For new landscapes people tend to generally plant the new 'purple leaf plum' trees in a square shaped small plots. They also plant some small plants around it to make it look good. However when the tree grows older it needs to spread its roots. At that time these plants may try to hinder the trees roots growth. Therefore it is advisable remove them once the tree starts growing bigger. Then you can also add water to the roots by spreading it around the area of the tree.Whenever there is proble...

Do you wonder if what you are seeing on your trees or plants is a problem, or simply natural? John White and Lois Pierce discuss various issues with Manzanitas, Red Buds, Viburnums, Mexican Buckeyes, and Cacti.

First of all whenever there is low rainfall and higher heat then there are problems.You shall notice that there are brown colored needles which dry up and then drop of. Sometimes they start at the tip and then move towards the branch. This shows drought and you need to soak in lots of water to overcome. However if you notice the brown needles going from the middle to the tip then these are due to natural process. Another problem is the presence of spider mite. Take a white sheet of paper and ...

This easy to follow silent and accurate video will guide you quickly and easily through what you'll need, (like a Power Supply, a sound system that has a Subwoofer Pre-output and a High Input adapter, which may already come with your amp.) First learn what colored wires should be connected to simulate your PC starting. Then connect the amp to the power supply to simulate the car Head-Unit starting. Once the power issues are handled, the video assists you with connecting your audio input. It i...

Your IP address is what identifies your personal computer while you are online. You may want to change your IP address for privacy, to bypass website settings, to download, or for various other reasons. This tutorial will take you through the steps you need to start surfing more anonymously.

This feature also comes with Windows 7. Right click on desktop then click "Personalize". You can see the numbers of themes for example choose Nature theme and click "Desktop Background". You can see the some pictures and a tick mark on the corner of the pictures which tells these pictures are the part of my slide show. Also you can set the time for new pictures to come.

Circuit bending an audio device typically involves removing the rear panel of the device and connecting any two circuit locations with a "jumper" wire, sending current from one part of the circuit into another. Results are monitored through either the device's internal speaker or by connecting an amplifier to the speaker output. If an interesting effect is achieved, this connection would be marked for future reference or kept active by either soldering a new connection or bridging it with cro...

Cleaning House: This mission just might be the best one of all. Talk to Antonio, the head of the thieves guild and you'll at first get a cut scene and a memory sync, without having to do anything. Talk to him again, however, and you'll get a mission to identify and kill some traitors. The nearest traitor is in an area just north of you, so head toward the green area on your map.

Just like Apple and Google, Facebook has been working to develop computer vision shortcuts designed to give mobile apps augmented reality superpowers.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, Apple has added many new features to Safari, most of which have their own unique way of keeping you safe online.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

TouchWiz might not be the Android skin of choice for hardcore aficionados, but the Galaxy's OS still has a ton of great features up its sleeve that help provide one of the most enjoyable smartphone experiences out there. Many of these are relatively hidden and overlooked features that you may not be aware of.

Whether your palate runs to domestic or imported, a piece of cheese can be a real treat for the senses. Its smell, taste, and texture are all parts of its appeal. A big part of what makes that savory wonderfulness comes from the microbes in and on the cheese. Thanks to a team of researchers dedicated to studying those microbes, we have a better understanding of their importance to cheese and us.

With a death rate of one in five, sepsis is a fast-moving medical nightmare. New testing methods might improve your odds of survival if this infection ever hits you.

Intense exercise can cause problems with our digestive tract. It even has a name — "Exercise-induced Gastrointestinal Syndrome." Simply put, strenuous exercise can damage the gut and let the bacteria that reside there potentially pass into the bloodstream.

Fighting fire with fire, scientists are harnessing the adaptability of helpful microbes to challenge the adaptability of deadly microbes. What are we talking about? Hunting with phages — viruses that attack and kill bacteria.

As much as you try to safeguard your personal information, you may have made a small mistake by giving your phone number to the wrong entity, and now you're being bombarded with dozens of spam calls every day. To help parse your call log and reject the proper numbers without answering or trudging through voicemail, a good reverse phone lookup app is needed.

A sometimes serious disease spread by fleas is making inroads in Texas, quietly doubling case numbers since 2008, and beginning to encroach on larger metropolitan areas.

A recent pathogen outbreak in Illinois is just one of many outbreaks of an underappreciated, but serious, viral infection passed from rodents to humans. These hantaviruses have been cropping up more frequently in the last decade or so, giving us more reason to clean out our dusty attics, basements, and garages.

One thousand feet under the ground, extremophile microbes that have not seen the light of day for four million years are giving up some fascinating facts to scientists who go the distance.

This is a Q&A video with the question asking if glaze putty can be applied over primer or not. In this short Q&A video I am going to answer this question.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

Android uses a set of permissions that apps can request to perform certain actions, and you're notified of these permissions each time you install an app. The problem here is the fact that you aren't given any built-in way to deny apps these permissions (although Danny just showed a workaround for this).

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

Need to dry greens in a jiffy? When you are ready to make a fresh salad or sandwich, it is a pain to wait for them to dry. Avoid the mess off a salad spinner or a towel, and follow this quick tutorial.

When selecting a hairstyle for your face shape, identify if your face is square, oval, round or heart shaped, and then style hair and bangs accordingly. Shape hairstyles for each type of face using this free video from an experienced hairdresser.

Healthy drink recipes like these can can help you burn carbs, hydrate and make you feel great. Watch this how to video to learn how to make a simple yet flavorful water. It is very similar to the refreshing water offered at a spa. Add a cut up lemon and some refreshing peppermint to feel instantly relaxed.

Rubber bands are an ordinary, everyday, common household item, right? Their hidden in your desk, wrapped around your bills, holding your pencils together at the office, but what else can you do with rubber bands? What are some extraordinary uses? Woman's Day Magazine tells you how you can repurpose those rubber bands!

John White (Doña Ana County Extension Agent) talks to Natalie Goldberg (Extension Plant Pathologist) about Powdery Mildew that affects many plants. They look at a Japonica that is heavily infested. Powdery Mildew is enhanced by shaded condition despite the dry climate. It starts with a spot spore infection that will easily spread by the wind or by rubbing. Control methods are difficult and involves a lot of routine applications of chemicals (ornamental fungicide) to keep it in check once the ...

Some times malicious programs can infect your registry and fill it with lots of unwanted information. You may need to clean it to prevent the virus from causing any further damage to your computer or to even disable the virus. It is a very lengthy and complex process to do this manually. So you will need to use one of the powerful free tools available online. Hijack This is one of the most powerful program that can be used for this purpose. So go the website and download this free tool. Insta...

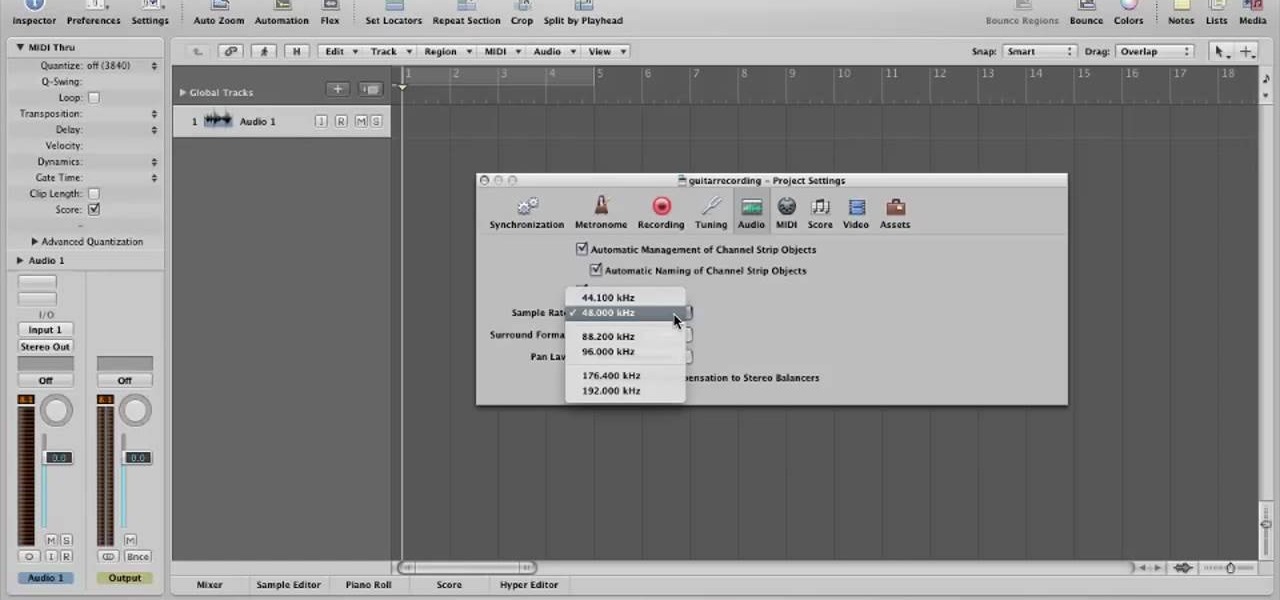
In this video, you will learn how to record using Apple Logic Pro 9. First, open the program and save the session. Make sure your audio interface is set before recording. Go to global settings and navigate to audio. Click on the general tab and change the audio settings. Wave files are the industry standard. Make sure 24-bit recording is checked. Software monitoring will allow you to monitor the audio. Save this and change the project settings. You can adjust the sample rate of your recording...

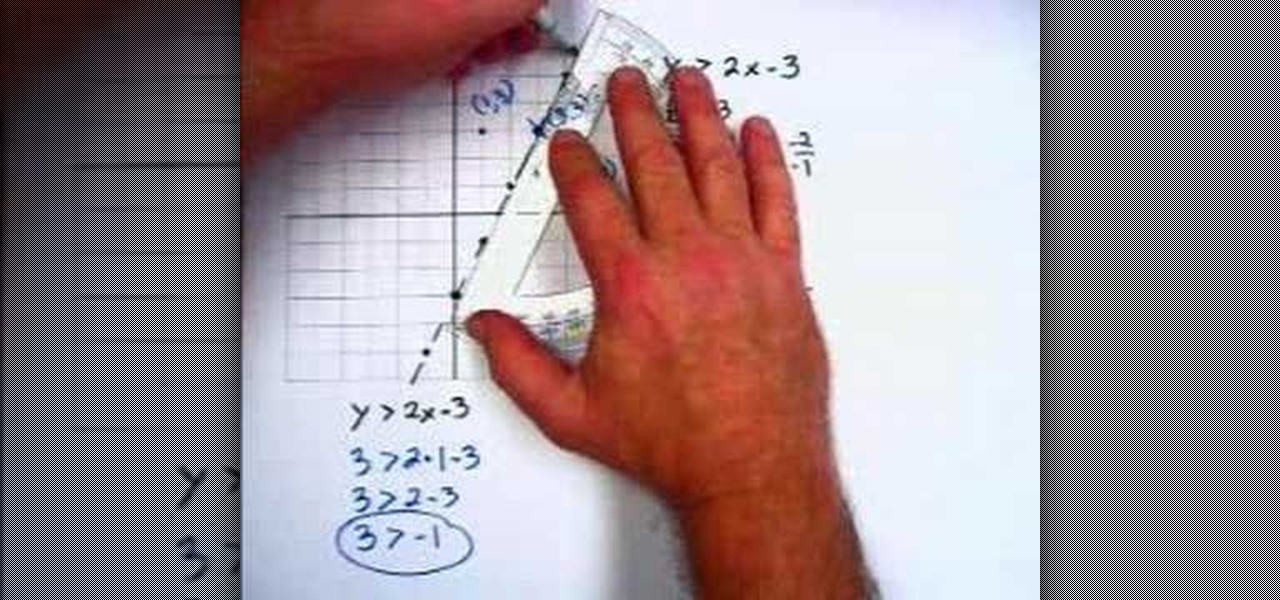
In this video the instructor shows how to graph linear inequalities. A linear in a equation is almost similar to a linear equation except for the sign in the equation. Now treat the in equation as a linear equation and graph the line. So substitute the lesser than or greater than symbol in the liner in equation with the equals to sign and graph the equation. Find the slope of the equation and identify the points that the line passes through. Now take a point on the either side of the pointed ...

The video deals with a clear step by step process of making a plastic airplane. He asked us to select the model of the airplane we are going to make first. He has selected the North American F86A SABRE model in this demo.

This video shows the method to change a word problem into algebra and to identify rational numbers among a group of numbers. In the first part of the video we take a word problem namely - The product of 9 and seven, less than a number. 9 multiplied by something can be expressed as 9(). The unknown number can be expressed as 'x'. Seven less than a number can be expressed as x - 7, so that the final equation becomes 9(x - 7). In the second part we are given a list of numbers. A rational number ...