In the 21st century, we're all looking for ways to stay private, especially on our electronic devices. We have big tech corporations, enemy countries, malicious hackers, and other prying eyes watching our every move, so it's only natural to want to limit what they can see. Making your web browsing experience on iPhone and iPad more private is one way to do that.
Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software.

Apple officially announced iOS 15 at WWDC Monday, June 7. With that announcement, we got our first look at brand new features like redesigned notifications, FaceTime screen and music sharing, and Focus modes in Do Not Disturb. All of these new iPhone features are available to test out today, thanks to the iOS 15 beta.
Your iPhone is full of features, many of which you might not even know about yet. Still, Apple keeps adding feature after feature with each new iOS update, and iOS 14.5 is no exception. The latest iOS version adds at least 69 features for your iPhone that you should be happy about.

Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's literally over 100 ways to make iOS on your iPhone genuinely unique, some of which are hiding in plain sight.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings change, interface update, or hidden improvement.

This video shows you how to work with the Text tool, and how to style text using the Property Inspector in Flash CS3 Professional. You learn about the difference between dynamic, input, and static text fields. This tutorial also covers device fonts, and explains the benefits of embedded and non-embedded fonts. Work with text in Flash CS3 Professional.

This video shows you how to style text using the CSS panel, instead of using the Property inspector in Dreamweaver CS3. You'll also learn how to tackle cross-browser CSS rendering issues using CSS Advisor. Check out this cool tutorial from Joseph Lowery now! Style text using CSS in Dreamweaver CS3.

This video shows you how to create email links, text links, and image links to internal and external pages on a website using Dreamweaver CS3. You learn how to use the Link box, folder icon, and Point-to-File icon in the Property inspector to create links for text or images. You also learn how to add e-mail links using the Insert bar. Create links in Dreamweaver CS3.

This video shows you how to change the appearance of form fields using CSS. You create a new class for the form labels then apply the style to labels in your form using the Property inspector. You create another style to affect the look and feel of the form elements. Style forms with CSS in Dreamweaver CS3.

While mold is a naturally occurring phenomenon outdoors and in nature, it can be a major health hazard and an expensive problem if it infiltrates the inside of your home.

Iraq war reconstruction: $6 billion to $8 billion wasted, US official says - Open Channel. The official in charge of monitoring America’s $51 billion effort to reconstruct Iraq has estimated that $6 billion to $8 billion of that amount was lost to waste, fraud and abuse.

Hey Everyone! Welcome to my post. We have seen a numerous GUI Tool in kali linux. Armitage, wireshark, Burpsuite etc,. Lets see an another GUI tool.

Geoff Blake goes through some of the new CSS features of Dreamweaver CS4. Whether you are a CSS (Cascading Style Sheets) rookie or veteran, you’re going to enjoy the new CSS tools and layout which make it easier to apply and remove formatting, creating external style sheets, and reviewing related files to your current document. You will also see how well the new properties inspector works. Familiarize yourself with the new CSS tools and layout in Dreamweaver CS4 in this Adobe tutorial. Use th...
Let’s say you have a MOOG keyboard you want to send into Logic. To set this up, there’s a few things to do in Logic.

Well, I just saw this on digg and thought it was very funny. So what type of gamer are you?

Food & Flowers Freedom Act in Los Angeles

Welcome to the second Null Byte in a series educating you on Social Engineering awareness and techniques. Today, I'm going to show you how a saavy Social Engineer would trick a friend into unknowingly surrendering their Facebook password. My intent is to warn and demonstrate how easy it is to succumb to phishing via Social Engineering, and therefore expose yourself.

InfoWorld has some expertise advice for the new Windows 7 operating system from Microsoft. Now that Microsoft has made the Windows 7 beta available for public download, many people are trying to figure out what's new and different. And many others not willing to risk their PCs by installing a beta OS are curious, too.

Aram Bartholl over at F.A.T. is pretty pissed because MoMA is discriminating against internet artists. As most New York-based working artists know, MoMA offers annual membership for only $35 (compared to the standard rate of $75) to artists who can provide "credentials" that prove legitimacy. Though the offer isn't publicized on the MoMA site, word on the street is "credentials" equates to "a letter from the gallery or an announcement for one of the artist's shows within the past two years" (...
Fort Leonard Wood Public Affairs director Tiffany Wood has provided the first official response to the shocking U.S. Army document that outlines the implementation of re-education camps, admitting that the manual was “not intended for public release” and claiming that its provisions only apply outside the United States, a contention completely disproved by the language contained in the document itself.

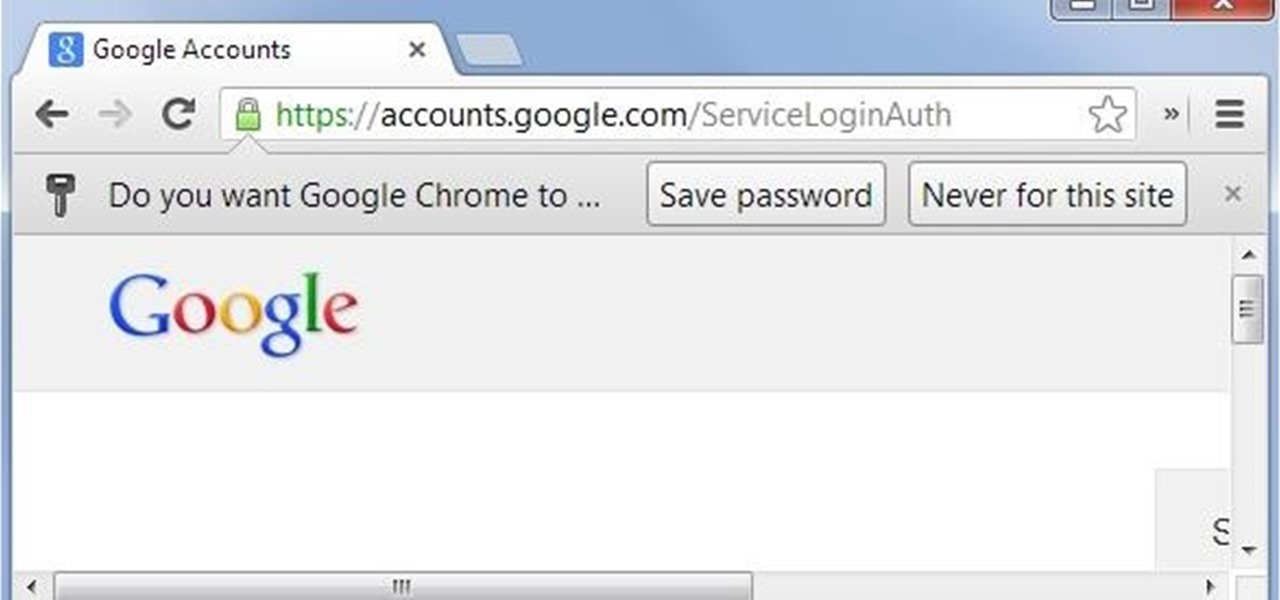
These days I found a very beautifull python script that just prints the google chrome usernames and passwords that are stored on your machine.

Hi everyone! This is my first How To. Before we start you need to have a Facebook account (of course) and...this only works with your Facebook friends (so if you're looking for someone's mail on Facebook but you're not friends this won't work)

Apple has announced the release of their OS X Beta Seed Program today, which allows anyone with an Apple ID and a Mac to download and run the latest developer build of Mac OS X 10.9.3—the most updated beta version of Mavericks. The OS X Beta Seed Program allows us to run software that was once only available to limited test audiences or registered Apple developers—with the latter costing $99 a year for a membership. With this program, not only do we get our hands on extremely new software, bu...

Blowing an egg out of its shell is one of the oldest tricks in the book. However, it's not quite as easy as a quick exhale into a fractured hard-boiled egg.

Last Friday's mission was to accomplish solving HackThisSite, basic mission 10. This mission teaches us how to use JavaScript to manipulate cookies on poorly coded cookie-based authorization.

Security awareness seems to be a hot topic these days on the web, with developers making apps and devices that can hack networks and machines with just a few clicks. But these applications aren't only exploiting security flaws in systems and networks, they're being used by amateur and wannabe hackers who want to have a little fun, but don't want to learn how to actually "hack" anything.

Firesheep caused quite a stir when it was released last October, giving both hackers and non-hackers instant access to people's account information when on a public Wi-Fi connection. When logged into an insecure website on the same network as someone with Firesheep, you're giving them access to the cookies that keep you logged in. This is called session hijacking, and grants them easy access to your accounts, like Facebook, Flickr and Twitter. Now, there's an even easier way to do this—a mobi...

If you own an Android device and a Windows computer, there is absolutely no reason you shouldn't have Pushbullet installed. With the Android app and a companion Chrome plugin, you can easily send files between all of your supported devices, and there's even a notification mirroring function so that you never miss an important update.

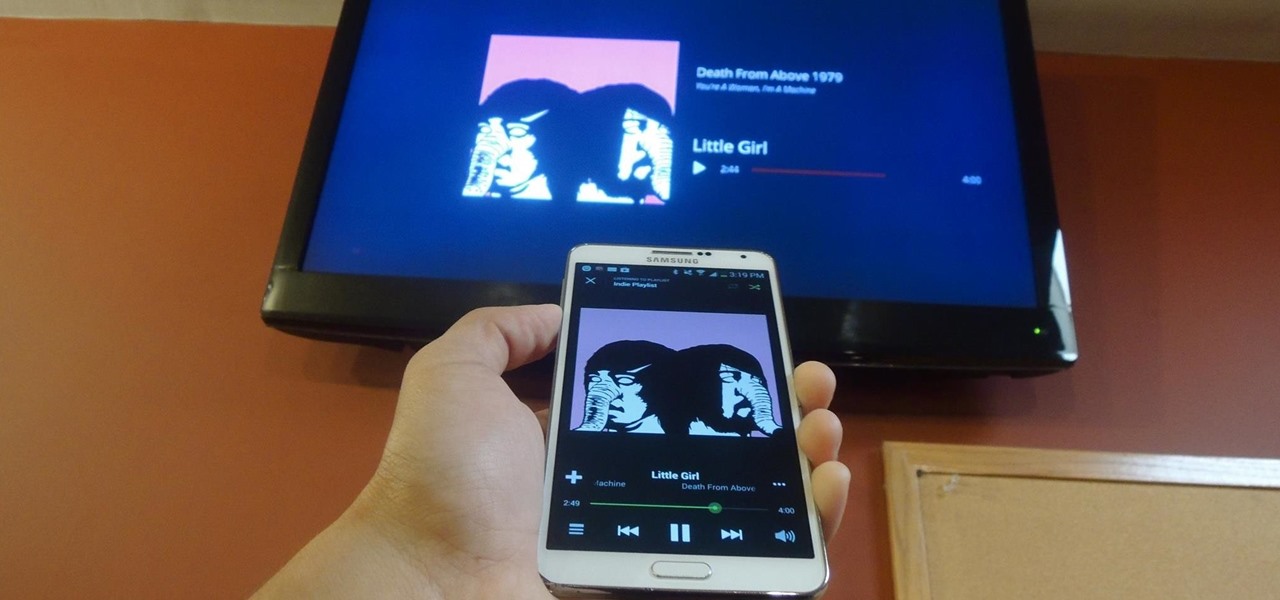
Up until now, the closest thing we've had to Spotify casting is Projectify, which streams music videos from YouTube and other video sites to Chromecast using music from your Spotify playlists.

Here's another delicious Byte. Ucha Gobejishvili, a Georgian Security Researcher under the handle of longrifle0x, discovered two cross site scripting (XSS) vulnerabilities on the official website of Forbes. He discovered the hole in two different locations on the site, and has already informed the website of the vulnerability.

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

Permanently deleting files is something that a lot of people aren't aware of. Actually, most people think that once a file is deleted, it is gone forever. This is not the case. Hard drives write to the disk via magnetic charges, positive and negative correlate to 1s and 0s for binary. This is then interpreted into information for the computer to use and access.
Many people must be asking, how do you enter a coupon code on Wizard101? This is a follow-up of the "Promo Code: 1000 Gold Coins" post. So here's how you do it:

Things You'll Need A fully working operating system that supports VirtualBox (Windows, OS X, Linux or Solaris)

Oh yeah, this is a big topic, at-least for me. All the frequent flyers will/should be interested in this topic. I'm sure all of you have heard at-least something about the TSA, and most of it should have been bad. Complaints, lawsuits and general disgust surround this organization. Is there a reason, or are the 'extremist liberals' at it again? Let's find out!

Here's a nasty little Null Byte. An open redirect vulnerability was found in both Facebook and Google that could allow hackers to steal user credentials via phishing. This also potentially allows redirects to malicious sites that exploit other vulnerabilities in your OS or browser. This could even get your computer flooded with spam, and these holes have been known about for over a month.

This is Part II in the Lockdown: The InfoSecurity Guide To Securing Your Computer series. Before beginning, check out Part I. This article will cover using alternate software to increase your security and will provide you with some information about websites and programs that test a computer's security. It will also guide you to software you can install or follow so you know what programs need to be updated on the computer. Lastly, I will talk about some features that should be disabled when ...

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...