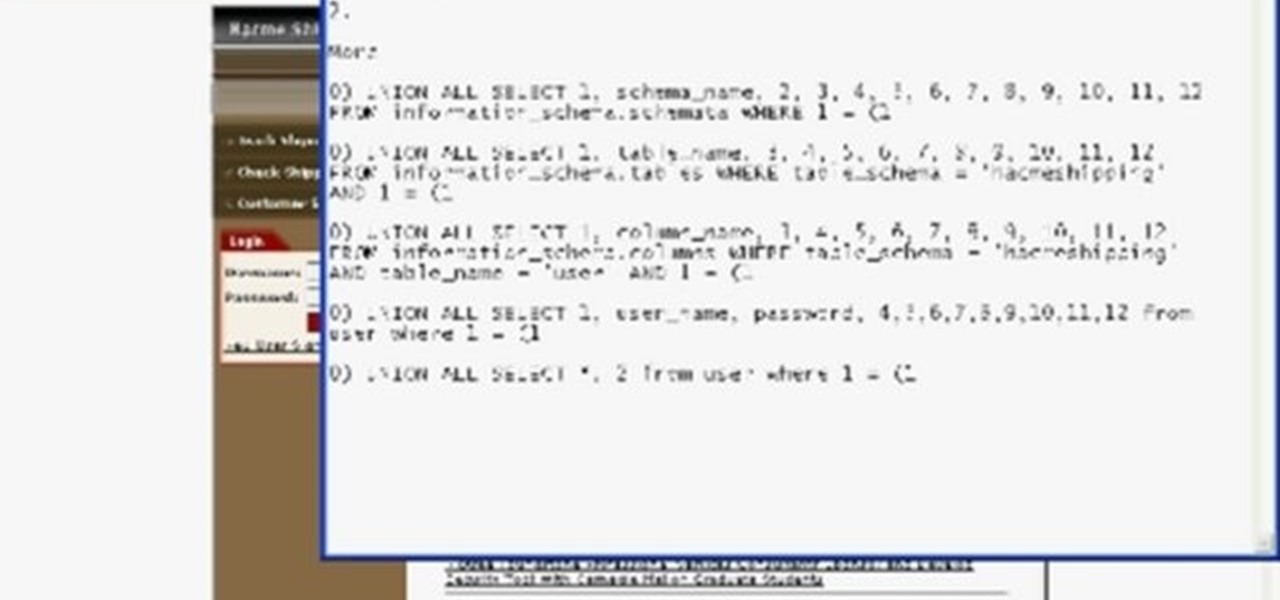
Foundstone Hacme Shipping is a web-based shipping application developed by Foundstone to demonstrate common web application hacking techniques such as SQL Injection, Cross Site Scripting and Escalation of Privileges as well as Authentication and Authorization flaws and how they are manifested in the code. Written in ColdFusion MX 7 using the Model-Glue framework and a MySQL database, the application emulates the on-line services provided by major shipping companies. This video will get you st...

As many as 700 species of bacteria live on our teeth and in our mouth, and just like the microbiomes inhabiting other parts of our bodies, they change in response to diseases and other health conditions.

Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.

In most collectible trading card games players fail to realize the value of low-level creatures. They aren't sexy, but they can win you games when used correctly. This video will teach you how to build a Yu-Gi-Oh! based on three stars or less creatures that is still pretty damn effective.

In this video, we learn how to make pork shoulder barbecue. First, heat up the grill with charcoal until it's hot all over. After this, prepare your pork shoulder by placing the entire piece of meat into a brine. If the liquid is saltier than the meat itself, it will cause the meat liquid to draw into the meat. After this, inject the meat with flavors that you like. The pork shoulder is many muscles, so you have to make sure to poke the injection into several of the right spots. When you're d...

In this video Dr. Schultz will show you how to control extreme underarm sweating. If you suffer from extreme underarm sweating, despite regular use of antiperspirants, follow these steps: Make an appointment with your doctor so that they can give you a prescription for a topical antiperspirant called Drysol. This liquid is applied once a week, at bedtime, and is covered with cling wrap. After a few weeks you will see a significant reduction in the amount of underarm perspiration you experienc...

One day, your car may break down and you won't be able to afford to hire a mechanic, so what do you do... you look on the web for some how-to vehicle repair videos and become your own car mechanic, that's what. You don't need any advanced training to perform repairs and simple maintenance on your automobile, but you may need a few tools. Invest in the basic tools and you'll be prepared for just about any car malfunction you can think of. These tutorials will help get you on your way, as long ...

Purple and gold make for an eye catching color combo in the eye look in this how-to video. The cosmetics used by the demonstrator are: MUFE HD Foundation #110, MAC - Select Cover Concealer, MUFE HD Powder, Bare Essentials - Thistle Blusher, Bare Essentials - Heaven Blusher, Stila - Starlight Shadow, UDPP, MAC - Royal Hue Shadestick, MAC - Shadowy Lady, MAC - Noctournelle, MAC - Beauty Marked, Cargo - Toronto e/s, Bare Essentials - True Gold Pigment, Tarte - EmphasEYEs in Black, Two Faced - La...

This makeup how-to video shows a fast way to do the classic smoky eye, but designed for Asian monolid eyes, or any eyes with small or undefined creases. The cosmetic products used to create this look are a Black Pencil eyeliner, L'Oreal in Lush Raven (MAC 217), NYX in Latte Foam (MAC 224), Lancome in Daylight, Shiseido Mascara Base, Too Faced Lash Injection, and Maybelline Define a Lash Mascara. Watch this video makeup application tutorial and learn how to apply a quick and easy smoky eye mak...

This makeup tutorial teaches you how to apply makeup inspired by the astrological sign Sagittarius. The products used for this loook are Too Faced Shadow Insurance, MAC Nude cream color base, Urban Decay Peace eyeshadow on inner lid, MAC Sea & Sky Mineralized eyeshadow: dark blue on outer corner, light blue as inner highlight, Makeup Forever #92 Shadow in crease and under eyes, Too Faced Lash injection mascara, and MAC Missy Slimshine. With this how to video you will be able to re-create this...

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

It seems like people are always trying to lose weight..but what if you have the opposite problem? Whether you’re recovering from an illness, are a growing teen, or you are an athlete trying to bulk up, a little information can go a long way in helping you pack on a few extra pounds.

SQL injection is a type of code injection that takes advantage of security vulnerability at the database level. It's certainly not the easiest form of hacking, but if you're serious about turning a website upside down then this is the way to do it.

Suffering from acne scars that are as noticeable as the pimples that caused them? You can find an effective acne scar treatment, from laser resurfacing to collagen injections. Here, the skin care and scar removal you may discuss with your dermatologist.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

Dirty, malformed, and outright mischievous text strings have long been the enemy of interactive website developers. Strings contain any combination of letters, numbers, spaces, and punctuation, and are entered into text boxes on websites by users. These strings in particular can do everything from highlighting XSS vulnerabilities to soliciting 404 error pages.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Injecting intramuscularly is a difficult thing to learn and it takes a lot of practice. This instructional medical how to video guides your through the step by step process of selecting a site for an intramuscular injection. Intramuscular injections should be given in areas where major blood vessels and nerves are avoided. Watch and read along. It is important to wash your hands before handling any injection material.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

Popular Mechanics' Senior Auto Editor Mike Allen shows you how to safely stop your car if you become the victim of sudden unintended acceleration.

Acne develops when pores become blocked with dead skin cells and oil. They usually disappear over time but sometimes they leave a scar. When those blemishes form white blood cells rush to the surface to help heal the area. But occasionally a scar forms. Popping and picking can send bacteria further into the skin and increase the blemish and it greatly increases the likelihood that a scar will appear. Nodules and cysts are more severe blemishes and have an increased likelihood of leaving scars...

Watch this video tutorial from the Polish Guy to see how to polish a stainless steel roller using Autosol. In this polishing tip we polish a stainless steel roller using Autosol Metal Polish. The tutorial includes detailed work instructions and best practices.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

Several recent research studies have pointed to the importance of the microbes that live in our gut to many aspects of our health. A recent finding shows how bacteria that penetrate the mucus lining of the colon could play a significant role in diabetes.

Creamer, milk (whole or skim), sugar, or even butter—you've probably added at least one of these to your coffee to improve its taste at some point. If you're looking for something different, though, try a new twist with a dash of cinnamon. This sweet, sharp spice can do so much more than improve coffee's taste, and I've got 10 examples for you to consider.

Injecting intramuscularly is a difficult thing to learn and it takes a lot of practice. This instructional medical how to video guides your through the step by step process of giving an intramuscular injection. Watch and read along. It is important to wash your hands before handling any injection material.

Injecting intramuscularly is a difficult thing to learn and it takes a lot of practice. This instructional medical how to video guides your through the step by step process of drawing up a substance for an intramuscular injection. Watch and read along. It is important to wash your hands before handling any injection material.

Bone loss and belly fat may no longer be certain fates of menopause, thanks to new research from an international team of scientists.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

A new medical development is going to change the way many of us look at getting the flu vaccine. A painless flu vaccine skin patch is making needles and vials a thing of the past. Researchers from the Georgia Institute of Technology and Emory University have shown that a flu vaccine can be administered safely and comfortably with this new patch, which delivers the vaccine through a matrix of tiny dissolving microneedles.

It's about time people acknowledged that judging drug users would do nothing productive to help them. In the US this week, two new programs are launching that should help addicts be a little safer: Walgreens Healthcare Clinic will begin offering to test for HIV and hepatitis C next week, and Las Vegas is set to introduce clean syringe vending machines to stop infections from dirty needles.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

The setting of this video is at a restaurant that was once a Czechoslovakian social club that was turned into an award winning barbecue restaurant called Honky Tonk Barbecue.

Get your grout floors looking brand new again! With this tutorial, you'll learn how to remove stains that tend to form on grout.

The Hyco cold vaporizer. This is a cold vapor unit which can give 50-80 % fuel mileage plus, if done to the instructions on the video.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.









































