Not every nurse can get an IV every time, that's why it's important to stay in practice for the proper technique used for inserting a peripheral IV. This is a common medical procedure that all fields related to medicine should know. Even the soldiers in the military are taught how to insert an IV — every soldiers, not just the medics.

One of the hardest things a man can go through in life is a trip to the hospital, especially when he knows he's going to need a catheter. It's every man's worst fear. But for a nurse, it's necessary knowledge. Learning the male urinary catheterization procedure hands-on is difficult due to the urgency involved in patient care, so this video aims to prepare nurses so they can learn and stay fluent with the proper urinary catheterization technique of a male patient.

In many situations, learning proper medical procedures is difficult due to the urgency involved in patient care, so this video aims to prepare nurses so they can learn and stay fluent with the proper urinary catheterization of a female patient.

Second Class Boy Scouts work on building their outdoor survival and camping skills. Compass work, nature observation, camp tools, and swimming are areas where new skills are mastered and demonstrated. A second class scout, having completed all the requirements, should be able to lead a hike, care for his own equipment, set up a campsite, and perform basic first aid.

In this installment of the online prank video institution Do Unto Others, you will learn a wide variety of great ways to mess with people in a variety of situations. Some of these situations include at a job interview, at the gym, when meeting a new roommate, and when using a public restroom. All are sure to add a little spark and concern to your fellows' day.

Are you going INSANE cause you don't have a costume yet for Halloween? Worry no more, because this video tutorial from Thread Banger, Rob shows us a crazy tutorial on how to make your very own straitjacket.

In Wisconsin, is there any burger topping more appropriate than a liberal dollop of butter? Travel with Hamburger America to Glendale institution Solly's Grille, located just next to the Milwaukee Heart Hospital. The Grille' calls its hamburgers the "butter burger".

In order to find out if an email is a scam, you should avoid clicking on any links in that are in any emails. The links that are attached to emails, in this manner, usually have cloned the website of the institution where you do your banking. The link will look similar to your banking institutions site. Do not enter any of your personal information in emails in this fashion. Your bank will not contact you in this way.

Check out this video tutorial to see how to tansfer blood specimens with the BD Blood Transfer Device.

Just got piad? Turn your check into dollar bills by endorsing it at the bank. Don't know how? Watch this.

Check out this video to see how to collect blood with the BD Vacutainer Eclipse Blood Collection Needle.

Welcome back, my rookie hackers!

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Has you rent check bounced again for no apparent reason? It happens to everyone, but if you're roommate needs the money fast, you need to fix it fast, and wire transfers are the fastest way to give money to someone else. Executing a wire transfer is as easy as making one phone call.

Roughly half of all Americans believe in extra sensory perception... Are you part of that statistic? Ever get the feeling you have a paranormal ability? You can investigate your psychic abilities and hone your skills with these tips.

BD Quikheel Safety Lancet The BD Quikheel Lancet is a safety-engineered product designed for heel sticks on infants and premature babies. It features a sweeping surgical blade that permanently retracts after creating an incision. Additionally, it offers a tapered window providing the healthcare worker with the ability to accurately position the lancet.

Check out this video tutorial to see how to use the BD Genie Safety Lancet blood sampler device. BD Genie Lancets are high quality, safety-engineered, single-use capillary blood sampling devices. They offer a permanently retractable blade or needle feature that minimizes the possibility of injury or reuse. BD offers a full range of blade depth and needle gauges for sufficient blood volume in multiple sample requirements. All Genie's can be used in conjunction with BD Microtainer Tubes.

Check out this video tutorial to see how to collect blood with the BD Vacutainer Safety-Lok Blood Collection Set.

American Horror Story might just be the craziest TV shows out there, with its absurd plot twists, creepy, over-the-top characters, and wicked storyline. It's gained a cult following ever since the first season, Murder House, and has even earned some Emmys along the way.

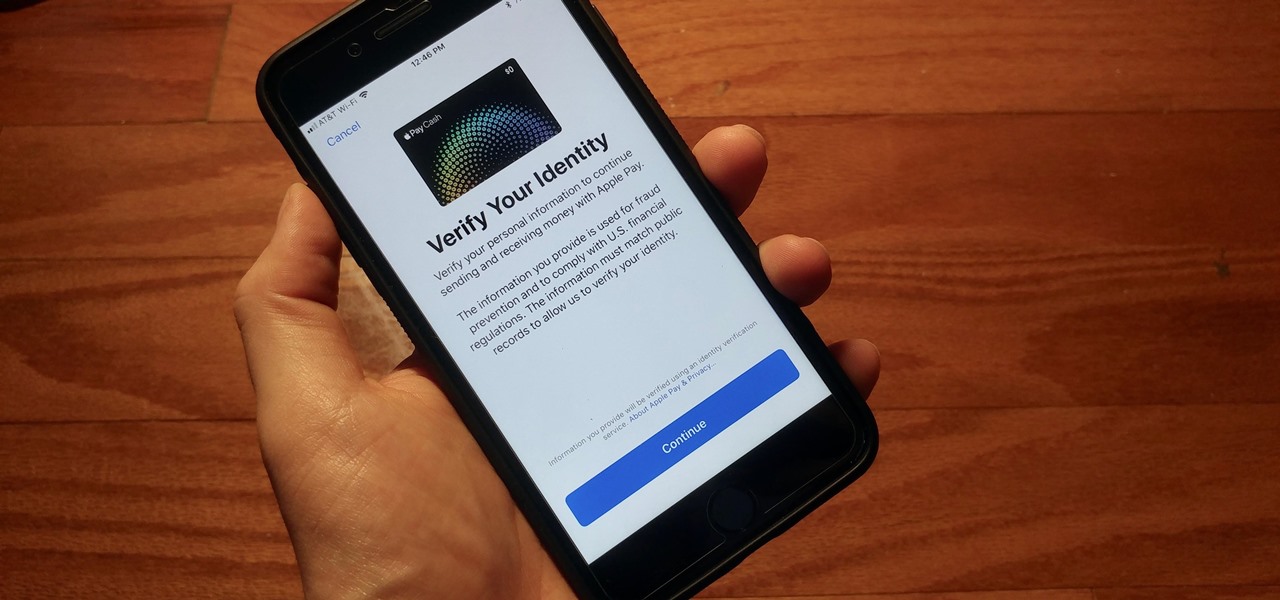
With iOS 11.2's introduction of Apple Pay Cash, you can send and receive money to others directly through iMessage, using the convenience and security Apple Pay is known for. However, if you want to make sure your efforts go uninterrupted, you'll want to make sure you verify your identity with Apple.

Traditional media institution The New York Times continues to break new ground in its augmented reality news coverage, this time with a 3D volumetric capture of model Ashley Graham.

The HoloLens is a natural medium for 3D data visualization, which offers a far more ideal approach over 2D screens to managing multiple resources simultaneously and grasping the bigger picture. We've already seen how management is using holograms to oversee cities, firefighters, and the military, and now training for sports teams is being addressed with VAR Football.

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

Ethical hacking is a useful skill that can make you stand out in the field of cybersecurity. Whether you're just entering the field or are already established and are looking to stay current, learning the fundamentals of the white hat is an essential skill for your professional development.

Media subscriptions are all the rage these days. Between Netflix, Apple Music, HBO Now, and countless more, your TV, movie, and music options have never been better. Unfortunately, all these choices weigh heavily on your wallet. So, when there's an opportunity to snag not just Spotify but Hulu and Showtime as well, all for just a tad bit over five dollars a month, how could you turn that down?

We've worked hard to reduce the flow of toxic chemicals into our waterways, which means no more DDT and other bad actors to pollute or destroy wildlife and our health. But one observation has been plaguing scientists for decades: Why are large quantities of one toxic chemical still found in the world's oceans?

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

Many home cooks were taught never to press down on a burger as it cooks since that would ruin your all-beef patty by getting it to release the juices it needs to stay tender and moist.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

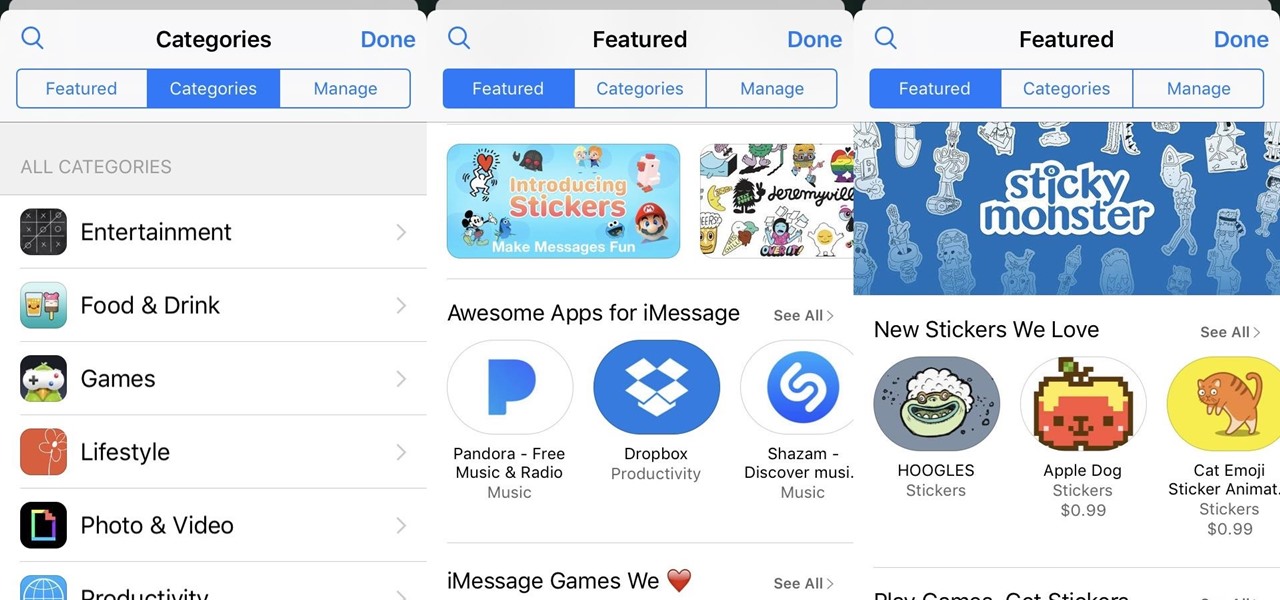
The latest update to iOS 10 brought with it a number of great new features. Of these, the one that will likely have the most impact on people's iOS experience in the long term are the new apps and stickers for iMessage.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

OSAGYEFO DR. KWAME NKRUMAH (1909-72) Founder and Father of the Nation Osagyefo Dr. Kwame Nkrumah, the first Prime Minister and President of Ghana, stands out not only among the Big Six but also among the greatest statesmen of history. It was he who canalized the discontent of the people of the Gold Coast Colony into the highly organized movement of protest against British rule, and within a relatively short period won political independence for Ghana on March 6, 1957. With Ghana independent, ...

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

At a global security conference in Munich, philanthropist and businessman Bill Gates spoke about the next pandemic and a dire lack of global readiness. Here's how his statement could come true—and how to be ready when it does.

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.