Getting a good night's sleep is critical to maintain good health, a better mood, and clear your mind for whatever the day has planned for you. But in practice, whether you're tired or not, the world has a way of preventing it, either through your partner's snoring, your neighbor's music, or the road construction going on right by your bedroom window. It can get rough.

Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.
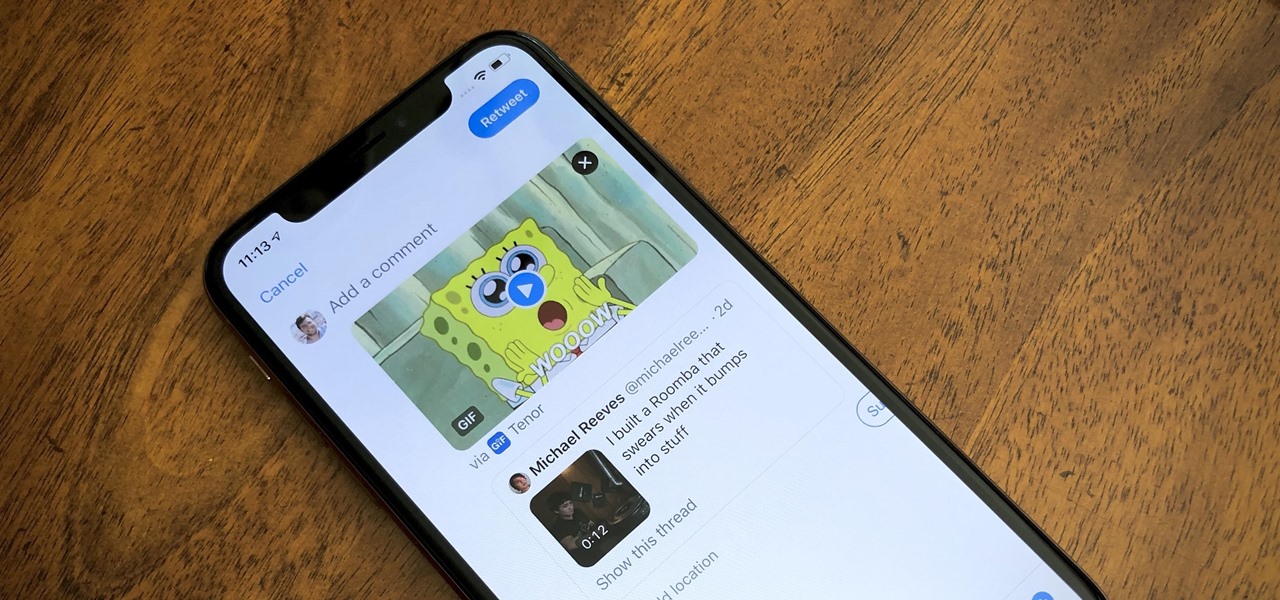
On Twitter, quote retweets are a great way to share someone else's tweet with your view of their message. Twitter has expanded on this idea by giving us the ability to attach images, video, and GIFs to quote retweets. With these extra options, you should have no problem adding your own unique perspective on that funny, serious, or professional tweet.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

I was today years old when I first heard of Bhad Bhabie, but I'm told she is apparently a rapper with a rags-to-riches story.

Now that the holiday season has officially kicked off, Office Depot has updated its popular Elf Yourself app with a few new augmented reality options.

Christmas came early for Apple, as the company was awarded more than 40 patents by the US Patent and Trademark Office on Tuesday, including one covering a system for compositing an augmented reality construct based on image recognition.

Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

Augmented reality is becoming a slam dunk for sports entertainment, as leagues, their teams, and their broadcast partners have been quick to adopt AR.

While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

We've reached the point in the trajectory of augmented reality's growth where AR advertising experiences are becoming commonplace tactics rather than rare experiments.

The latest whispers about Apple's plans to launch its long-awaited (yet still unconfirmed) augmented reality device hits several familiar notes, but lands on a different refrain.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Shark Week, which debuted in 1988 as a week of programming on the Discovery Channel dedicated to the titular predatory fish, has grown into a cultural beast of its own.

June is Pride Month, an annual celebration of LGBTQ+ communities in commemoration of the Stonewall uprising of 1969.

Whether you're in high school or college, you no doubt will have your iPhone in your pocket all day long. To make your iPhone last the whole time and even help you out with your studies, these are the accessories you'll want to get your hands on.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

Still on the fence about Apple's native Notes app? The latest Notes update for iPhone, iPad, and Mac is about to change your mind. With some fantastic new features and plenty of valuable tools from previous software versions, Notes is becoming a clear winner when it comes to saving important information from your personal and professional life.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

This video shows how to easily record your voice and insert a sound podcast to your WebQuest or webpage using Dreamweaver. It shows how to have the sound play on the same page without auto starting. The tutor initially goes to the Start button and in All programs selects Accessories. Next he selects Sound Recorder from the Entertainment option and records his voice reading out the content of the page. He then saves the file in the folder called websites creating a subfolder in the name of ‘so...

Dogs need toys too! Show your dog some love by making him a handmade squeaky toy. You can put an old pair of jeans to use, practice up on those sewing skills and hear the sounds of enjoyment as your dog squeaks to his heart's content.

Painting your car's interior is a great way to enhance your driving surroundings and give you a new plush look. In most cases it can even increase the value of your car when you trade it in or sell it.

Bob Schmidt from Home Remodel Workshop demonstrates how to frame a wall 16 inches on center. His tutorial is especially helpful, so pay attention to his tips, tricks, and specific techniques.

There are several helpful ways to boost one's bosoms. You can add inserts to the bra, workout your chest or buy a different brassiere. Make your breasts look bigger.

Tommy gets a second wind now that he can see noticeable progress on the Bombe. He draws and cuts the dividers for the pigeonhole assembly and inserts them from the back. Using scrap wood from previous cuttings because it has the same colors, tones and textures, he designs a pattern for the valances. Now the top row is almost complete, and Tommy is “feeling energized again.”

Photoshop Disasters presents their top 20 monstrosities of 2010. Wow. Take a lesson. Egyptian newspaper Al-Ahram doctors the above photo to put President Hosni Mubarak at the head of the procession. (Read more)

53-year-old artist Scottish artist David Mach uses tens of thousands of matchsticks to create sculptures of animals, as well as religious and political icons. He first creates a plastic or fiberglass mold, and then inserts the matchsticks, one at a time. His work sells anywhere from $30,000 to $52,000... unless he sets the piece on fire, of course.

Every day of the week, WonderHowTo curators are hard at work, scouring the web for the greatest and most inspiring how-to videos. Every Friday, we'll highlight our favorite finds.

We've seen wearable electronics before, but we've yet to see a dress that dually operates as a cell phone. The idea is interesting, though not especially pragmatic (yet).

What's the highest score you ever achieved in one SCRABBLE game? 500? 600? 700?

The game has undergone many transitions over the years, since its days as LEXIKO (1931) to its briefness as CRISS CROSS WORDS to its current and amalgamated, renowned brand of SCRABBLE. There has been many editions of the word board game along that historic metamorphosis, and SCRABBLE has even given in to pop culture, sports memorabilia, and fanaticism.

Antimatter15, author of the popular Surplus Chrome extension, was suspended from Google+ for using a pseudonym instead of a name that fits Google's community standards. As such, he's no longer supporting the extension, and if you're using it, now might be a good time to find a replacement. It's a reminder that nothing on the web is guaranteed to work forever. Luckily, there's no shortage of innovative coders whipping up creative and useful Google Chrome extensions.

Final Fantasy 14 the MMO is now live. The special edition priced at $75 enables people to play eight days earlier than people getting the regular edition, which comes out on September 30th. Mine arrived yesterday and here are some pictures of what's inside the special edition version of the game:

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.