When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

By default, there aren't many customization options for the notification badges on iPhones — you can either leave the numbered red bubbles there, or turn them off. But thanks to a new jailbreak tweak, you can now give your badges a unique look with new functionality.

On Monday, with just days left before Christmas, Lowe's dropped a surprise augmented reality treat in everyone's lap: a brand new Magic Leap One app.
According to Google's new Android ecosystem transparency report, you're eleven times more likely to be infected by malware if you're running Android Lollipop (5.0) as opposed to Android Pie (9). The same report shows that if you sideload apps, you're almost seven times more likely to be infected than if you stick to Google Play as your app source. All of the data provided in the report is quite interesting, but there's a clear pattern among malware-infected users.
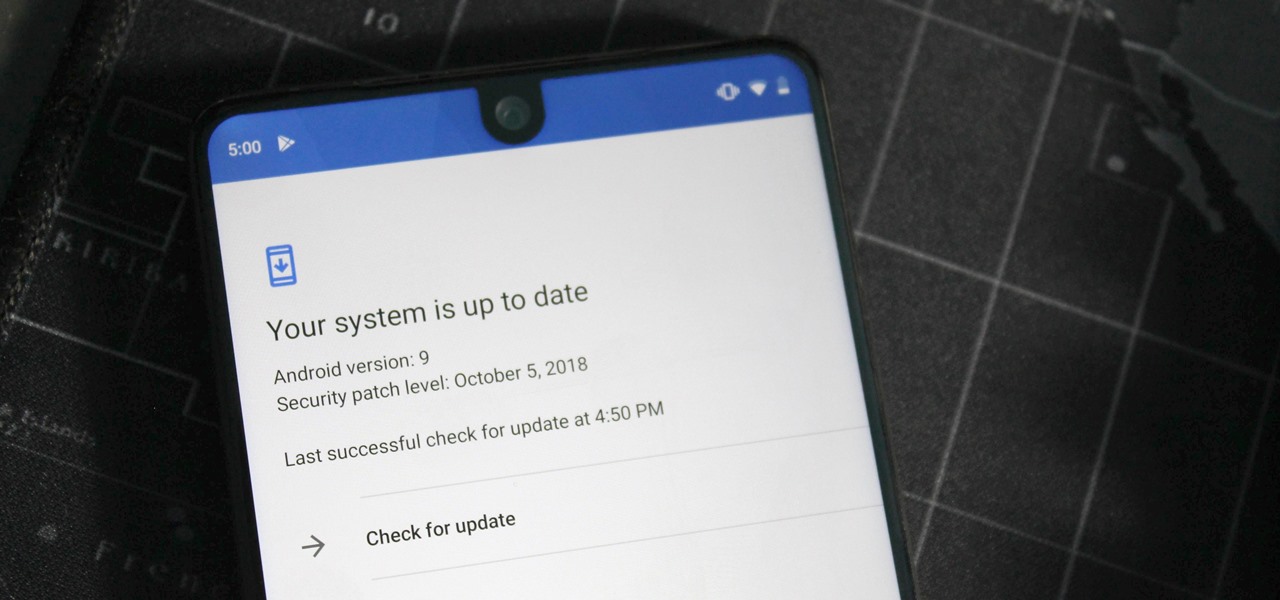
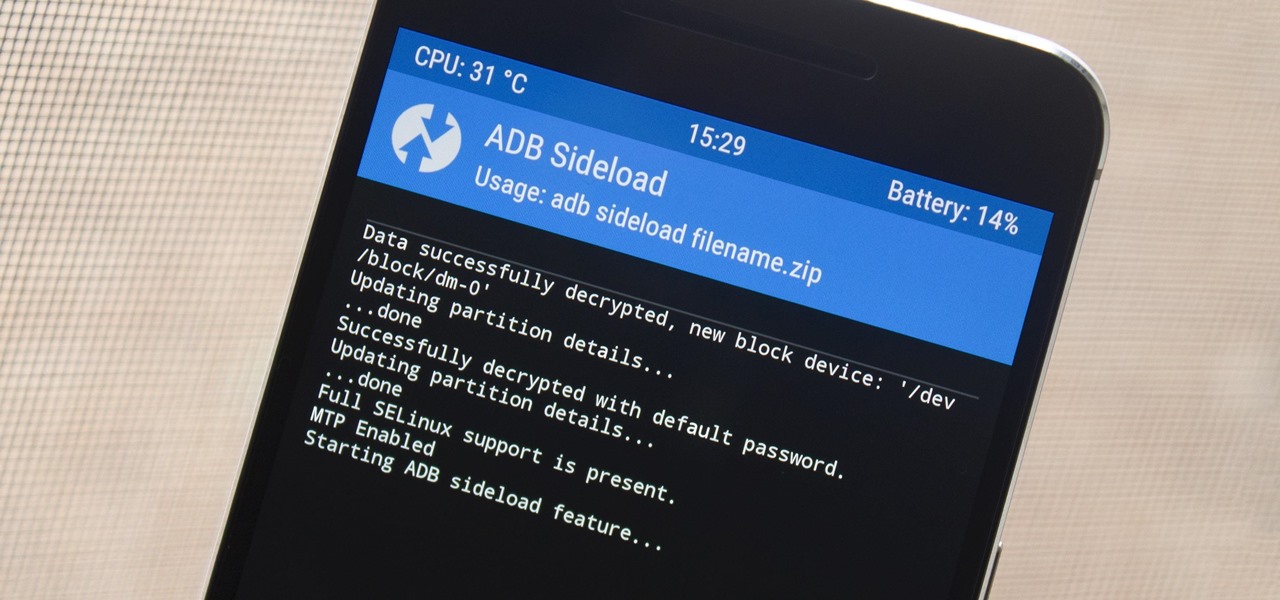
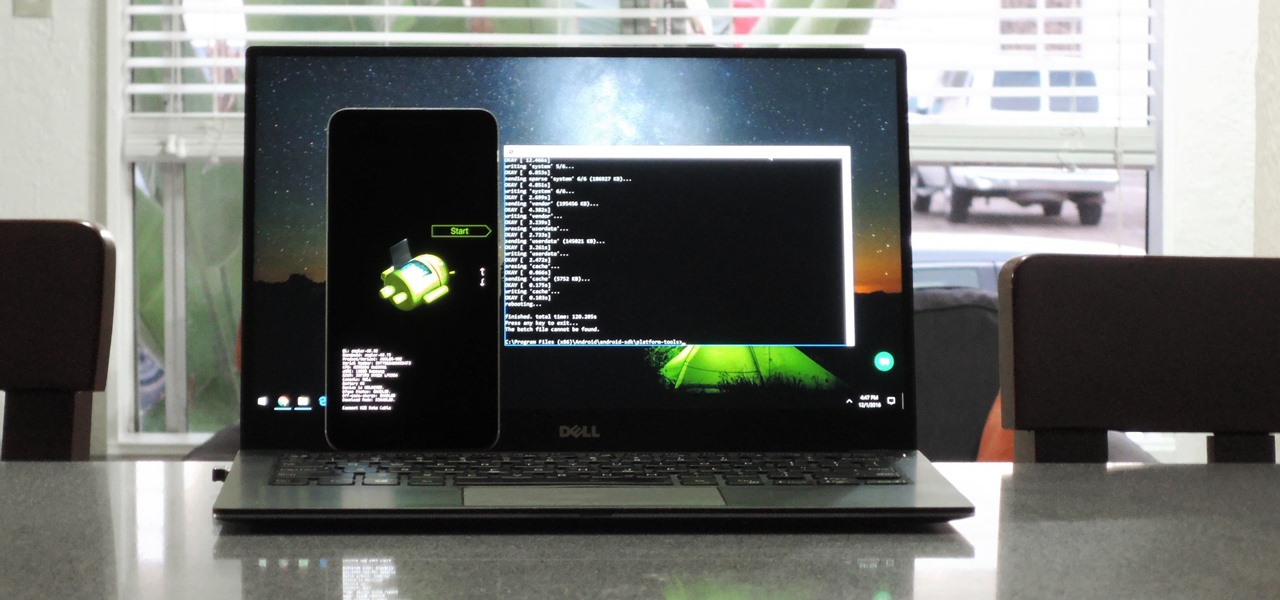
One of the issues with rooting your device is the inability to update your phone via OTA. Any security patches or software updates pushed out by the OEM are lost because your bootloader is unlocked. However, you still can update your device, it just a take a bit more effort.
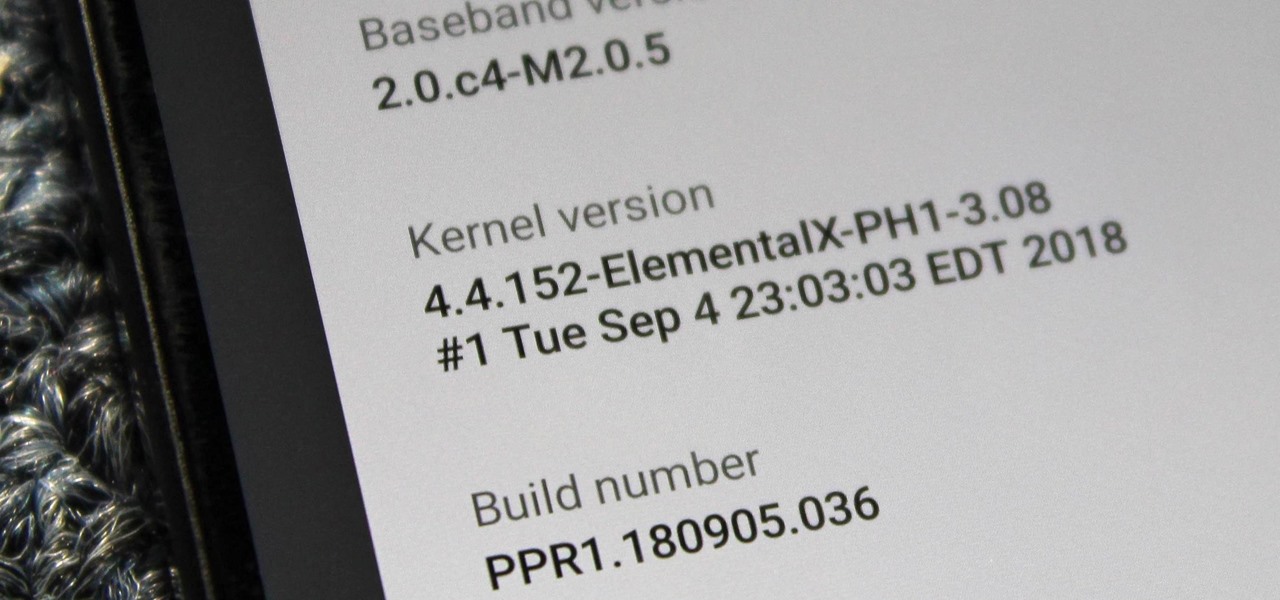
When you unlock the bootloader on your Essential PH-1, you open your device to a host of new possible tweaks. One popular modification is a custom kernel, which can not only speed up your phone, but give you new features that wouldn't be possible otherwise.

Google and Apple are working to enable augmented reality content for the web, but startup 8th Wall has managed to launch a web AR platform that works on mobile browsers now.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Low Power Mode can go a long way in preserving your iPhone's battery life in a pinch. It can be set manually or appear as an option once your battery levels dip to 20 and 10 percent. If you have a jailbroken device, you can take Low Power Mode a step further by having it automatically turn on whenever using Do Not Disturb.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

When it comes to modding Android, there's no better tool than Team Win's TWRP custom recovery. You can use it to root your phone, flash mods like Magisk or Xposed, and even replace the entire operating system with a custom ROM like LineageOS — honestly, there's not much this utility can't do.

Thanks in large part to our phones, many of us don't get the recommended eight hours of sleep. In Android Pie, Google introduced a feature called "Wind Down" that aims to help combat this. However, thanks to a creative app developer, we don't need to wait for Android 9.0 to enjoy this feature.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Starting with Android 8.0 Oreo, the process of sideloading apps has changed dramatically. Google removed the old "Unknown Sources" setting and replaced it with a permission that you have to grant to individual apps. It's really an interesting security feature.

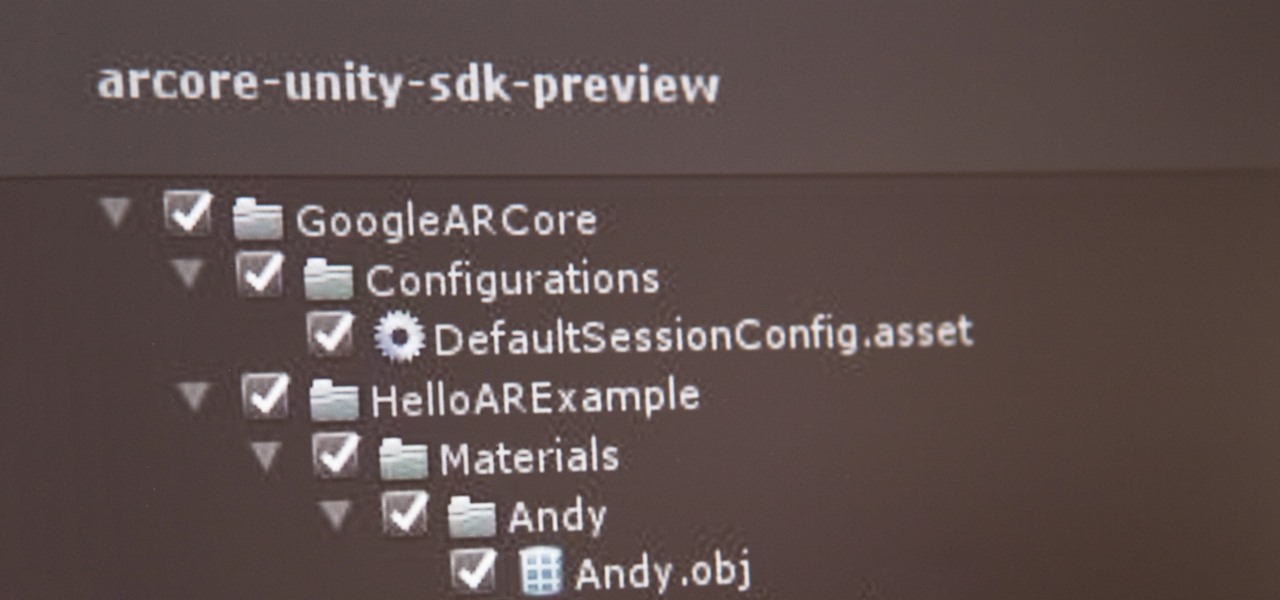
If you've contemplated what's possible with augmented reality on mobile devices, and your interest has been piqued enough to start building your own Android-based AR app, then this is a great place to to acquire the basic beginner skills to complete it. Once we get everything installed, we'll create a simple project that allows us to detect surfaces and place custom objects on those surfaces.

For parents that have an iPhone X, things are about to get a lot easier for you in iOS 11.3, which finally lets you approve app and media downloads on your child's iPhone using Face ID instead of typing in a password.

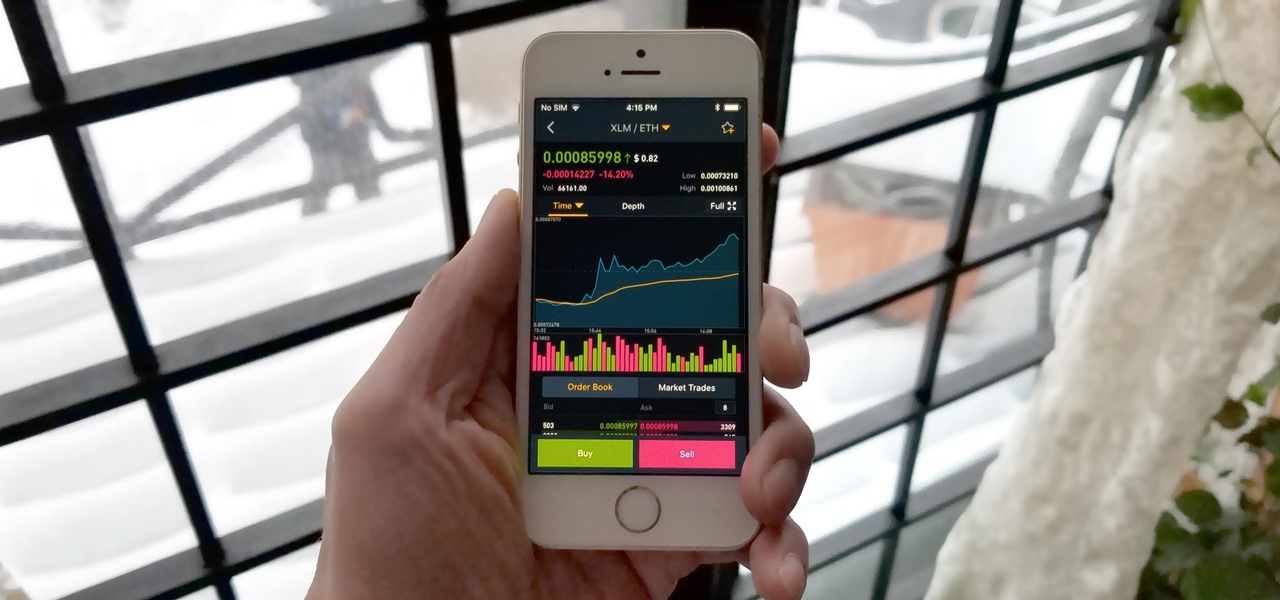
Binance, a China-based cryptocurrency exchange, is rapidly gaining popularity thanks to the sheer selection of digital currencies you can purchase — Ripple (XRP), Tron (TRX), IOTA, and Stellar (XLM), to name a few — using both Bitcoin (BTC) and Ethereum (ETH). Binance has an iOS app, and there are a couple ways to install it. Either way, you can trade cryptocurrency from your iPhone today.

For years, PuTTy has reigned supreme as the way to establish a Secure Shell (SSH) connection. However, those days are numbered with the addition of the OpenSSH server and client in the Windows 10 Fall Creators Update, which brings Windows up to par with macOS and Linux's ability to use SSH natively.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

The OnePlus 5 had been in the hands of the public for a meager twenty hours before developers on XDA released a custom recovery image for it, and the 5T had a similar trajectory. The installation process is simple enough, but it can be somewhat confusing if you're new to modding Android.

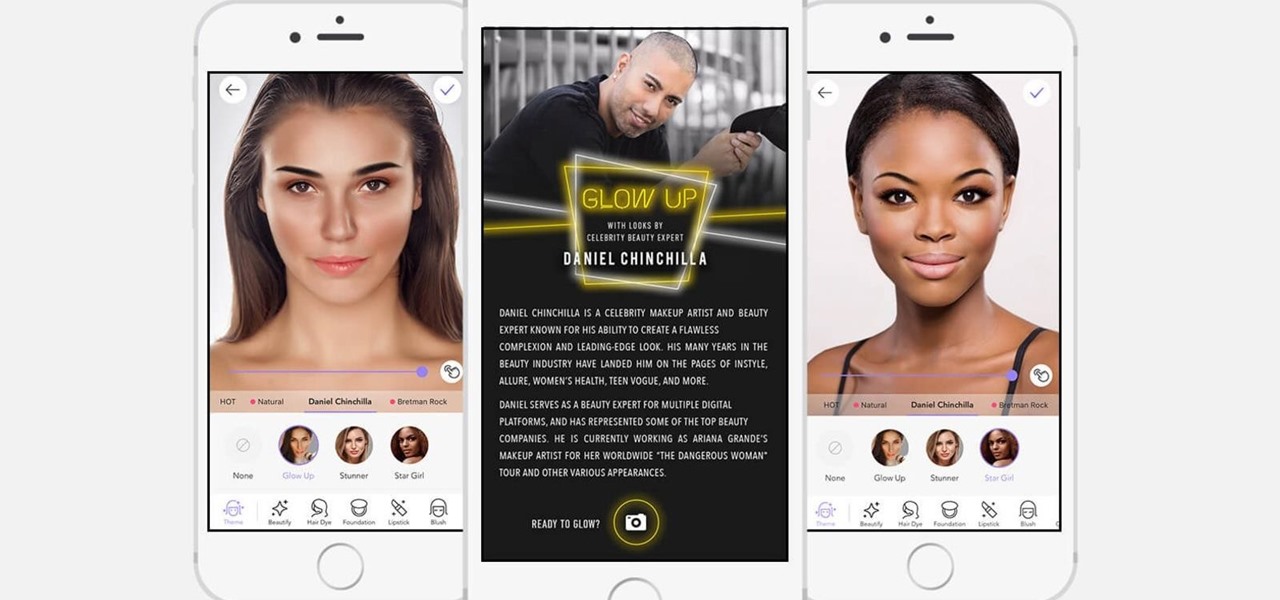
If it's not official by now, it really should be: if you're going to sell cosmetics, you need an augmented reality app. Of course, that's not all augmented reality is good for. It can be used to animate medical models and engage sports fans. Read on below…

Despite packing some really nice camera specs, the OnePlus 3 and 3T don't take the best pictures. That's because, these days, great software is just as important as great hardware when it comes to image quality.

Every now and then, it's refreshing to play a game that doesn't involve much thinking. Sega is set to bring us just that, as a new game called WWE Tap Mania has soft launched for iOS and Android in the Philippines.

Preorders for the LG G6 have all been fulfilled, and the phone has been up for grabs at local cell phone providers for three weeks now. However, not every LG G6 was created and released equally. The T-Mobile variant of the LG G6 features an unlockable bootloader, while most other North American variants come with a tightly locked down bootloader, which effectively limits the full potential of your brand new fairly expensive phone.

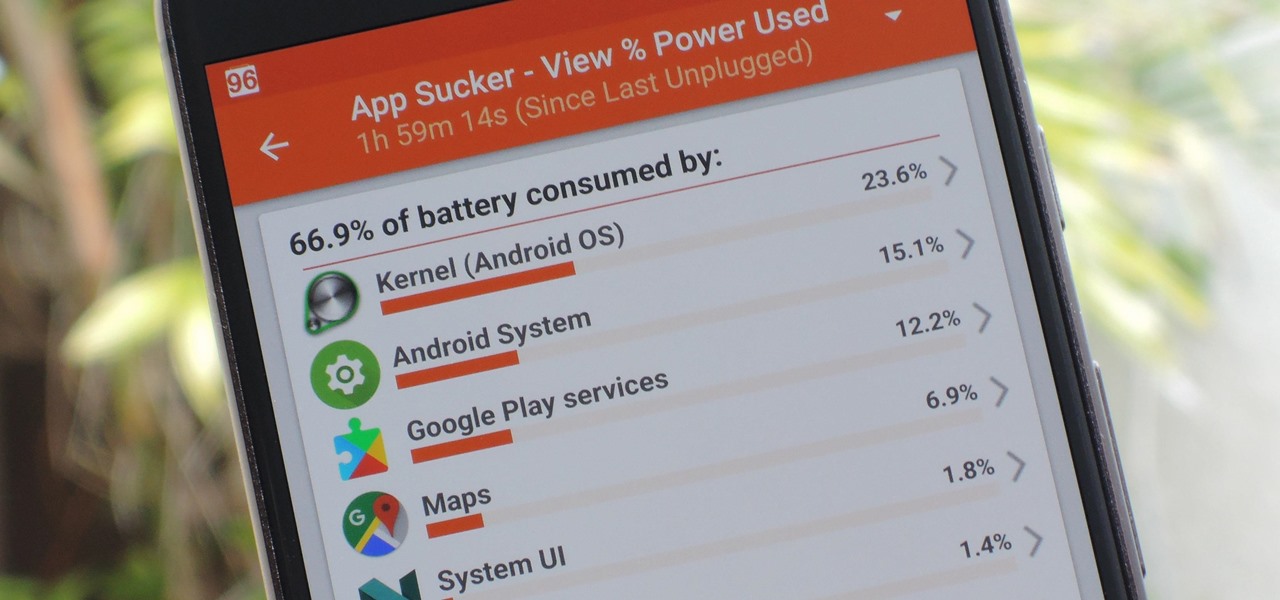
Figuring out exactly which apps on your phone are eating through resources and battery life can be a difficult task. Though some information can be found in Android's battery menu, the charts and graphs provided here pale in comparison to what's offered by the GSam app. If you configure this app properly, it provides deep insight into battery, CPU, and data usage.

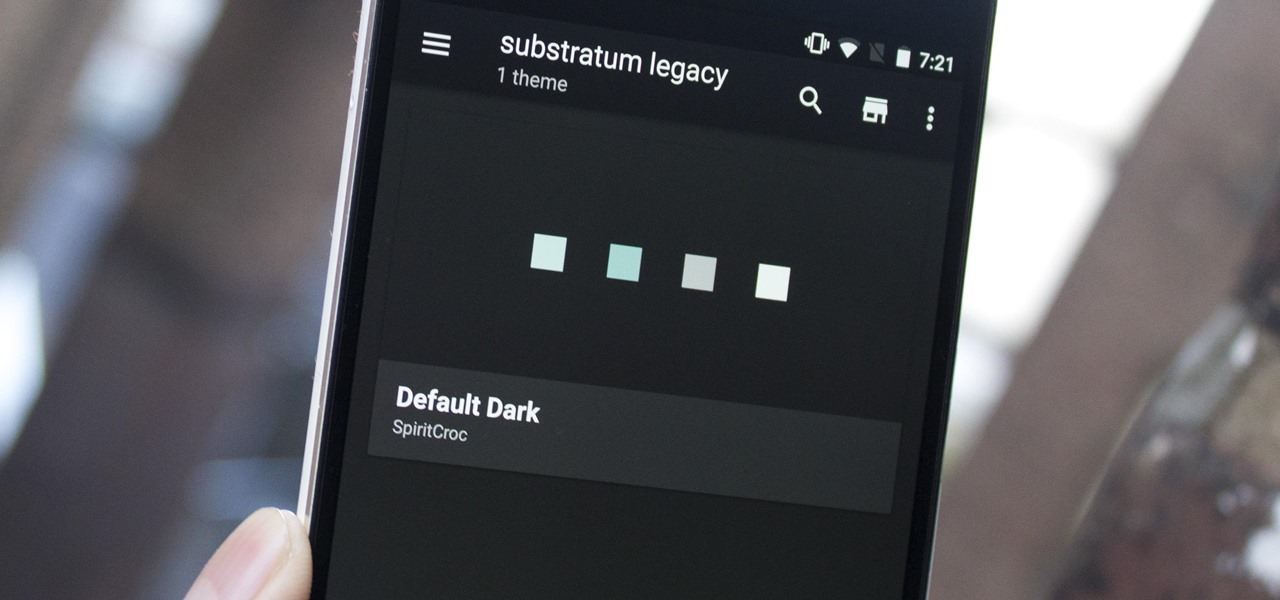
Perhaps one of CyanogenMod's greatest features was its built-in theme engine. It wasn't perfect, but it got the job done and gave users a unique look. Now that CyangenMod is defunct, and the developers behind its successor, LineageOS, have confirmed they won't be continuing the theme engine, users have to find another way to theme their devices. No need to fear, though, Substratum is here.

The Galaxy S8 and S8+ haven't even hit shelves yet, but some of the stock apps from Samsung's latest flagships have already been leaked. The biggest one so far is the new Samsung Experience Launcher, which replaces TouchWiz Home, and is quite a bit different from anything you'll find on previous Galaxy models.

Just days after the first Android O preview build was released, the development community had already started bringing some of the exclusive features over to older Android versions. For instance, the Pixel Launcher received an update in Android O, and developer linuxct quickly ported the new version to work on devices running Marshmallow or higher, and even managed to do so without requiring root.

It's official — the newest version of Google's mobile operating system is called Android 8.0 Oreo, and it's in the process of rolling out to many different devices. Oreo has plenty of changes in store, ranging from revamped looks to under-the-hood improvements, so there's tons of cool new stuff to explore.

If you're one who likes to tinker with Android, TWRP is the first thing you should install. It replaces your phone's stock recovery mode interface and adds over a dozen advanced features to your device—most notably, the ability to flash ZIPs that can modify practically every aspect of your operating system. It's certainly one of the most powerful tools available for Android, and there's simply nothing capable of replacing it.

If you need to do some hardcore multitasking on your Windows PC, a second monitor can go a long way towards getting things done. If you opt to "extend" your Windows desktop across a dual monitor setup, it's as if you have two computers side by side, with each display getting its own set of windows and programs that can be open simultaneously.

When you're sitting at your desk trying to get some work done, your Android device can be a big distraction. If a text comes in, you have to pick up your phone, unlock it, then respond with the clumsy touch screen keyboard—and by then, you've probably forgotten what you were doing on your computer.

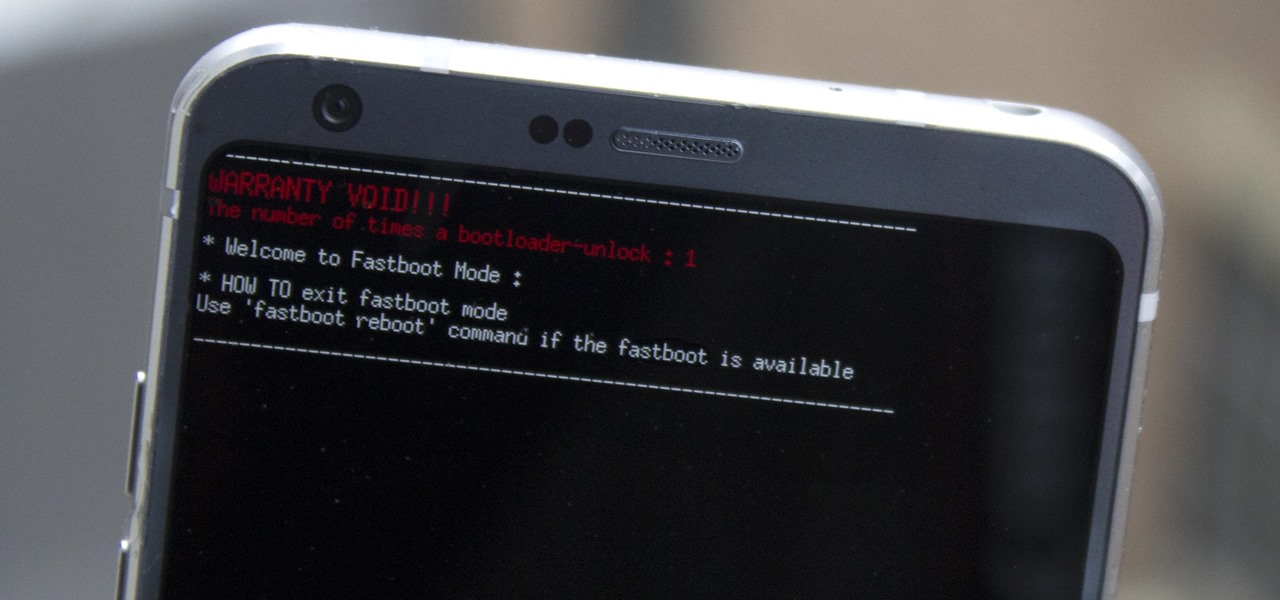
If your phone has an unlocked bootloader, you can use Fastboot commands to flash factory images. That may sound like a bunch of technical jargon, but when it comes down to it, this is the best method for updating a rooted device, fixing a bricked phone, reverting to stock, or even getting new Android updates before everyone else.

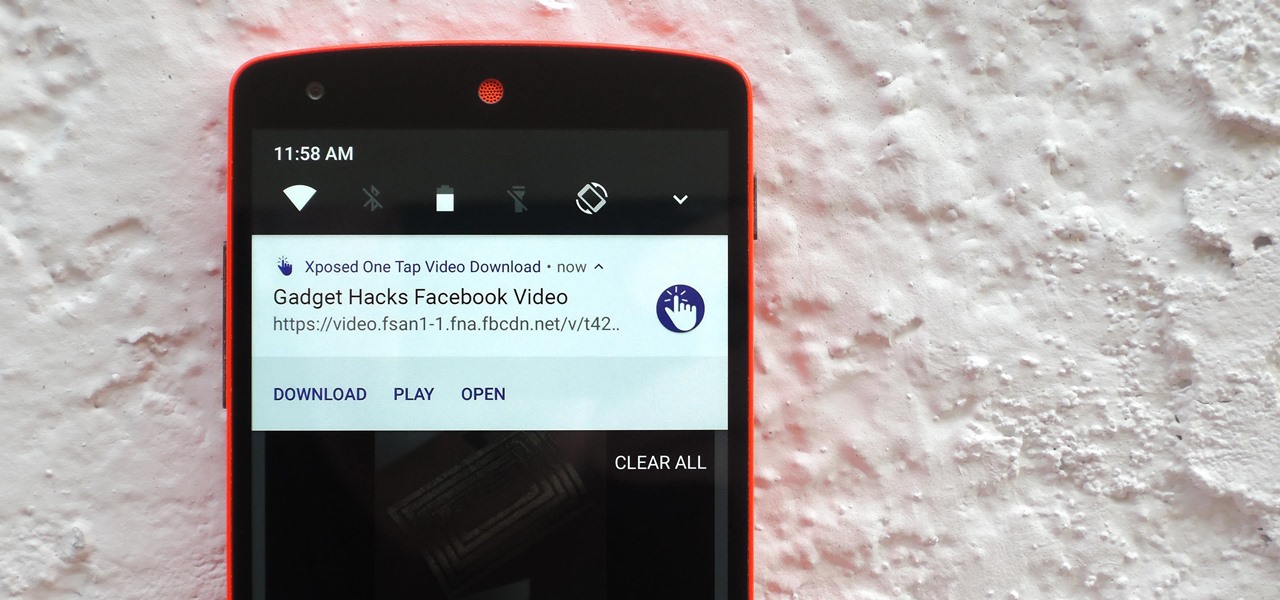
Most websites prevent you from saving embedded videos, but if you have the Xposed Framework installed on your Android device, a cool module from developer Ashish Bansal will now let you download almost any video. The way it works is simple—just start playing a video in your favorite web browser, then you'll see a notification that lets you download the source file in one tap.

Don't let the lack of owning a HoloLens stop you from joining in on the fun of creating software in this exciting new space. The HoloLens Emulator offers a solution for everyone that wants to explore Windows Holographic development.