One of the only things I remember from watching Nickelodeon as a kid is the epic green slime. Looking back, I don't know what was so great about it, but every kid my age thought that being drenched in slime would be the coolest thing on earth.

As NASA nears the launch of another mission to the Moon in 2024, and a subsequent mission to Mars in the 2030s, augmented reality is increasingly being woven into the normal space operations to test various capabilities.

After facing delays due to the COVID-19 pandemic, the Olympic Games are underway in Tokyo, but a surge in cases worldwide has taken the spectator out of these spectator sports.

Like its predecessors WandaVision and Falcon and the Winter Soldier, Marvel's latest series for Disney Plus, Loki, has its own augmented reality experience.

Gamers, anime fans, and those with an interest in Japanese culture are in for an AR treat courtesy of Google.

Since launching its web-based AR platform in 2018, 8th Wall has continued to push the boundaries of what brands can do with AR experiences outside of native apps.

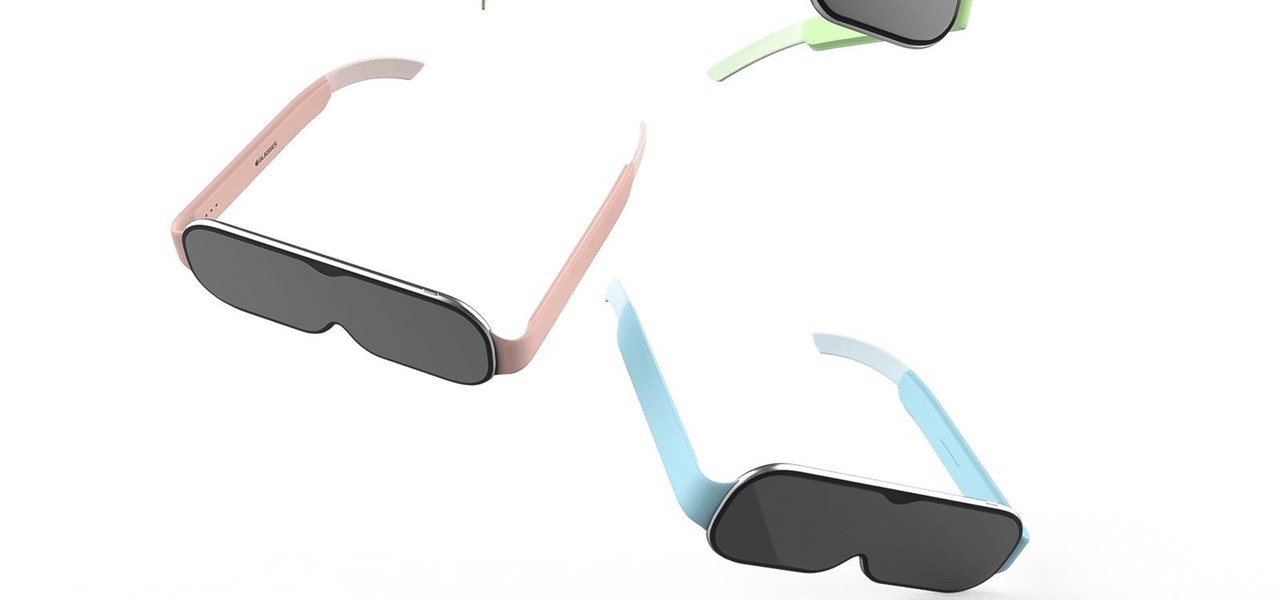
Rumors of Apple developing smartglasses have persisted as prophecy since 2016, but the arrival of what many herald as the savior of augmented reality have eluded even Nostradamus himself.

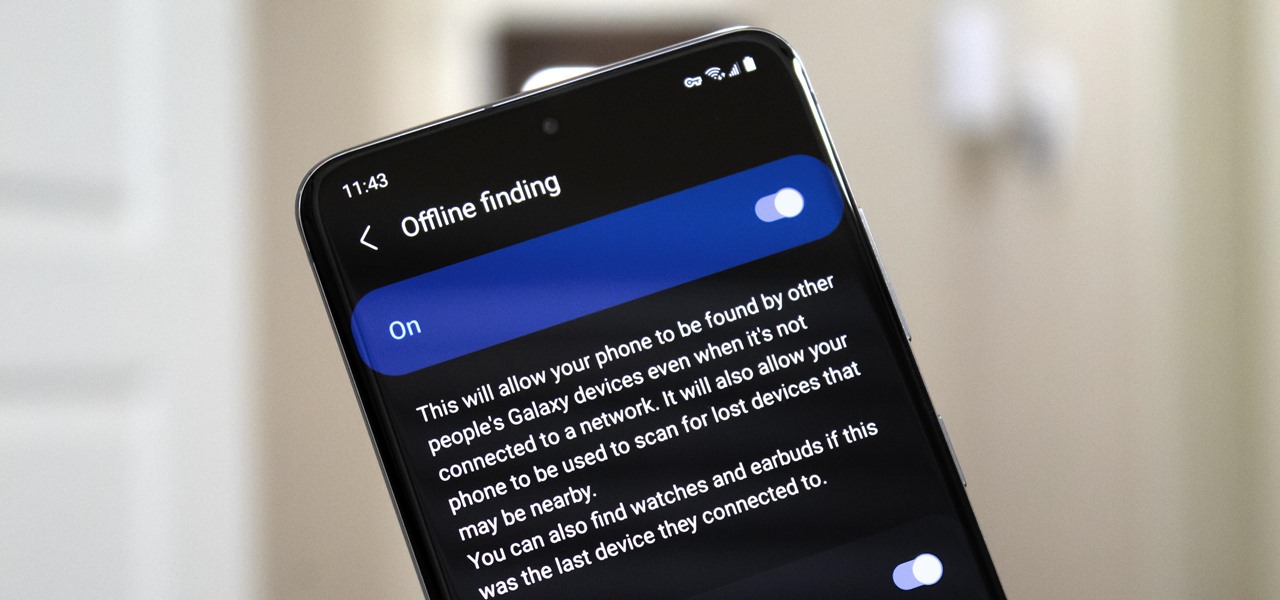
Nowadays, even the dumbest thieves know that the first thing you should do after you steal a phone is turn on airplane mode. Not only does this make it harder for police to track the phone through cell tower triangulation, but it also disables security features the person you stole it from may have implemented — for instance, Samsung's Find My Mobile service.

It's incredible what technology can do these days, but sometimes, it gets a little scary. For instance, FaceTime's "Eye Contact" feature, which Apple beta-tested in iOS 13 but released with iOS 14, makes it appear like you're looking right at the camera, even when you're actually looking at your friend on the screen. If you find this artificial trick a bit creepy, rest assured you can turn it off at any time.

Apple's Dark Mode in iOS 13 and later offers a cool, comfortable viewing experience on your iPhone. You may prefer the dark theme all day long, but if you like to use it only at night, it's not very convenient to switch it on and off daily. But there's a setting that lets you set it and forget it, so you never have to do it manually again.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

When you're stuck working or learning from home, video meetings can help you stay connected to employers, coworkers, schools, students, and more. And Zoom is the hottest video conferencing service at the moment. While Zoom is easy to use, it does have a fair share of sketchy features you should know about, such as attendee attention tracking.

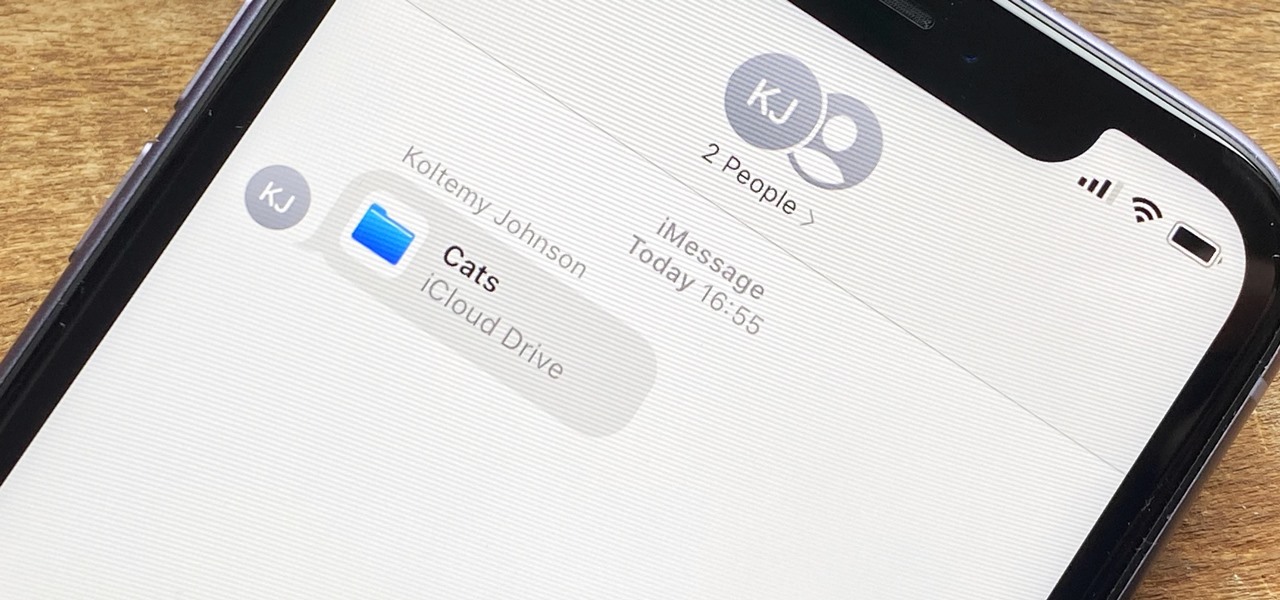
In the iOS 13.4 update, Apple added folder-sharing capabilities in the Files app. That means you can share multiple documents at the same time instead of doing it one by one. But that's not all — you can share folders with numerous contacts and even enforce access and permission settings.

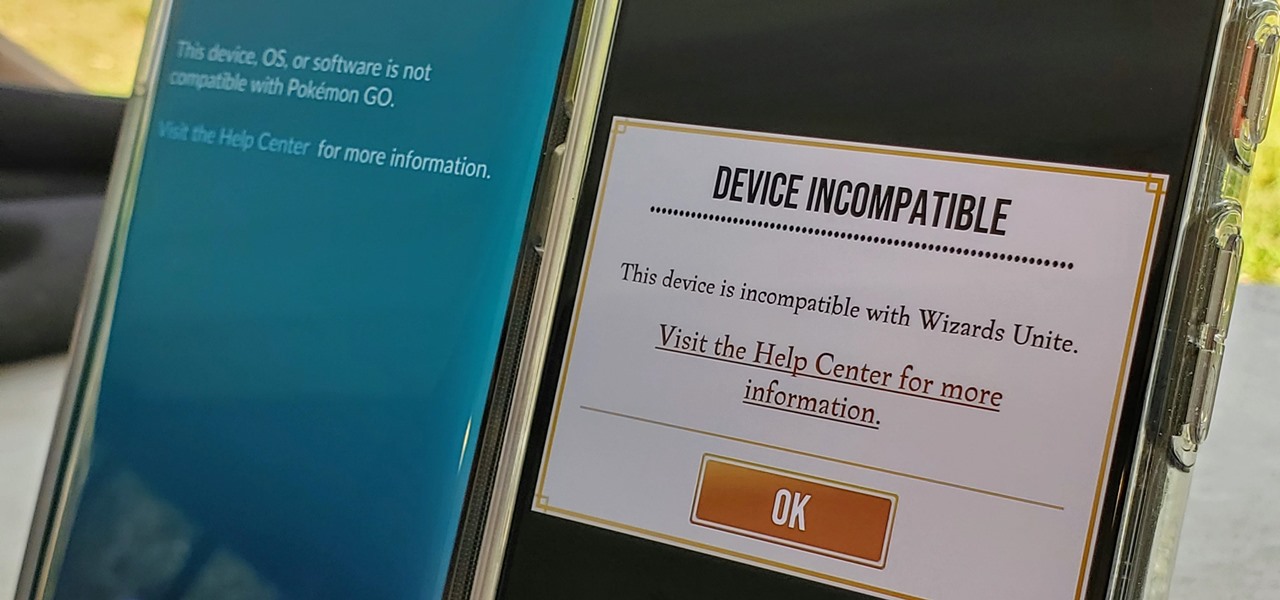
Both Pokémon GO & Harry Potter Wizards Unite are augmented reality games developed by Niantic, and neither needs much introduction. Pokémon GO, all by itself, created a worldwide phenomenon that still carries a strong fan base years later — Wizards Unite is working on doing the same. However, things are not all fun and games, as you might think in the world of monsters and magical creatures.

Sending Christmas cards via snail mail is so passé. Why spend the time and money for a bougie photoshoot, saccharine card design, and postage when you can use augmented reality to instantly dress up photos and videos to send to friends and family instead?

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

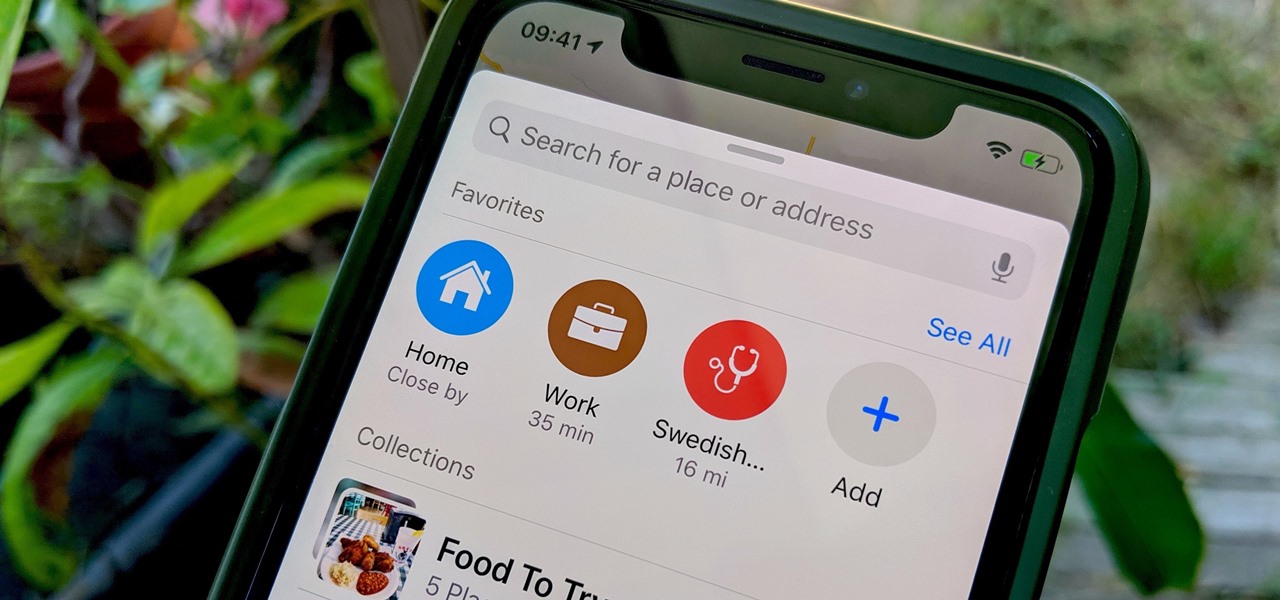
In iOS 13, Apple Maps makes it easier for you to organize essential places on your iPhone, allowing you to save locations as favorites that you can access at a glance.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

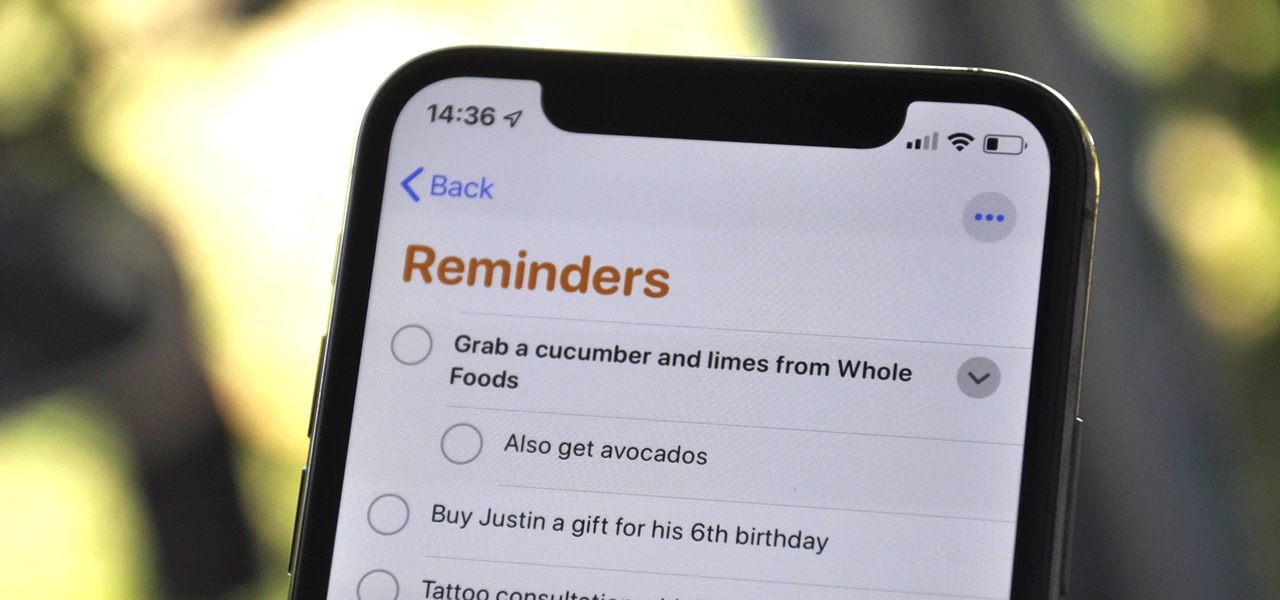
Things are a bit more organized in Apple Reminders, so the cluttered mess that it once was is no more in iOS 13. The slapped-together feel in older iOS versions was the main reason I never used it that much, but the updated version for iPhone has finally got me hooked.

Many popular apps automatically share your personal data. While I have accepted a certain amount of data collection from Google, to know companies such as Facebook perform this without my consent bothers me. After some researching, I've found a great solution, and it doesn't require root.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

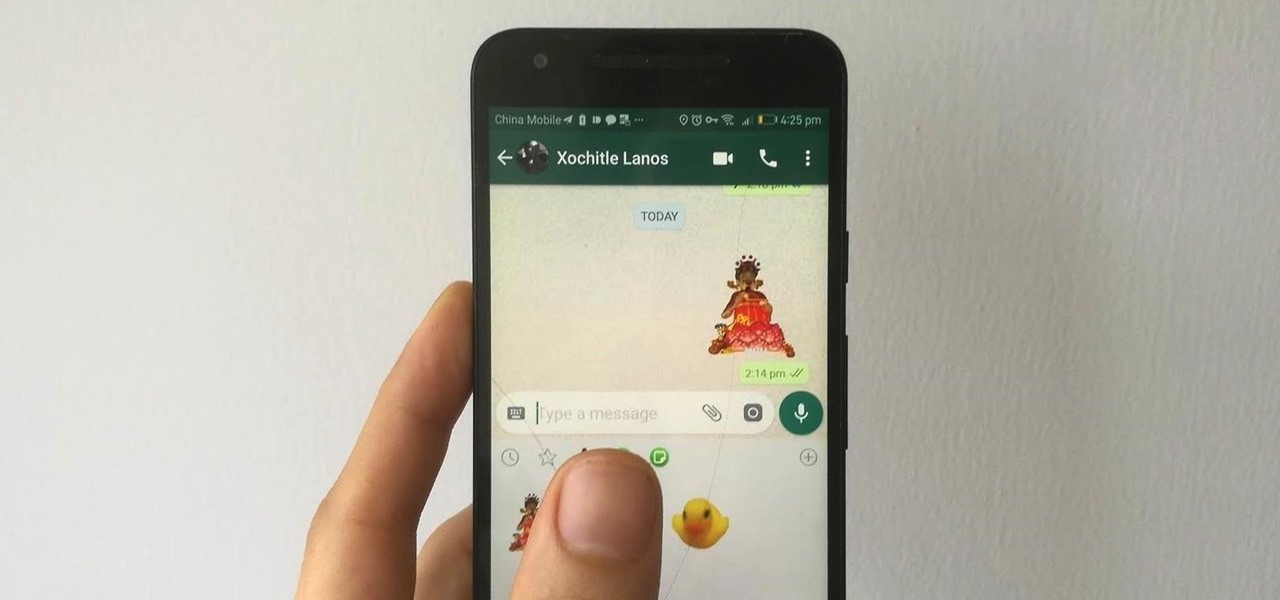
WhatsApp stickers can make your chat more fun. The stickers that come with WhatsApp are fine, but they're standard and accessible to everyone. What if you wanted to show off unique stickers that your friends haven't seen? To take things to the next level, you can create your own WhatsApp Stickers.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

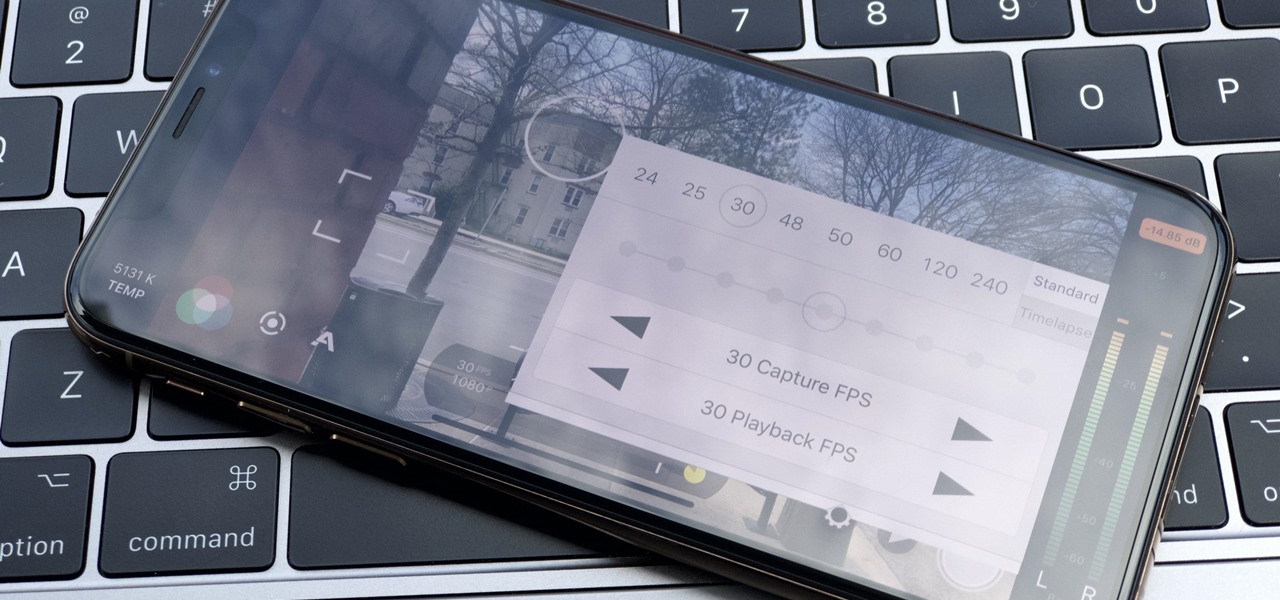
There are many reasons to use Filmic Pro if you're a mobile videographer. Chief among them is its automated controls, called "pull-to-point" sliders. These pull-to-point controls not only allow you to manually adjust focus, zoom, exposure, ISO, and shutter speed before and during the action, they also let you set start and end points to automate each function, leaving you free to focus on filming.

The days of bad smartphone videos are long gone. Your iPhone or Android phone is a capable video recorder, even offering different frame rate options in the native camera settings. Filmic Pro makes things a little simpler, however, and adds additional controls you wouldn't find on your device alone.

Apple's aiming to take over the TV world, and it shows in iOS 12.3. Nothing is going on yet with Apple TV+, Apple's video streaming platform with original content, which isn't supposed to come out until the fall. But there are some goodies in the new Apple TV app for iPhone that you should get to know.

Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available to all users, on Android and iOS — you just need to know where to look.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Until very recently, Apple apps were among the only ones that would play nicely with Siri on iPhones. If you wanted to take advantage of the digital assistant to, say, compose an email, you would need to go with Apple Mail instead of the email client you actually use. As of iOS 12, this is no longer the case.

Last year's augmented reality investments roundup was impressive. And in 2018, the dollars flowing toward AR haven't decreased, as venture capitalists and strategic investors continue to aggressively fund AR startups at a rapid pace.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

Because timing is everything, the latest entry in the location-based augmented reality gaming sweepstakes, Ghostbusters World, has arrived just in time for Halloween.

Apple's iOS 12 has finally landed. The big update appeared for everyone on Monday, Sept. 17, and hiding within are some pretty amazing augmented reality upgrades for iPhones, iPads, and iPod touches. We've been playing with them ever since the iOS 12 beta launched in June, and here are the things we learned that you'll want to know about.

With new iPhone models out, you'll have updated cameras to try out, a faster processor, and new colors to choose from. The only thing that could stop you from picking one up yourself is, well, your current iPhone. Here's how to check if you're eligible to upgrade to iPhone 11, iPhone 11 Pro, iPhone 11 Pro Max, or any other iPhone still being sold.

Like an overbearing mother, Apple will constantly nag you through annoying red bubble alerts about iOS updates that are ready to install. Fortunately, you don't have to take this issue lying down, as there are ways to prevent your iPhone from receiving OTA updates and their corresponding prompts, regardless of whether your device is jailbroken or not.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, Apple has added many new features to Safari, most of which have their own unique way of keeping you safe online.