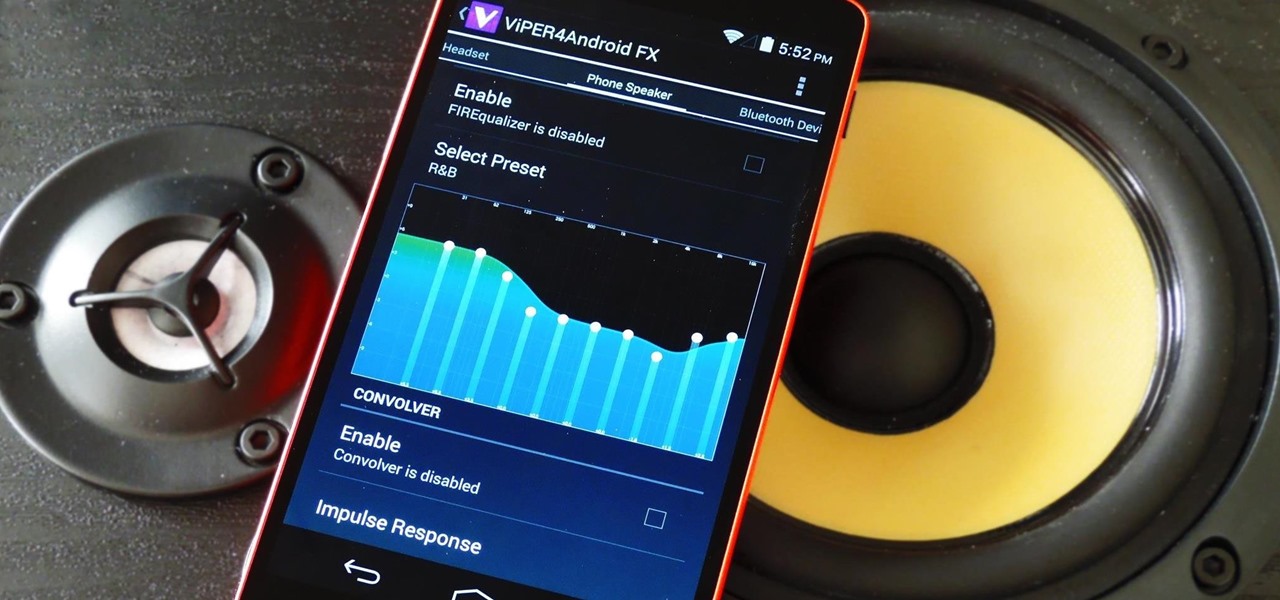
How To: Boost Audio Performance on Your Nexus 5
The Nexus line of devices consistently offer the most bang for your buck. It's why many of us purchased a Nexus 5—at a $350 entry price, it's half the cost of any other phone with similar specs.


The Nexus line of devices consistently offer the most bang for your buck. It's why many of us purchased a Nexus 5—at a $350 entry price, it's half the cost of any other phone with similar specs.

For those of you who've already gotten Beta Preview or Developer Preview access to Mac OS X 10.10 Yosemite, I highly recommend installing it on a separate partition on your hard drive.

Nokia's recent foray into the world of Android brought a plethora of goodies along with it. The Finnish smartphone manufacturer offers a slightly different take on our favorite mobile operating system, with customizations ranging from ringtones to its very own app store.

Whether you have the original Nexus 7, or the 2013 Nexus 7 tablet, rooting it will give you access to tomorrow's features, today.

The @DesignGears guys have been busy today, leaking an unofficial KitKat build (Android version 4.4.2) for the AT&T Samsung Galaxy Note 3. The latest is a peek into what the international variants are beginning to see, although this build is far from official. Still, if you want to give it a shot, I'll show you how to install it, but make sure to check out the details below the how-to to see what you can expect, good or bad.

There are much better things that can go in your iPhone's status bar besides an always-on indicator displaying what carrier you're shelling out money to every month. While it would be nice to get rid of the carrier name altogether at the top of the screen, an even better option is switching it out with something else to better personalize your iPhone.

WhatsApp is one of the most well-known and most utilized cross-platform chat applications available today. It's free for one year, and only $0.99 a year after, which is chump change when you realize there are no hidden costs like international charges. Basically, it creates an easy to use forum for you and your friends to chat, regardless if they're an Android or iPhone user.

The newest Android operating system, Android 4.4 KitKat, has been unleashed with the arrival of the Nexus 5, and soon to be rolled out to other Nexus devices and Google Play Edition smartphones any day now. Only problem is, the Samsung Galaxy S3 isn't getting 4.4 for a very long time. It doesn't even have 4.3 Jelly Bean yet.

This is going to be guides on the Bukkit plugin and Minecraft Mod. WorldEdit is an in-game world editor for Minecraft, supporting both single player and multiplayer. It is easy to use, extremely flexible, and actively developed.

In photography, creating a double or multiple exposure photo involves combining two different images to make one single image. This technique has been used in film photography by exposing a piece of film twice to two different images. The second image becomes superimposed onto the first image, creating various effects that may mirror one another or seem ghostly.

Using a Phillips head screwdriver remove the screw under the handle in the back of your iMac. Remove the screws outlined in the picture below. Remove screws 1 and 2 with a standard Phillips head screwdriver. Screws 3 and 4 use a standard flat head screwdriver. After removing the screws, gently pull out all of the plugs. Next holding the clear handle just below the bar code, pull out the section of the iMac.

In this series of home improvement videos, expert engineer and licensed home inspector George A. Finn III guides you through the entire process of installing a new hand-held shower head. He shows you what tools you’ll need to get started and offers tips on planning the installation process. He demonstrates how to remove the old shower head, tape the pipe for proper threading, and then shows you the correct procedure for installing the hand-held showerhead, connecting the hose, and how to test...

At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit.

Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added.

Wireless charging is pretty much ubiquitous among modern iPhones and Android smartphones, but the technology has brought a lot of clutter with it.

We already know that the US Army will be using its modified HoloLens 2 for special missions, and major businesses are deploying the augmented reality device for enterprise use cases.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?
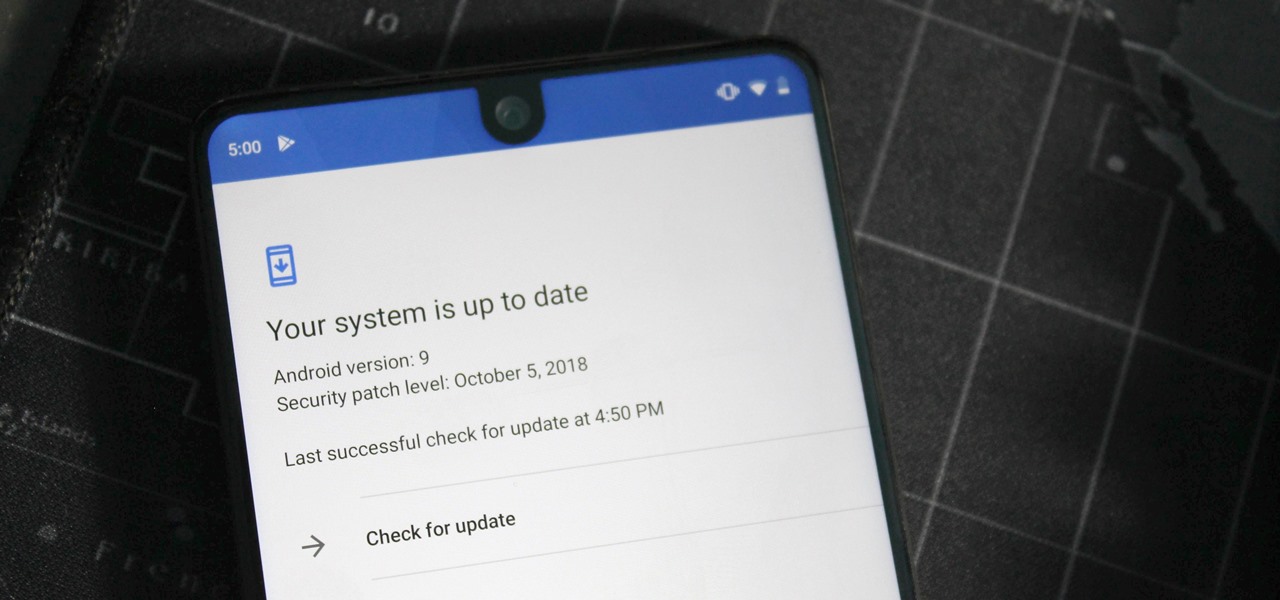
One of the issues with rooting your device is the inability to update your phone via OTA. Any security patches or software updates pushed out by the OEM are lost because your bootloader is unlocked. However, you still can update your device, it just a take a bit more effort.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.
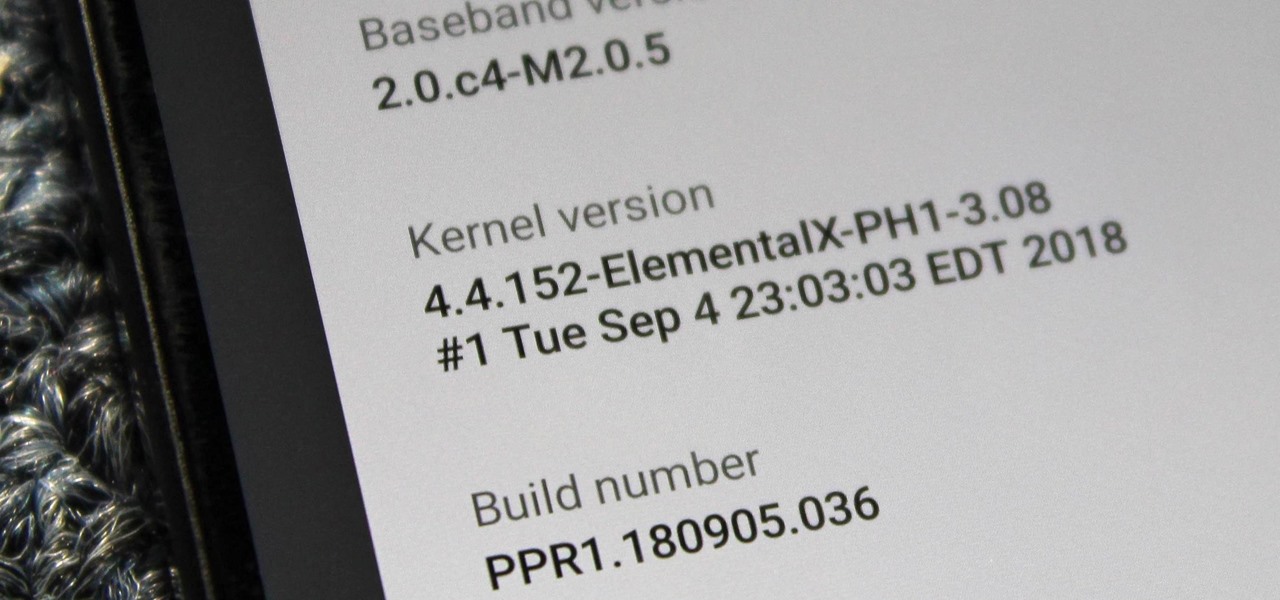
When you unlock the bootloader on your Essential PH-1, you open your device to a host of new possible tweaks. One popular modification is a custom kernel, which can not only speed up your phone, but give you new features that wouldn't be possible otherwise.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.
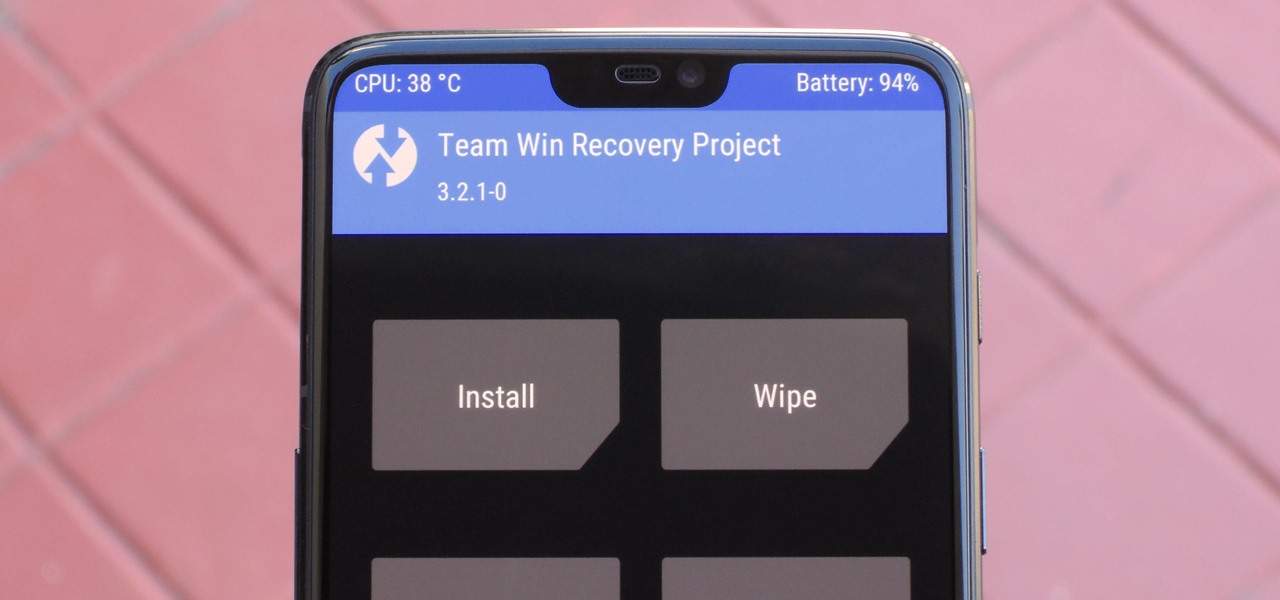
When it comes to modding Android, there's no better tool than Team Win's TWRP custom recovery. You can use it to root your phone, flash mods like Magisk or Xposed, and even replace the entire operating system with a custom ROM like LineageOS — honestly, there's not much this utility can't do.
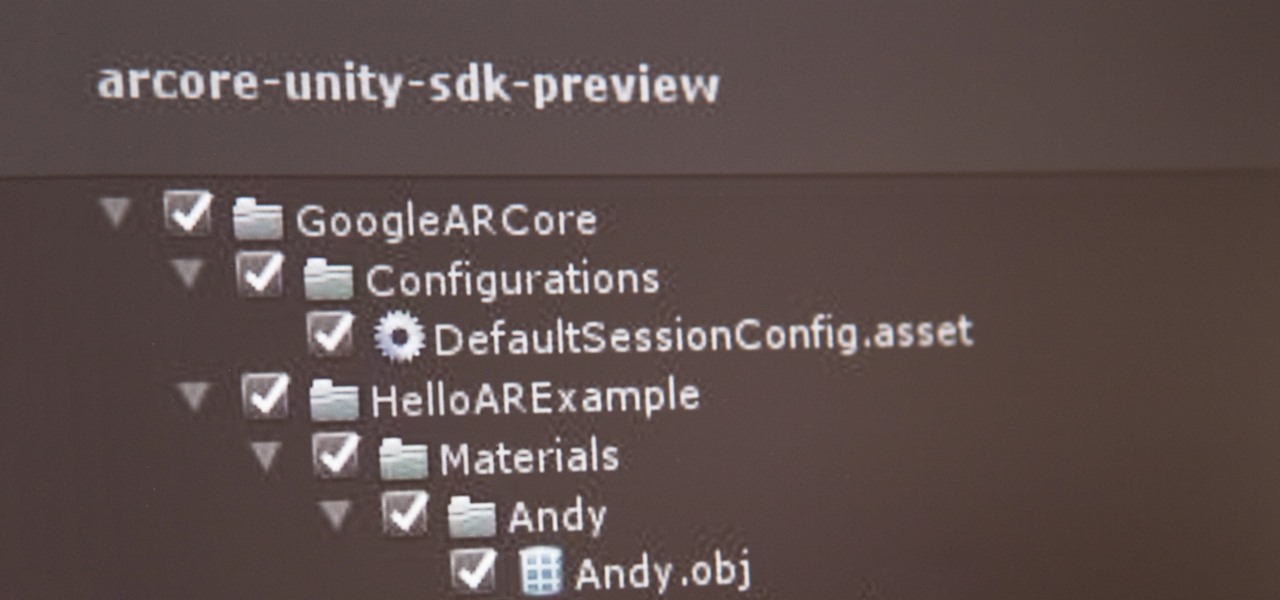
If you've contemplated what's possible with augmented reality on mobile devices, and your interest has been piqued enough to start building your own Android-based AR app, then this is a great place to to acquire the basic beginner skills to complete it. Once we get everything installed, we'll create a simple project that allows us to detect surfaces and place custom objects on those surfaces.

For years, PuTTy has reigned supreme as the way to establish a Secure Shell (SSH) connection. However, those days are numbered with the addition of the OpenSSH server and client in the Windows 10 Fall Creators Update, which brings Windows up to par with macOS and Linux's ability to use SSH natively.

With the V30, LG has really delivered an amazing smartphone that hits all the major features consumers want. Amazing camera, beautiful edge-to-edge display, great battery life, water resistance, and smooth performance — there isn't much not to like about the LG V30. Unfortunately, it does suffer from heavy bloatware thanks to the carriers. The good thing is, unlike in the past, you are not stuck with it.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

The OnePlus 5 had been in the hands of the public for a meager twenty hours before developers on XDA released a custom recovery image for it, and the 5T had a similar trajectory. The installation process is simple enough, but it can be somewhat confusing if you're new to modding Android.

Pot, weed, bud, herb – whatever you want to call it, the green earthy treat makes everything way more fun. Now that marijuana is legal to some extent in more than half of all US states, we thought it was high time to showcase some apps that enhance your experience with the controversial pastime known as rolling up.
Google has already issued a few updates to Android 7.0 Nougat. There aren't many headlining features, as these minor updates are mostly bug fixes and performance improvements. But there's a few security enhancements as well, so staying up-to-date with the latest patches is important for a number of reasons.

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

Yes, screen savers are fun to look at for a few seconds, but those animations actually used to serve a purpose beyond simple entertainment.

Welcome back, my hacker apprentices! A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial, materialistic society and wants to make a better world. I believe we will see a lot more of this actor in coming years.

When the Chromecast first came out about a year ago, developers were quick to find a way to root the streaming device. Google was almost as fast, however, in updating the Chromecast's firmware to close the loophole that this method used.

As the largest wireless service providers in the United States, AT&T and Verizon Wireless carry some serious clout. Sadly, they use some of this power to heavily modify the Android phones that they offer.

You send out a lot of emails, but probably get very few responses. How can you be sure those emails are even opened?

With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

Welcome back, my newbie hackers! Recently, I "upgraded" to Kali as my hacking platform, despite my preference for BackTrack. I did this reluctantly, primarily because new readers here could no longer download BackTrack from their site. I want to point out here that we all must keep in mind that with any software—or for that matter, any product—that is newer is not necessarily better.