hidden improvement.

A post about Cyber war from BBC, want to share. http://www.bbc.com/news/world-32534923

This is a video for children to learn about the traffic light for pedestrians use. It is an interaction game where the children can push the proper light to answer questions pertaining to the traffic light. Teach children about traffic lights.

The new sync lock feature in Premiere Pro CS4 is a very useful tool that will maintain the relationship between clips in multiple tracks so that when you are editing you make changes to one clip, Premiere will keep your edits in place by adjusting the other clips in the timeline. Sync lock is a new feature added to Premiere Pro CS4 and this tutorial shows you how and when to use it as it pertains to your normal editing workflow in Premiere Pro. This is especially helpful when ripple editing. ...

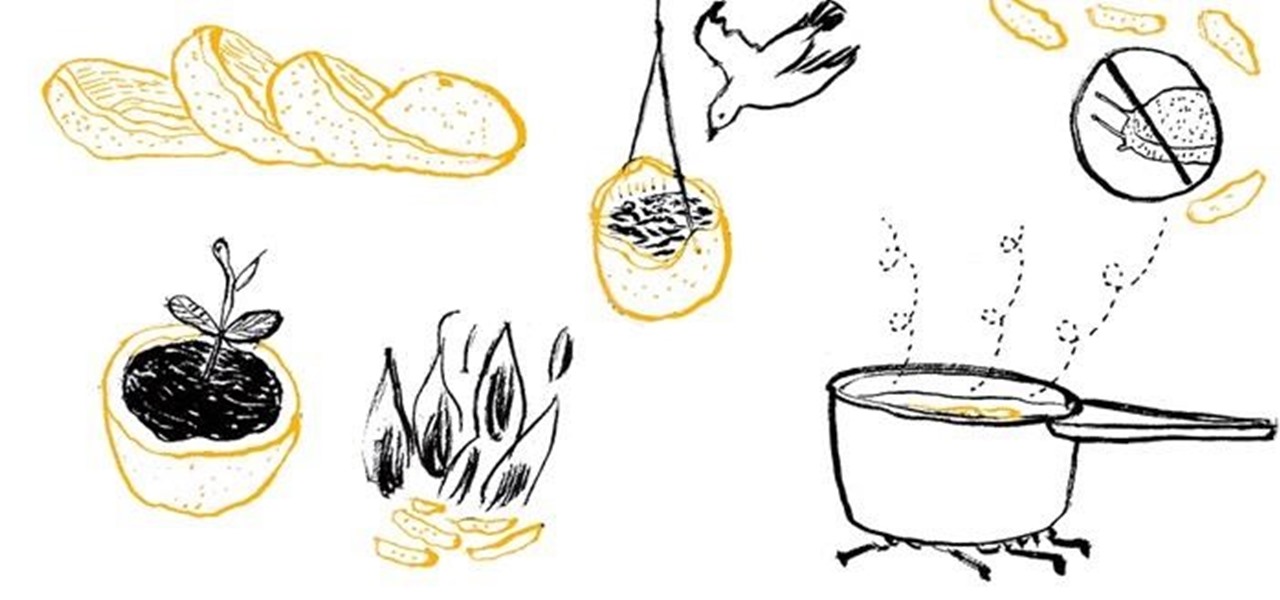
What should you do with an orange peel after you're done eating the fruit part? If at least one half of the orange peel is still intact, consider using it as a seed starter pot, emergency oil lamp, bird feeder, or a super-easy, salt-packed DIY fridge deodorizer.

ZEPHYRS n sing. ZEPHYR gentle breezes 74 points (24 points without the bingo)

Winner Announcement by Tom Stack & Associates, Inc. Chasing the Light Juried Photo Competition - The Avian Persona

So, when Christopher brought up Nikola Tesla in his very first post on Fear of Lightning, it got me interested in learning more about the man behind alternating current. There is plenty of info out there on the Internet, widely available for free, but sometimes it's just nice to have a book in your hands... or on your computer or mobile device.

Scrabble Bingo of the Day: MIASMIC [adj] Miasmic is an adjective for miasm (or miasma), which means a noxious vapor—"bad air" harmful to health. The word miasma comes from the ancient Greek word for pollution. And the concept of bad air also gave rise to the name malaria, from old Italian "mala" (bad) "aria" (air).

GUISARD n pl. -S a masker 59 points (9 points without the bingo)

ZEBRASS 68 points (18 points without the bingo) Definition: the offspring of a zebra and an ass [n]

Call Your State's Nurse Aide Registries for School Inquiries

Grey's Anatomy fans— you have just gotten a better viewing experience— an interactive viewing experience. But you need an Apple iPad to bask in the sweet delight of doctorly debauchery and do-goodery.

Psychology Today's Elizabeth Svoboda presents an interesting argument on the merits of no holds barred truth telling versus the social sensitivity involved in telling little white lies. Svoboda poses that while truth tellers may rest easy at night, brutal honesty can have negative emotional repercussions for others.

Dating sites are getting more and more culture specific, and this week's brand new girl + guy site offers a very specific service. Cute girls are paid to play video games. Gamer dudes pay to play with them.

Oh Data, You so Awesome! We are going to use Node.JS to gather us some data. Given nodes plethora of well abstracted network abilities and it's deep evened nature, it will make quick work of plugging into various data sources and gathering / making good use of said data.

It's sad to say, but I will no longer be writing up anymore Scrabble Challenges. Frankly, I just don't have the time to make them now. And though they are incredibly fun and "challenging" to conjure up, I'm not sure that people are finding them as useful as I had hoped. But really, it all comes down to time. So, unless I have a future craving for puzzle-making, last week's Scrabble Challenge #20 was the last one.

Scrabble Bingo of the Day: * CAGANER [n] A caganer is a small figurine of a person defecating in place, pants humorously around the character's ankles. It's a traditional Christmas decoration in Catalonia, Spain and in neighboring areas, where it's placed within the nativity scene.

Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each server will have numerous known security holes, but until then, let's get back to the regular weekly coding sessions and realistic hacking missions on HackThisSite.

We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But for now, back to the normal flow of things...

We're aiming for this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with, we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But, for now, back to the normal flow of things...

The community tore up the first realistic mission last week. You've applied the techniques learned in the basic missions to a real scenario, so I'm pretty content. The realistic missions are where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, f...

Community byters, it's time to get serious. We are finally moving on to the realistic missions in HackThisSite. This is where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the 10th Community Byte session for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Null Byte is looking for forum moderators! Welcome to the ninth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the eighth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the seventh Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the sixth Community Byte for coding in Python and beating the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and essentially grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the fifth Community Byte for coding in Python and beating the challenges given to us from HackThisSite. These sessions are created to bring our community together, to learn from each other, and essentially grow together. Everyone is welcome, from novice programmers to aspiring hackers—even people that are nearly computer illiterate.

CARRION n pl. -S dead and putrefying flesh 59 points (9 points without the bingo)

Oh, teenagers. Maybe you would be better off planning a scavenger hunt for the screaming toddlers. Just kidding! Despite the mood swings, teens will enjoy a scavenger hunt more than younger kids. Some things to keep in mind, though:

Below, 10 step-by-step instructional videos for transforming yourself into a Na'vi being this Halloween. Step 1: Choose your favorite Avatar look from the list below. Step 2: Apply your chosen look. Step 3: For the dedicated fans with (more than a little) time on their hands, learn the Na'vi language and your transformation is complete!