With the plethora of programming that we promote at Null Byte, I figured a lot of you newbies that stop by IRC will need a big boost in the right direction to make your dive into programming a lot easier. A hot question that has been thrown around in IRC a lot when making the initial dive is, "How do I write code?". People who do not know much about computers can't understand how code is written. Code that we write here is usually scripted and written in Python, so we will use it as our examp...

This is the Windows OS counterpart to my tutorial on how to burn the new XDG3 formatted games on Xbox 360. Microsoft invented a new disc format system to trump piracy, it's called XDG3. XDG3's standard is to burn a whole extra gigabyte of data to the disc, to allow more content, but more importantly for stopping piracy. This extra gigabyte of data makes it impossible to burn or rip a game the traditional way. So how on earth can we burn our fully-legal back-ups that we should rightfully be ab...

File recovery on Linux is a bit different than Windows. It requires different software than the Windows counterparts because every OS has their own file system. Windows uses NTFS, or FAT file systems, while on the other hand, Linux uses ext-based file systems. I personally use ext4 file system because it's the latest and greatest ext-journaling system and supports a large level of directory recursion and file sizes, but most installations still use ext2 or ext3. When files are deleted from a ...

Welcome to another Community Byte announcement! In the past two sessions, we have coded an IRC bot in Python capable of issuing commands. Since it can issue commands and most of you are new to programming, that project will stay idle for a while. Other commands such as voice and half-op can be easily hacked in via common sense, even if you weren't there for that session.

This morning, the Official Google Blog and Chrome Blog revealed the new tab page, which lets you flip between your installed apps and your most visited web sites. To take a look at how it works, check out the video below. The Chrome Web Store also received a facelift. It's now a lot bigger and brighter, with infinite scrolling instead of pagination. Adding new apps and extensions is a snap; all you have to do is select your app or extension, read more about it, and then click on the +Add to C...

Beginning this week, Null Byte will be hosting a new feature called Community Byte, a weekly coding and hacking session held in the Null Byte IRC. This is a chance for our community to do something fun, and make something awesome together!

Sharing a laptop's wireless Internet connection with other computers connected to its Ethernet port is a great skill to know. It can be good for a number of reasons; Your computer may not have proper hardware to have a standard setup, or you may have an awkward network topology where sharing your wireless Internet via Ethernet would just be a better option.

The Google +1 button isn't as ubiquitous as the Facebook Like button, but it's getting there. Google's working hard on improving its functionality, and recently we've seen some innovative features added. The +1 button now appears on over one million sites, and you can do more with it than you could initially.

There are over 250,000 apps in the Android Market, ranging from free productivity programs to a ridiculous $200 for a vuvuzela horn effect. But chances are you don't have the vuvuzela app on your Android smartphones right now, but you are likely to have one of the ten most popular apps in the Android Market.

The whole world is connected to the Internet, which means bank for advertising companies who track your every move online. Most of the content you see on the web is free, and that's because of advertisements. If there were no ads, none of us would be addicted to the Internet because none of us would be able to afford it.

With give or take 250 million cars in America, odds are most city dwellers waste time hunting for parking spots. And while a smartphone app can't make free parking spots magically appear, it can aid in the searching process.

Are you one of countless Facebook users who find the classic Thumbs Up symbol tiresomely sycophantic? You're not alone. Back in August of 2010, the widespread addition of an "official" Thumbs Down symbol to Facebook pages quickly revealed itself to be a scam, but only after countless users opted in.

Warning If you don't trust that these steps are safe or that they won't work, than have your computer/laptop backed up so you can restore it if necessary.

The cup of augmented reality options for Winter Olympics fandom runneth over, with Google pouring a pack of AR Stickers into the mix.

If you've recently noticed that you're missing Quick Settings toggles on on your Samsung Galaxy S6 or S6 Edge—specifically ones for Mobile data, Private mode, and Mobile hotspot—you aren't alone.

The last of the major Google apps has finally received a much needed update to Android's new Material Design aesthetic, and it's a big one—YouTube. While the update will hit the Play Store and your device soon enough, you can download the APK right now, courtesy of our friends at Android Police, from this link.

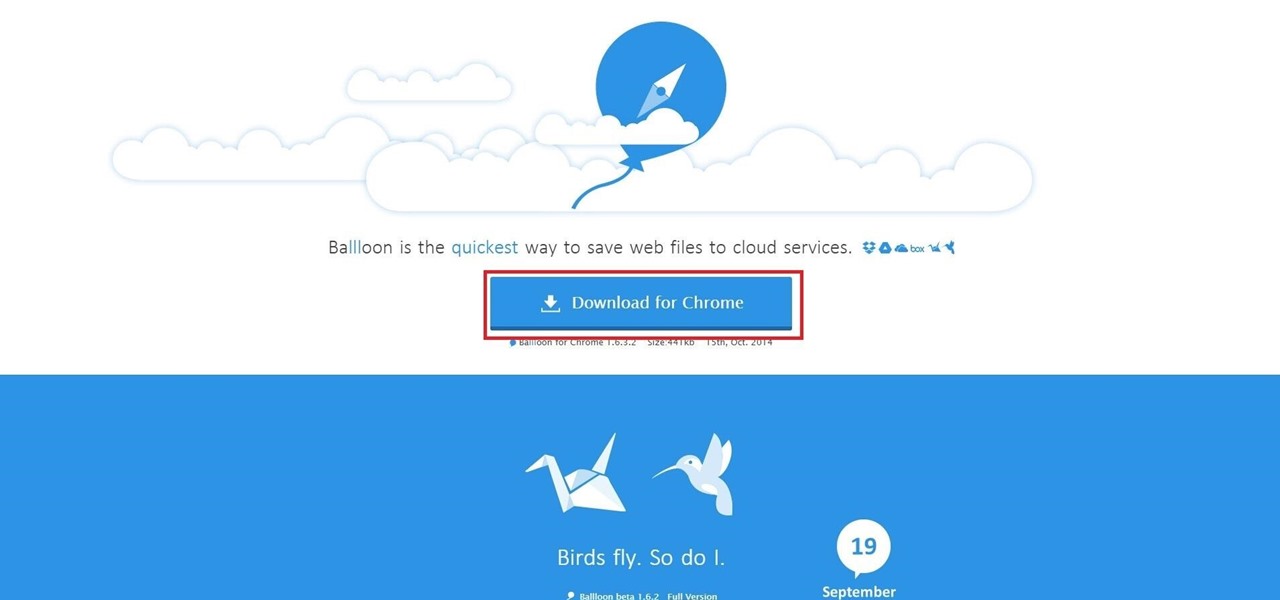
Step 1: First in first, you have to install a Chrome browser, and download Ballloon from official site You can also download it at Chrome Web Store

We love Google Now around here (okay, maybe I do more than others), and today Big G snuck in a nice little functionality when searching for an artist. Exclusive to the US for now, when you enter an artist or band into Search, you'll be presented with listening options for apps you have installed on your device.

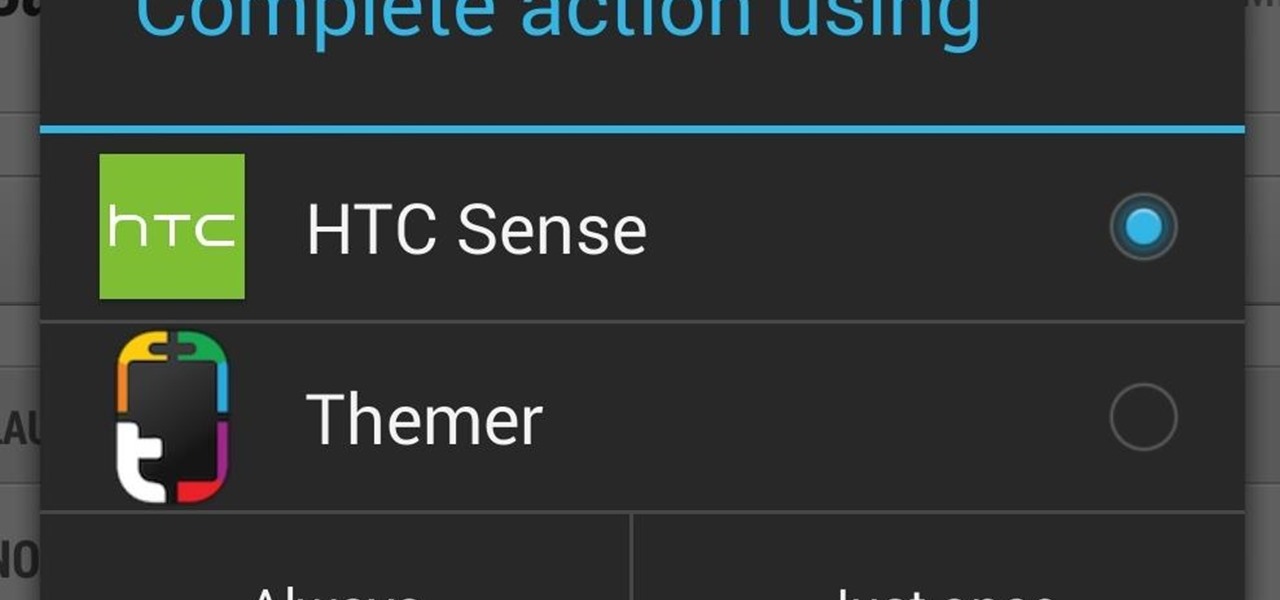
So, you've installed a shiny new launcher but find that it doesn't quite meet your needs? Unfortunately, Sense doesn't come with a setting to choose the default launcher. No worries, though, because in this short guide, I'll show you how to revert back to any launcher, including the stock one. All you have to do is clear the default settings for your current launcher.

One of the biggest reasons we jailbreak our iPads and iPhones is to add and change themes. Apple locks down a lot of how we can personalize our devices, and while the stock look is easy on the eyes, sooner or later we may realize how boring it can be. Now, it doesn't have to be.

It seems like Apple is always releasing something new, so there must be a lot of lonely iDevices out there going unused, right? With Seedio, you can make the most of your Apple products by connecting them to make one synchronized loudspeaker. As long as all the devices have the Seedio app installed, you can connect as many iPads, iPhones, and iPod touches as you want. All you need is a wireless connection. You can play music from anywhere: your library, YouTube, or the Web. It also works as a...

Jan Vorman has installed quick LEGO-fixes all over the world - from Italy to Germany to Israel to Holland.

No one likes it when random people wander into your home and mess things up, which is why it behooves you to hide your things from even the most prying eyes with builds like this totally invisible, 2x2, piston-operated door with no visible redstone either inside or outside. The story of Goldilocks and the Three Bears may have gone differently if they would have had one of these babies installed in their home: I did a tutorial for a piston-powered trapdoor and many people wanted to know how to...

Bikes are a great form of transportation. They use human energy more efficiently than any other machine. You can keep it in your closet or hallway. You can even take it on the train in a pinch. However, this portability is also the bike's biggest draw back. If you own a bike in the city, chances are it will be stolen. Locks barely deter thieves armed with bolt cutters and crowbars. Throw the bike thieves for a loop and make a tilt-sensitive alarm. It will hopefully startle your bike's assaila...

In the last article, we left off with the Tor network and its hidden services. As I mentioned, Tor is not the only option in the game, and I want to offer a general introduction to I2P.

I recently posted a link to what seemed to be a very useful guide on Lifehacker for creating a TOR button in Chrome. However, when I tried it myself, it did not work. Also, it lacked a warning on the limits of Tor, which I think are important. Therefore, I decided to create an updated and more comprehensive tutorial.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

When it comes to webcams these days, most people are using their laptops over desktops. The cameras are centered, integrated, and require no configuring. They're a cinch and usually have great resolution. So, then what do we do with all of those old wired desktop webcams that we've accrued over the years? Even if you still use an external USB one, chances are you're not using it daily, so why not come up with a better use for it?

Continued from Organize Yo'sef Part One!

Following the first part in this series on advanced cracking techniques, we are going to go over how we can intelligently crack passwords using the old-fashioned bruteforce method. These unique cracking techniques aren't widely used, because most crackers are Script Kiddies who have no idea what the concepts are behind cracking passwords, thus, word won't get around too quickly.

How did it happen? How did your ultra-secure WPA password on your wireless network get broken into? Well, you might have just found yourself at the mercy of a cracker.

As per Alex's request, I am posting about generating word-lists in Python. However, this is my FIRST attempt with Python, so please provide me with critiques and any and all comments. I really want to know what you think as there was a little bump here and there seeing as I am transitioning from C#.

Today's tutorial will teach you how to erase data permanently so that it cannot be recovered. Many believe that having a file shredder on the computer means you are up to no good.

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...

If you've ever wondered how software pirates can take software and crack it time and time again, even with security in place, this small series is for you. Even with today's most advanced methods of defeating piracy in place, it is still relatively easy to crack almost any program in the world. This is mainly due to computer processes' ability to be completely manipulated by an assembly debugger. Using this, you can completely bypass the registration process by making it skip the application'...

Windows 8 Beta (Developer Preview) It wasn't that long ago Windows 7 was released - now Windows 8 Beta is here. I did do a Google search to see when the stable version will be out but wasn't able to find an official statement from Microsoft. However - I saw several articles on Google hinting that the final release might be in August or there about.

Shortening URLs has become a necessity in this age of Twitter and limited-character status updates. It not only allows us to cram more words into our oh-so-important Twitter statuses, but it also helps us with a few other things.

If you have made the switch from Windows to Linux, I want to congratulate you in advance. I'm sure you have noticed a huge performance increase when using Linux over other operating systems. This is only half the battle, though! Most users who are new to Linux end up using Ubuntu. I have no gripes with Ubuntu, but I do not agree with their philosophy. It almost mimics Windows. Ubuntu favors ease of use, and despite valiant efforts by the development team thus far (Ubuntu is crazy fast), all o...

Last week's Community Byte we got off to a great start! We had a few people build our IRC bot, and all went well. We had some great contributers, ideas, and people willing to learn. So, needless to say, we will be having another. Let's try to get a few more people involved this time!

Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it.