Want to find every instance of a person's name on a particular website? This Googler's guide from the folks at Mahalo will teach you how to do just that. For all of the relevant details, and to get started using this handy Google hack yourself, watch this video tutorial.

If someone violates a protective order, there are — the remedy would be the police would be involved. You'll get arrested. So, basically, a protective order is usually good for two years, and it has all the specific things you cannot do. For instance, you can't go by that person's — within 200 feet of them or their residence or their employer. So it has some very specific things. A restraining order is different. It's a standard thing that's given that's a mutual thing where it just says be n...

While browsing the web on a computer, most of us are familiar with using Ctrl + F (or Command + F) to search for a specific word on a page — but what if you want to do that on mobile? If you're using Google Chrome, there's a simple way to search for specific words on iPhone or Android.
In this video, John Heaney gives advice on how to answer a simple but difficult question during a job interview. If interviewers ask job seekers to tell them about themselves, they can be put on the spot and be unable to even begin to answer the question. Heaney puts this question into perspective from the employer's perspective. For instance, he reminds you to remember that you are applying for a job and your answer should be related to your technical abilities rather than your personal inte...
In this video tutorial, Chris Pels will show how to determine what capabilities a user’s browser has when viewing pages in an ASP.NET web site. First, learn how to access an instance of the HttpBrowserCapabilities object from the ASP.NET Request object associated with the web page request. Next, see the different information available in the HttpBrowserCapabilities object such as the type of browser and whether the user’s browser supports JavaScript and Cookies. Then see an example of how to ...

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

With the use of Terminal, anyone can run multiple instances of the same application on a Mac. When you have multiple windows open in a web browser, the windows are all running under the same Process ID (PID). But, with multiple instances, each has its own unique PID. So why would you want to run multiple instances of the same app? There are several reasons a person may run clones of the same application, but the most popular would be so that the user could multitask. Some applications, like t...

The Deadmines are a heroic instance you can play through in World of Warcraft: Cataclysm. It's a general dungeon instance, whose most notable quality is how hard everything hits. So when you make this run, make sure you have some good tanks with you.

You're at the final encounter, so make sure your party doesn't get completely wiped! This video is a guide to defeating Nefarian, the final encounter in the Blackwing Descent instance on World of Warcraft. You'll need quite a lot of DPS characters, and don't forget the healers.

Another WoW strategy guide! This video shows you how to get past Cho'Gall, one of the encounters your party will go up against when you're fighting your way through the Bastion of Twilight instance. Avoid a TPK by following these tips!

Throne of Tides is the second instance in the newest expansion for World of Warcraft, Cataclysm. Be aware of all the perils and monsters in this map, know how to beat the final boss and make sure to get the best loot drops!

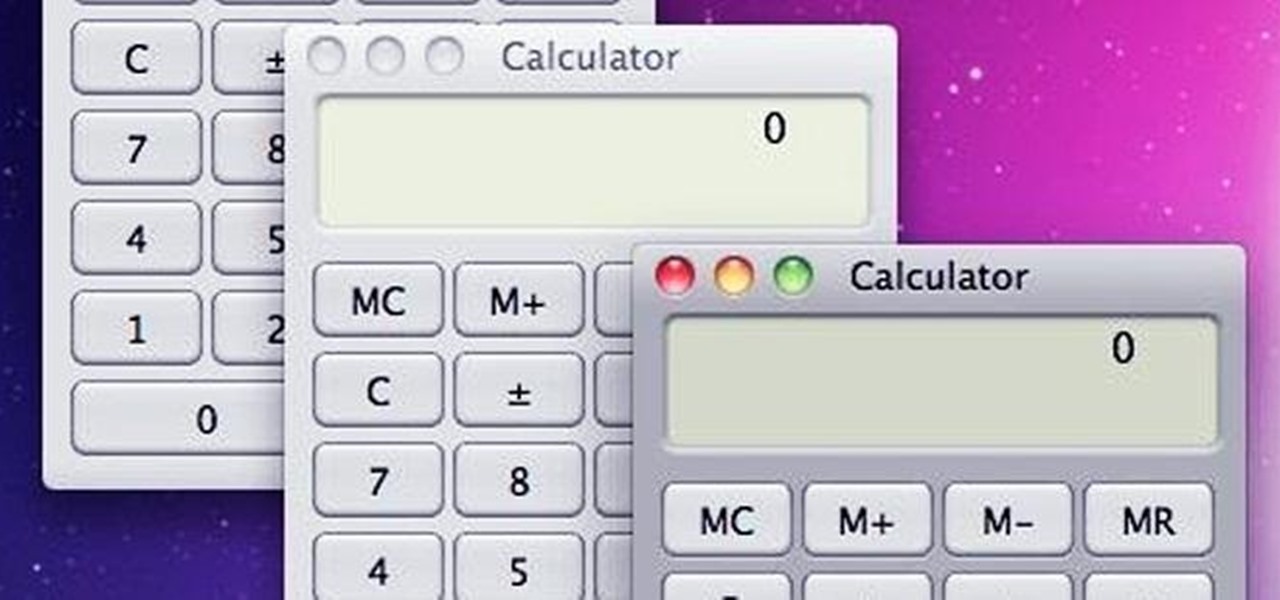
Interested in quickly creating a new instance of a program in Microsoft Windows 7? This will show you how it's done! It's easy! So easy, in fact, that this home-computing how-to can present a complete overview of the process in just over a minute's time. For more information, including detailed, step-by-step instructions, watch this Win 7 user's guide.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

This is a presentation of different types of immune responses in human body. There are two types of immune systems i.e., non specific and specific or adaptive immune system. Again, non specific immune system is sub- divided into barriers. It is the first line of defense. The second line of defense is the inflammatory response. They are phagocytes. These are all products of white blood cells. It is also called as leukocytes. Lymphocytes are another type of white blood cells which are carriers ...

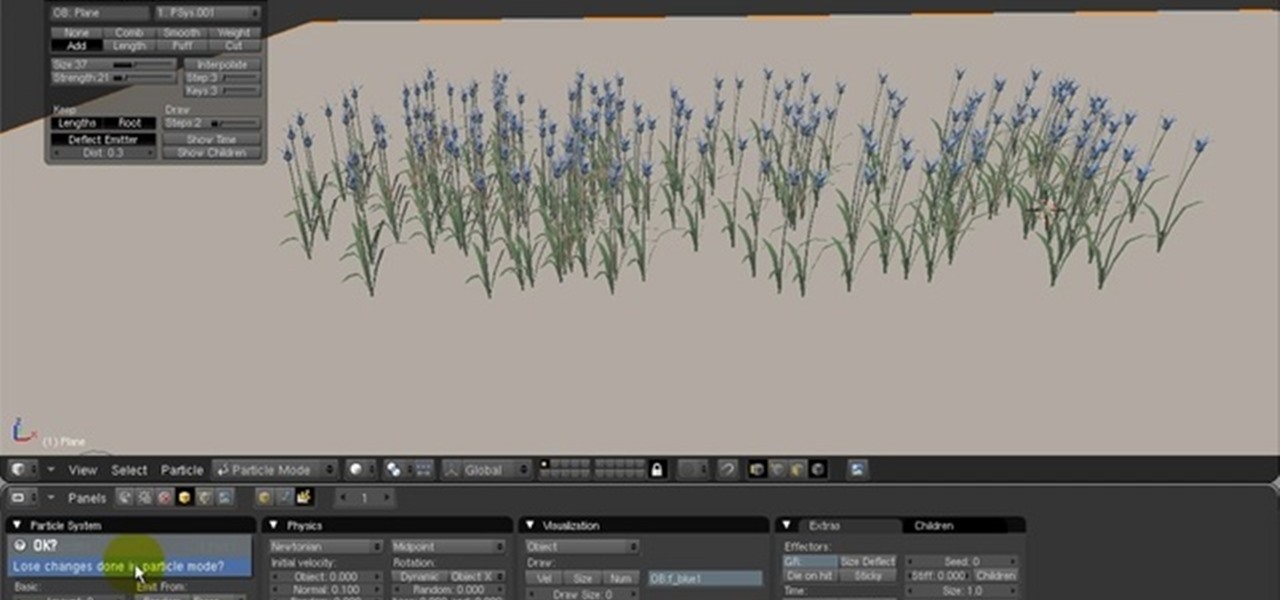
This tutorial teaches how to use Blender’s particles system to “paint” instanced objects onto mesh surfaces. Similar to Maya’s “Paint Effects,” though not nearly as powerful, it’s a very nice way to fill a scene with flowers, vegetation, rocks, pebbles, gravel, debris, etc. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or are a seasoned digital artist merely on the lookout for new tips and tricks, you're sure to be well served by this free...

Need some help figuring out how to configure safe frames and grids in Maya 2011 when animating for specific output source? This clip will show you how it's done. Whether you're new to Autodesk's popular modeling software or a seasoned 3D artist just looking to better acquaint yourself with the Maya 2011 workflow, you're sure to be well served by this video tutorial. For specifics, watch this free video guide.

Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBostonian will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to multiple methods and also instance variables inside a class when writing in Java. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.

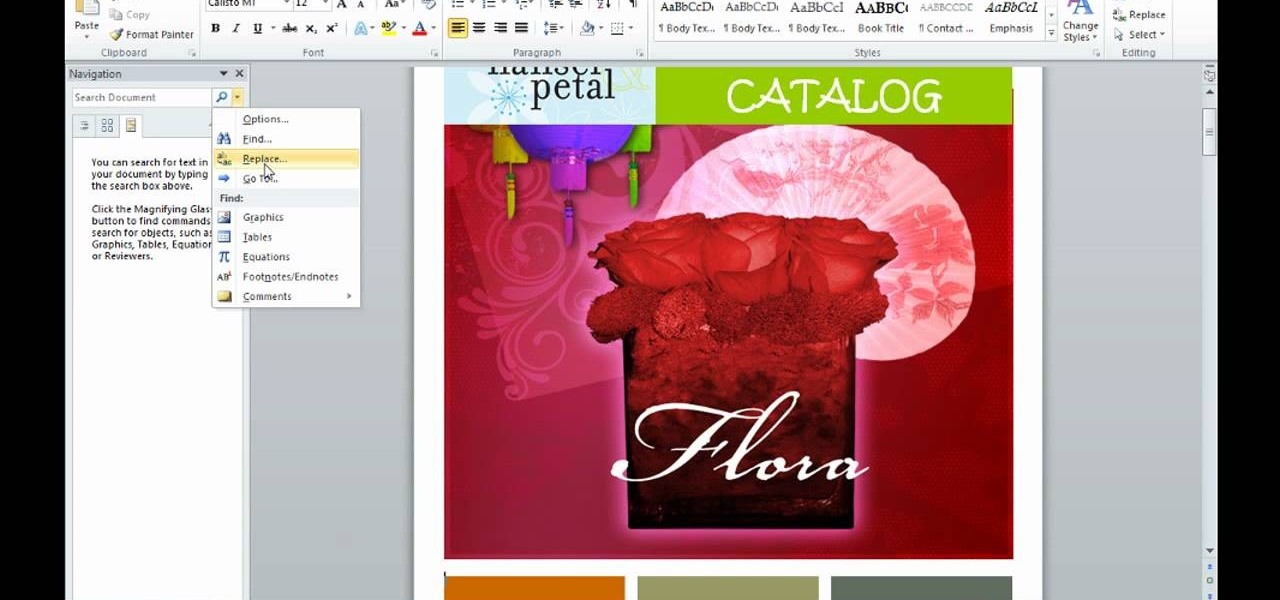
This is an informative video tutorial on how to search graphics, tables and charts using MS Word 2010. The author informs that the earlier MS Word editions had fast and easy search options, but the same feature built into the 2010 edition is vastly improved. One simply has to click the ‘Find’ option at the top right-hand corner and a navigation pane opens on the left-hand side. In the search box, the keyword is typed in and all the instances of that word in the document are highlighted, while...

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

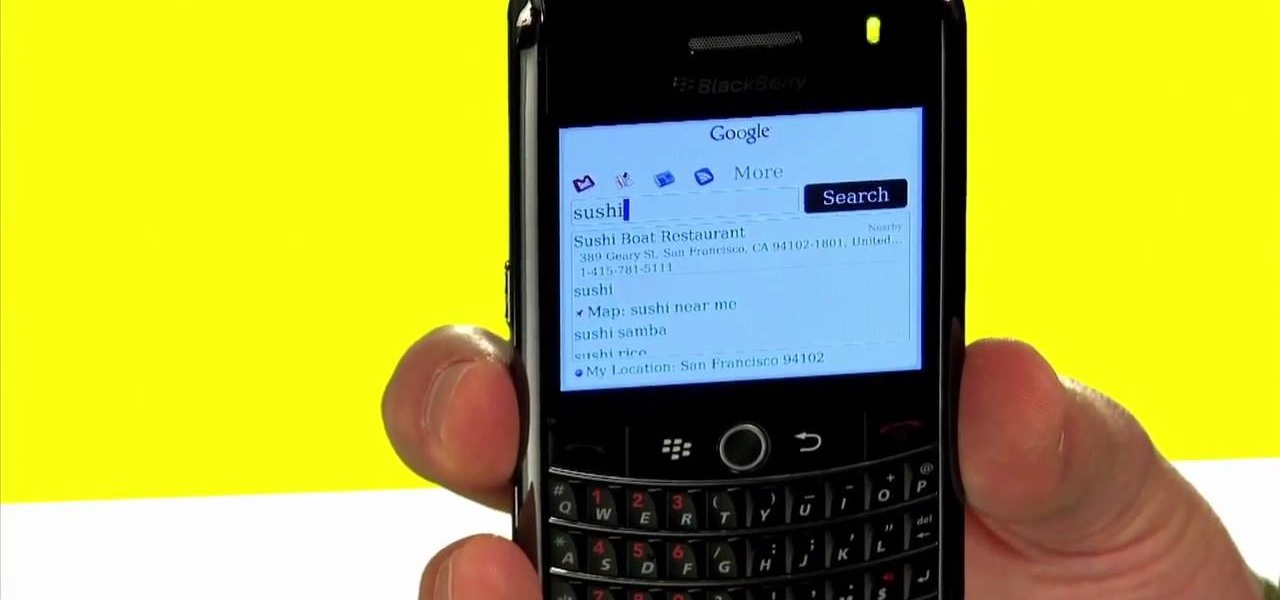
Best Buy shows us how to use the Google Mobile App for location specific searches on your mobile phone. Google Mobile can find you the nearest restaurant in your town, and provides maps and directions. It's pretty easy to use, and you can use it on many phones, including Blackberry, Windows Mobile, Droid, iPhone, and Nokia.

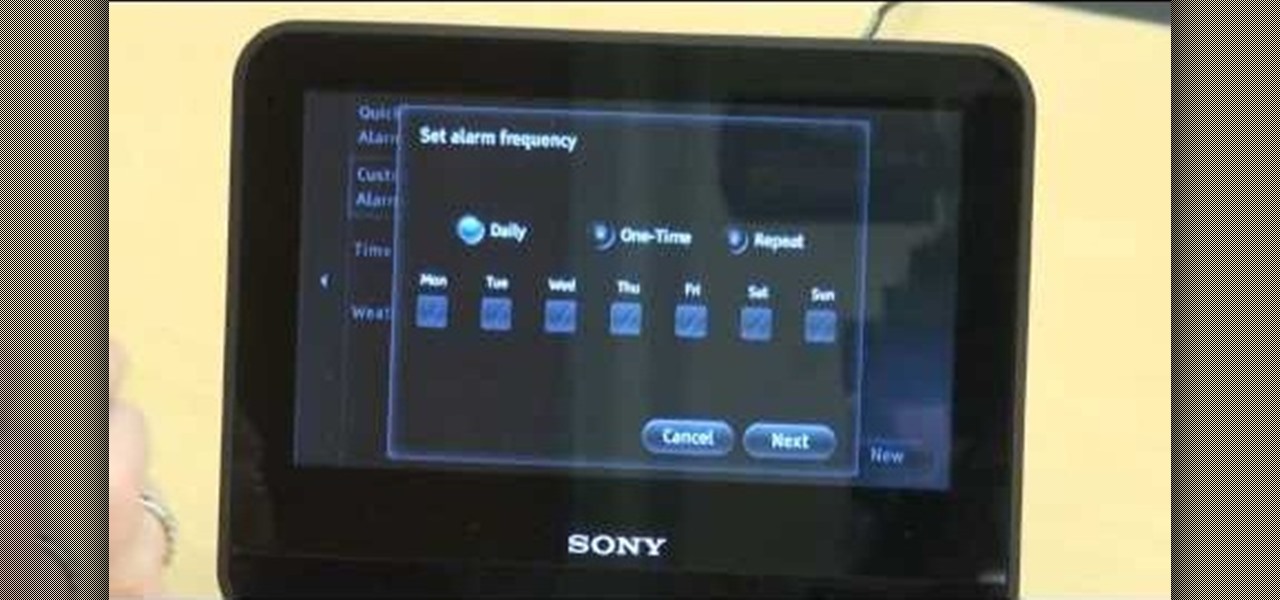
The Sony Dash is a hot tablet, and like most tablets it can be used for all sorts of awesome purposes that full-sized computers are not suited for. Alarm clocks, for instance. This video will teach you how to set music and video to your alarm clock on the Sony Dash.

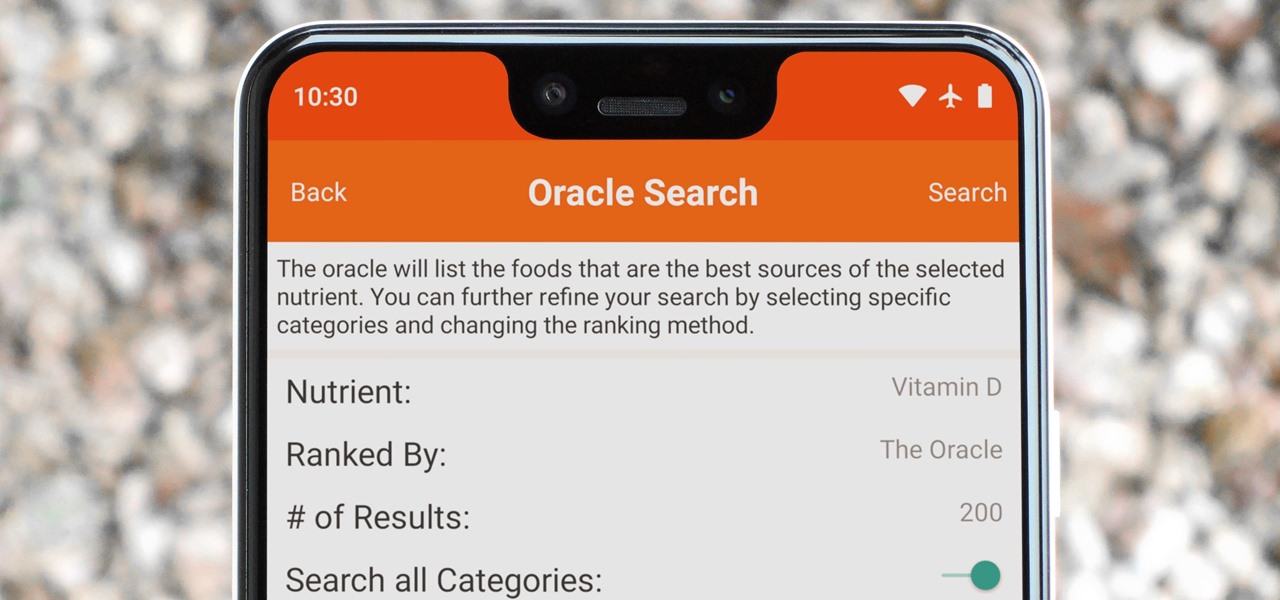
Micronutrients are essential to our health. Unfortunately, many of us aren't getting enough of each nutrient from our diets. It isn't that the food we're eating is bad, but rather we are not eating enough of the right food to get our recommended daily allowance. But with the help of a micronutrient tracker, we can change this.

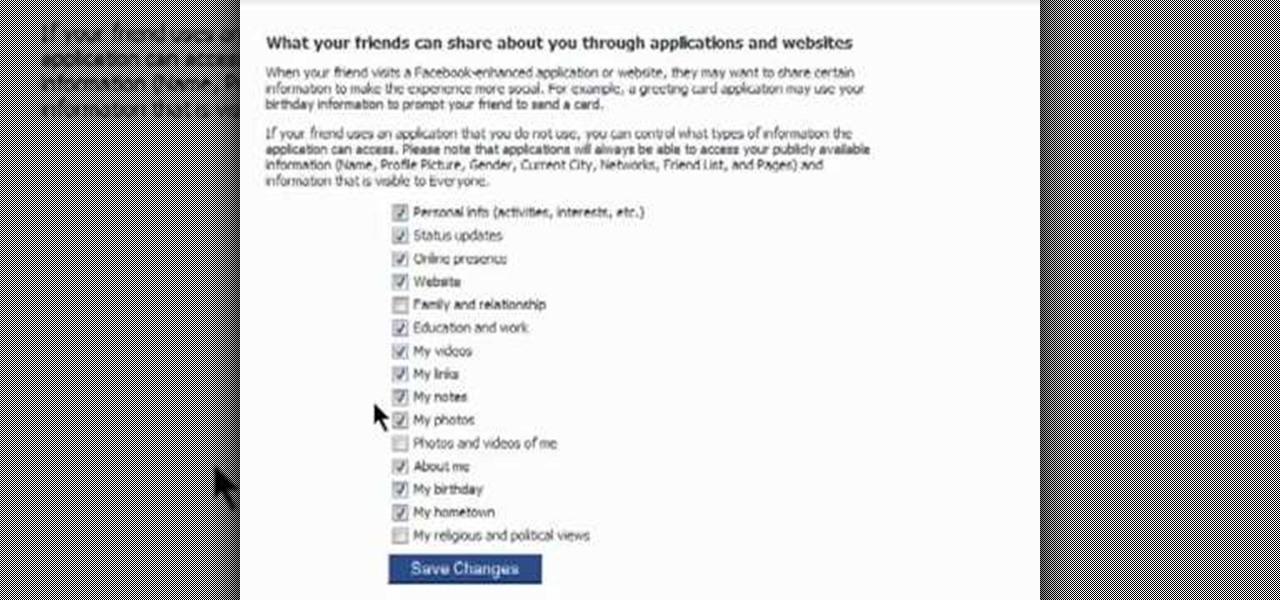
You might be unaware that Facebook has a separate settings menu for what your friends can share about you. This includes information about you that can be shared through websites and applications. This clip provides instructions on how to adjust friend- a group-specific privacy settings on Facebook. For more information, including detailed, step-by-step instructions, and to get started adjusting your own Facebook privacy settings, take a look.

In order to Find, Replace, and Sort, using MS Excel, become familiar with your home tab. When you click on Sort, it will give you the opportunity to sort in different ways: e.g. alphabetically. If you accidentally shift your table, you can undo it by using Ctrl + Z. Custom Sort will allow you to be very specific in the way you want your data sorted. You can add or remove a filter with the same drop down menu, in order to be even more precise.

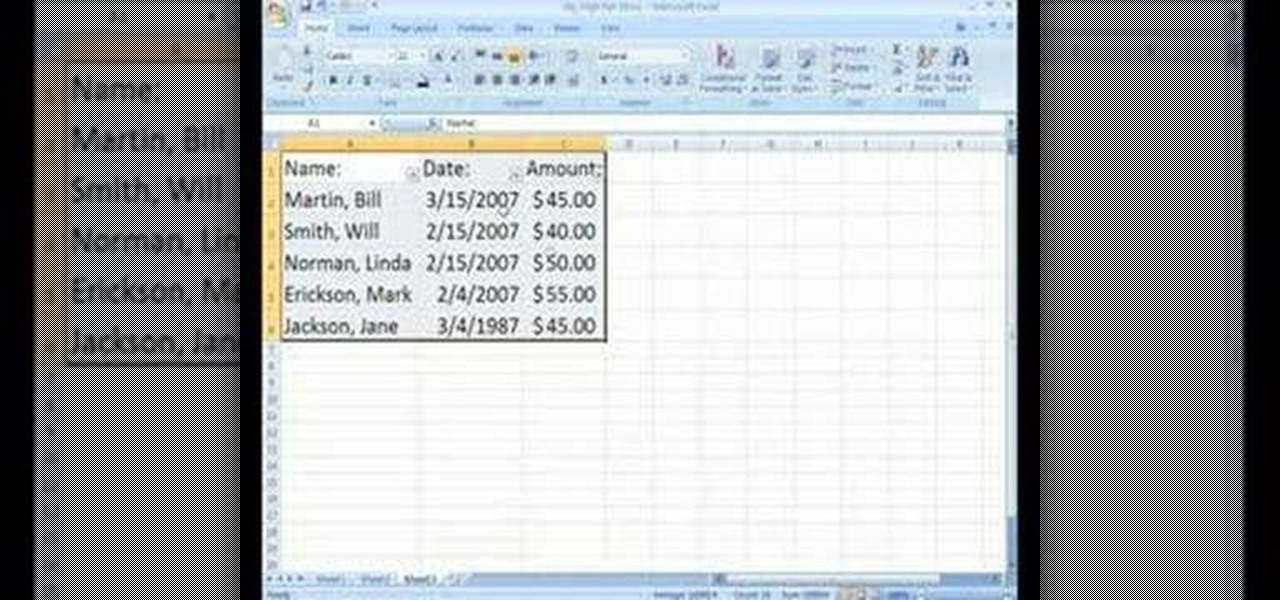
Want a way to dynamically reference the number of instances of a given word in a Microsoft Office Word document from Excel? Who doesn't, am I right? In this Microsoft Excel tutorial from ExcelIsFun, the 543rd installment in their series of Excel magic tricks, you'll learn how to do just that.

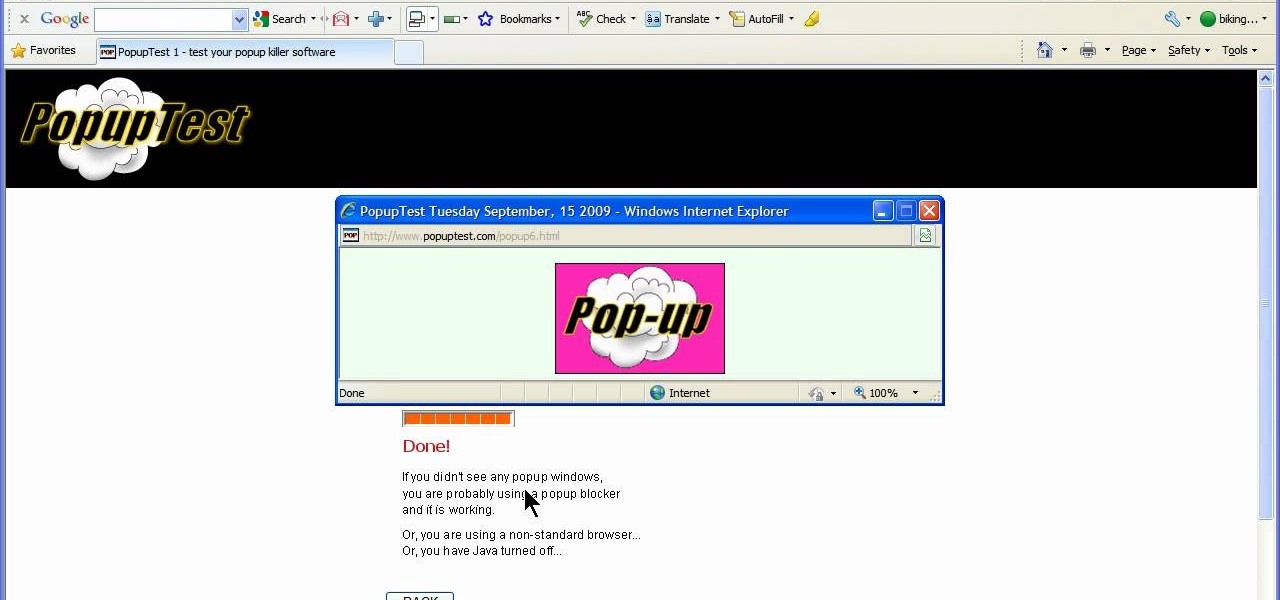
This video will show you how to enable/disable the pop up blocker for a specific web page: 1. To allow pop ups on a specific website click on the pop up blocker button on your tool bar, the Icon will change to show that pop ups are now allowed.

Feeling lost inside a library? The Dewey Decimal System is a logical and popular book classification system for libraries and schools helping you to easily locate any book or periodical you need. Fool these steps to better understand the Dewey Decimal System.

For many of us, being the interviewer is as nerve-racking as being the interviewee. You can keep your cool and quickly weed out unqualified applicants.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.