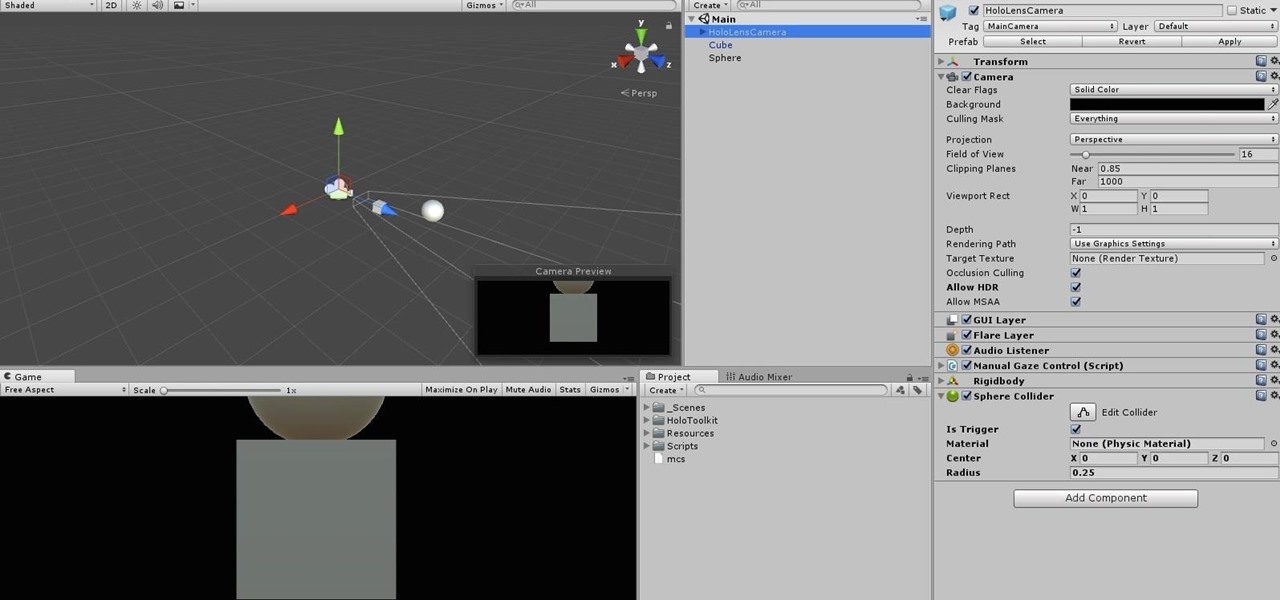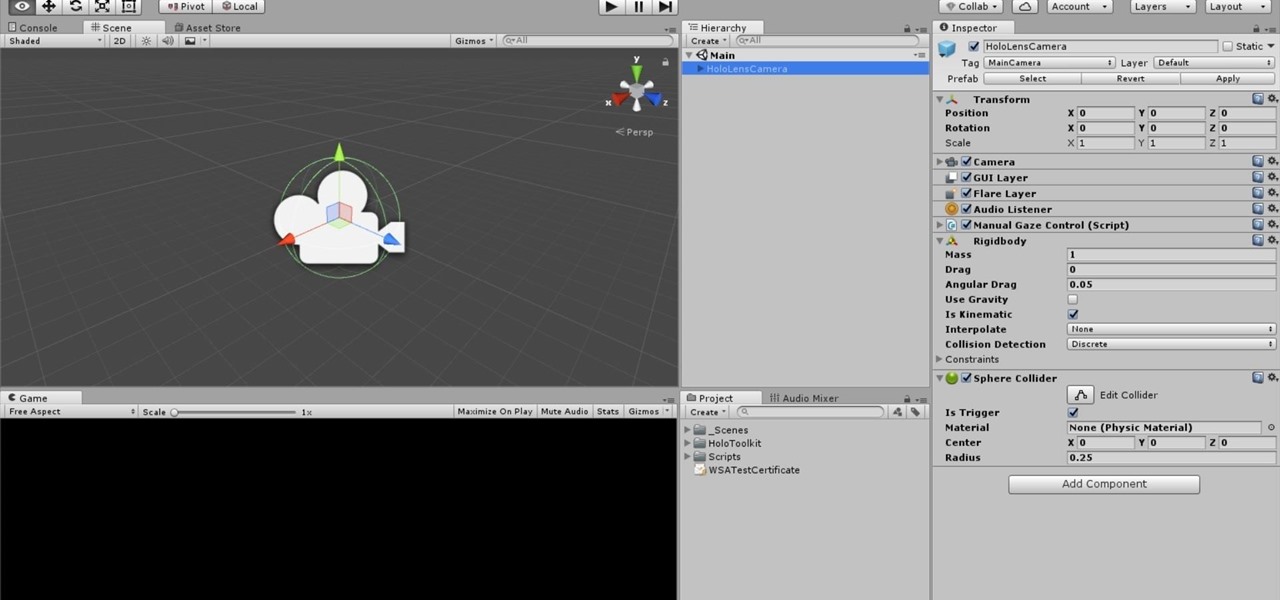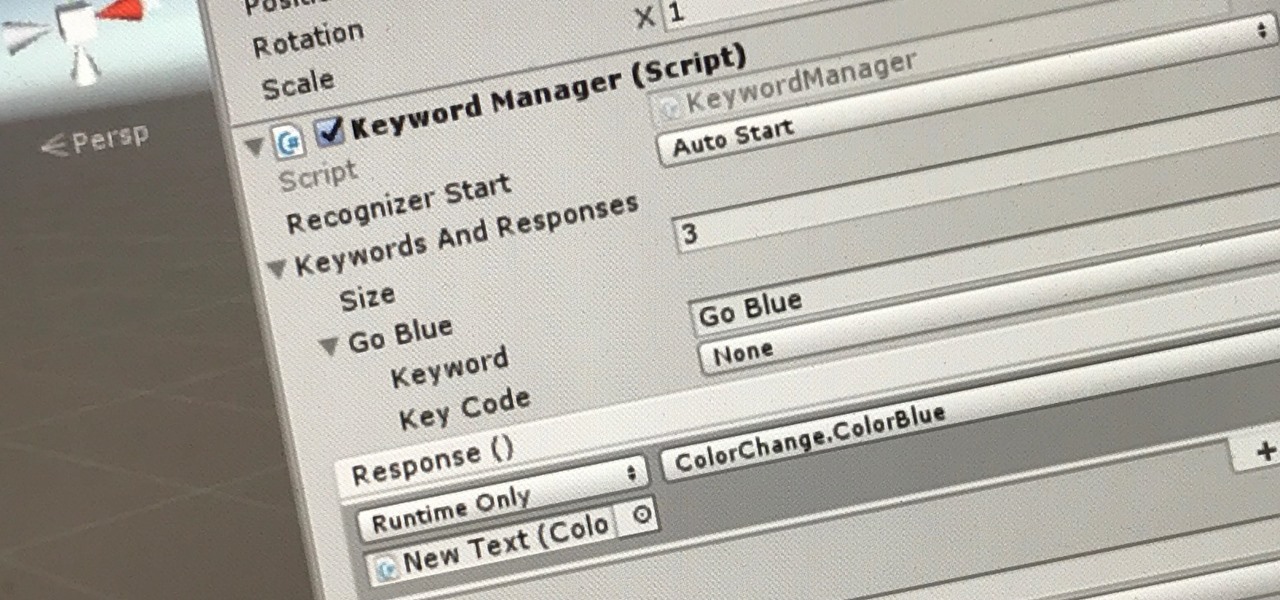
The HoloToolkit offers a great many, simple ways to add what seems like extremely complex features of the HoloLens, but it can be a bit tricky if you're new to Windows Holographic. So this will be the first in an ongoing series designed to help new developers understand what exactly we can do with the HoloLens, and we'll start with voice commands.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.
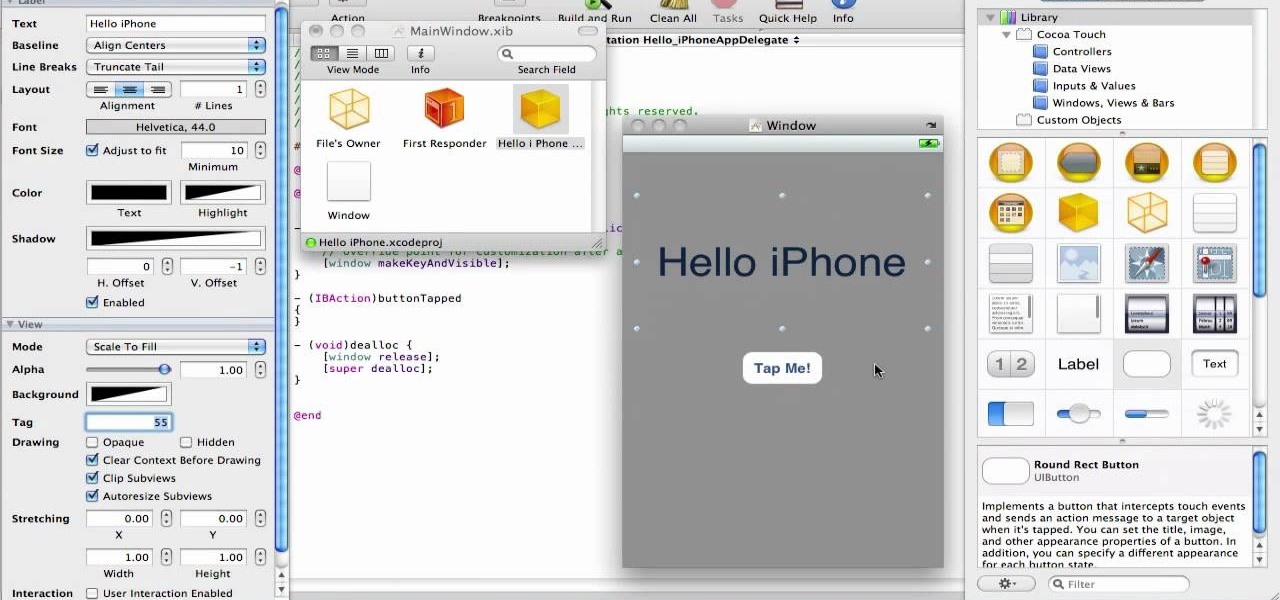
In this video from XcodeMod we learn how to make an iPhone app with Xcode. Open up XCode and go to File...New Project. Pick what kind of app you'd like to save it as and come up with a name to save it as and save it to your desktop. Open the Classes folder and go into the AppDelegate.H. In the space above @end, type - (IBAction) buttonTapped to create a button. Save that, copy that line and paste it where you want the button in your appdelegate.M. Now in Resources folder open the Mainwindow.x...
If you're not much for office computers, and like using your own powerful PC at your workstation, then chances are, you're going to have to login to the network. Microsoft shows you how to quickly login and join a Domain or Workgroup in an office network.
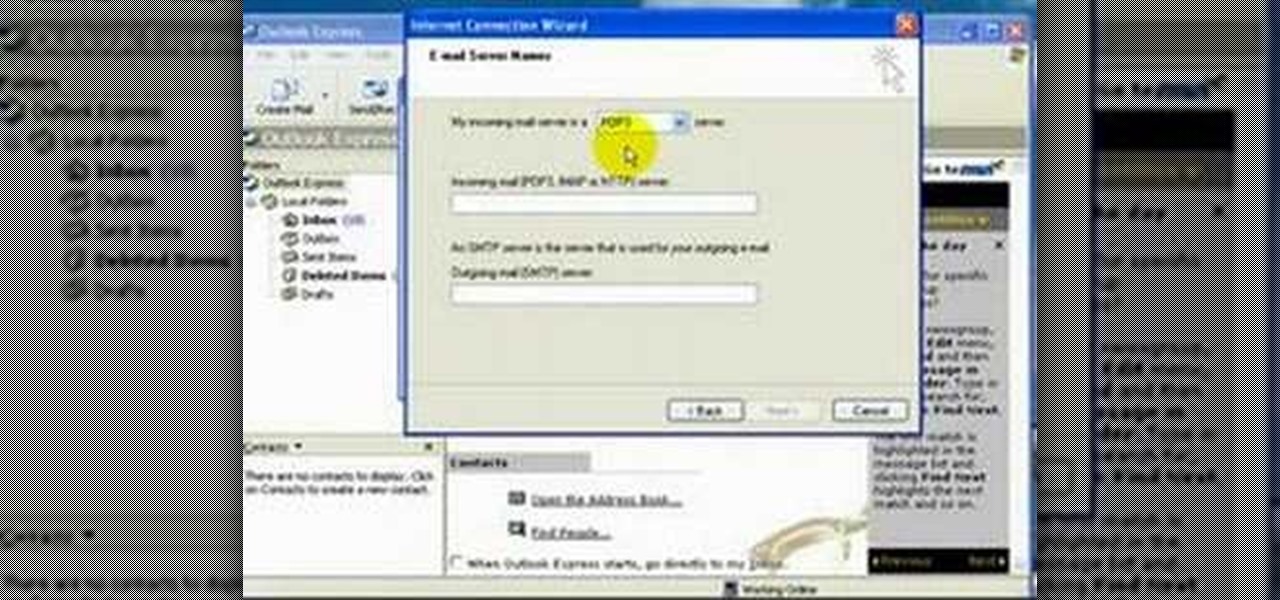
Carole Gallesie from Creative Media Web shows viewers how to set up a new account in Microsoft Outlook Express. Express is preferred because it is a scaled-down version of the popular email client and it is easier to navigate. From your Windows desktop, go to the start menu, all programs, and click on outlook express. When the program opens, look at the top of the page for the "tools" menu, select accounts, add, and mail. The new account wizard will then appear and will walk you through setup...

This video shows you how to make a title intro with iMovie and keynote. Step one is to open up keynote. The resolution for the videos should be in 720 HD. The next thing to do is to type in the text that you are going to use. Change the font and the color to suite the style you are going for. Insert graphics where ever you would like to. Then in the top right hand corner click on the inspector button and add in the animations and movements that you want to see in the video. Now you have to or...

Michael Weisner teaches us how to draw a cartoon bed. His credentials boast of him to be a computer animator. He starts the video off in a rather creative way with him as a cartoon. He slowly draws a cartoon bed by hand. He does this step-by-step, starting from the base up. Going rather quickly, he draws a bed and outlines it in marker. As Michael is drawing, he narrates the process and explains what he is doing and how it is done.

Oktay1979 takes a look into writing an annotated bibliography. Learn the steps such as citing a source, summarizing your reading, accessing your source, documenting your authors credentials, and reflecting on your source. Each bibliography is usually 150 words long and done in new times roman. You can also get a form to show you how to format the bibliography correctly. Make your writing process unique and accurate. Make sure you're doing your bibliography right by following the correct steps...

This is a basic video in order to draw a very pretty heart. The credentials that this creator boasts is that of a computer animator. He already drew a heart in pencil. He starts off by telling us the materials that he needs. The video shows him highlight and underline the pencil heart that he drew earlier and making it bolder. He talks us through making the heart, but does not slowly explain the specific strokes or techniques into making it.

Got some information you want to circulate quickly and extensively? Learn what it takes to get people to pass it along.

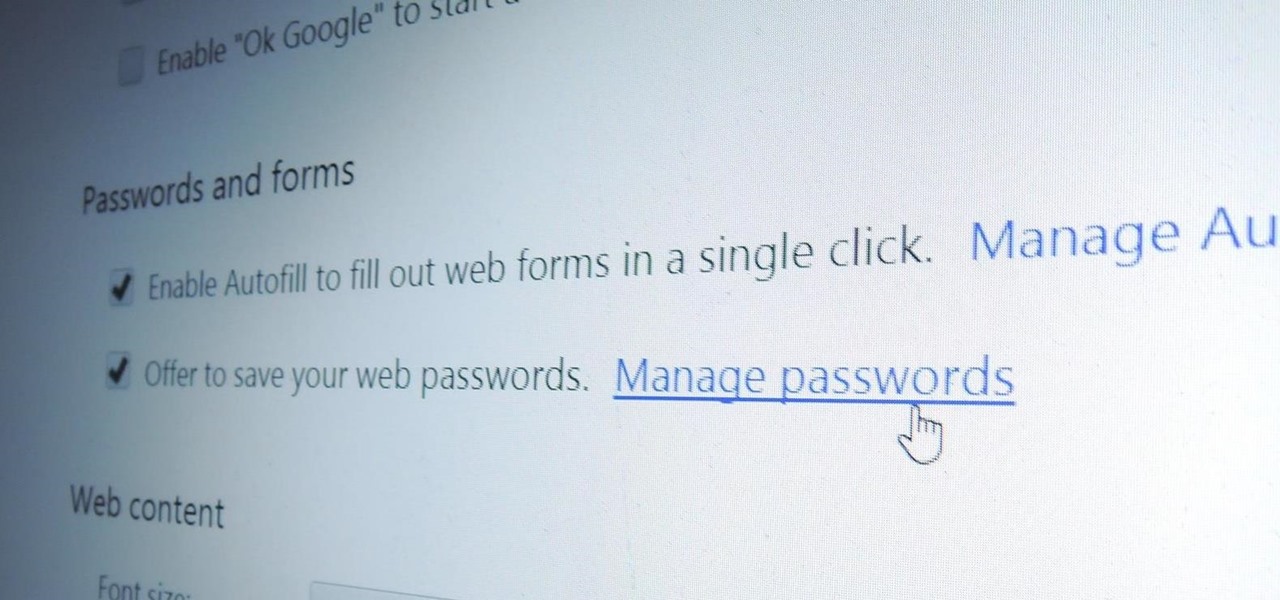
A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface.

YouTube's main player interface got a pretty big makeover recently, but chances are, the new UI hasn't made it your way just yet. Google has a habit of slowly testing the waters as they roll out new features, so cool tweaks like this can take some time to reach all users.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

It's March once again, and while that might signify the beginning of spring for some, basketball fans have this month marked on their calendars for one good reason: NCAA March Madness. Though the tournament is already underway, the Sweet Sixteen leg begins Thursday, March 23, 2017. If you fear you may miss the upcoming games, worry not, as free apps for smartphones and tablets are available to help you watch all the action.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

Welcome back, my greenhorn hackers!

As deeply as smartphones are integrated into our daily lives, it's no surprise that people are finding ways to use them to stay healthy. From detecting cancer and radiation to diagnosing STDs, phones have come a long way, baby.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

While iPhones may be more expensive than ever, it won't stop us from losing them or having them stolen. Whether you have an iPhone 5S or an iPhone XS Max, there's a good chance it'll go missing at some time during your ownership. It could end up in a couch cushion or in the hands of a pickpocket, but no matter what happens to it, you need to prepare it beforehand for the inevitable.

iOS 12 has a feature that lets you instantly share saved Wi-Fi passwords with other iPhone users, but it can be finicky when you're sharing with multiple people. Then there's an even more pressing question: How do you share your password with Android users? Thankfully, there's a Shortcut that can solve these problems.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.

Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them.

The folks behind StumbleUpon have created a video service that is just as awesome at introducing you to new content as their website service is.

Now that we have unlocked the menu movement — which is working very smoothly — we now have to get to work on the gaze manager, but first, we have to make a course correction.

Now that we've set up Vuforia in Unity, we can work on the more exciting aspects of making physical objects come to life on the HoloLens. In this guide, we will choose an image (something that you physically have in your home), build our ImageTarget database, and then set up our Unity camera to be able to recognize the chosen image so that it can overlay the 3D holographic effect on top of it.

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

When making a convincing mixed reality experience, audio consideration is a must. Great audio can transport the HoloLens wearer to another place or time, help navigate 3D interfaces, or blur the lines of what is real and what is a hologram. Using a location-based trigger (hotspot), we will dial up a fun example of how well spatial sound works with the HoloLens.

One of the truly beautiful things about the HoloLens is its completely untethered, the-world-is-your-oyster freedom. This, paired with the ability to view your real surroundings while wearing the device, allows for some incredibly interesting uses. One particular use is triggering events when a user enters a specific location in a physical space. Think of it as a futuristic automatic door.

Welcome back to this series on making physical objects come to life on HoloLens with Vuforia. Now that we've set up Vuforia and readied our ImageTarget and camera system, we can see our work come to life. Because in the end, is that not one of the main driving forces when developing—that Frankenstein-like sensation of bringing something to life that was not there before?

Now that we've got all of our software installed, we're going to proceed with the next step in our HoloLens Dev 101 series—starting a fresh project and building it into a Holographic application. Then we will output the application to the HoloLens Emulator so we can see it in action.