
How To: Feel Alive Again with Maca Root
I'm sure I'm not the only one on here that has googled "Why am I always tired?"... and I'm definitely not alone when I say that all of the advice I've found so far is useless:


I'm sure I'm not the only one on here that has googled "Why am I always tired?"... and I'm definitely not alone when I say that all of the advice I've found so far is useless:
Smartphones have been around for nearly a decade now, so we've had plenty of time to develop preconceptions and bias. People that have never owned an iPhone will tell you that Apple devices are restrictive and bland, while others might say that stock Android is boring compared to manufacturer skins like HTC's Sense, despite never having owned a Nexus or Pixel.

The magic of an ice cold popsicle on a hot summer's day is undeniable, whether you're a child or a kid-at-heart. Neon-colored, store-bought popsicles may have a special place in your memory, but homemade popsicles are pretty hard to beat. Here's how to create delicious frozen treats that will both delight your inner child and tickle your adult taste buds!

Often, the most frustrating part of crafting the perfect dinner is feeling like you have to clean every single pot and pan in your kitchen after cooking just one meal. With so many components, it can feel like each step of a single dish requires its very own pot.

Though the word "pie" may conjure up images of a dessert made of dough with various fillings, the famous Frito Pie is, in fact, something of an entirely different nature. Absurdly simple in its construction, this pile of Fritos and chili is served in the actual chip bag and more closely resembles nachos than it does a traditional pie.

No summer season would be complete without potato salad, an essential side dish. The flavors and textures of a simple potato salad can be totally satisfying as is, but add in a few items and you can have a dish that is absolutely extraordinary.

This is a Q&A video with the question asking if glaze putty can be applied over primer or not. In this short Q&A video I am going to answer this question.

We love standing around a barbecue with an icy cold beverage in hand, enjoying the delicious smell of smoky food and chit-chatting with pals. Grilling season — it's our favorite time of the year.

The original frozen hot chocolate is from Serendipity 3, an extremely famous eatery in NYC. However, its fame had created many copycat recipes, which eventually prompted its owner, Stephen Bruce, into releasing the delicious recipe in 2004.

Desserts always taste better when they are sugar-coated—and even more so when they're coated in powdered sugar. In particular, crinkle cookies—cake-y cookies that are chewy on the inside and crispy on the outside—are famous for the powdered sugar that creates their cracked appearance.

It seems like everything old is new again these days where food is concerned, and that includes the recent renaissance of babka. The name of this rich, rolled yeast bread, with roots in both the Jewish and non-Semitic Eastern European communities, means "little grandmother" in Ukrainian, Russian, and Yiddish.

My Cuisinart ice cream maker was a wedding gift; it wasn't something on my list, but I jumped up and down with delight when I unwrapped it. I never would've purchased this appliance on my own because it didn't seem practical, yet I loved the idea of making homemade ice cream.

Whatever you want to call it for now—Android Nutella, Android Nougat, or Android 7.0—the upcoming "N" release of Android will surely bring in tons of new features and functionality. We know it will be named after a dessert, and we know that Google uses an alphabetical naming system, so something starting with "N" is next in line after Android 6.0 Marshmallow.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

My father never cooked a meat without some kind of marinade. He always used a slew of ingredients: salt, pepper, Season-All, Cajun seasoning, vinegar, olive oil, liquid smoke, Worcestershire, hot sauce, onions, lemons... I'm pretty sure this isn't a complete list, but I've honestly forgotten the rest! It always tasted amazing, but the long list of ingredients was definitely a detriment whenever replicating the marinade.

While most of your iPhone's features are intuitive or well-covered across the web, there are some features hidden deep within iOS that you probably never even knew about. (These could also apply to an iPad or iPod touch.)

Depending on your child's age, their first smartphone may be a little too open for them, or you, to handle. With essentially a world of information—both good and bad—available at their fingertips, it can seem like a huge hurdle to instill parental controls on their device.
We recently lost Grooveshark, the free music streaming service that supplied users with a huge catalog of free music anytime, anywhere. Since its shutdown, I have been scrambling to find a half-decent alternative, and my expectations were more than exceeded when I found NetEase Music.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

While I frown upon any form of uneaten cookie, sometimes we overestimate our late-night cravings for baked goods leaving us with extra cookie dough at 4 a.m. If you're in the privileged dilemma of not having enough excess dough to make another batch of cookies but just enough left over that you can't justify tossing it, don't fret. Here are five effortless and unexpected ways to salvage it.

Due to the way Android works, you normally need to be rooted to uninstall the pre-loaded system apps, aka bloatware, that came with your device. This is because the underlying files for these apps are stored on your system partition, which can only be modified with root-level access.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

There's nothing more jarring than the sound of your morning alarm. Even hearing it on others' phones, hours after your own abrupt wakeup, can cause you to flinch in fear. Though we depend on that shrill sound to get up each morning, it's actually better to wake up naturally—so don't even think about hitting that snooze button.

A little cooking mistake can lead to tough meat, spoiled food, and even a bacterial explosion in your kitchen if you're not careful. These five simple, easy-to-fix kitchen mistakes are some of the most commonly made in households around the world. Luckily, you can correct these innocent errors with just a few minor tweaks.
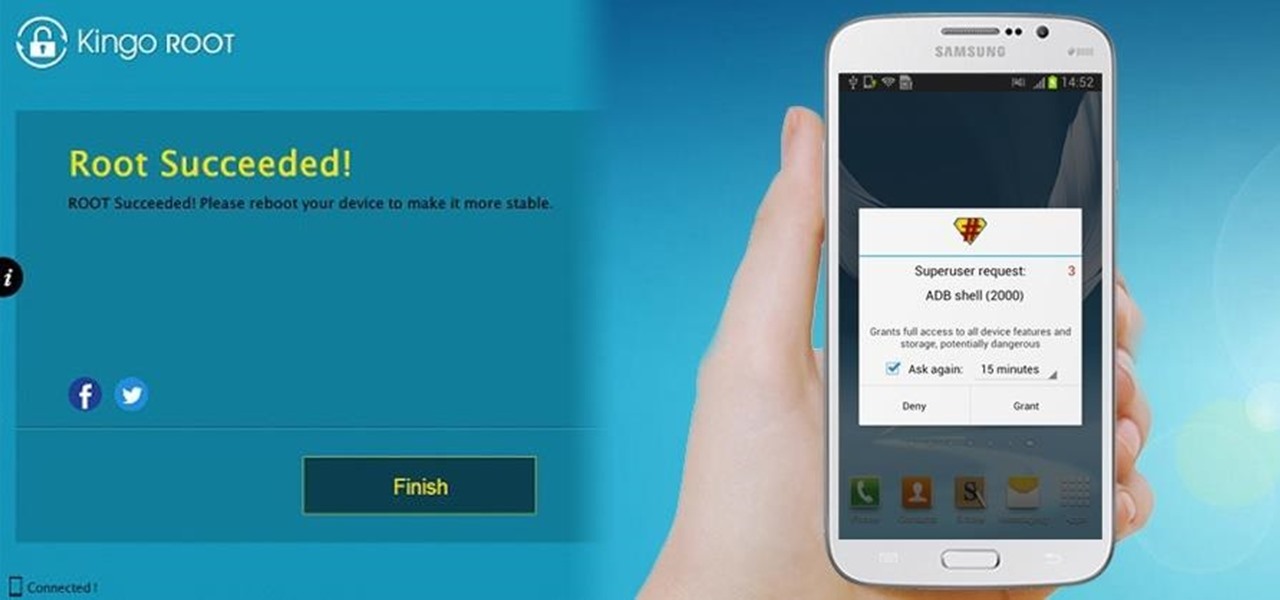
To Android users, especially advanced ones, rooting their phones or tablets is becoming a necessity. Rooting Android could be complicated, if you do it all by yourself, even with a step-by-step tutorial. However, what Kingo Android Root offers you is a true one-click experience when rooting your Android.

Before Apple jumped into the phablet game with their iPhone 6 Plus, there was the Samsung Galaxy Note series. Initially knocked for their size, the Notes slowly but surely gained popularity, thanks to powerful hardware, incredible displays, extensive features, great battery life, and a surprisingly-useful stylus.

I am an English major physically allergic to all algebraic formulas, so you're unlikely to get any help from me when it comes to solving any expressions. But in the glorious technological age we live in, there are plenty of apps that actually make math and problem solving fun, even a little bit addictive.

Without a comprehensive root method for all Android phones and tablets, a device-specific approach is needed. And since we always cover new rooting methods for all the popular phones here at Gadget Hacks, we've built this always-updated guide to rooting many mainstream Android devices.

Android's permissions system is simple, transparent, and straightforward. When installing an app, you get a chance to review all of the permissions that the app has requested. These can range from accessing your location data to holding a "wakelock" in order to prevent your phone from entering sleep mode. But your only choice in this matter is to accept all requested permissions, or not install the app.
Fifty-four percent of Americans 18 and older drink coffee every day, and why not? With 100 milligrams of caffeine per six ounces of drip coffee, it's just the morning beverage to wake you up and kickstart your day. You can feel the caffeine surge through your body like the Holy Ghost, making you aware, focused, and ready for action.

Many people drink green tea for health reasons, and it's no wonder. This beverage is a superstar when it comes to antioxidant levels, and is being studied for its potentially curative properties on multiple health concerns, whether it's staving off the aging process or fighting cancer.

Android enthusiasts have their own opinion as to whether you need antivirus software on an Android device. This debate will never end, provided that Android malware is in existence. This guide is not here to say, "Yes, you need antivirus," or "No, you don't." It's to give you all the facts, so that you can make a decision as to whether or not you need antivirus on your Nexus.

It's a small but very real frustration: you want a chilled drink, but you open the freezer only to see nothing but empty ice trays. Fortunately, there's a simple way to make ice cubes quickly—use hot water. Yup, you read that correctly. Hot water freezes more rapidly than cold.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"
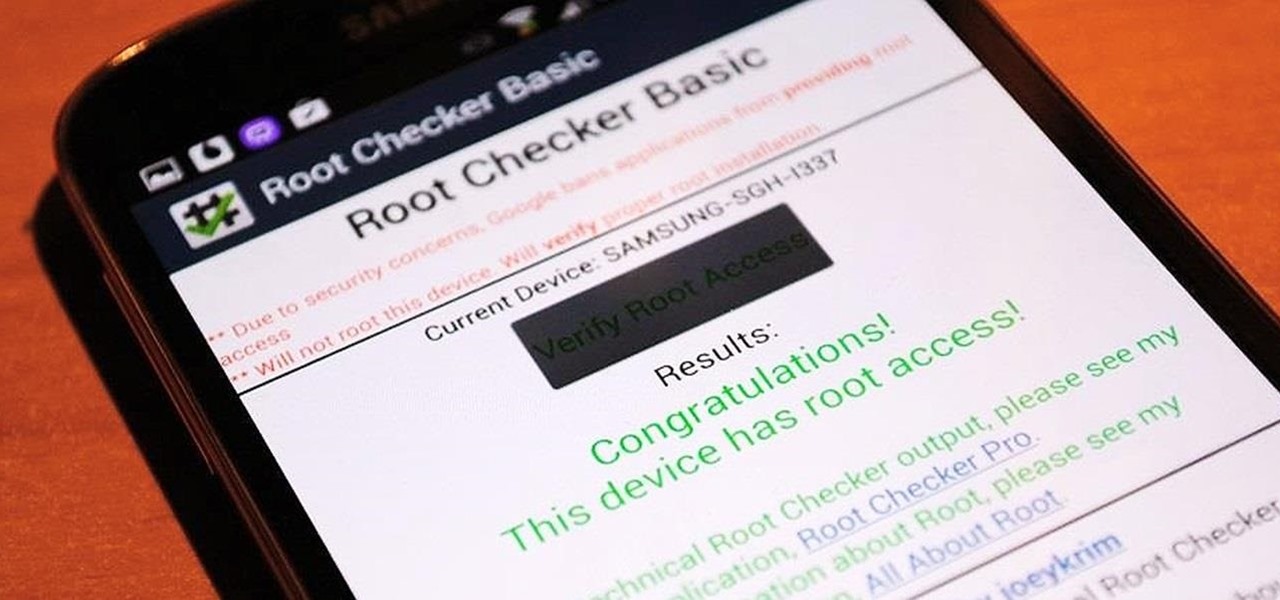
Rooting is usually the first thing on the to-do list whenever one of us softModders gets a new Android device. Unfortunately our efforts are sometimes hindered by certain obstacles; a common one is a locked bootloader.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Last week, I highlighted 5 of my favorite free interactive live wallpapers that you could use on your Android device. But where do you go from there? What's the next step up?
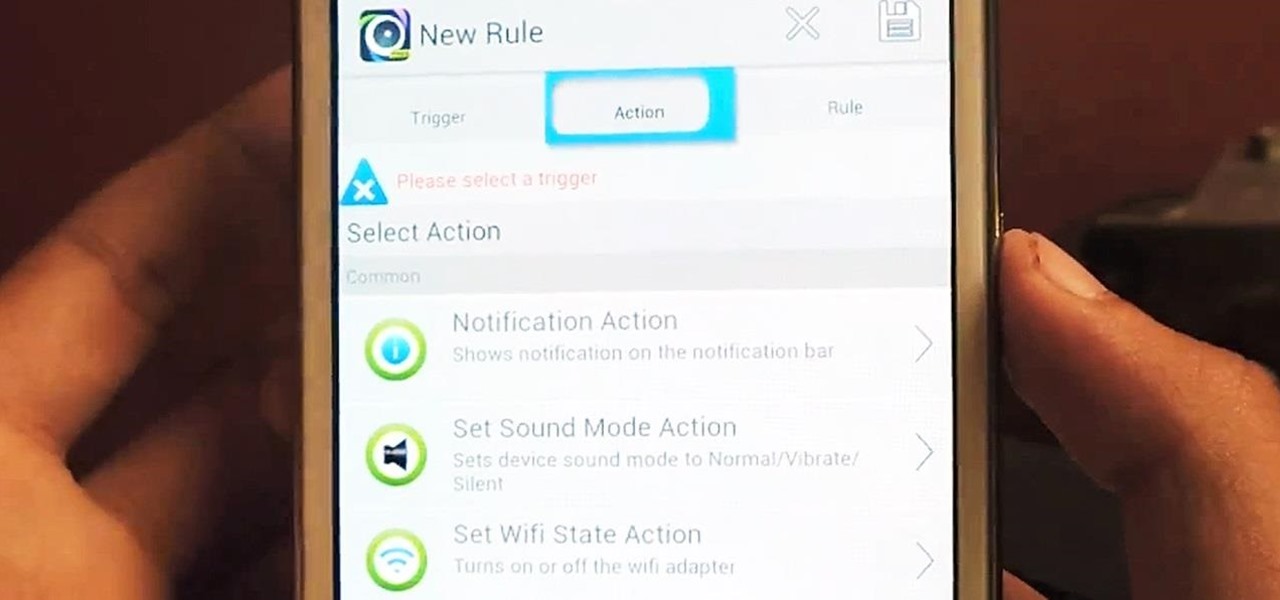
Automating tasks on your Samsung Galaxy Note 2 is nothing new. Everything from adjusting screen brightness, to turning on the flashlight, to saving Snapchat pictures can be done automatically with the help of a few function-specific apps. The only problem with task-specific apps is that you have to download a handful of them to get everything you want, which can quickly add up. Now, thanks to AutomateIt, you can clean up your app drawer on your Note 2 and create loads of custom tasks using ju...

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

As practically the entire Steampunk world knows by now, IBM has predicted that Steampunk will be the big new trend from 2013 to 2015. They based this prediction on their computers, which sift through broad swathes of the internet in order to see patterns that may help commercial industries. According to them, Steampunk has been on the rise for the last few years, and they predict that it will explode into peak popularity within the next two years. But what does that mean and how will it impac...