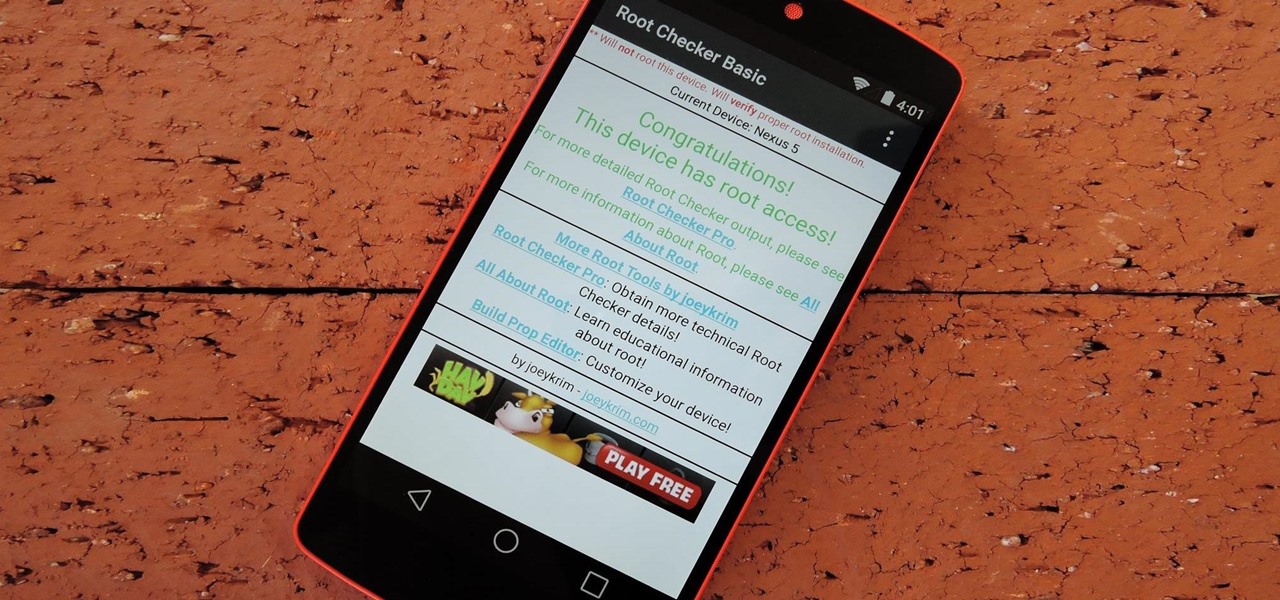
While the preview images for Android's upcoming "L" release just came out yesterday, the new firmware has already been rooted, as is standard with its openness. So if you were feeling reluctant to try Android L because it didn't support existing root methods, then you might want to reconsider.

Apple is set to release its latest operating system for iPad, iPhone, and iPod touch this fall, and if you haven't noticed yet from our iOS 7 softModder guides, it's going to be pretty slick.

Apple released iOS 13.0 on Sept. 19 and announced on the same day the release of iOS 13.1 on Sept. 30. But that deadline was pushed up to Sept. 24, and that's why we have 13.1 just five days after 13.0. But that's good news since we don't have to wait any longer for some of the features promised in iOS 13 that didn't make the first cut.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

You watched the live stream, pored over the specs, and are now super excited for the Google Pixel 4. But specs don't tell you everything. After using the Pixel 4 XL for over a week now, we've found several things you wouldn't know without getting your hands on the phone.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

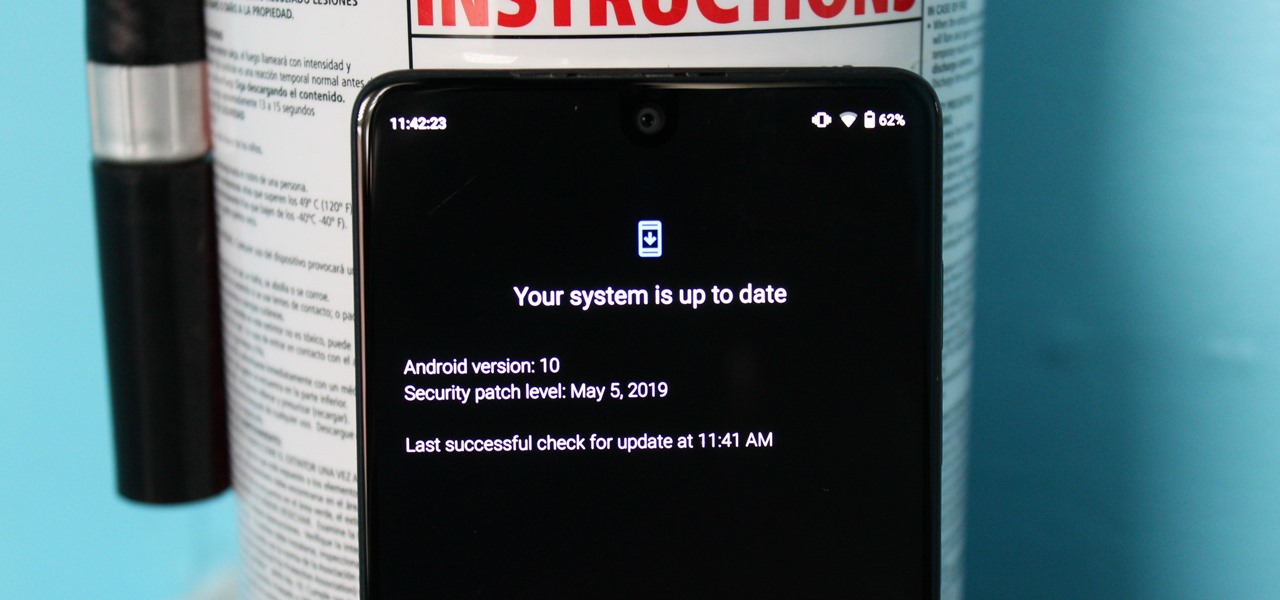
Like last year's beta release of Android Pie, Google has allowed the Android Q Developer Previews to support some non-Pixel devices. Announced at Google I/O 2019, there are 15 non-Pixel smartphones eligible for the Android 10 Beta, including 2017's Essential PH-1.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

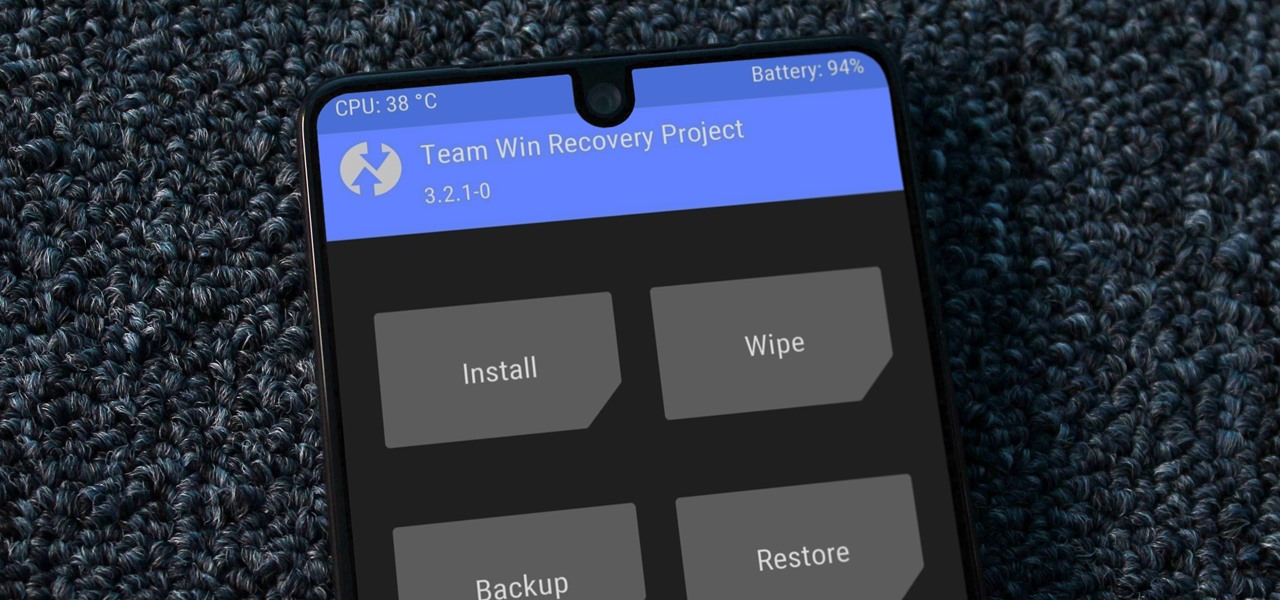
There once was a time in the Android rooting scene where we couldn't rely on using a custom recovery for all of our modding needs. Manual file flashing was very popular in the early days of Android before custom recoveries started taking over. With the rise of TWRP, it seemed like there was almost no need for manual file flashers; however, they appear to be making a welcomed return in a big way.

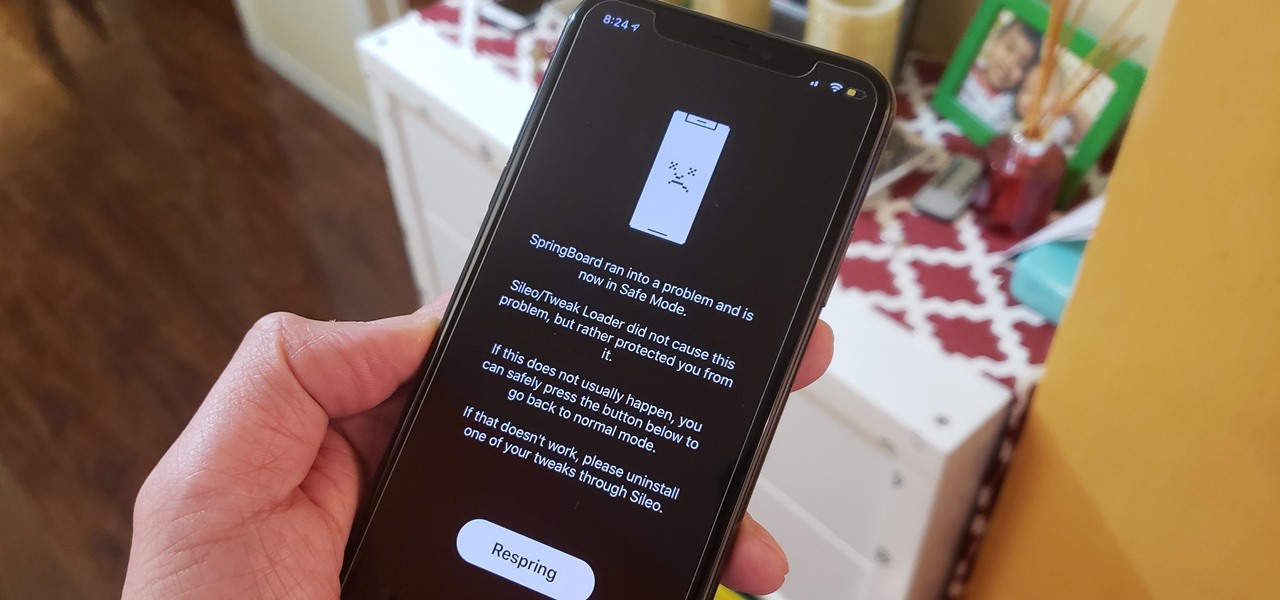
If you're familiar with jailbreaking, you're well aware of the fragmented nature of downloading tweaks. Unlike the iOS App Store, which contains about two million apps of varying categories, installing jailbroken packages often requires you to first install a separate repo into either Cydia or its replacement Sileo, as many of these tweaks aren't available outright.

Removing unwanted apps from your iPhone is a straightforward affair — long-press an app's icon, then hit the delete button once it appears. Unfortunately, the same can't be said when it comes to uninstalling tweaks from a jailbroken iPhone.

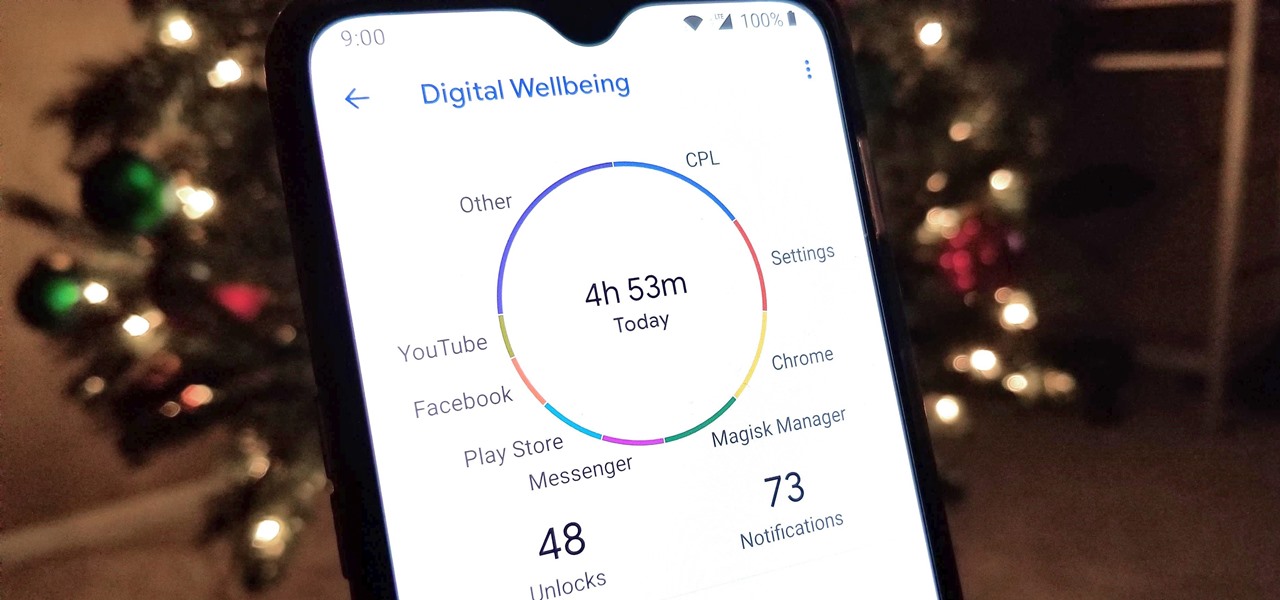
Living in this age of smartphones and always being connected can sometimes have us getting carried away with our devices. Whether it's an addiction to our phone or if we just feel like cutting back on some daily screen time, there's a great tool that can help with that — Google's official Digital Wellbeing app puts you in control by laying out all the stats you need to help curb your daily smartphone habits.

With the recent launch of the OnePlus 6T, the company continues to impress us with some of the best phones when it comes to the rooting and modding. OnePlus has made it easy enough to get up and running with the rooting process as fast as possible. The OnePlus devices follow the same core principles Google uses for their Pixels, which is excellent news for both the user and the development side of things.

For modders, there are few tools more important than TWRP. TeamWin's custom recovery makes flashing mods like Magisk, Xposed, and custom ROMs incredibly easy, and it lets you root your phone at the press of a button. On top of that, it can make complete backups of your phone in case you mess up. That's why, for Essential users, this should be the first mod you add.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

There are over 3 million apps in the Google Play Store, all optimized for the small screen in your hands. While that number sounds staggering, there are still many online tools and websites that require you to use a mobile browser since app development is expensive. However, that's where Progressive Web Apps (PWAs) come into play, a cost-effective way to turn websites into mobile apps.

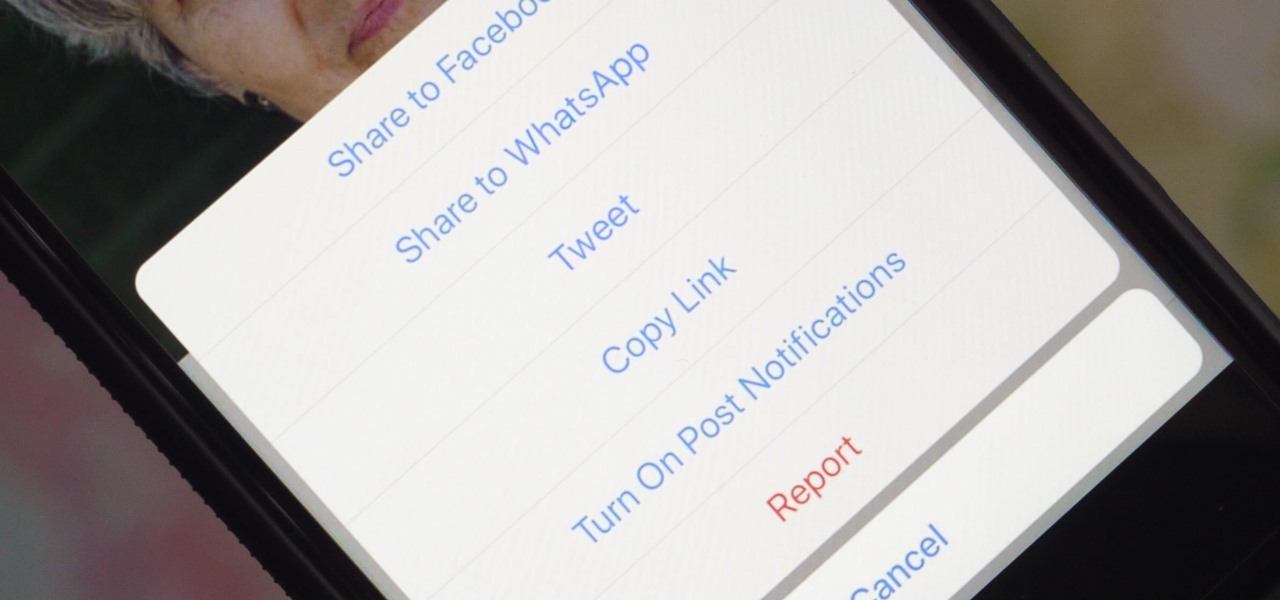
WhatsApp is a great app to keep in touch with friends and family across phone brands and countries, but sharing a post on Instagram hasn't always been as easy as it should have been considering Facebook owns both companies. Now, whether you have Android or iOS, all it takes is a few taps.

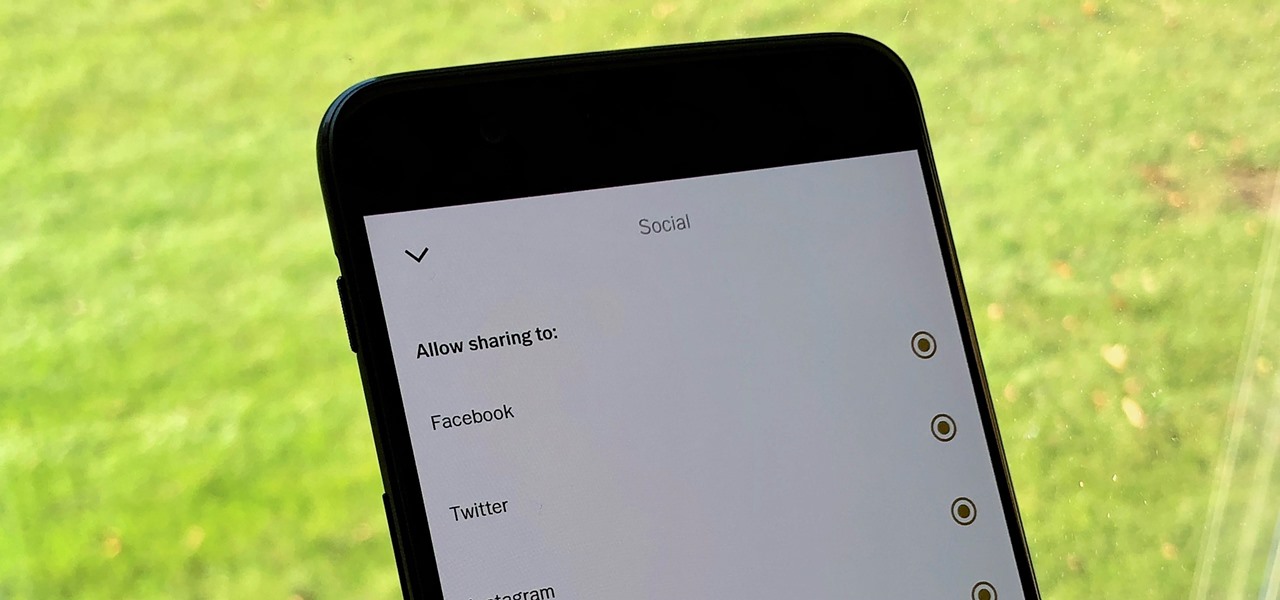
In this day and age, publishing content to one social media account just doesn't cut it. VSCO, Facebook, Twitter, Instagram ... you need to be active on all. And if you prefer editing and posting all of your photos on VSCO, you need a way to share those images with your other accounts.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

On the surface, iOS 10.2 might look the same as iOS 10.3, but there's one big difference between the two versions: iOS 10.2 can now be jailbroken! Jailbreaking your iPhone means gaining access to thousands of tweaks and mods which greatly enhance the iOS experience, so this is great news for the power users out there.

It couldn't be any easier to remove apps from your iPhone — simply do a long-press on the app's icon, then tap on the delete button once it pops up. However, when it comes to removing unwanted tweaks and apps from a jailbroken iPhone, the process is often a little more involved.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

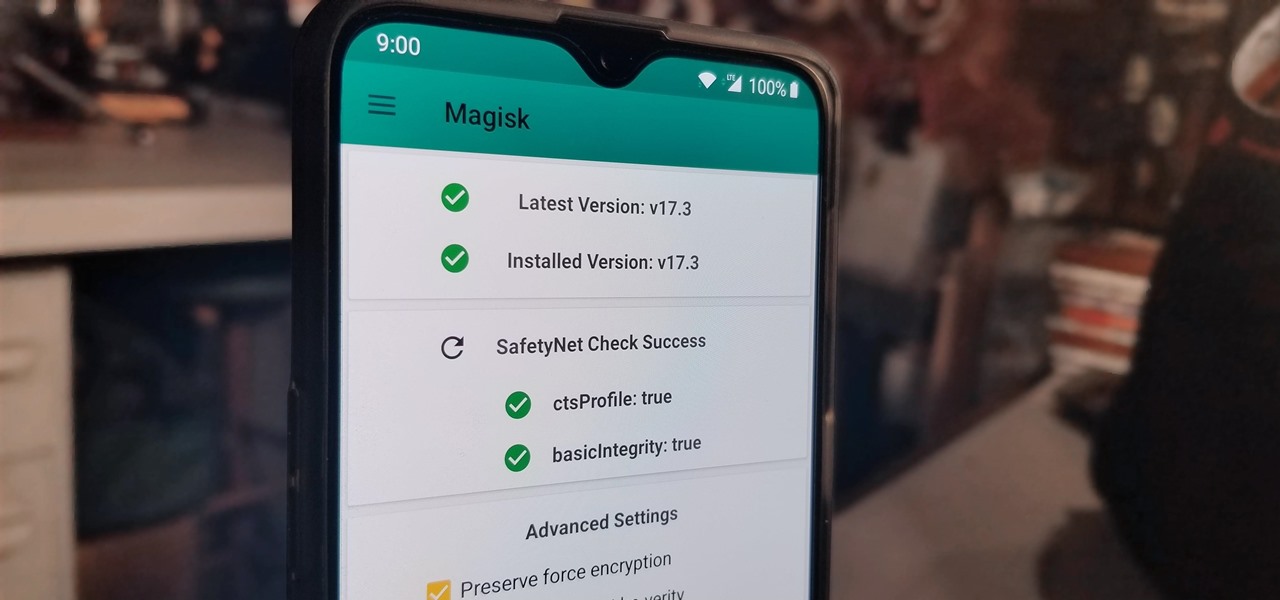
Because of Android's new SafetyNet system, certain apps can now block rooted users or prevent you from accessing them altogether — but at least for now, there are still ways around these restrictions.

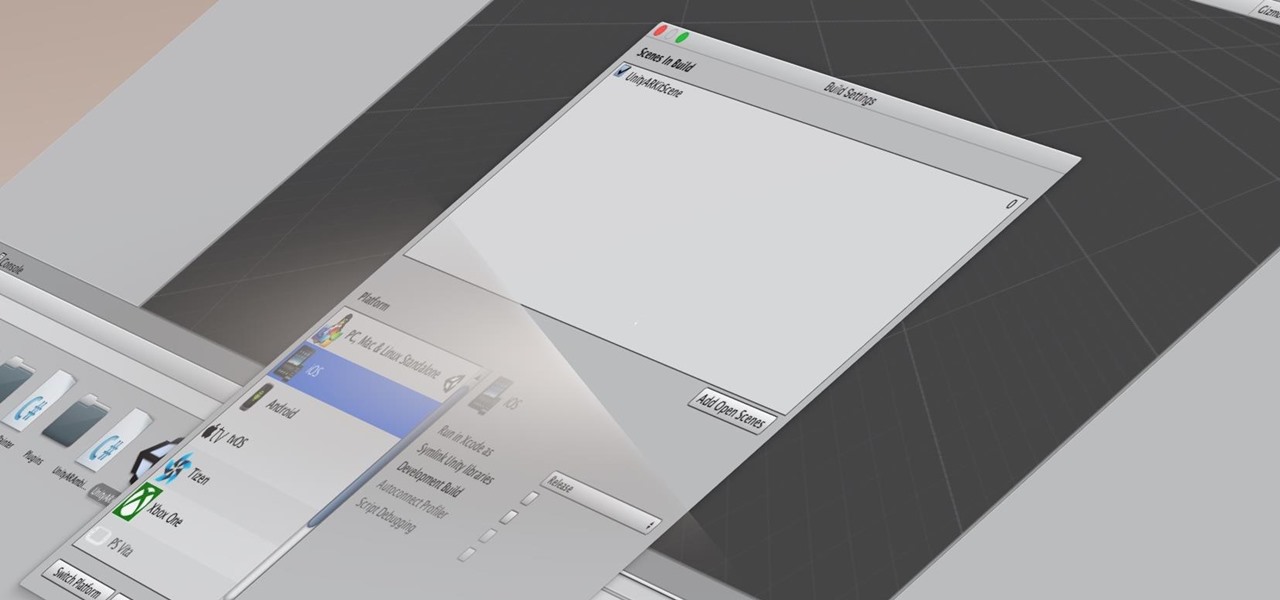
Many developers, myself included, use Unity for 3D application development as well as making games. There are many that mistakenly believe Unity to be a game engine. And that, of course, is how it started. But we now live in a world where our applications have a new level of depth.

Kik is an extremely popular messaging app, but it has a few annoying features that we all just sort of put up with. You can't turn off read receipts, nor can you hide when you're typing, and the photos you take with Kik's camera show up differently than ones you send from your gallery app. At least a couple of these features should be subject to change, but they aren't — well, not without some tinkering.

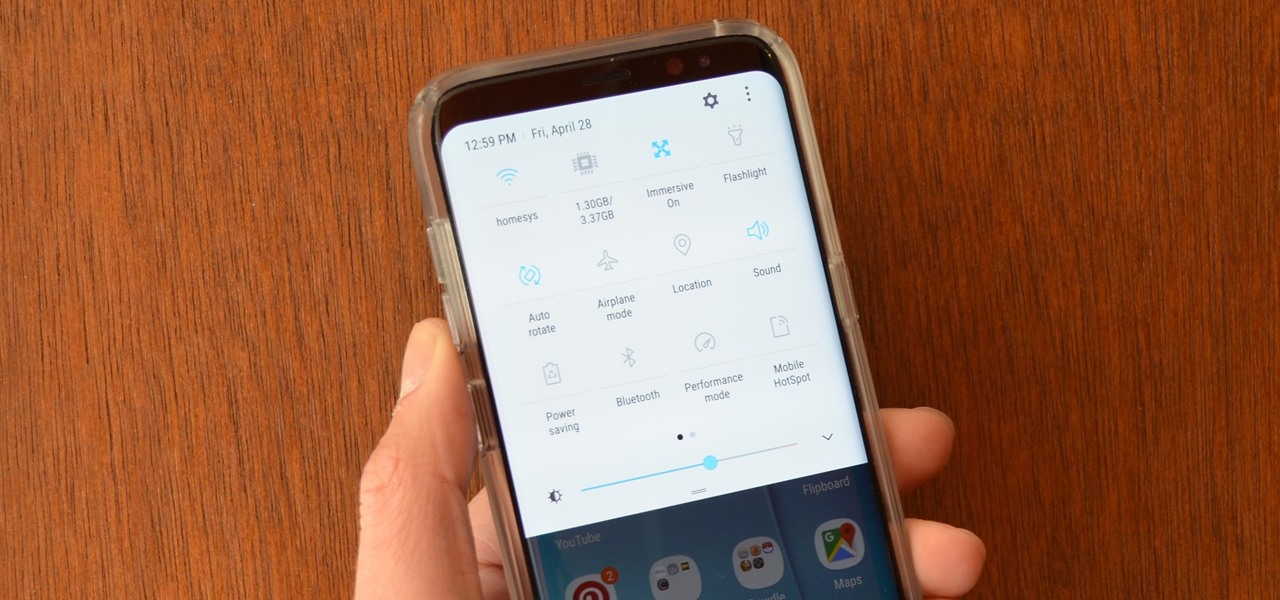
Up until now, enabling full-time Immersive Mode on an Android device has been a tedious task which required you to run individual ADB commands each time you wanted to toggle it on or off. This was a shame, too, since Immersive Mode helps reclaim lots of screen real estate by auto-hiding your navigation and status bars.

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

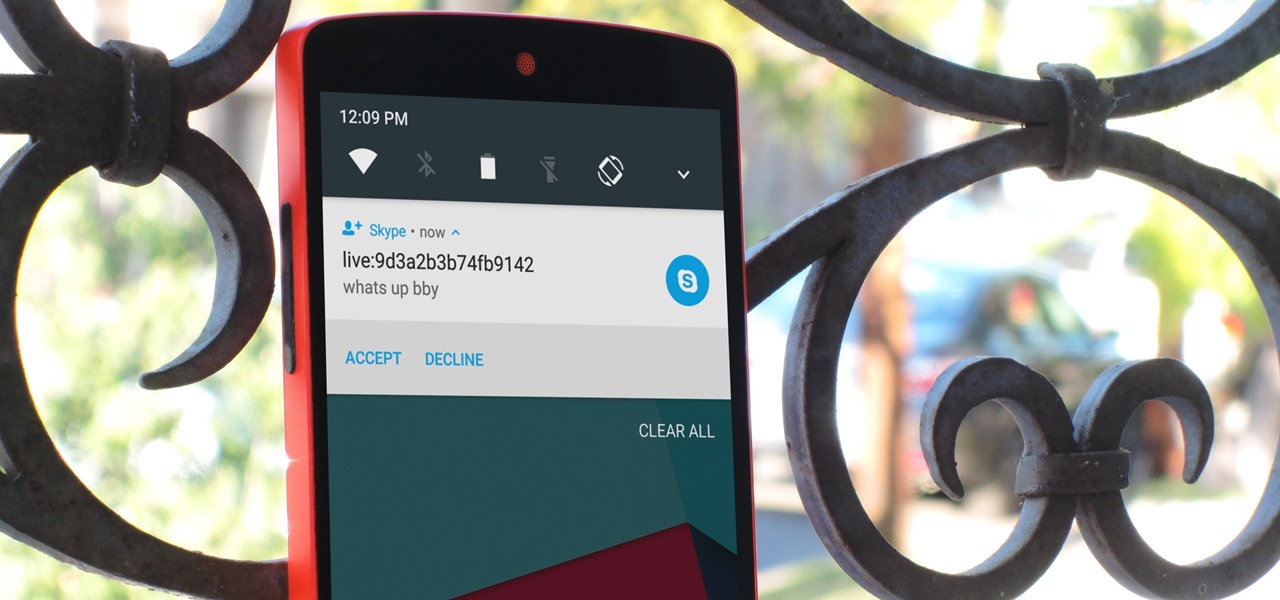
Skype is one of the most popular messaging and video chat services for a good reason—it's packed to the brim with tons of cool features. But one bit of functionality that Microsoft left out is the ability to block friend requests from people that aren't in your contacts, which can lead to a lot of unwanted notifications from spammers and bots.

When it comes to modding an Android device, a custom kernel can take you farther than almost anything else. Most offer the ability to overclock your processor for performance gains, change your CPU governor, or even under-volt to increase battery life, among other features.

We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs.

We recently covered an app called Touch Controls for YouTube that allows you to swipe up or down on any YouTube video to quickly adjust volume levels or brightness. As awesome as that app is, commenters here and on our YouTube channel thought it was lacking one big feature—the ability to seek forward or backward in the video by swiping the screen.

By default, the Play Store app on Android is set to automatically update your apps in the background. This definitely makes it easy to ensure that you're always running the latest versions, but it does come with some downsides.

Ever since developer bponury created his TouchControl app for the Galaxy Nexus back in 2011, manufacturers and modders alike have been racing to re-implement the "Double-tap-to-wake" functionality it brought to the table. We've seen LG do it with their "Knock On" feature, we've seen Motorola put a twist on it with "Active Display," and we've even seen Google implement the feature in their Nexus 9 tablet.

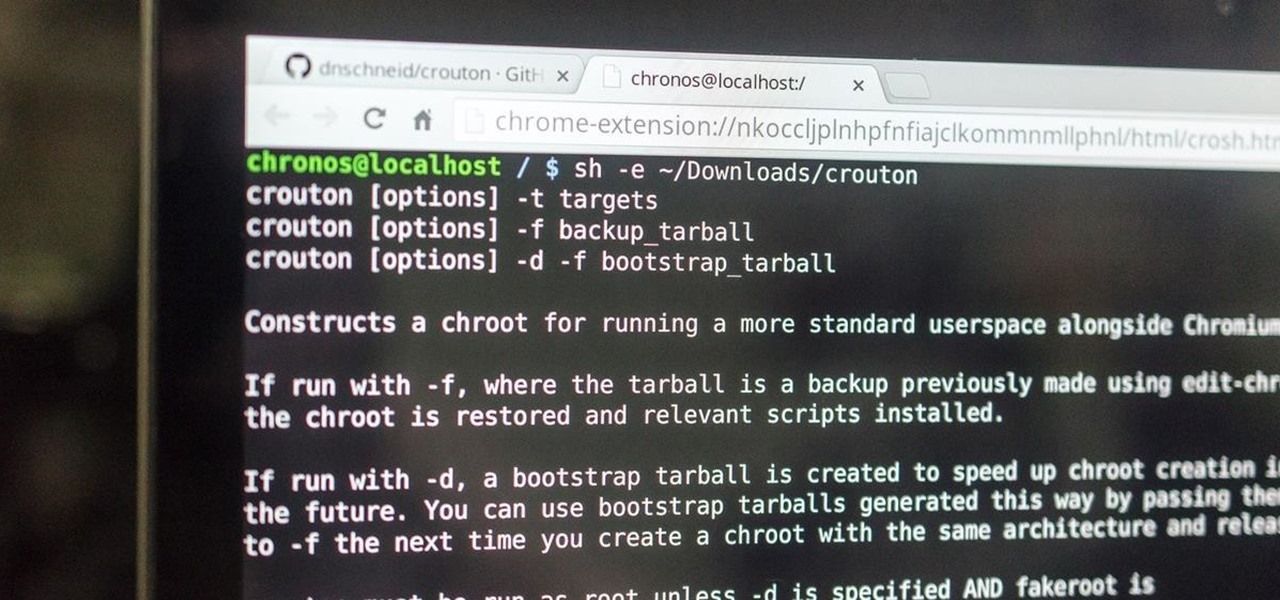
This is my first how-to for this site so feel free to let me know if I can somehow improve! Inspired by the great Jailbroken iDevice and Rooted Android PenTesting tutorials I decided to share how I use my Toshiba Chromebook 2 with Kali Sana.

If you exceed your monthly mobile data limit, your cell phone bill can skyrocket pretty quickly. This is why a lot of people vigilantly monitor internet usage and even uninstall apps that use too much background data.

Android Marshmallow was recently released, and as we've grown to expect, a root method was quickly made available to devices running the brand new operating system. Legendary root developer Chainfire has stated that he's working his way towards retiring from the scene, but he still had enough left in the tank to quickly publish an update to his popular SuperSU root method.

There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various other categories where developers compete against one another to garner the largest user base.
Welcome back Hackers\Newbies!