A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Ever notice how some augmented reality apps can pin specific 3D objects on the ground? Many AR games and apps can accurately plant various 3D characters and objects on the ground in such a way that, when we look down upon them, the objects appear to be entirely pinned to the ground in the real world. If we move our smartphone around and come back to those spots, they're still there.

Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

NJStar is a program which you may purchase online, and which will allow you to translate individual Chinese characters. This tutorial shows you how to use the software, and explains the limitations of the progam (it cannot translate whole paragraphs, for instance).

We're not saying that we don't like Rihanna's current red fauxhawk, but back when the curvy diva had longer hair she pulled off some major trendsetting hairstyles.

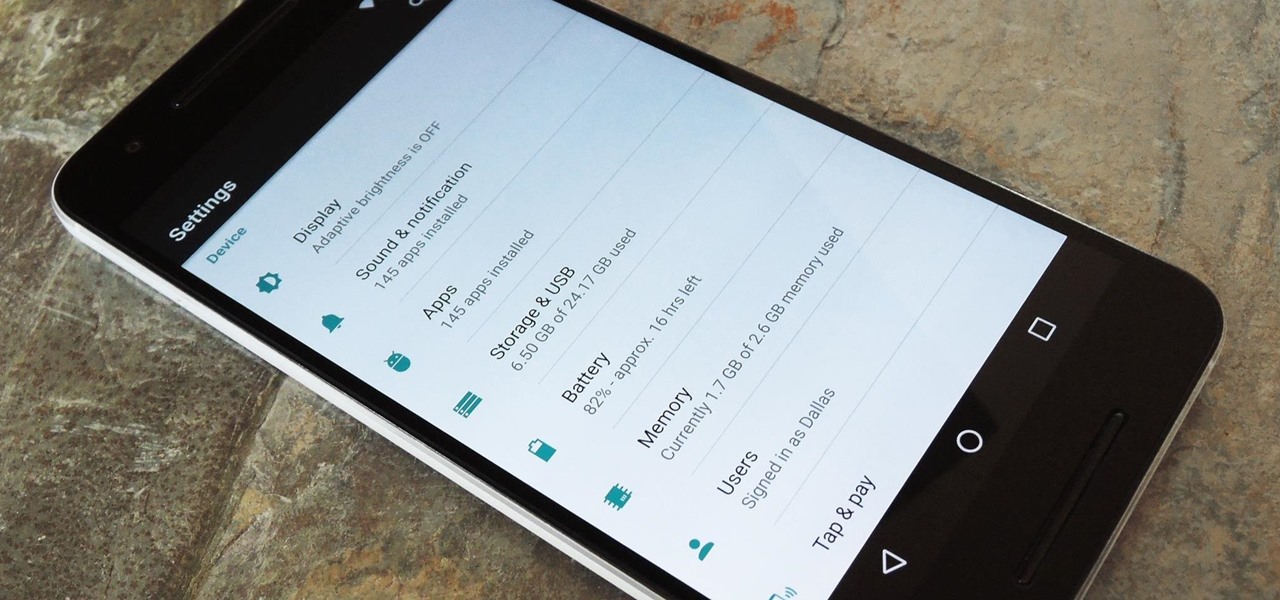
Android 6.0 Marshmallow added a new permissions system that can make your digital life much more secure. Unlike previous versions, apps now have to ask for your consent before they can access certain data, which puts you firmly in the driver's seat.

Like Marvel's Avengers, Facebook's Camera AR platform now has a number of new AR superpowers at its disposal, so it is fitting that Earth's Mightiest Heroes have the distinction of displaying them.

Chrome's text selection interface is pretty nice, but it could definitely use some improvements. For instance, when you're in Incognito Mode, you can't perform a web search for words you've highlighted. And when you're typing out a forum post or using any text input field, for that matter, there's no option to search or share any of the text you've written.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.

After the mobile augmented reality platforms of ARKit and ARCore moved Google's previously groundbreaking Project Tango (the AR platform that gave us the first smartphones with depth sensors) into obsolescence in 2018, we've seen a bit of a resurgence of what was then a niche component for flagship devices.

There's never just one way to wear a shirt. For instance, you don't have to pair your crochet top with the same pair of acid wash blue jeans EVERY time, nor do you have to pair the same gold Tiffany's pendant with its matching Tiffany's bracelet. In fact, switching around what pieces you wear together is part of the fun of dressing up.

Some of the best kids activities are done right in your own home, recycling everyday items. For instance, an egg carton. What could you possibly make out of an old egg carton? This video will show you exactly what you could do! See how to make egg carton flowers. These decorative flowers can proudly be displayed anywhere. All you and your kid will need are:

In this video a user shares how to use an external monitor as the main display on the Mac. For instance a recently purchased flat screen TV can be used as the primary display. So if you want to use your external monitor as your primary display then all you have to do is follow these simple stops.

Your first step is to bring your decimal point up to the top of the equation. The you divide the whole number into the decimal number. In this instance, 5 into 1.25. 5 goes into 1 0 times, so you put the zero in the first space. 5 goes into 12 twice, so you place a 2 up top, after the decimal. Then you subtract 10 from the 12 to leave you with a 2. This then gets added on to the 5, so you divide 2 into 25 giving you 5. So your answer is 0.15. You can then do this for any whole number and frac...

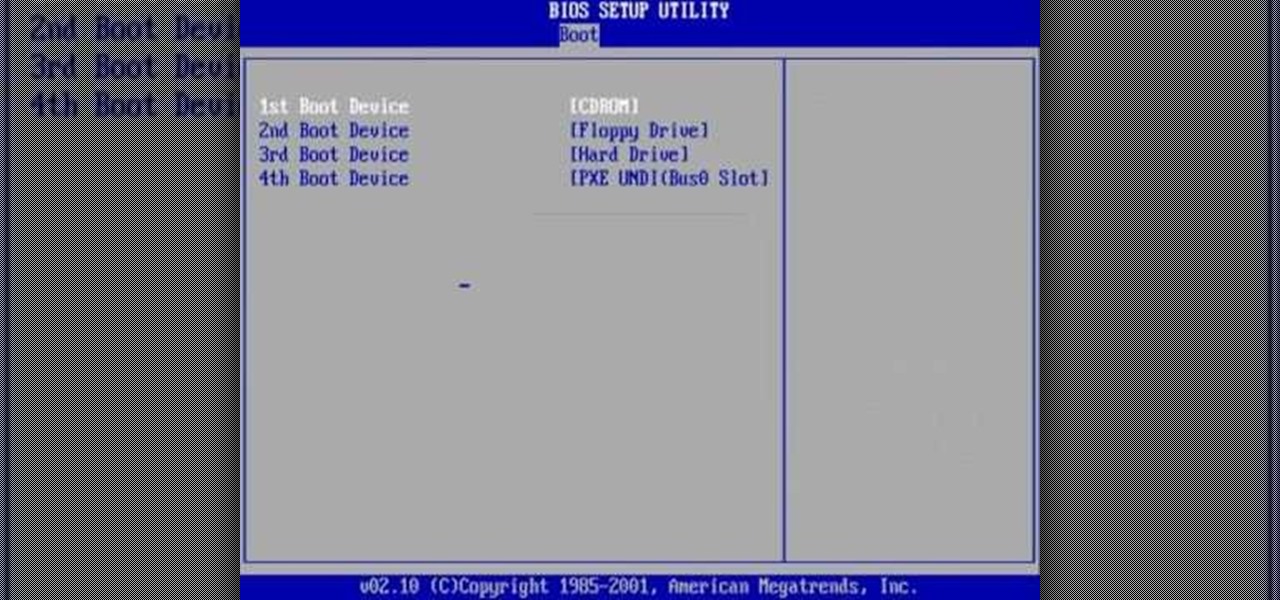
The video shows users how to change the boot sequence in a computer with an older AMI (American Megatrends, Inc.) BIOS to boot from the CD/DVD drive. This is required, for instance, if you need to reinstall an operating system, or fix a corrupted windows installation by running Windows Setup from the installation CD. Users should first enter the BIOS setup by pressing the delete key when prompted shortly after powering the computer on. Once the Bios Setup screen has loaded, users may navigate...

Tim Gilbert breaks down the task of singing & playing the acoustic guitar into 3 simple steps. Step 1: Strumming

An instructional video by tradigital artist Merrill Kazanjian. Step 1- Scan the image

For all kinds of 3D material channels, it sometimes benefits the project to have a small, tileable image that will fill the surface of the object without an obvious seam. Of course, a tileable image will show the duplication if the instance shows up enough times. The trick is to avoid any hard lines where the image might change dramatically as it tiles across the face of the 3D object. Here's one method to avoid those nasty straight seams. (In two parts).

Every home is a little different, and for a smart home app to work, it has to be able to be customized to work with each person's unique setup. With the iPhone's Home app, everyone can set up a smart home just how they want, including the number and names of rooms, and where those rooms are in the house.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

Owners of Google Pixel devices now have a plethora of imaginary friends to play with thanks to the Playground augmented reality app.

As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.

When Android N is officially released sometime later this year, it will bring a lot of cool new features along with it. We've already had the chance to play around with some of these, thanks to a preview build available to Android beta testers, and one change that we like in particular is a revamped Settings menu. Among other things, each settings entry now has subtext beneath it that shows relevant info at a glance.

Welcome back everyone! In the last training session we covered basic file input and output. We're going to leave this topic for a bit and start on something that will change the way we write scripts, classes.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

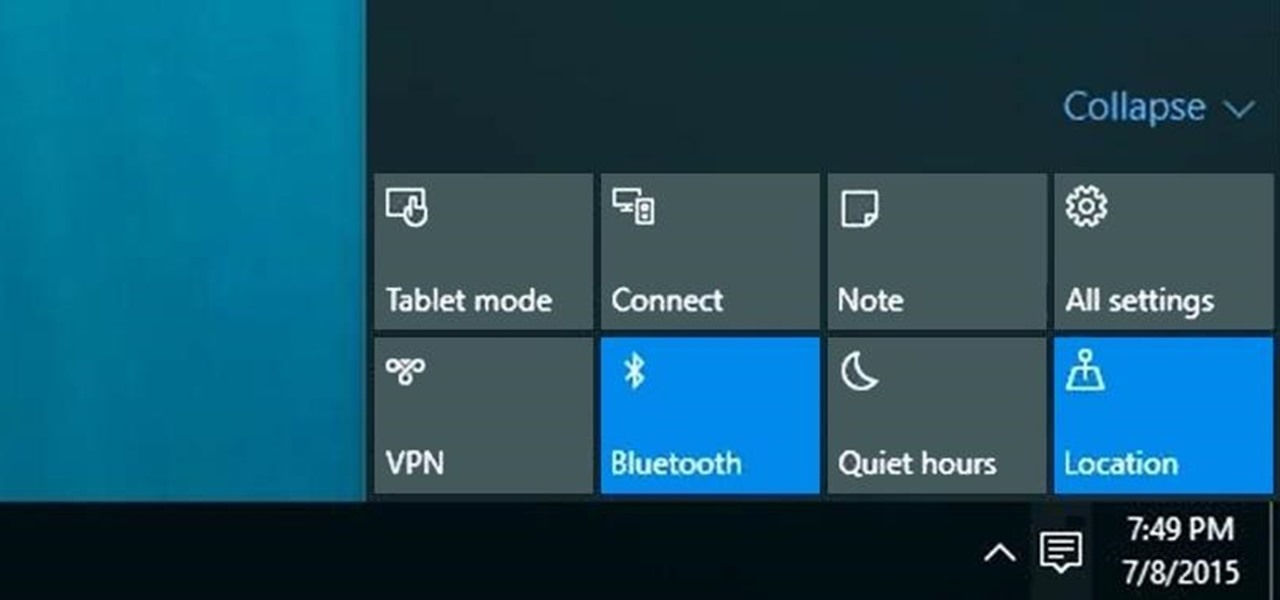
Microsoft's new voice-enabled virtual assistant, Cortana, is a lot like a blend of Siri's personality and Google Now's predictive capabilities—but the best part is it's baked right into the taskbar in Windows 10.

The world's most commonly-used desktop operating system is getting a huge makeover in the form of Windows 10. While there are many sweeping changes in this new version, some of the smaller tweaks may prove to be the most useful.

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

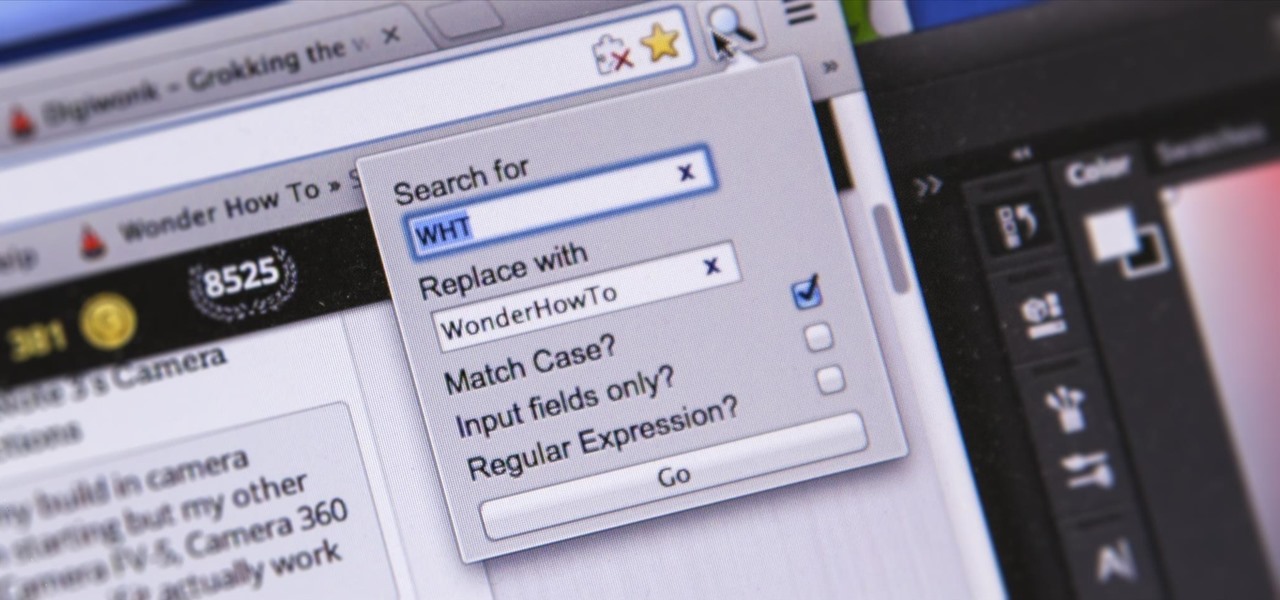
I'm sure you've been there—halfway through typing something out, you realize that one word you've been using more than any other has been misspelled. Perhaps it's a single word, acronym, or line of code that you find yourself typing quite often at work, but this one requires complicated hand gymnastics that you'd simply rather not perform over and over again.

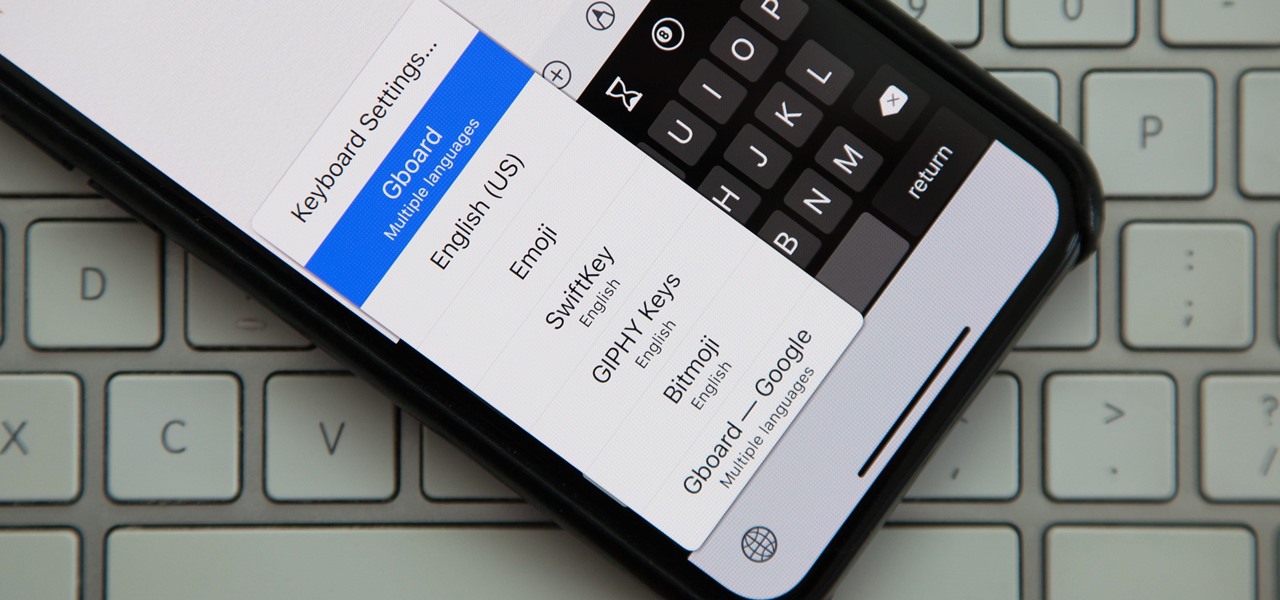
Back in iOS 8, Apple introduced the option to use third-party keyboards on iPhone, and since then, there have been a ton of third-party keyboards available such as Gboard, AudioShot, SwiftKey, Slated, and many more. However, adding and even using these keyboards can be kind of tricky.

As an added functionality to the S Pen, the Pen Window enables you to create floating application windows on your Samsung Galaxy Note 3—a tool that's extremely useful when it comes to multitasking.

If tradition holds, we're roughly one month away from Apple's big iPhone announcement. While we're excited to see what will mainly be a significant camera upgrade, it's not all about the hardware. Apple will also release the official version of iOS 13 to coincide with the iPhone XI. Before then, however, iOS 13 needs beta testing, and developer beta 6 just hit on August 7.