Did you know you can help protect yourself when traveling with a gun? No, not like that; and not in any way that's going to land you in prison. Simply by packing a gun, you can ensure that not only will your luggage be safer, but that the airline will make certain that it reaches its destination. Photo by Alamy

As the COVID-19 virus continues to spread, counties, cities, and states are closing down businesses, events, and schools that aren't absolutely necessary. Some companies around the US are recommending or requiring employees to work from home during the coronavirus pandemic. If you're stuck at home, there are apps and services to help you make it through a lockdown.

When it comes to resistance to the elements, Samsung seems to believe in the old saying "if it ain't broke, don't fix it." They've carried over the IP68 rating under IEC 60529 that was first found on the S8 all the way to their tenth-anniversary flagship, the Galaxy S10. While this certainly sounds great on paper, it's natural to want to dig a little deeper and find out what the rating means.
You really can't go wrong with Samsung Health when it comes to staying on top of fitness-related data. Its features help you keep track of workouts, track calorie and nutrition intake, and monitor your heart rate, just to name a few. And if you start exhibiting symptoms you've never had before, you can even use the app to find out more about what's wrong with you.
If you subscribe to notifications for Magic Leap CEO Rony Abovitz's Twitter feed, you'd think everyone in the world already has a Magic Leap One. Alas, that is not the case, but those not within the geographic areas of Magic Leap's LiftOff service now have a loophole through which they, too, can join the "Magicverse."

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.

Despite what you may have heard, sleep is NOT for the weak. It's essential, not to mention it makes us feel a hell of a lot better in general. But for some, getting to sleep is easier said than done. In fact, about 50 million to 70 million people in the US have a sleep or wakefulness disorder, according to the CDC.

When it comes to busted smartphones, liquid damage ranks right up there with shattered screens as one of the most common issues owners have to deal with—as well as the most embarrassing. Thankfully, though, with the rise of waterproof phones such as the Samsung Galaxy S7 and even the iPhone 7, this is becoming less and less of a worry. But not everyone has a waterproof device.

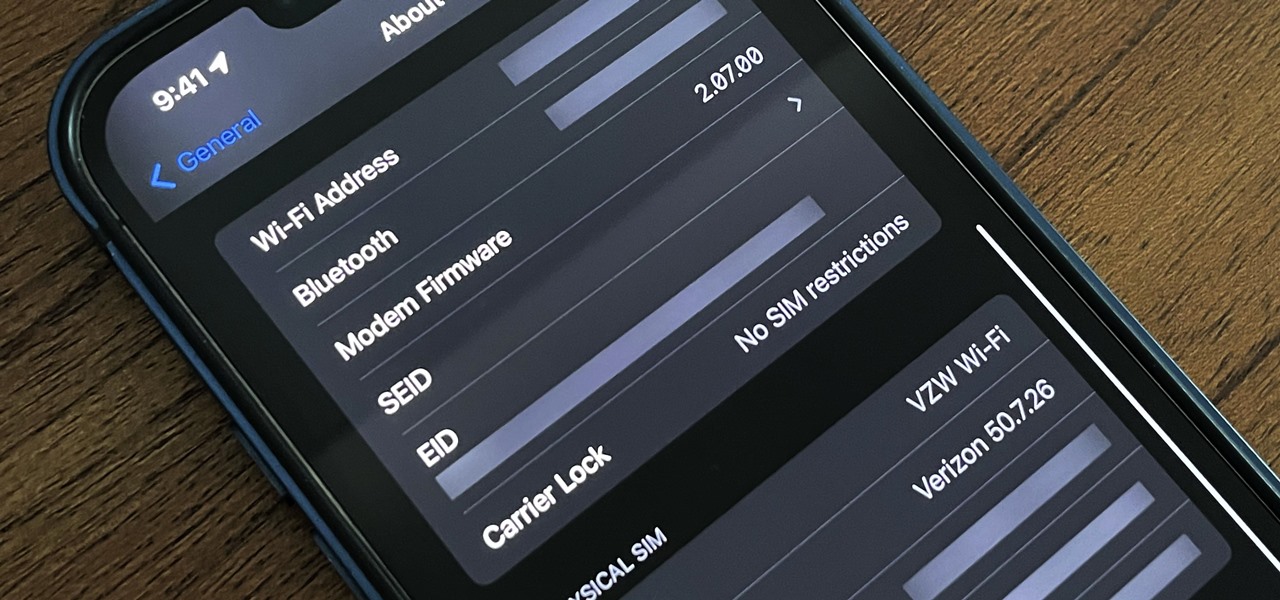
If your smartphone is ever lost or stolen, it's a terrible experience. If you file a police report, chances are the responding officer will need your device's IMEI or MEID number if you want to stand a chance of getting it back. Same goes for making an insurance claim on a lost or broken phone, so it's definitely important to have this unique identifier handy.

Assuming that you're not going to knit a sweater and celebrate New Year's Eve with Ryan Seacrest and Jenny McCarthy on ABC's “New Year's Rockin' Eve," it's a pretty safe bet to say that you're probably going to consume alcohol—a considerable amount of alcohol.

If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.

If your current cellular provider costs too much, has poor reception in your area, or doesn't support features you'd like to use, switching to another carrier is the obvious move. But can you bring your current iPhone or Android phone?

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Do you want to sell your car? It's important to make sure that you have everything in place before you hand off your car. Do your research, and everything will fall in place. Watch this video to learn how to cancel your license tags when you sell your car.

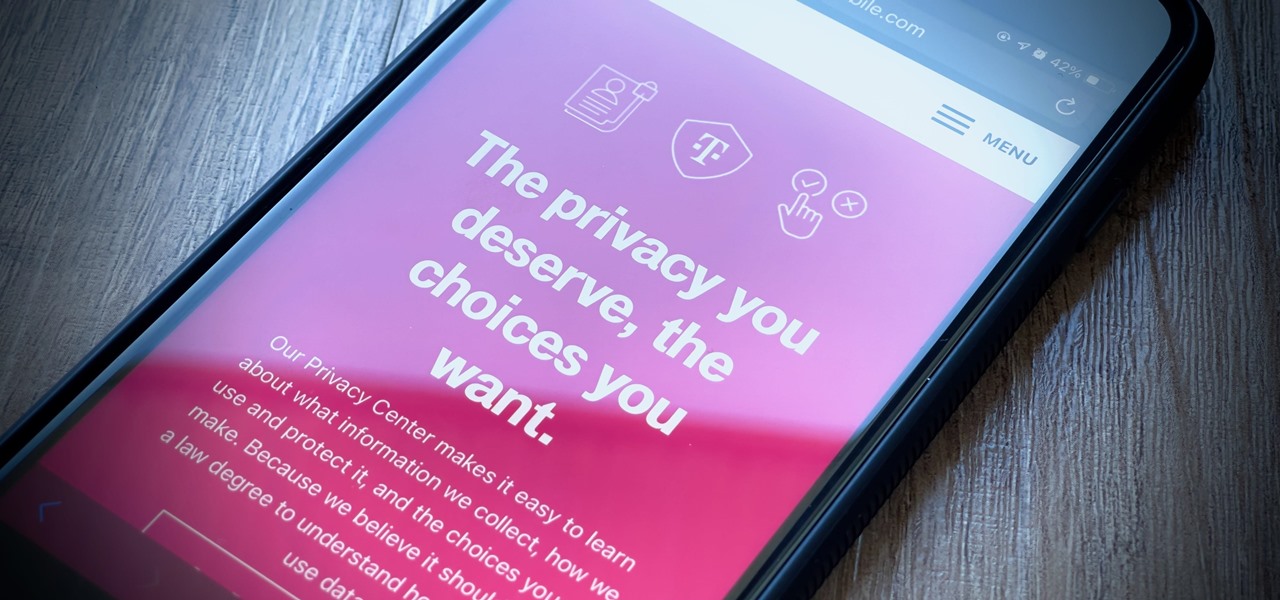
It's getting harder and harder to escape ad tracking by the day. For the latest example, look no further than T-Mobile. The No. 2 carrier updated its privacy policy on Feb. 23, 2021, indicating that it would start sharing customer data with advertisers under the guise of more relevant ads starting April 26. If that's not something you'd like to participate in, there's a way to opt-out.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

If you work for a company you are probably entitled to maternity leave. Gather as much info as possible and then have an honest conversation with your employers. With tact and civility should be able to have time to recover with your baby and keep your job too.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

Facebook and its Oculus subsidiary have been open about their intentions to bring AR wearables into the mainstream for some time now.

I love finding new artists on Spotify to listen to but hate when musicians I don't like keep popping up in recommended playlists and radio stations. For the longest time, there was nothing you could do about it, but now, Spotify lets you block specific bands and singers from ever playing again.

Thanks to recent reports, we now know third-party apps have a lot more access to our Gmail than we may have initially thought. In fact, these third-party apps have the ability to read our emails, not because these companies are necessarily shady, but because we agreed to it. Luckily, there's a way to view which apps have this access, as well as a way to boot those apps from your Gmail entirely.

With each year that we anxiously await Apple's next big version of iOS, there comes the sad reality that the eldest iPhones will not continue to receive support. That's not the case with iOS 12, however, as the software is compatible with all iPhones currently running iOS 11, going back as far as the iPhone 5S.

A development duo has concocted an iPhone app that displays related tweets based on objects recognized by the device's camera.

In late June, the biggest measles outbreak to strike Minnesota since 1990 seemed to be winding down. Today, public health officials announced a new confirmed measles case in the area.

Much work needs to be done before laws and regulations no longer block driverless' rollout in the US, Rob Csongor, vice president and general manager of Nvidia's automotive division, said today during a US Senate committee hearing.

Apple is notoriously private when it comes to perspective products, but the latest leak from their De Anza office in Cupertino suggests that a new augmented reality device could be coming to a store near you.

Apple seems to want the public to perceive it as an environmentally-conscious entity, as evidenced by the company's recently published Environmental Responsibility Report. But as it turns out, they may be hindering recyclers from salvaging old iPhones and Macs by ordering the devices to be shredded instead.

The Huawei Nexus 6P was released a little over a year ago, but despite doing moderately well in sales, the device has had more than its fair share of issues. When first released, there were numerous reception and memory management difficulties that left users extremely frustrated, though, those problems were solved with updates pushed by Google.

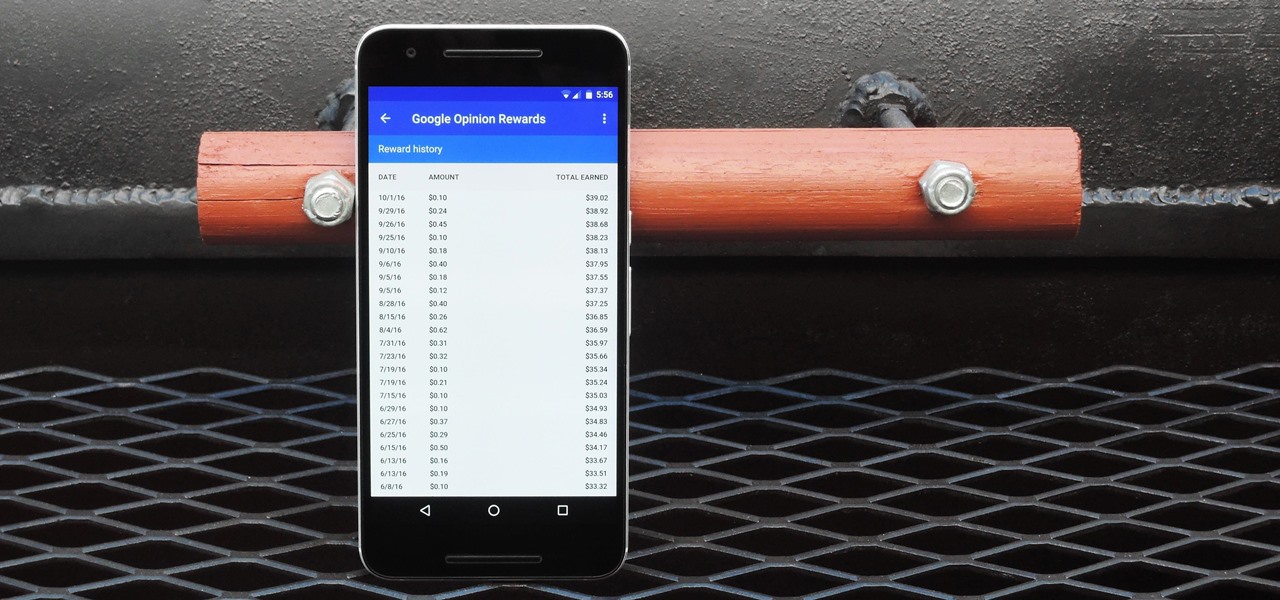
In case you didn't know, Google has an awesome app that gives you free money to spend on apps, games, movies, books, and virtually anything you can buy on the Google Play Store. The app is called Google Opinion Rewards, and all it asks in exchange for the Play Store credit is that you answer a few questions every now and then.

If you're looking to customize your Android beyond its stock options, things can get confusing quickly. One of the best places to get into developer mode is the XDA forums.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

While CNN, FOX News, and MSNBC are valuable sources of information for what's going on in the world today, they may not be the best news stations to watch if you actually want to learn something. They, along with local news stations, are great at grabbing your attention, but if you truly want to learn something about recent events, you're tuning into the wrong channel.

Apple's new iOS 8 has a ton of new features, and so does their revamped Safari app, only some of the features aren't quite as obvious as others. In this guide, I'll show you my 5 favorite Safari secrets in iOS 8 for your iPad, iPhone, or iPod touch.

Amazon.com has been around for a long time now, but there are still a few things most people don't know about when it comes to buying products from them. Here's a quick roundup of tips to help you get the most out of Amazon and save some money in the process. The holidays are the busiest time of year for online shopping, but these tricks will work all year around.

Every time you Google something or click on an ad in a YouTube video, Google gets paid. They are estimated to make well over $100 million a day, and I honestly think that's low-balling it.