Buying a used car is a task humbling in it's complexity, but certain parts of it are still simple. In this video you will learn several easy, effective ways of inspecting a used car you want to buy to make sure it hasn't been in a flood or accident and has a properly working engine.

This two part video goes over the procedure for testing and inspecting lead acid batteries. A machine is required to test the battery itself. You can do the visual test at home, and then bring it to an auto parts store for the machine test part.

Removing a vehicle's tires and inspecting the brake rotors is possible with a few easy steps. First, remove all five lug nuts and remove the wheel from the vehicle. A power tool will easily remove the lug nuts. You now have access to the wheel so the next order of business is to lift off the wheel. Once the wheel is off the vehicle and safely set aside, return to the vehicle. You now have access to the brake pad. The final step in the process is to inspect the brake pad for thickness and abno...

If you're a medical student, you'll learn a lot from this video lesson on examining your patient's eyes. If the patient is having trouble seeing, like double vision, blurred vision, pain or any other problem, a proper eye examination is detrimental to properly diagnosing and treating him/her. You can also determine and potential problems which may arise bases on your family history. Watch to see the complete procedure outlined, which is great for any med student or doctor. Even nurses can ben...

If you're a first year medical student, this is one of the skills you will be learning when training to become a doctor or physician— the ophthalmoscopic exam, which is an instrument for visually inspecting the retina and other parts of the human eye. Every doctor will carry an ophthalmoscope around in his/her pocket daily, so it's necessary that this would be one the first things you should learn in medical school. See how to examine the undilated eye, in five steps.

This video will teach doctor and medical students how to perform a full abdomen examination. John D. Gazewood, MD, MSPH, will show you the whole process, from the first steps of inspecting the abdomen, looking for abdominal contour and symmetry, to auscultation, percussion, and palpation of the abdomen. Some common findings during the inspection phase of the exam could be scars, striae, colors, jaundice, and prominent veins.

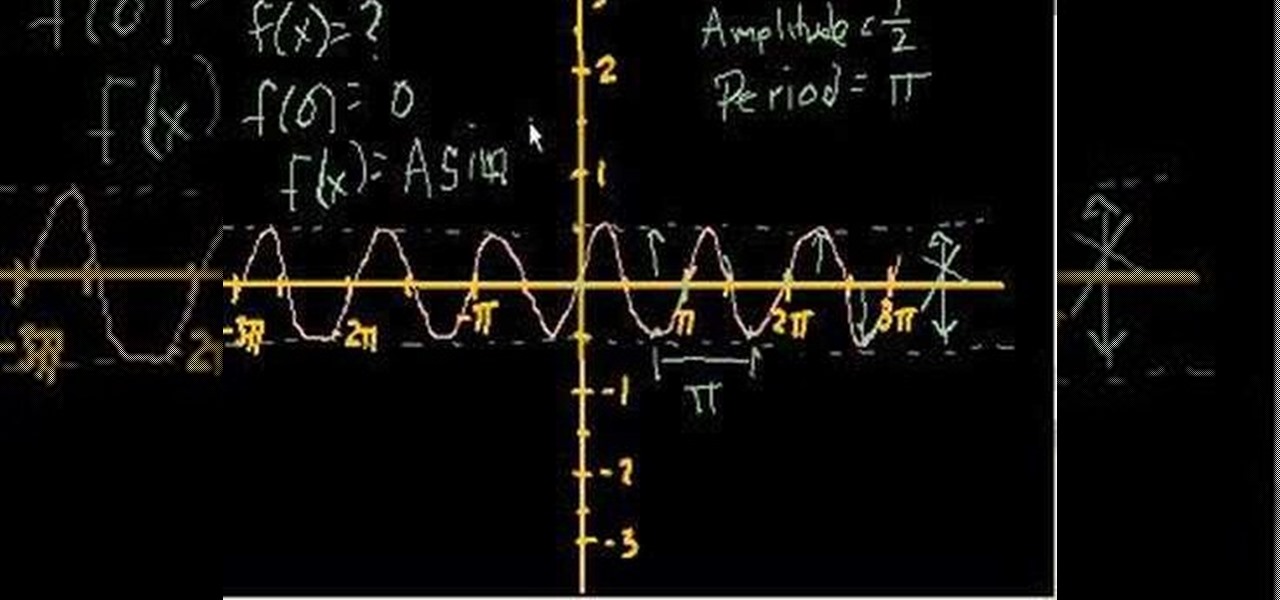
Need to know how to determine the equations of trigonmetric functions by inspecting their graphs? Learn how. Learn how to use trigonometric functions to calculate the sides of a right triangle. Need to know how to solve a matrix-form linear equation in algebra? From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just f...

Back again with another great instructional video, Mike Kraft, a Lowe's home improvement expert, demonstrates how to properly sharpen or replace the lawnmower blades on a riding lawnmower. Mike provides tips on inspecting your worn lawnmower blades to determine whether or not your blades need to be replaced, or merely sharpened. This video will give you an idea of the tools you will need to complete this project, as well as the steps involved in both removing and re-installing the lawnmower d...

In this tutorial, we learn how to install a ceramic tile floor. Before installing, you need to prepare a solid base. First, you want to take off the trim, then calculate the area of the room. Prepare the floor by inspecting low or high spots. You will want to apply mortar, then set the backer boards into place. Screw these into place, then finish covering the floor with seam tape. Apply mortar over these then let dry. Now, you can start laying your tile onto the top of this! Once you are fini...

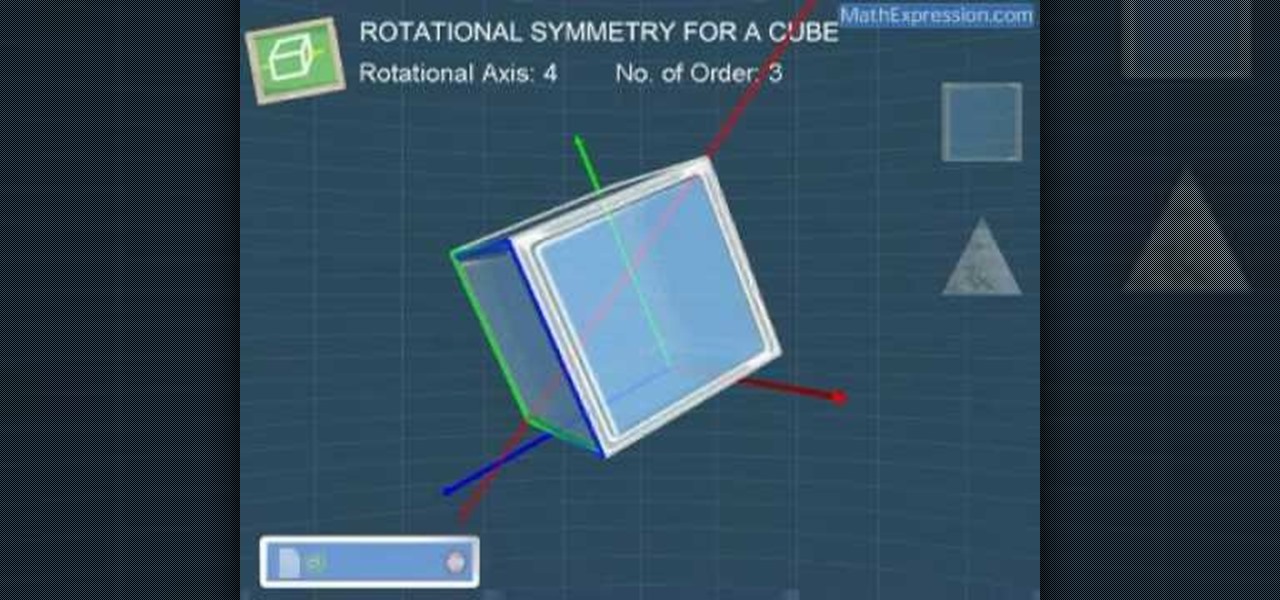
One of the most fascinating figures in the 3 dimensional world is the cube. This video goes into details about the rotational symmetry of a cube. The video examines this property of cubes by rotating the figure on different axis and inspecting how this property of cubes change or react. This video is for anyone interested in 3 dimensional figures. After watching this, viewers should have a basic overview and understanding of this unique rotational symmetry property of a cube.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Matteo Pisani, CTO and co-founder of Remoria VR, has managed to do something the folks over at Google said couldn't be done for at least a couple of years. With a little bit of tinkering, Pisani was able get his Google Daydream VR headset and remote to work on an iOS device.

With HoloLens and its enterprise-focused software offerings, Microsoft continues to make an impression on companies looking to adopt augmented reality, with Toyota Motor Corporation among the latest.

Traces of bacteria at a precinct in East Harlem created an all-out scare after doctors diagnosed an NYPD officer with Legionnaires' disease, a deadly infection caused by Legionella pneumophila.

Hello you sexy, savage, surreptitiously tech-savvy penetrators (Pun intended)!

Drone mishaps, such as the collision that scratched a military helicopter in New York, are becoming something of an everyday hazard.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

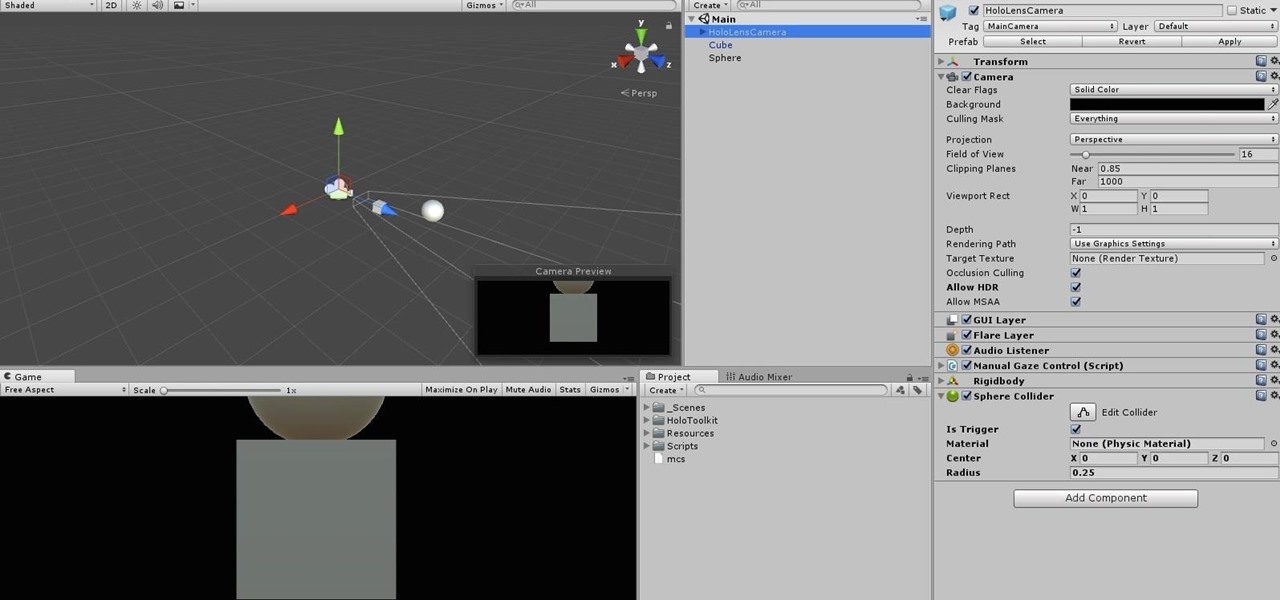
When making a convincing mixed reality experience, audio consideration is a must. Great audio can transport the HoloLens wearer to another place or time, help navigate 3D interfaces, or blur the lines of what is real and what is a hologram. Using a location-based trigger (hotspot), we will dial up a fun example of how well spatial sound works with the HoloLens.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

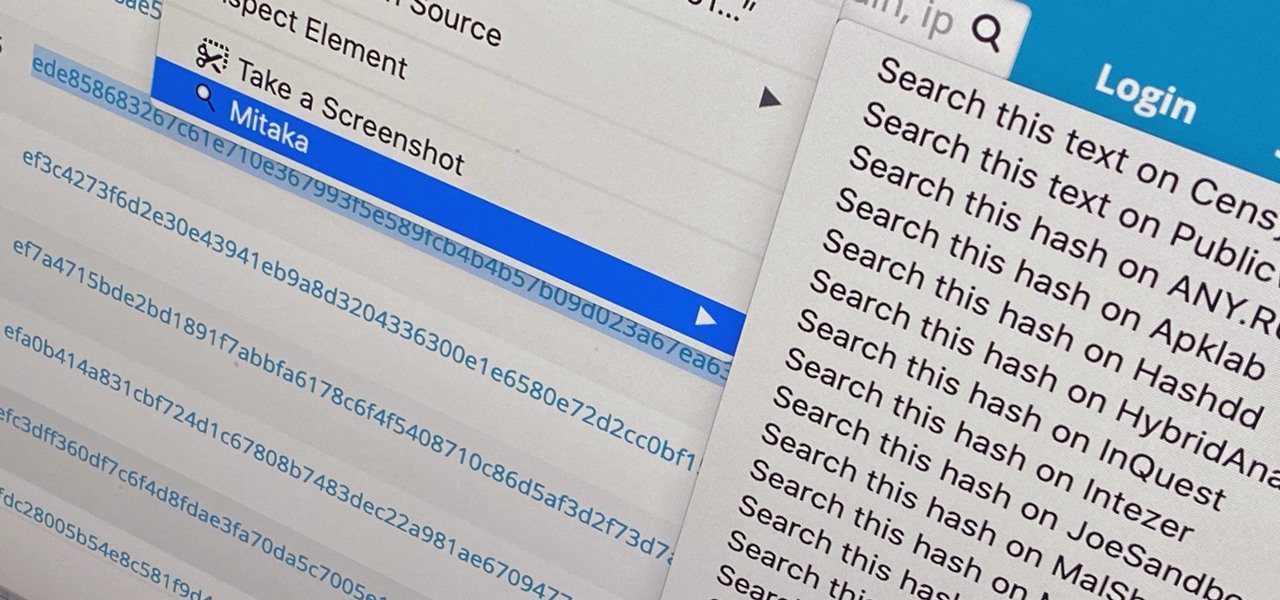
Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in particular, makes OSINT as easy as right-clicking to search for hashes, email addresses, and URLs.

Imagine the river and all its nobleness until the Jetski rips into the frame. In the distance you see a line across the river. Instead of inspecting the line the rider (Robb-me) goes full throttle at the line ( bunji-cord) Then the rider stands up just in time to catch it on the ribs. Sending the rider flying into the air like a bottlerocket. Landing what ever way was intended by what ever god you choose, personally I am choosing Poseidon because he could release the cracken would'nt that be ...

Yep, that's Michael J. Fox himself (aka Marty McFly) inspecting an 8-foot-long Delorean cake, complete with flaming tire tracks. The facsimile was artfully crafted by cake decorating masters Ace of Cakes for the 25th anniversary of Back To The Future and the Blu-ray releases.

Camera manufacturers release new versions of the same cameras, mostly point-and-shoot models, as frequently as Detroit's auto industry upgrades minivans. They also add new lenses regularly, upgrading previous models with adjusted zoom ranges or the image stabilization feature. The same goes for tripods, portable flashes and even camera bags.