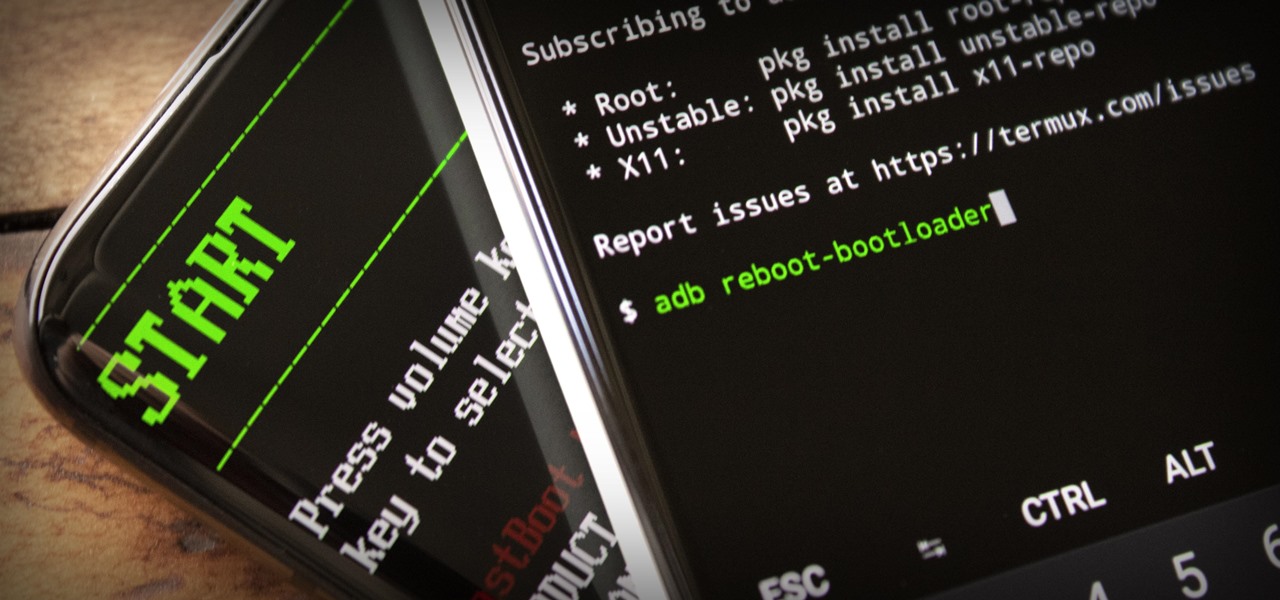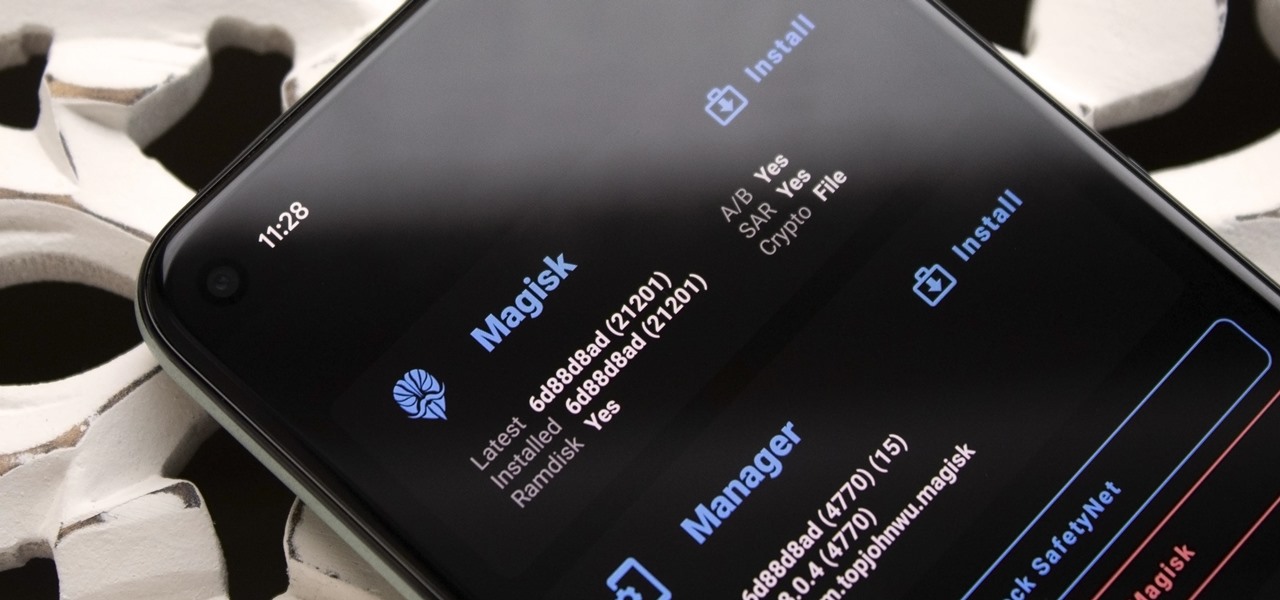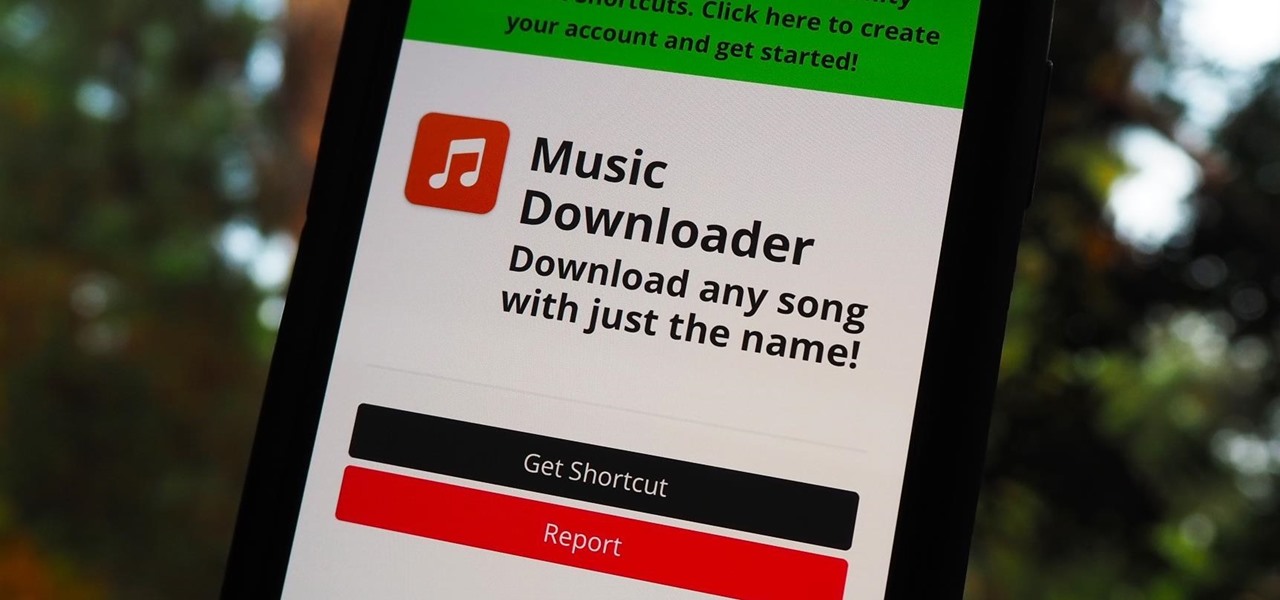
Facebook Home was just released in the Google Play Store a couple days ago, and for those of you eagerly waiting to get it on your Nexus 7, you'll unfortunately be stuck with this message: The new Facebook Home launcher app is blocked on the Nexus 7, because Facebook only released it for a few select Android phones. Home for tablets probably won't appear for months, but that's okay, because you don't have to wait that long! In this article, I'm going to show you how to get Facebook Home insta...

I check my email every morning as part of my daily routine (usually while I'm brushing my teeth, if you really want to know). As a result, there have been many, many times where I've read an email on my phone or computer and forgotten to respond in a timely fashion.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

I had my wallet stolen a few months ago, and I knew I would never see it again. My biggest gripe was not the credit cards in there, since they're easily cancelled, but the gift cards. I had some pretty good gift cards in there, and there's no way to get those back.

If you have a Barnes & Noble Nook, you may be surprised to find that your eReader can do a lot more than just display ebooks, which makes it a great alternative to those more expensive all-in-one tablets that do everything (seriously, everything). If you want to get more bang for your buck, here are a few ways you can hack your own Nook.

Mountain Lion (OS X 10.8) is out today, available in the Mac App Store for just $20. Unfortunately, installing Mountain Lion requires that you already have a Mac running Snow Leopard (OS X 10.6) or Lion (OS X 10.7). If you're currently running a Leopard system, you're out of luck, and need to pay $29 to upgrade to Snow Leopard, and then an additional $20 to upgrade again to Mountain Lion. That sounds like way to much trouble to me. But why exactly is Leopard incompatible? Turns out it's not—m...

Apple just released the fourth public beta for iOS 14 today, Thursday, Aug. 6. This update comes two days after the company released iOS 14 developer beta 4, 15 days after Apple seeded developers the third dev beta, and two weeks after the release of public beta 3.

Apple's TV app for iPhone didn't get any new features with the iOS 17.1 software update, but iOS 17.2 is a totally different story. There are big changes to playback controls, your channels, store content, and more.

ADB and Fastboot are powerful tools that have always required a computer. But with the right setup, you can now send commands to a phone using another phone.

Okay, so you rooted your Android phone .... now what? There are a few ducks you need to get into a row, like backing up your stock boot image, getting SafetyNet sorted, and improving security with biometrics. But there are also awesome root mods waiting for you — just don't get ahead of yourself.

Music streaming services like Apple Music, Spotify, and YouTube Music make it easy to find and play your favorite artists and albums on your iPhone — but they cost upward of $14.99 per month. If you're more into listening to downloaded music, a shortcut can help you find free music online that you can get and playback in almost any media player of your choosing.

Don't be too disappointed if you don't have the spiffy new Kindle Touch, there is an up side. The benefit to owning the older (duller) models is that the firmware remains the same throughought generations, so the hacks retain their usefulness. This has given the modding community for Kindle a bunch of time to flourish, with tons of great code, hacks and homebrew. Today's Null Byte is going to show you how you can root, and then remove the crappy original screensavers that come installed on th...

If you're painting your auto yourself, you might need a little help if you've never done it before, especially when it comes to the primer sealer and apply your first base coat of paint. This video will show you how to do just that. An OEM fender was already prepped by sanding with 500 grit sandpaper on a DA with a soft pad and surfing the edges with a maroon scuff pad.

In this tutorial, learn how to install superstar fonts like those used for Hannah Montana and High School Musical in Windows XP.

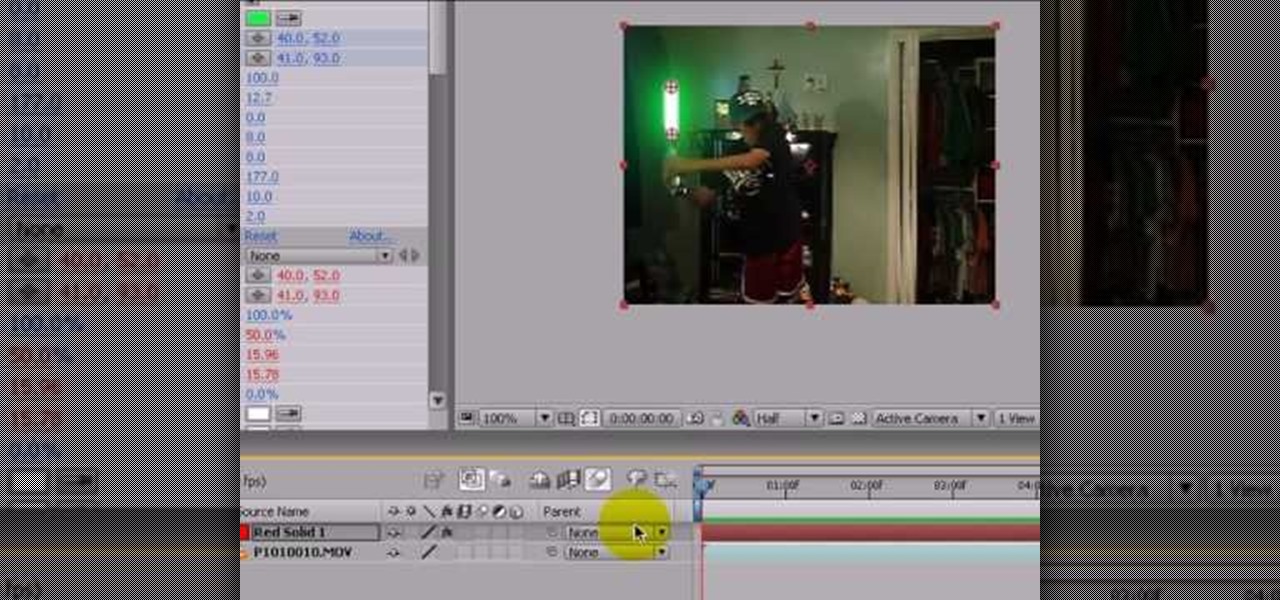
Did you ever want to know how to create Star Wars style lightsaber effects for your own home videos? Youtube user Comphelper225 has a way make this little bit of movie magic come to life using Adobe After Effects. Once you have a video of yourself or a friend swinging a base for your sword, the next step is to download Andrew Kramer's lightsaber presets from the Video Copilot website. Once it's installed, open up your video in After Effects to begin. Within the program, click Layer, New, and ...

Wartex8 demonstrates how to use remote desktop in Windows XP. Remote Desktop is a useful utility that you can use to control another computer and its applications.The necessary steps that are adopted to activate remote desktop are:1) Right click on my computer icon (either the icon on the desktop or the one on the start menu list) and select properties, and a new dialog box called system properties will pop up on the window.2) In the System Properties, select the computer name tab and write d...

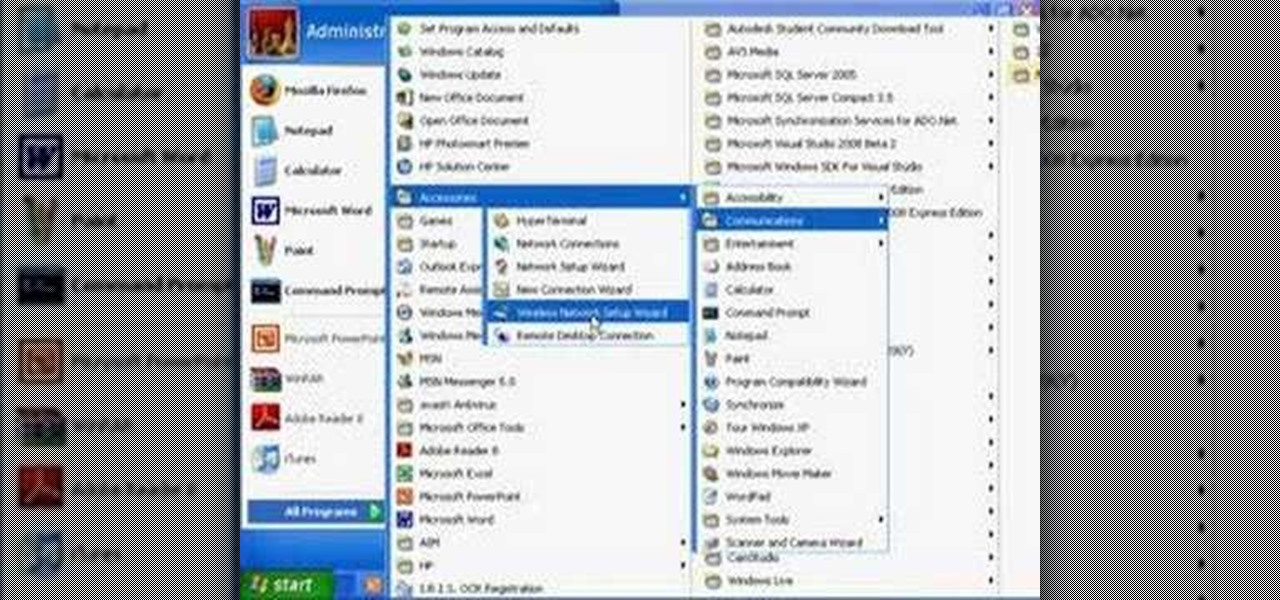
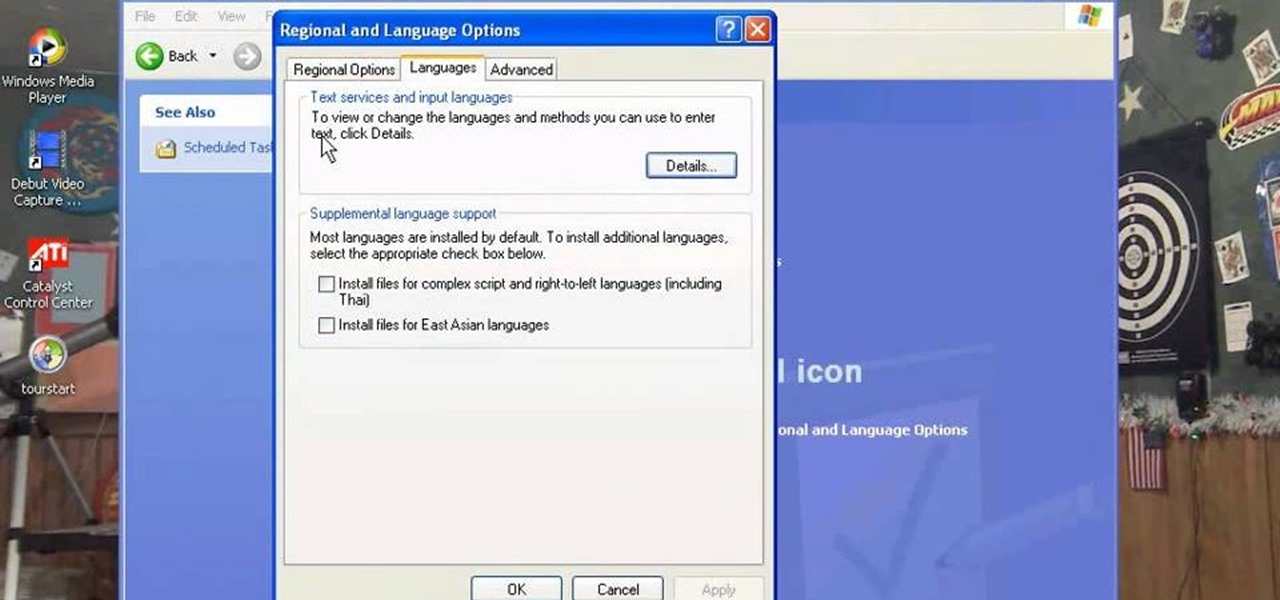
There are a number of items that you will have to use your mouse and click onto in the process of changing your clock, language and religion in Windows XP. Click START-CONTROL PANEL-DATE/TIME/REGIONAL OPTIONS. This will get you to the window that allows you to change any of these settings. To change the date or the time click on Date/Time icon. Here is displayed the current time. If you change the time here, you will have to click the Apply button to enable the new setting. Set to the correct...

This video is about downloading videos in Firefox. Firefox is a web browser, but it will be used rather than Internet Explorer because Firefox allows you to install plug ins. Go to the tools menu and click "add-ons". Download helper is the add on we will select. Click "get extension". A web page opens. In the search box, choose "search for add-ons". Add to Foxfire. Install now. Restart to complete installation. On the toolbar you will see three rotating bars which will let you know the add on...

Still got stock? Many factory installed exhaust systems not only sound anemic, they actually are because they scrub power. The designers who are given the task of producing these pipes are often handcuffed by several different requirements that add up to one big compromise. Exhaust engineers are required to build systems that are quiet and that meet certain types of emission standards, but not all of the design concerns are driven by government regulations. Some are based on a perception of w...

Ceiling light fixtures can be installed easily with help from an expert. In this free video series learn how to install ceiling light fixtures.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone are all it takes to start listening in on radio conversations happening around you.

Samsung isn't known for its timely rollout of major Android updates, and Android 9.0 Pie won't be an exception. If we go by their Oreo update timeline, we can expect Android Pie to officially touch down for the Galaxy S9 and S9+ sometime around November, with the final version rolling out the around the first quarter of 2019. But a leaked version of the beta has already hit the internet.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Apple officially released iOS 12 to everyone on Sept. 17, and while the new iPhone XR, XS, and XS Max will come with the software by default, you have a choice on whether or not to update your current iPhone model from iOS 11. There are a lot of tempting features to want to update right away, but there are also some compelling reasons to wait it out and install at a later time.

If you want the ability to play YouTube videos in the background as you multitask on your iPhone, you'll have to shell out $11.99 a month for the privilege of doing so with YouTube Premium. Not all of us can afford nor justify such an expense, but if your iPhone is jailbroken, you can get your hands on this sought-after feature — and much more — without spending a dime.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

To please those of us who love to mod and root our Androids, OnePlus has made both the OnePlus 5 and 5T relatively easy to customize — so much so that the 5T topped our list for the best phones for rooting. Unfortunately, unlocking the bootloader and using root to modify the firmware on your OnePlus 5 or 5T makes it hard to update to a new firmware such as Oreo when compared to stock.

Gboard is one of the best third-party keyboards available for iPhones, but you probably don't know everything you need to know about it to become a real Gboard pro and stop using Apple's stock keyboard for good.