Since the 1960s, bacteria have been hopping a ride into space on space vehicles and astronauts, and have been cultivated within experiments on space shuttles and the International Space Station (ISS). The extreme growing conditions and the low gravity environment on the Earth-orbiting vehicles offers a stable research platform for looking at bacteria in a different light.
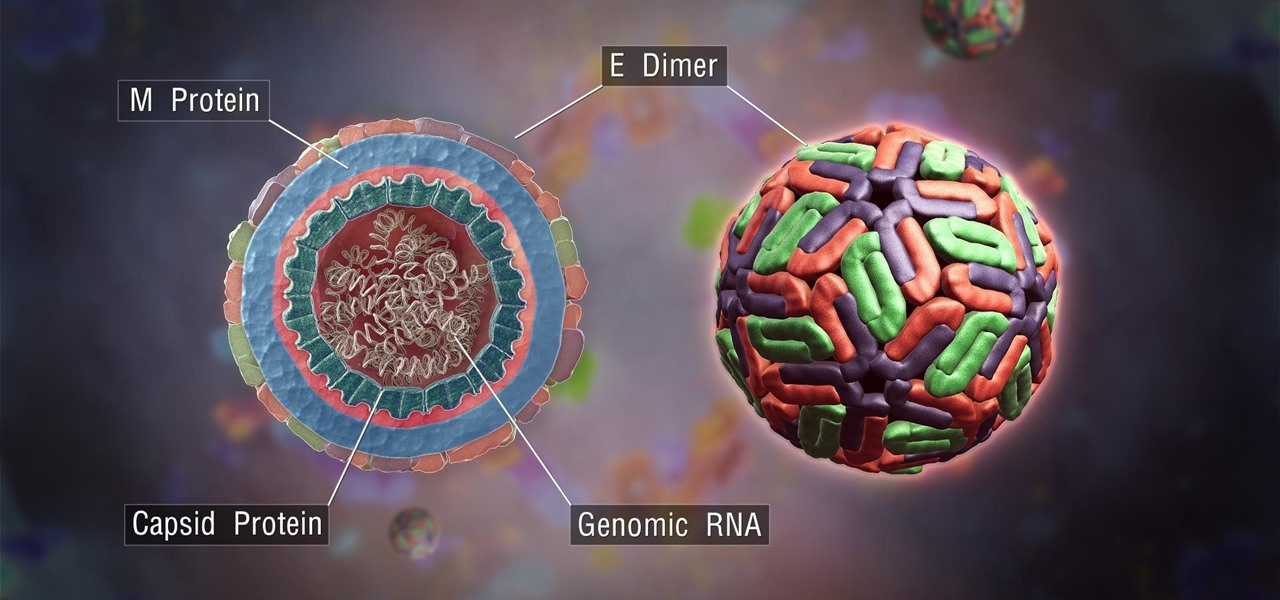
The mention of Zika can strike fear in the hearts of pregnant women. With infections increasing around the world, including in the US, researchers are fighting the clock to figure out how the virus can have such horrific effects in some people.

For some time now, there has been quite a bit of speculation as to when the selection of augmented and mixed reality head-mounted displays would begin to trickle out to the public. Pricing, availability, and software selection are all issues that will have to be addressed before widespread adoption will start.
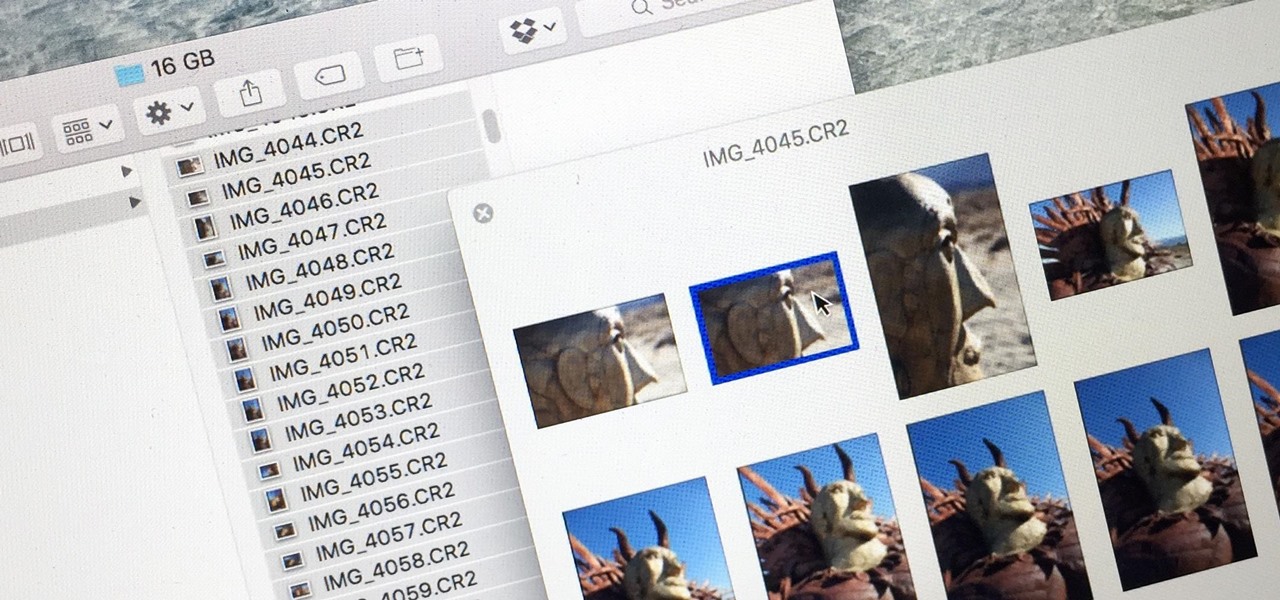
Quick Look, first introduced in 2007, is an instant preview feature on the Mac operating system that lets you view files and folders without opening them up. Just highlight a file, like a picture or text document, then press the spacebar on your keyboard to get a speedy preview of it.

With the weather warming up and the days getting longer, fruit salads are starting to appear at backyard BBQs, beach picnics, and pretty much everywhere else. Often these sweet side dishes are unremarkable, with each colorful bowl blending into the next. Luckily, there are easy ways to spice up your fruit salads so that everyone will still be talking about them next summer.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

I grew up eating Korean, Japanese, and Chinese food, but it wasn't until college that I experienced Thai and Vietnamese cooking. Once I started, I couldn't get enough of these cuisines. The dishes had an incredible richness and savor that I couldn't identify, but whatever it was, it made me want to keep eating.

One thing I absolutely cannot stand is lag when I'm gaming. Every time I'm about to beat my killstreak record on Call of Duty, my internet connection drops and I'm a goner. It never fails. This usually happens because someone else on my Wi-Fi is streaming a movie or downloading a huge file.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

There are a number of reasons why you might want to trick a web server into thinking you're on a different operating system (OS) or web browser. One might be that you want to test the mobile version of your website from your computer. Or perhaps for some reason a website is restricted to a certain OS or browser and you wish to circumnavigate that barrier. Today's guide shows you how to do just that!

Cross-dressing and gender-bending are nothing new, but the realm of Steampunk seems to be especially accepting of role-reversal in dress.

To calm our 8 week old baby Logan, the hair dryer is the foolproof white noise machine. Baby quiets down instantly. (But if he is hungry, then nothing works but milk.)

Ever need ice right away but do not have time to run to the store? Here is an easy way to make water turn into ice instantly. Using a few common household products, produce ice from water in the matter of seconds and enjoy a nice tall glass of a chilled beverage.

Researchers have found that there are simple things anyone can do to appear more appealing. You Will Need

This video demonstrates how to use a Nikon SD-80 Battery Pack with a Nikon SB-800 Speedlight. The first step is to identify the different power adaptors on the ends of the cable leading to the battery pack. This pack is powered with AA batteries. Remove the outlet plate on the SD-80 and insert the power cable into the SB-800 Speedlight. Then attach the communication cord to the Speedlight. Now place the Speedlight in the hotshoe of the Nikon camera and let the battery pack dangle or attach it...

You can get an expensive ticket for driving with a busted tail light. But that's not all. Driving with a faulty brake light can be dangerous. Replacing the bulb is a simple task that takes only a few minutes.

Are you a magician on a budget? Impressive feats of magic don't require an assistant to saw in half, or even a rabbit to pull out of a hat. You need only the slightest sleight-of-hand to perform this impressive magic staple.

Organic fertilizer is based of natural occurring compounds instead of chemical based compounds. With healthy, natural soil, learn how your plants and the environment can thrive in this free gardening video series about how to use organic fertilizers on plants. The following clips illustrate:

Learn how to treat a fever, how to identify the symptoms, how to avoid getting a fever and how to deal with one comfortably with expert medical tips from a trained doctor in this free health care video series.

Box turtles can be found in many places and make great pets. Learn more about identifying box turtles, including different types of box turtles in this free pet care video.

Whenever you design elements for your garden, you should always keep in mind, that the more natural they are the better they seem to fit in. That's exactly what is done when you create this rustic bent wood trellis. But others have taken this idea a step further. In this how to video, Jim Long, author of the book Making Bentwood Arbors and Trellises, explains how to create these artistic garden ornaments.

In this video series, Nick and Valerie Wisniewski show you how to identify different animals like bears, beavers, bobcats, deer, rabbits, foxes and more, in the wild.

Since Shazam became available on iPhone, it's been easier than ever to identify a song playing somewhere in the background. You could hear something you like while watching a movie or sitting in a coffee shop, and all you have to do is open the Shazam app and have it listen for you. But what about music playing on your iPhone via Instagram, TikTok, and other social media apps?

The increasingly important world of white hat or "ethical" hacking is getting competitive. Thanks to growing salaries and opportunities for talented and trained coding pros who can infiltrate servers and safeguard networks against digital threats, demand for intrepid cyber warriors is through the roof, and it shows no signs of slowing down any time soon.

The COVID-19 pandemic has hit everyone hard. With over 36 million American workers filing unemployment claims, finances are at the front of everyone's mind. Understanding your accounts has never been as important.

SEO is the name of the game. If you want your business or brand to succeed, ranking on the front page of Google is a boon. Getting to the front page of search engines takes work, but it's not impossible when you master SEO best practices.

There are countless ways in which a talented and trained programmer and tech pro can earn a lucrative living in an increasingly data-driven age — from writing and creating apps and games to working for a cybersecurity firm or even the federal government.

Few things are more important than search engine optimization when it comes to increasing a brand's visibility online. Regardless of whether you're launching a new business from scratch or working as a marketing professional at a major corporation, you need to ensure that you're drawing the most people to your website and affiliate links by utilizing the latest and most powerful SEO tools and methods.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

After jumping to the head of the class of augmented reality journalism in 2019, USA Today is continuing to push the medium forward in 2020.

Songs new and old are given a fresh purpose through the TikTok meme machine, but it can be tricky to figure out where a track originally comes from. Sure, you can tap the name of the song to see the source on TikTok, but if it were a snippet uploaded by someone other than the track's creator, the song title likely wouldn't be listed. Luckily, there is an easy way to figure it out.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

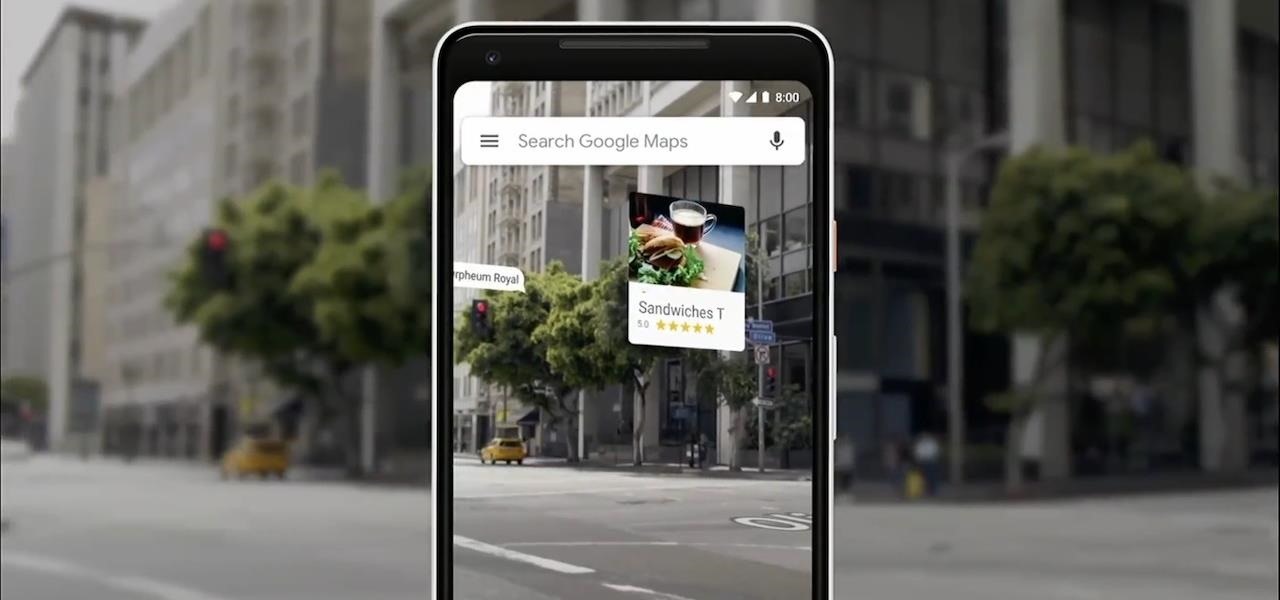
The augmented reality walking navigation mode for Google Maps appears to be closer to an upcoming release for the general public.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

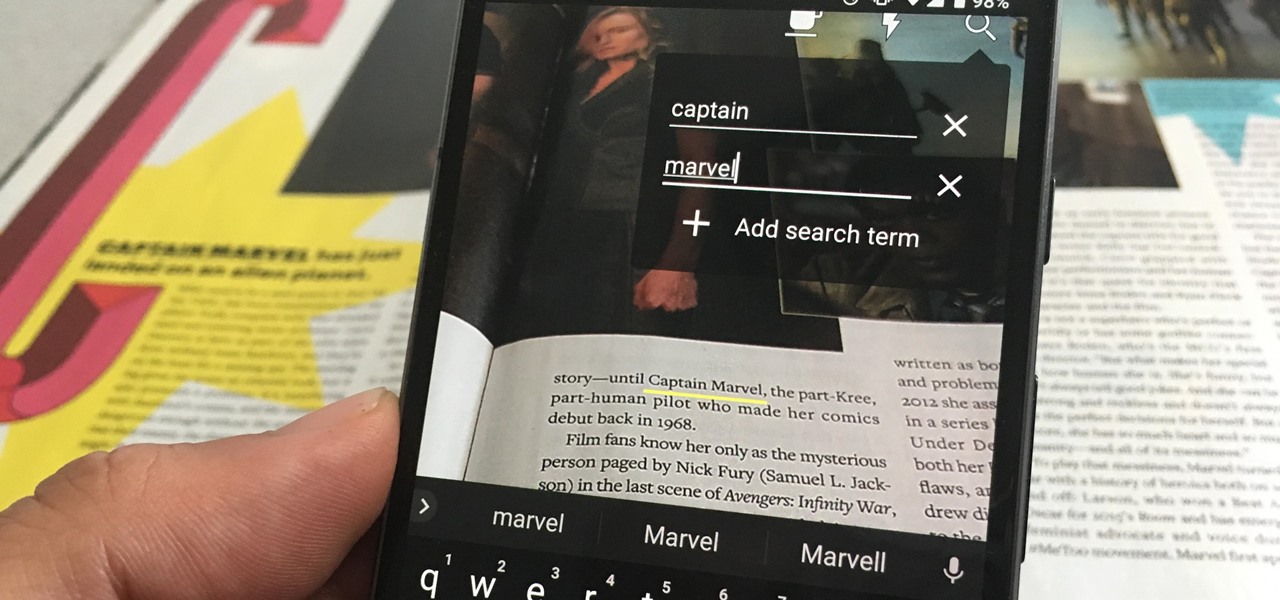
Safari has a convenient "Find" feature to search for specific words and phrases in a webpage, and Apple Books has a similar feature for e-books and PDFs. But those do nothing for you when searching text in the real world. Hardcover and paperback books are still very much a thing, as well as paper-based documents, and finding what you need is as simple as pointing your iPhone's camera at the page.

One of the neatest tricks available in Google Lens, an app that can identify and interpret real world information, is the ability to copy text from the app's camera view and paste it into a digital document.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

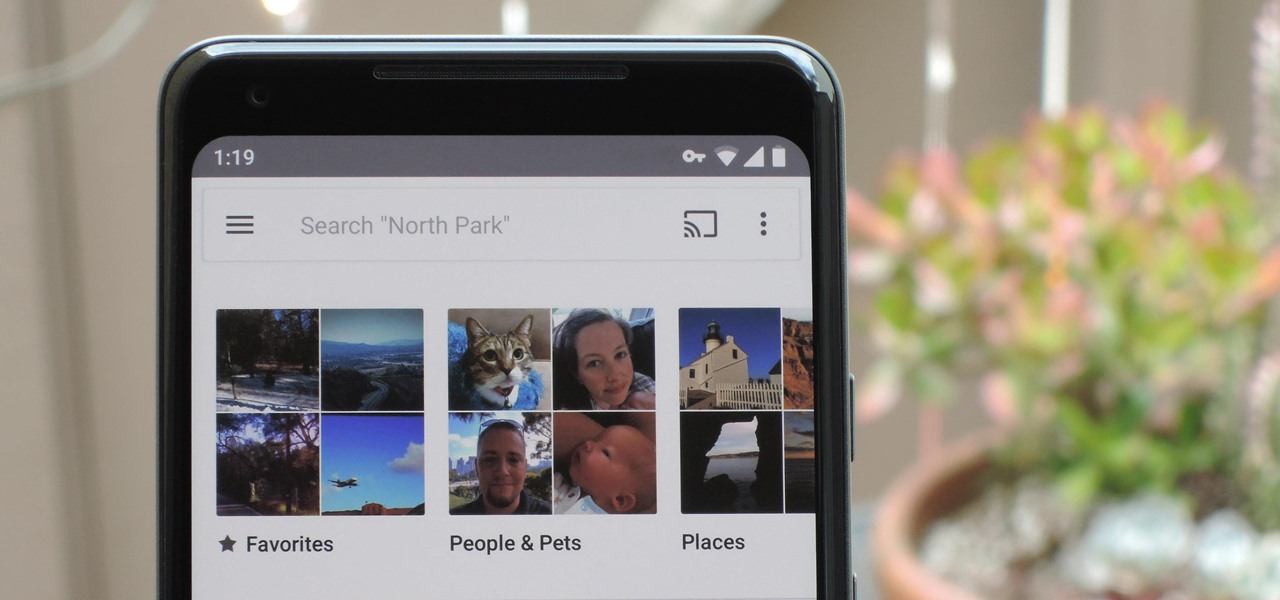
Google Photos is a fantastic service, giving you unlimited storage on either your Android or iPhone. With all this free space, some pictures can get lost in the shuffle. Fortunately, Google will now let users "Favorite" pictures — whereupon they're automatically put in their own standalone album.